- Checkmarx Documentation
- Checkmarx SAST
- SAST On-Premises Policy Management
- Configuring a Policy
Configuring a Policy
Select Policy Management to open the Policy Management home screen and select Create New Policy to open the Policy Details form.
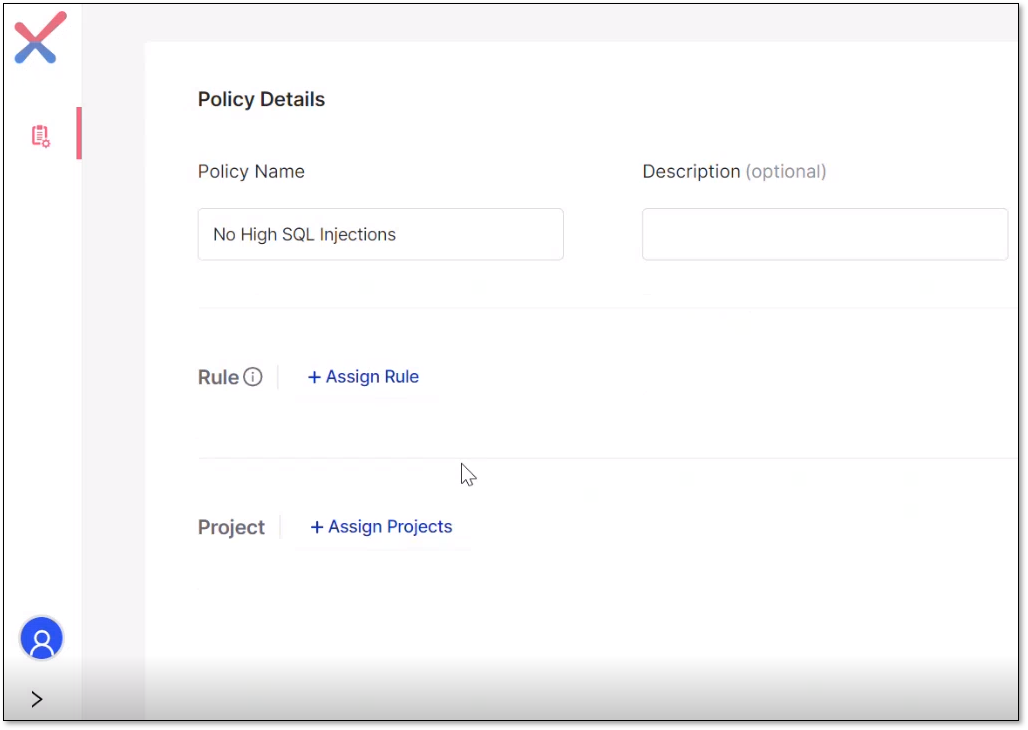
Fill out the rules and project details in the forms and assign them as relevant. Including a description of the policy for organizing and efficiency purposes is recommended.
