Installing and Setting up the Checkmarx Cursor Extension
Installing the Extension
The Cursor Extension is available on the Open VSX Registry. You can initiate the installation directly from within Cursor.
Notice
Although there is no dedicated Checkmarx plugin for Cursor, the plugin for VS Code has been tested and is effective for use in Cursor.
To install the extension:
Open Cursor.
In the main menu, click on the Extensions icon.
Search for the Checkmarx extension, then click Install for that extension.
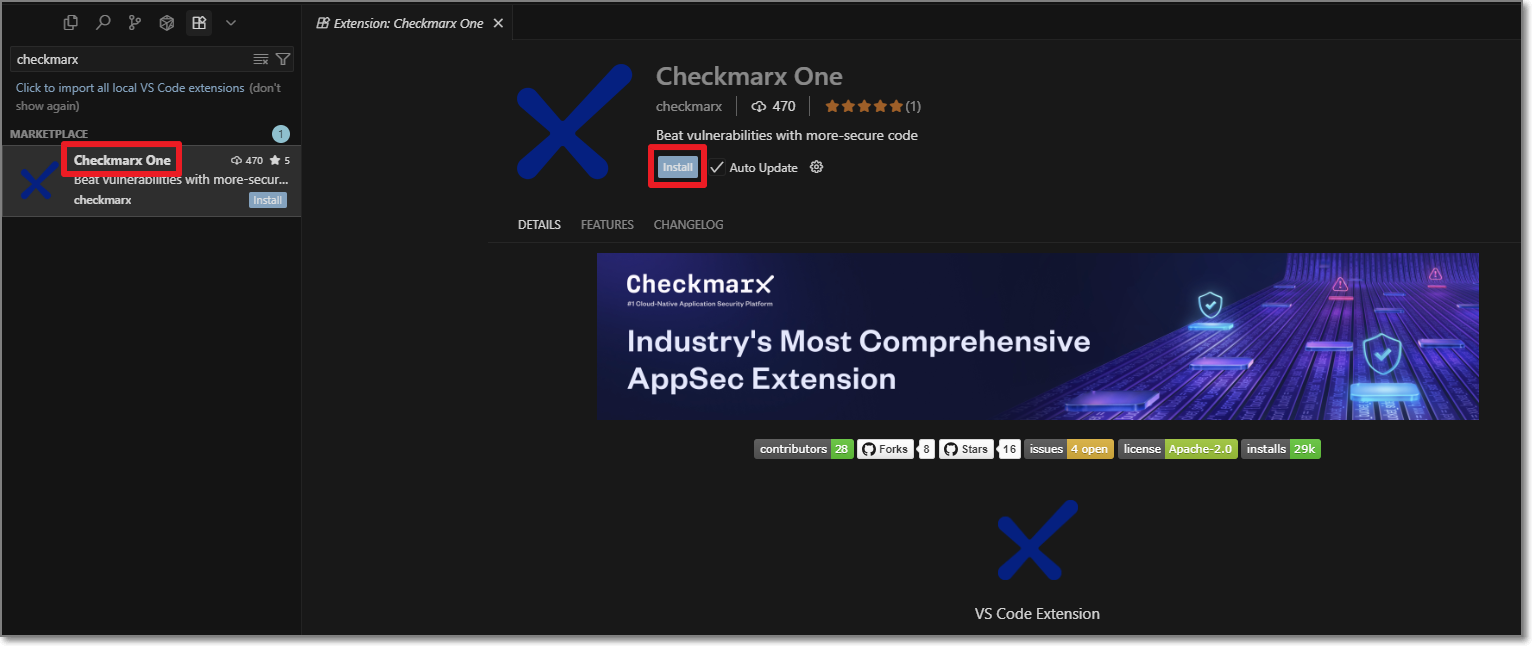
The Checkmarx extension is installed.
