LDAP Management in CxSAST
Notice
For SAST versions 9.2 and later, refer to Settings Tab - LDAP Server Settings (v2.0 and up).
To access the LDAP server, the LDAP client must first authenticate itself to the server. The client tells the LDAP server who is going to be accessing the data so that the server can decide what the client is allowed to see and do. If authentication is successful, the server subsequently receives the request from the client. The LDAP server then checks whether the client is allowed to perform the request. If authentication is unsuccessful, CxSAST tries to authenticate the client (user) via its internal database. For every LDAP authenticated user, CxSAST creates a new user in its internal database (provided the user does not already exist) and then automatically assigns that user to a group(s) according to predefined role mapping (see Defining Role Mapping Settings).
Adding an LDAP Server
To add a new LDAP Server:
Select Management > Connection Settings > LDAP Servers. The LDAP Server window is displayed.
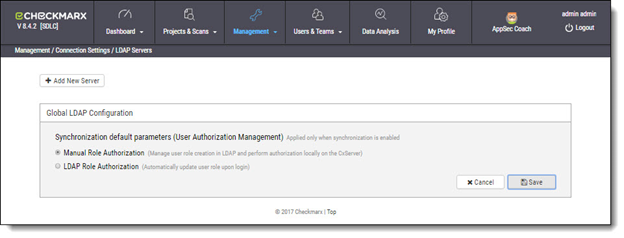
Click <+ Add New Server>. The LDAP Server Authentication window is displayed ready for configuration (see Configuring LDAP Authentication).
To delete an existing LDAP Server, click <Delete>.
Configuring LDAP Authentication
Authentication establishes proof of identity for users who attempt to log in to CxSAST via the LDAP server. When a user logs in, the user name and password are sent to the LDAP server to verify the credentials. To avoid exposing this information to the network, you can use the simple authentication mechanism (SSL), provided that it is supported by the LDAP server. User attribute values are case sensitive.
To configure LDAP Authentication settings:
With the LDAP Server window displayed, click the server header to open/expand the server parameter fields for configuration.
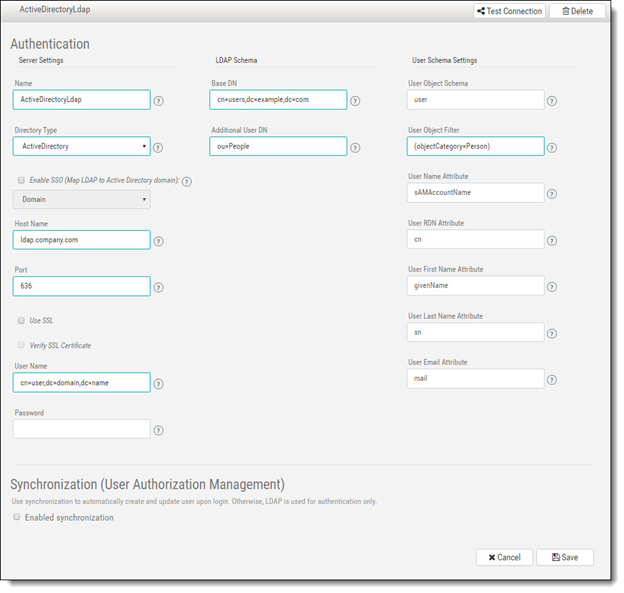
Define the Authentication parameters outlined in the table below.
When done, click <Save> to save the changes.