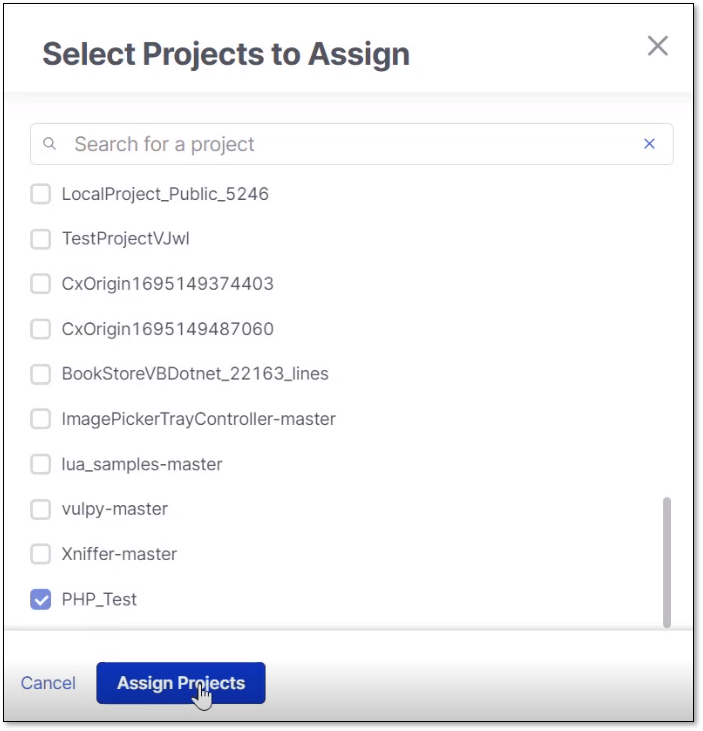 Assigning Rules
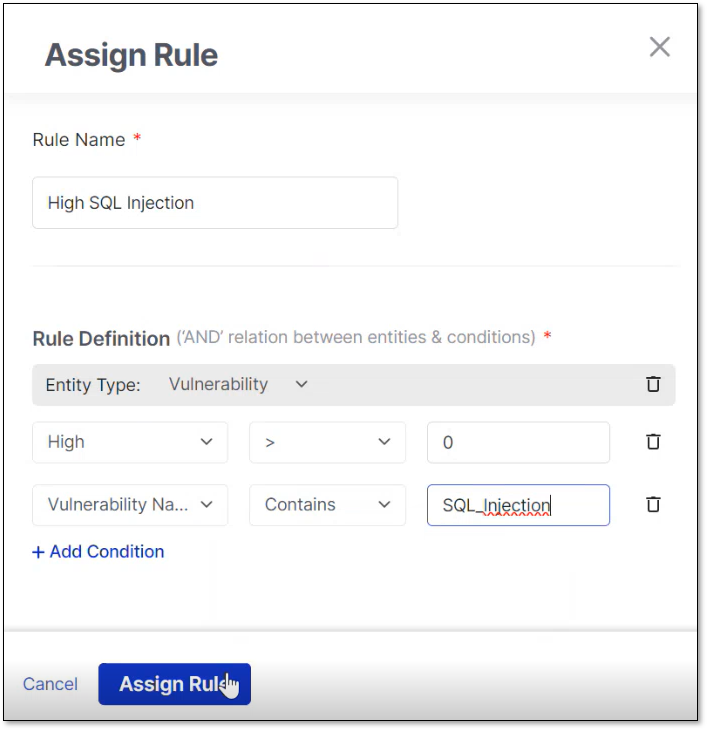
Assigning RulesIn the Assign Rule pane, perform the following:
In the Rule Definition section, click Select Entity and select the desired entity from the dropdown list.
Click + Add Condition.
Configure the following and click Assign Rule when done:
Rule Subject:
Severity - High/Medium/Low/Info
or
Result Status - New/Recurrent
Operator: > / >= / < / <= / =
Value: Numeric value
Notice
For example, if for Entity Type Vulnerability, you set the Rule Subject as High, Operator as >, and Value as 2. Then, a project with 3 or more High severity SAST vulnerabilities will violate this rule.
Note
It is possible to configure multiple rules.
An AND relationship links entities and conditions. This means that all specified conditions must be met simultaneously for the associated entities to be considered.
Select Create Policy to complete the policy and to view it on the Policy Management home screen.
Once policies are created, they are displayed on the Policy Management home screen. You may drag policy names to reorder them on the dashboard, multi-select them to delete, or filter them by clicking on the column headers or using the search box.