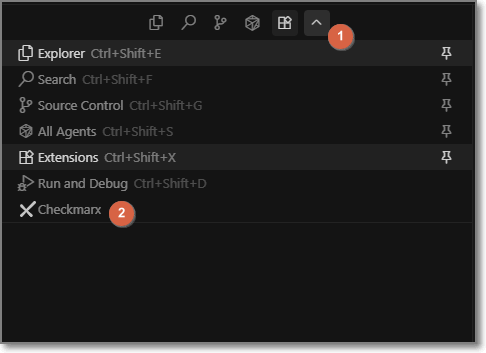
To open the Checkmarx extension, click the arrow box next to the extension icon, and select the Checkmarx icon.
Setting up the Extension
After installing the plugin, in order to use the Checkmarx One Platform tool you need to configure access to your Checkmarx One account, as described below.
Notice
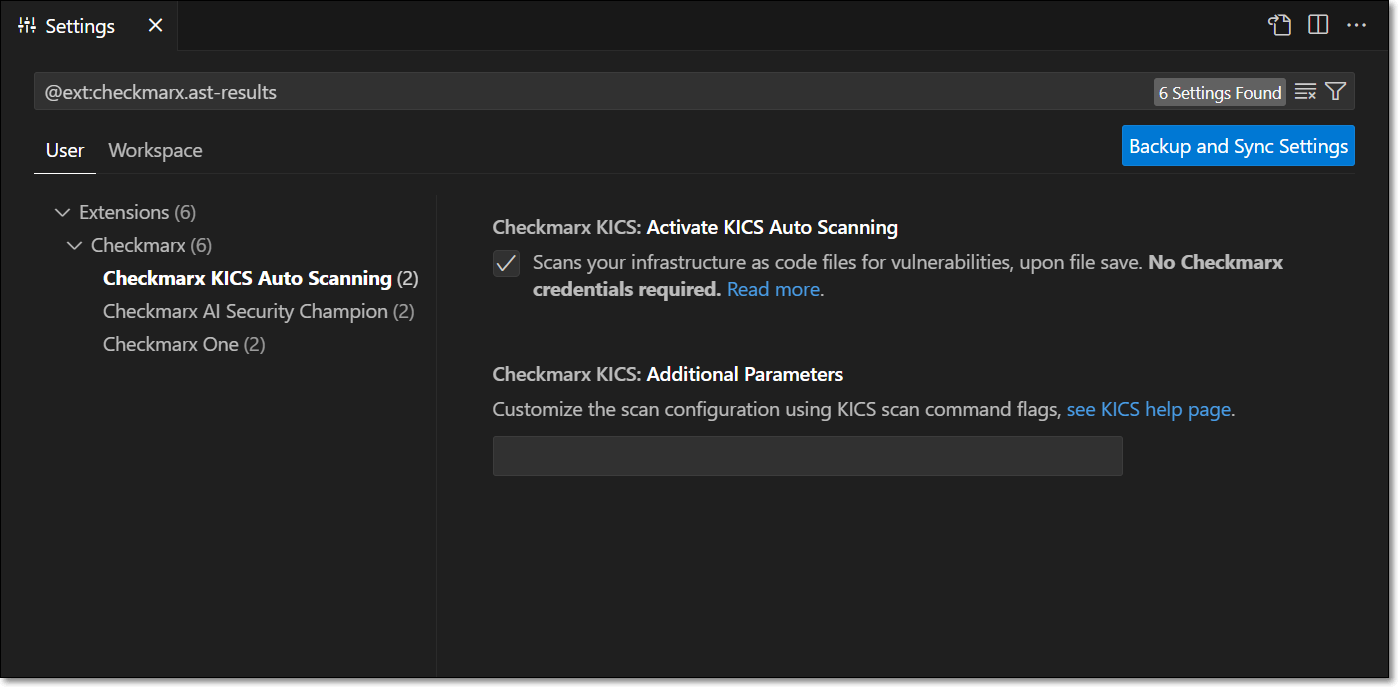
If you are only using the free KICS Auto Scanning tool and/or the SCA Realtime Scanning tool, then this setup procedure is not relevant. However, for SCA Realtime Scanning tool, if your environment doesn't have access to the internet, then you will need to configure a proxy server in the Settings, under Checkmarx One: Additional Params.