To test the connection, click <Test Connection>
Parameter | Description |
|---|---|
Name | Server name |
Directory Type | Provides auto selection for server parameters according to default settings (ActiveDirectory, OpenLDAP, or LDAP Server)
NOTE: SSO and domain selection is only enabled for ActiceDirectory users. |
Host Name | LDAP server hostname, for example ldap.company.com |
Port | Port of the LDAP server, for example 389, 636 (for SSL)
|
User Name | Name of the user that the application uses when connecting to the LDAP server, for example user@domain.name or n=user,dc=domain,dc=name NOTE: You can enable or disable the use of the LDAP control extension for paging of search results. If paging is enabled (default), the search will retrieve sets of data rather than all of the search results at once. Therefore, if you are searching for a specific user then the definition in the User Name field should also be specific (using full user DN, e.g., dn=myuser,ou=people,dc=company,dc=com) |
Password | Password of the user specified above |
Base DN | Used to search for users (e.g., cn=users, dc=example, dc=com) |
Additional User DN | Used to limit users search to specific DN (e.g., ou=People) |
User Object Schema | LDAP user object class type to use when loading users (e.g., user, inetOrgPerson) |
User Object Filter | Filter expression to use when searching user objects (e.g., (objectCategory=Person)) |
User Name Attribute | Attribute field to use on the user object (e.g., cn=sAMAccountName) |
User RDN Attribute | Attribute field to use when loading the user distinguished name (e.g., cn) |
User First Name Attribute | Attribute field to use when loading the user first name (e.g., givenName) |
User Last Name Attribute | Attribute field to use when loading the user last name (e.g., sn) |
User Email Attribute | Attribute field to use when loading the user email (e.g., mail) |
Configuring LDAP Synchronization
LDAP synchronization, once enabled, synchronizes CxSAST and LDAP directory users and groups in a single direction (LDAP to CxSAST). This process creates, removes and updates users and groups in CxSAST to match the user list attributes defined in LDAP as closely as possible . The behavior of the LDAP global synchronization is determined by the settings defined in the LDAP global configuration. Refer to Defining Global Synchronization for further information. If synchronization is not enabled, LDAP uses authentication only. Refer to Configuring LDAP Authentication for further information.
To configure LDAP Synchronization settings:
Check Enable Synchronization. The LDAP Synchronization window is displayed.
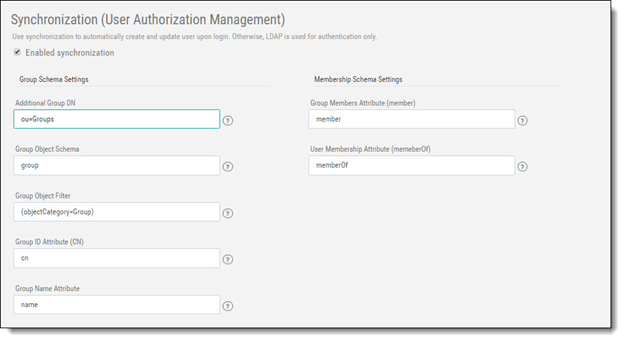
Define the following Synchronization parameters:
Parameter | Description |
|---|---|
Additional Group DN | Used to limit groups search to specific DN (e.g., ou=Groups) |
Group Object Schema | LDAP group object type (e.g., group) |
Group Object Filter | LDAP filter expression to use when searching the groups (e.g., (objectCategory=Group)) |
Group ID Attribute (CN) | Attribute in LDAP defining the group's id (e.g., cn) |
Group Name Attribute | Attribute in LDAP defining the group's name (e.g., name) |
Group Members Attribute (member) | LDAP member attribute is a multi-value attribute that contains the list of distinguished names for the user, group, and contact objects that are members of the group (e.g., member) |
User Membership Attribute (memberof) | LDAP membership attribute is a multi-valued attribute that contains groups of which the user is a direct member (e.g., memberOf) |
Defining Role Mapping Settings
Role mapping settings, once defined, determine the role of users created in LDAP and otherwise not assigned a role in CxSAST, for example Scanner, Reviewer. Role Mapping parameters only apply when the Manual Role Authorization option is enabled. Refer to Defining Global Synchronization for further information.
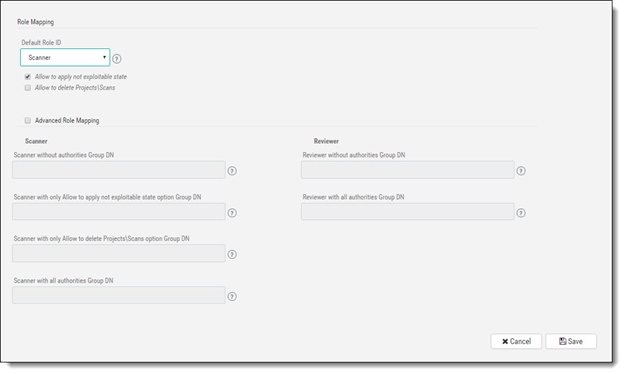
Define the Role Mapping parameters listed in the table below.
