- Checkmarx Documentation
- Checkmarx DAST
- Viewing Results
Viewing Results
Checkmarx One shows data for all the environments in your tenant account as defined in Access Control. The Environments page (Applications and Projects → Environment tab) shows a table listing all of your environments.
You can also drill down to view the Environments page for an individual environment, which shows information about the scans currently running or that have finished. You can drill down further to view the All risks view, which shows detailed information about each risk identified in the last scan.
Viewing DAST Results in the Risk Table
Note
Please see here for details on triaging your DAST results.
Alerts and Paths
Before viewing your risk table, note that there are two ways Checkmarx organizes DAST results: Alerts and Paths. Alerts are the default setting for new Checkmarx users. Alerts groups DAST results by vulnerability type, while Paths organize each vulnerability by the result's path. Perform the following to switch between the Alerts view and the Paths view:
Navigate to Global Settings.
Select DAST.
Select the display mode: By Vulnerability or By Path.
Click Save when done.
In the Alerts view, clicking a result's View opens a panel displaying all its related instances. Clicking on a specific instance will provide more details and the evidence of the vulnerability.
Note
For organizational ease, Checkmarx recommends the Alerts view.
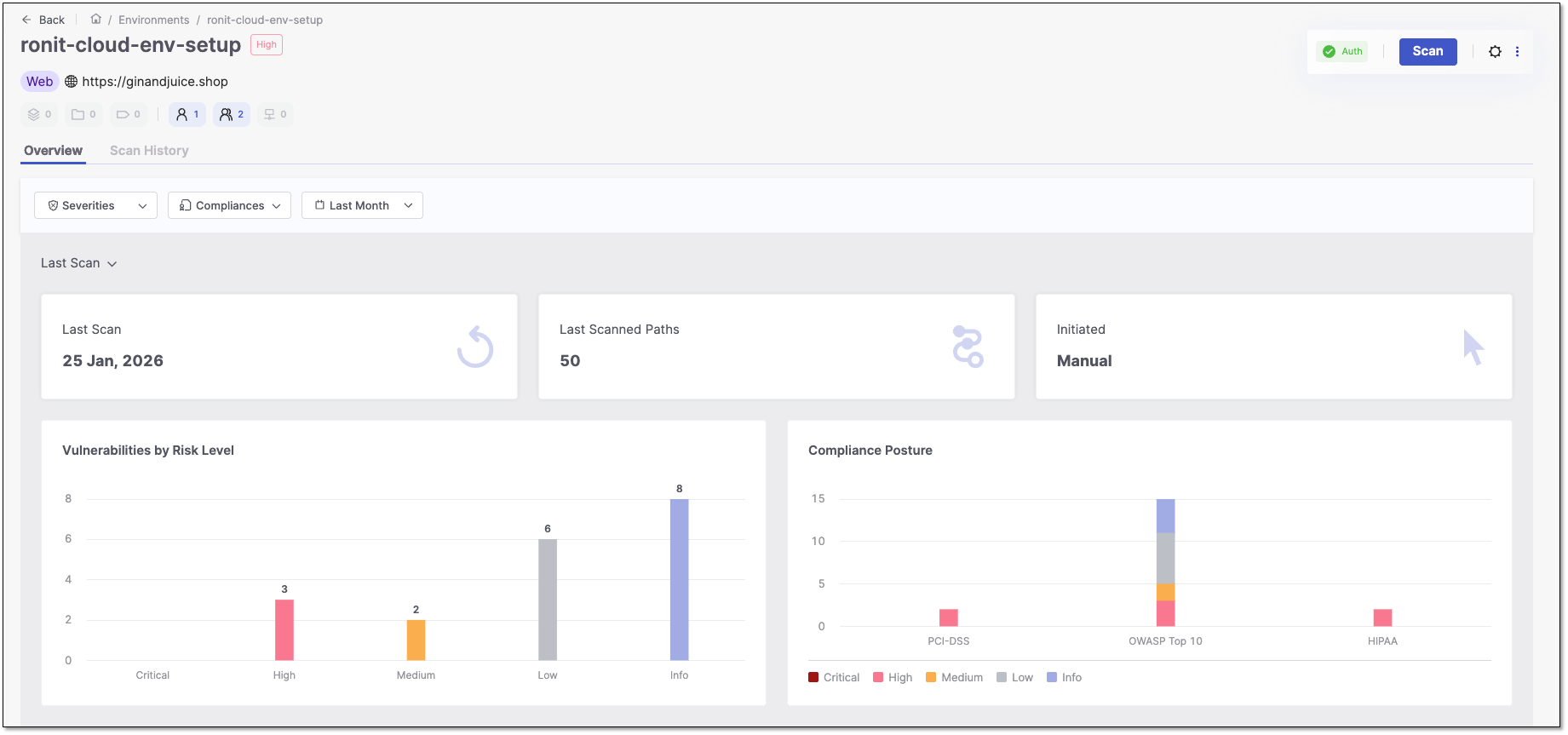
Overview Tab
Clicking  at the end of a result's row opens the result's overview. The overview tab displays an at‑a‑glance summary of an environment, including associated applications, groups, and users; scan dates and times; and high‑level dashboards of the discovered vulnerabilities and compliance postures. You can run a new scan for the environment by clicking Scan at the top of the page. Clicking
at the end of a result's row opens the result's overview. The overview tab displays an at‑a‑glance summary of an environment, including associated applications, groups, and users; scan dates and times; and high‑level dashboards of the discovered vulnerabilities and compliance postures. You can run a new scan for the environment by clicking Scan at the top of the page. Clicking  will open the settings for that environment. Clicking
will open the settings for that environment. Clicking  will open a dropdown of all the other actions for the environment.