In the Cursor console, click on View > Extensions.
On the Checkmarx extension, click on the Manage icon and then click Settings.

The Checkmarx Settings tab opens.

Click on Authentication.
Notice
There is an alternative method to enter credentials by clicking on Edit in settings.json and adding the credentials to the file, but this is generally not recommended.
A new tab opens showing the Checkmarx One Authentication dialog.

Connect to Checkmarx One either using an API Key or your login credentials.
Important
In order to use this integration for running an end-to-end flow of scanning a project and viewing results with the minimum required permissions, the API Key or user account should have the role
plugin-scanner. Alternatively, they can have at a minimum the out-of-the-box composite roleast-scanneras well as the IAM roledefault-roles.Login Credentials
Select the OAuth radio button (default).
Enter the Base URL of your Checkmarx One environment and the name of your tenant account, then click Sign in to Checkmarx.
Notice
Once you have submitted a base URL and tenant name, it is saved in cache and can be selected for future use (saves up to 10 accounts).
If you are logged in to your account, the system connects automatically. If you are not logged in, your account's login page opens in your browser. Enter your Username and Password, and then your One-Time Password (2FA) to log in.
API Key (see Generating an API Key)
Select the API Key radio button.
Enter your Checkmarx One API Key.
Click Sign in to Checkmarx.
Go back to the Settings tab, and in the Additional Params field, you can submit additional CLI params. This can be used to manually submit the base url and tenant name if there is a problem extracting them from the API Key. It can also be used to add global params such as
--debugor--proxy. To learn more about CLI globalparams, see Global Flags.
Configuring Checkmarx Developer Assist
Go to the Checkmarx settings and select CxOne Assist settings.
Make sure that the desired CxOne Assist checkboxes are selected.
If MCP is activated on the tenant level, then these should be selected by default. You can deselect any scanners that you don't want to run.
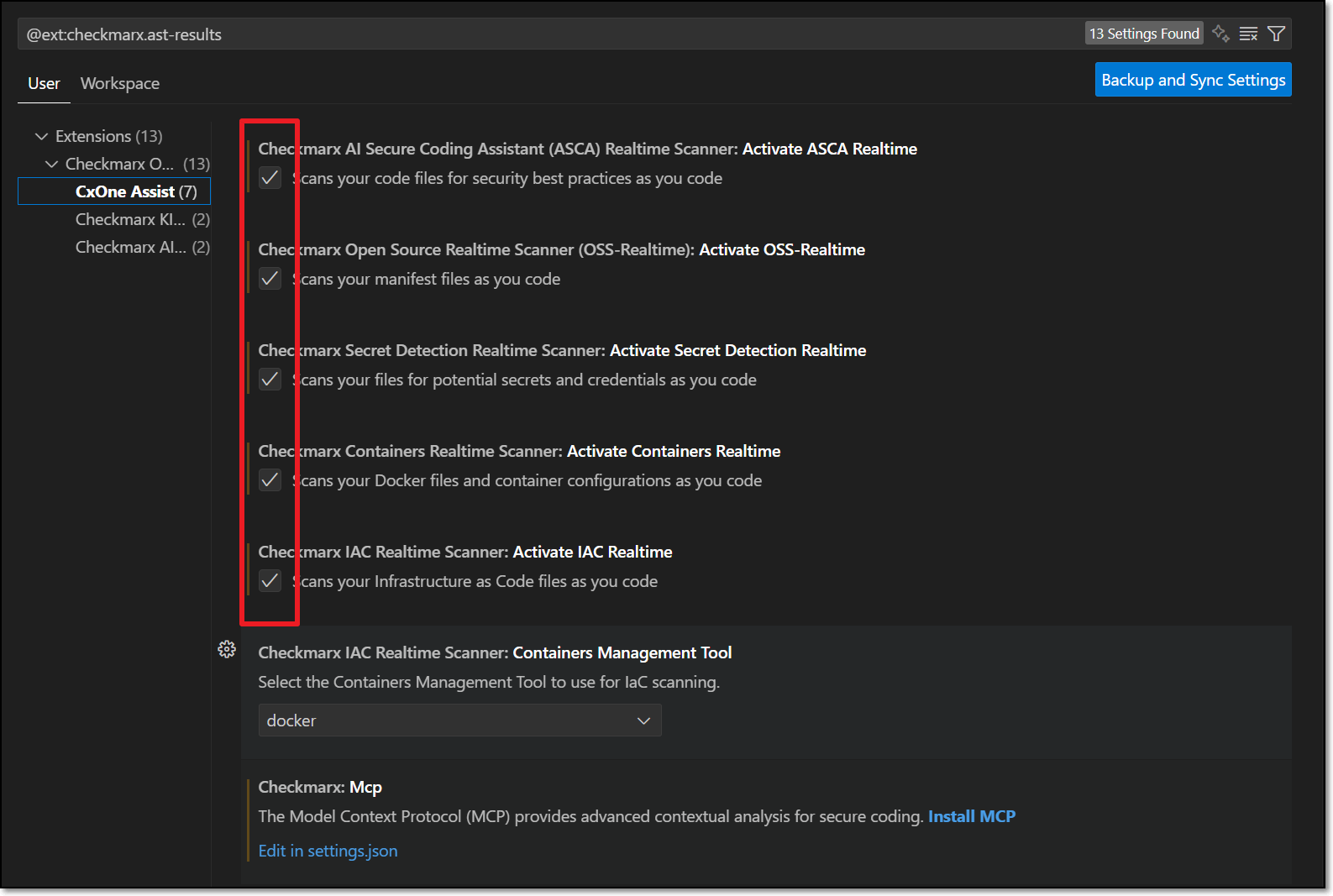
For the IaC Realtime scanner, select the Containers Management Tool used in your environment. Options are docker or podman.
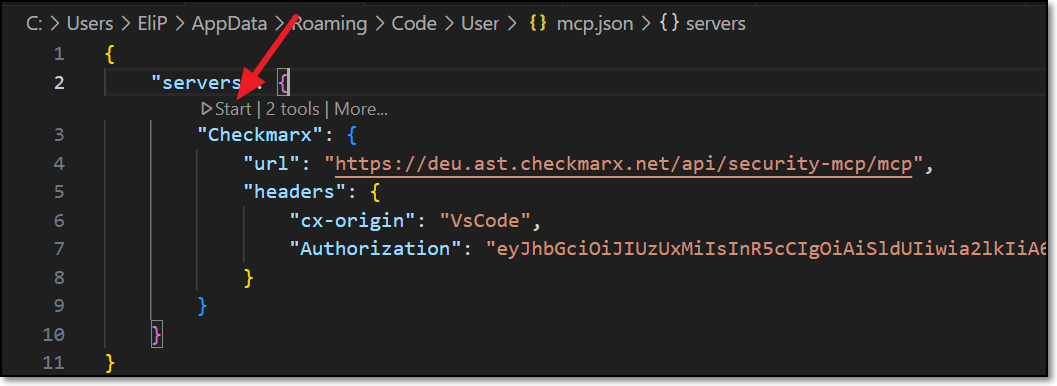
Click on Install MCP.
The Checkmarx MCP is added to your mcp.json file.
Notice
In some cases the MCP is installed automatically when you authenticate with Checkmarx. However, best practice is to click on Install MCP so that the MCP file opens and you can ensure that it starts running, as shown in the following step.
If the process doesn't start automatically, you may need to open the file and click Start.
Notice
If there is a problem with the automatic installation, check Troubleshooting - Manually Configuring the MCP Server.