Once completed, click <Save> to save the changes
Parameter | Description |
|---|---|
Default Role ID | Used to determine the CxSAST role of users who have otherwise not been assigned roles (e.g., Scanner, Reviewer) Scanner - can delete projects\scans if the checkbox is selected. Select the Not Exploitable state checkbox to provide authorization to apply not exploitable state to instances Reviewer - can make changes to the status or severity of found instances if the checkbox is selected |
Advanced Role Mapping | Role mapping in CxSAST can be managed by checking the Advanced Role Mapping checkbox and the defining the parameters below. NOTE: Roles managed by LDAP are automatically updated upon login to CxSAST. |
Scanner without authorities Group DN | Used to define a list of LDAP Group DNs. Members of these groups will be assigned the scanner role without Apply Not Exploitable State and Delete Projects\Scan options (e.g., cn=dev, ou=grp, dc=my, dc=org, cn=qa, ou=grp, dc=my, dc=org). |
Scanner with only Allow to apply not exploitable state option Group DN | Used to define a list of LDAP Group DNs. Members of this group will be assigned the scanner role with only Apply Not Exploitable State option (e.g., cn=dev, ou=grp, dc=my, dc=org, cn=qa, ou=grp, dc=my, dc=org). |
Scanner with only Allow to delete Project\Scans option Group DN | Used to define a list of LDAP Group DNs. Members of this group will be assigned the scanner role with only Delete Project\Scans option (e.g., cn=dev, ou=grp, dc=my, dc=org, cn=qa, ou=grp, dc=my, dc=org). |
Scanner with all authorities Group DN | Used to define a list of LDAP Group DNs. Members of this group will be assigned the scanner role with Apply Not Exploitable State and Delete Projects\Scan options (e.g., cn=dev, ou=grp, dc=my, dc=org, cn=qa, ou=grp, dc=my, dc=org). |
Reviewer without authorities Group DN | Used to define a list of LDAP Group DNs. Members of this group will be assigned the reviewer role without Allow Severity/Status Change options (e.g., cn=dev, ou=grp, dc=my, dc=org, cn=qa, ou=grp, dc=my, dc=org). |
Reviewer with all authorities Group DN | Used to define a list of LDAP Group DNs. Members of this group will be assigned the reviewer role with Allow Severity/Status Change options (e.g., cn=dev, ou=grp, dc=my, dc=org, cn=qa, ou=grp, dc=my, dc=org). |
Defining Global Synchronization (User Authorization Management)
Global Synchronization (User Authorization Management) supports the retrieval of users from the LDAP server as well as defining them in CxSAST. This enables full control over global team membership. For example, if a global team is synchronized to an LDAP database, and a developer leaves your company, the privileges granted through the global team membership will be removed and you will be able to reassign or remove the individual. This only applies if the LDAP synchronization option is enabled. Refer to Configuring LDAP Synchronization.
To define global synchronization:
Select Management > Connection Settings > LDAP Servers. The LDAP Server window is displayed.
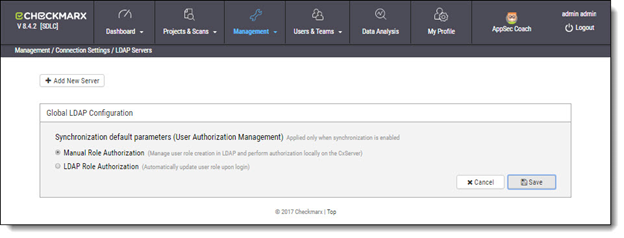
Select the preferred synchronization default parameters as outlined in the table below.
Once completed, click <Save> to save the changes.
Parameter | Description |
|---|---|
Manual Role Authorization | User creation is managed by LDAP and authorization performed manually by CxSAST user management. By default, LDAP users belong to one team and are either defined as scanners or reviewers upon login. You can manually change a logged in user’s Team and Role from CxSAST (see Mapping LDAP User Groups to CxSAST Teams). |
LDAP Role Authorization | Role authorization is managed by LDAP and automatically updated upon login to CxSAST. Role authorization and management definitions are defined during the creation and mapping of user attributes in LDAP. |
Page Contents
Defining Global Synchronization (User Authorization Management)
Read more