will open a dropdown of all the other actions for the environment.
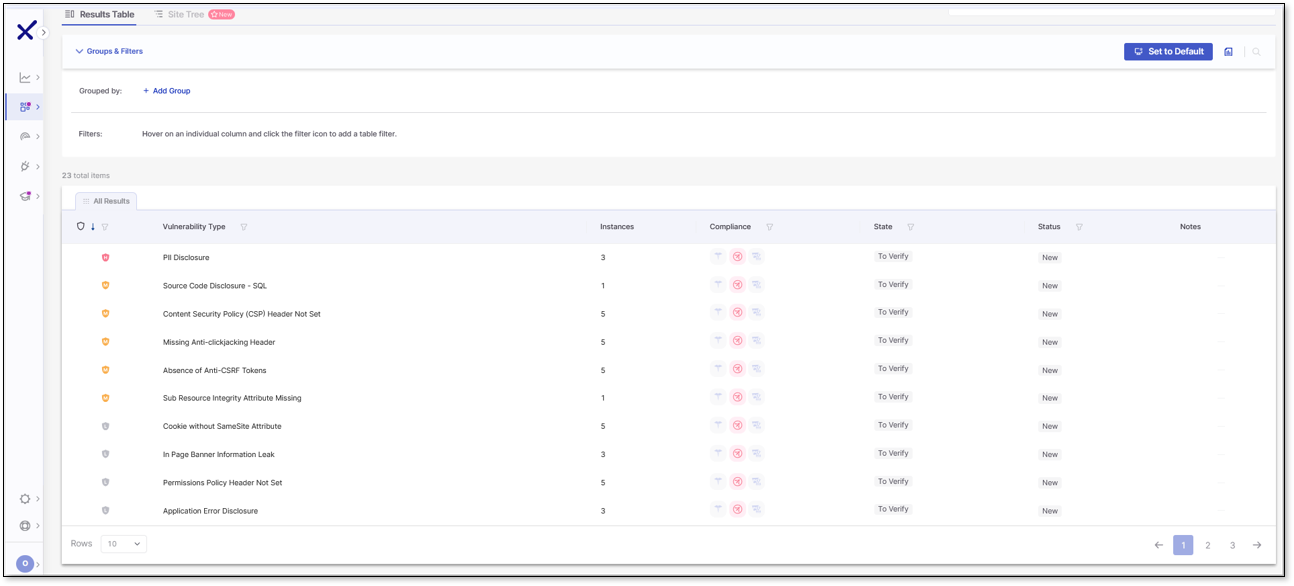
Results Table Tab
Click Results at the end of an environment row to open the Results Table tab alongside the Site Tree tab. The results table lists all vulnerabilities in your environment and organizes them by the following columns: Severity, Vulnerability Type, Instances, Compliance, State, Status, and Notes.
Severity - the vulnerability severity level: Critical
 , High
, High , Medium
, Medium , Low
, Low , or Info
, or Info
Vulnerability Type - the vulnerability type.
Instances - the number of instances the vulnerability appears
Compliance - when marked, the results failed to comply with one of the following standards: HIPAA
 , OWASP Top 10
, OWASP Top 10 , PCI-DSS
, PCI-DSS
State - the vulnerability state: To Verify, Confirmed, Urgent, Proposed Not Exploitable, Not Exploitable
Status - the vulnerability status: New or Recurrent
Notes - Any notes on the vulnerability.
By default, the table displays 10 rows, but you can change this to 20 or 50 in the dropdown. The table is paginated, and you can save your preferred view by selecting Set as Default.
You can also group or filter the data. To group results, add a grouping category such as Severity or Vulnerability Type. To filter results, hover over a column header, select  , and choose your filter options from the drop‑down menu. Columns can also be sorted in ascending or descending order by clicking the header.
, and choose your filter options from the drop‑down menu. Columns can also be sorted in ascending or descending order by clicking the header.