Configuring AI Security Champion
AI Security Champion can be used with the Checkmarx One tool as well as with the KICS Realtime Scanning tool. In order to use AI Security Champion you need to integrate the extension with your OpenAI account.
Notice
If the Global Settings for your account have been configured to use Azure AI instead of OpenAI, then the credentials are submitted on the account level and it is not possible to submit credentials in your IDE for an alternative AI model.
To set up the integration with your OpenAI account:
Go to the Checkmarx extension Settings and select Checkmarx AI Security Champion.
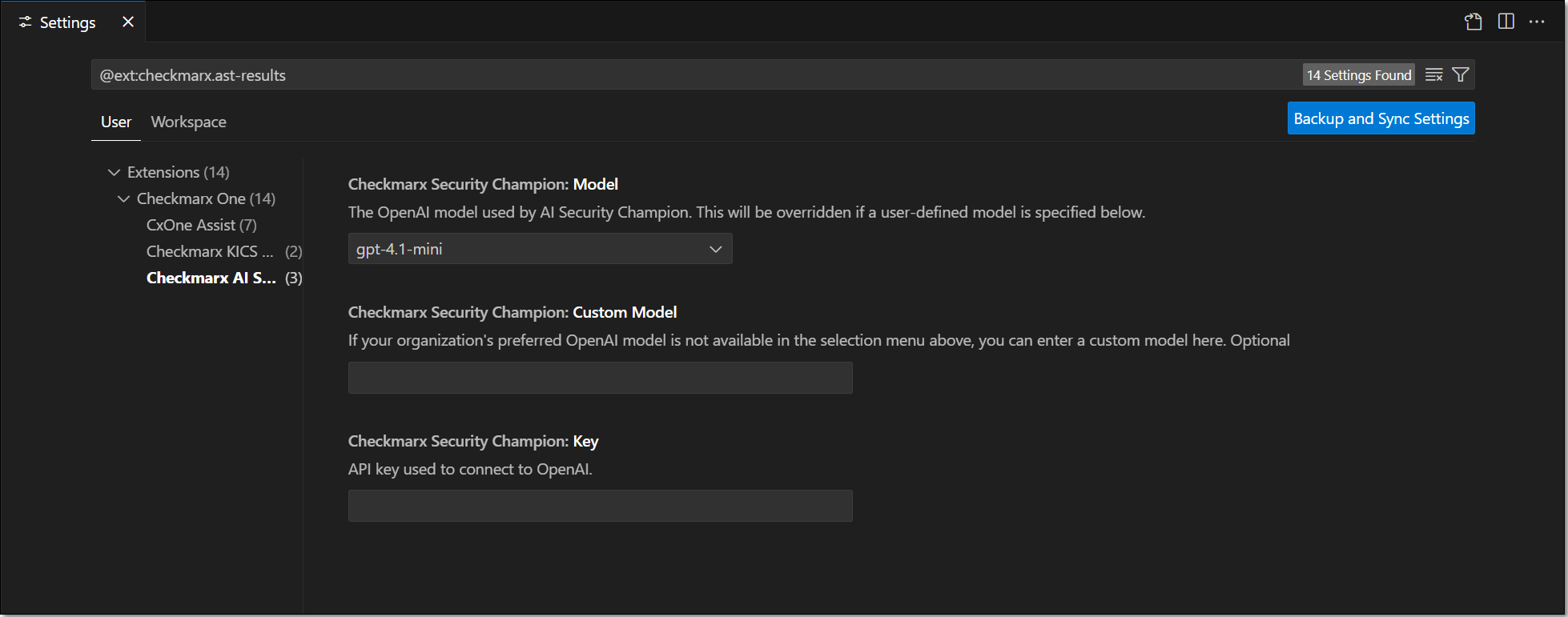
In the Model field, select from the drop-down list the model of the GPT account that you are using.
In the Key field, enter the API key for your OpenAI account.
Notice
Follow this link to generate an API key.
The configuration is saved automatically.