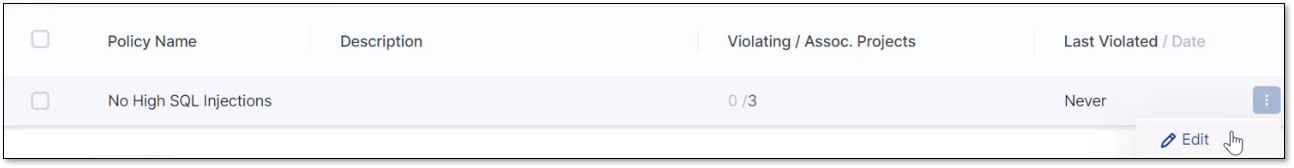
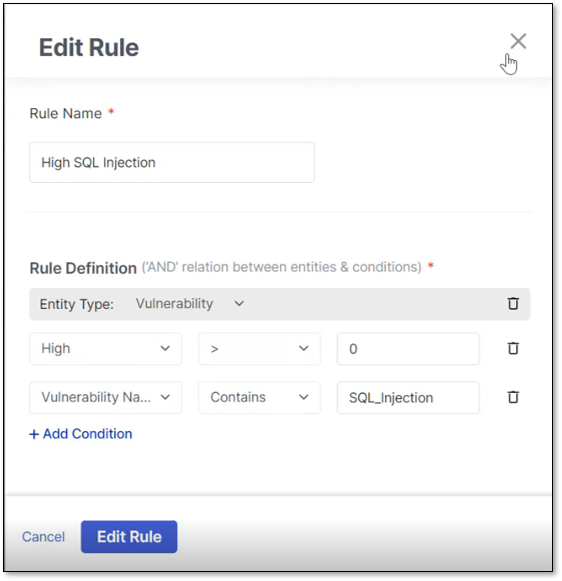
To pin the policy to the dashboard so it is always visible or to edit or delete a policy, click the ellipsis at the end of the policy row. Editing a rule opens the Edit Rule window like the Assign Rule window detailed above. Click Edit Rule when complete.
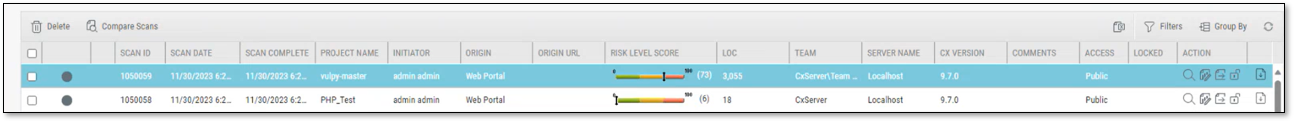
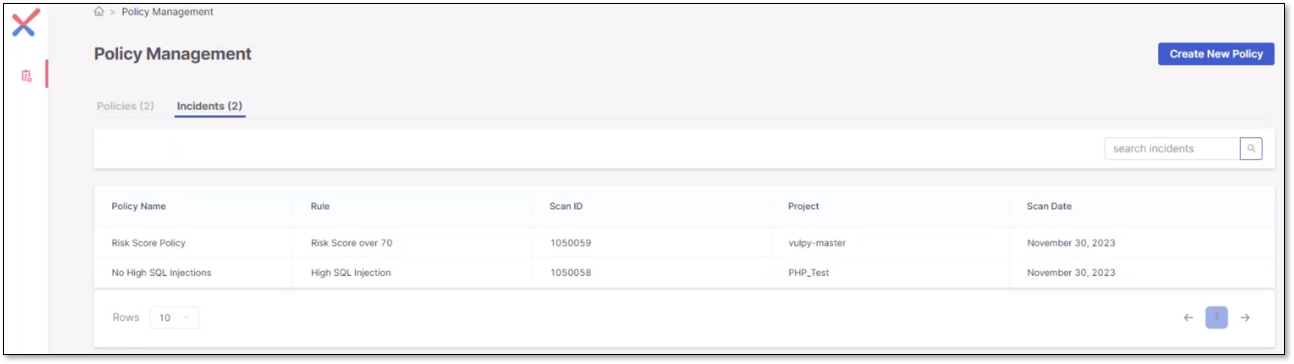
After assigning the policies to the relevant projects, you can scan them in SAST, and any violations of the policies and their rules will appear as incidents under the Incidents tab on the Policy Management homepage. The Incidents tab displays the policy names, the rules violated in the policy, the scan ID, the assigned project name, and the last scan date with the violation(s).
Similarly, on SAST, you can see the projects with the incidents and other details. Click on the  for a more comprehensive breakdown of the vulnerabilities detected and their severities.
for a more comprehensive breakdown of the vulnerabilities detected and their severities.