Accessing Risk Details
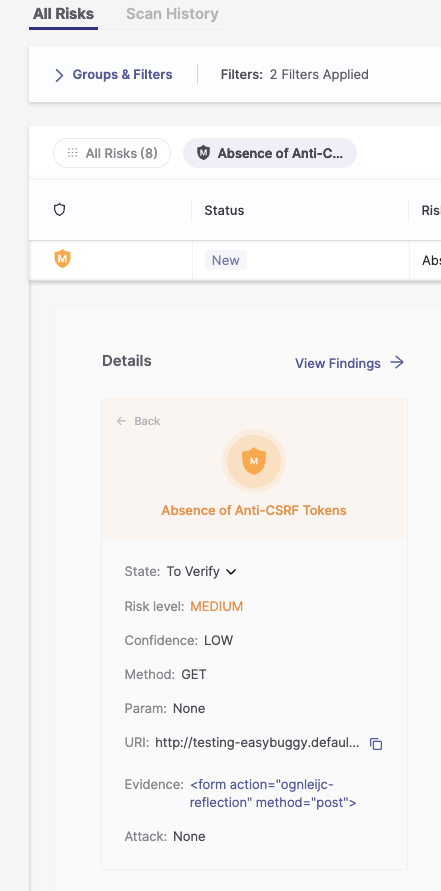
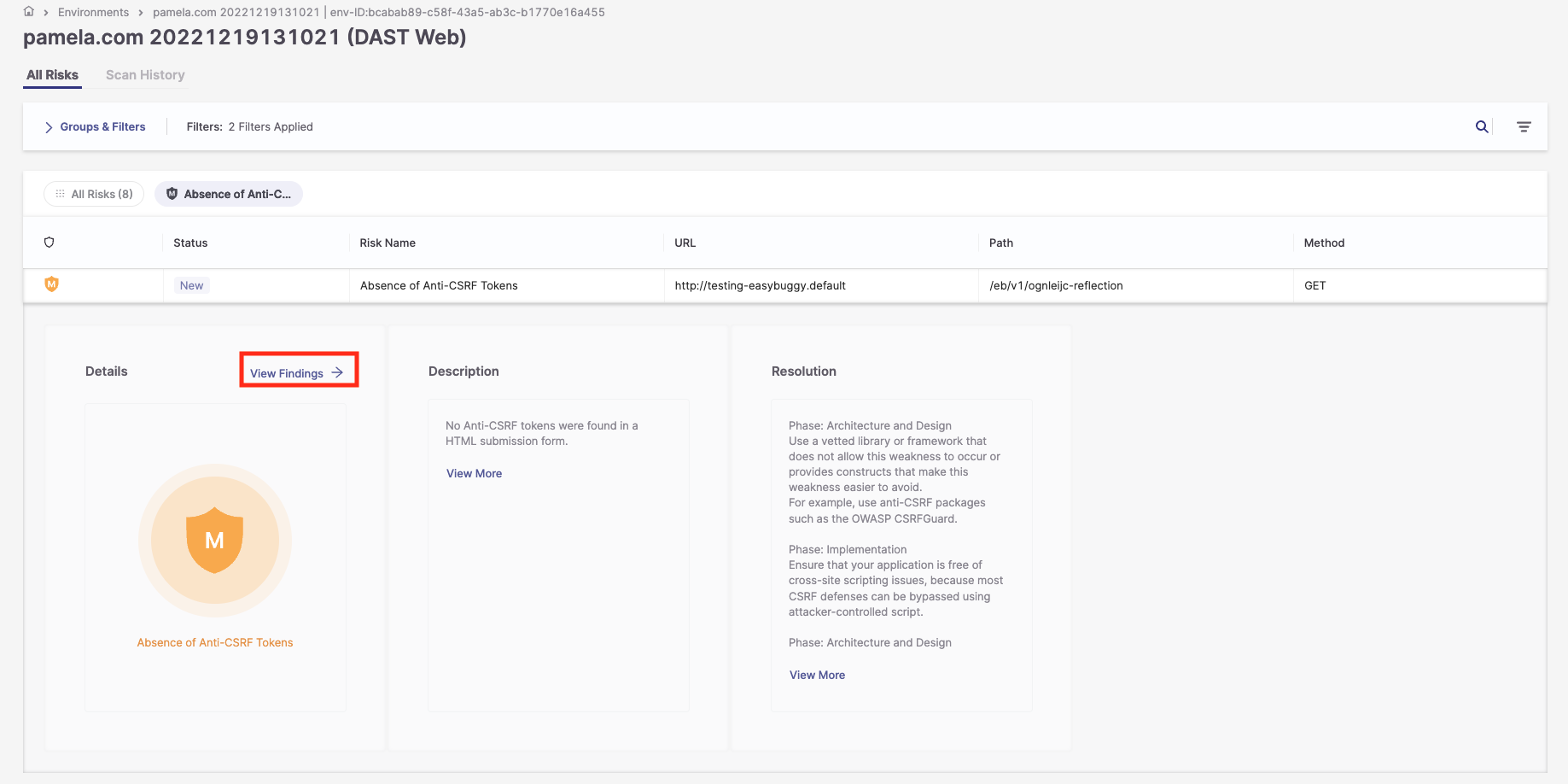
To access the risk details, click on the row for the risk you need details on. A new window will open, presenting a brief description of the risk and its resolution.
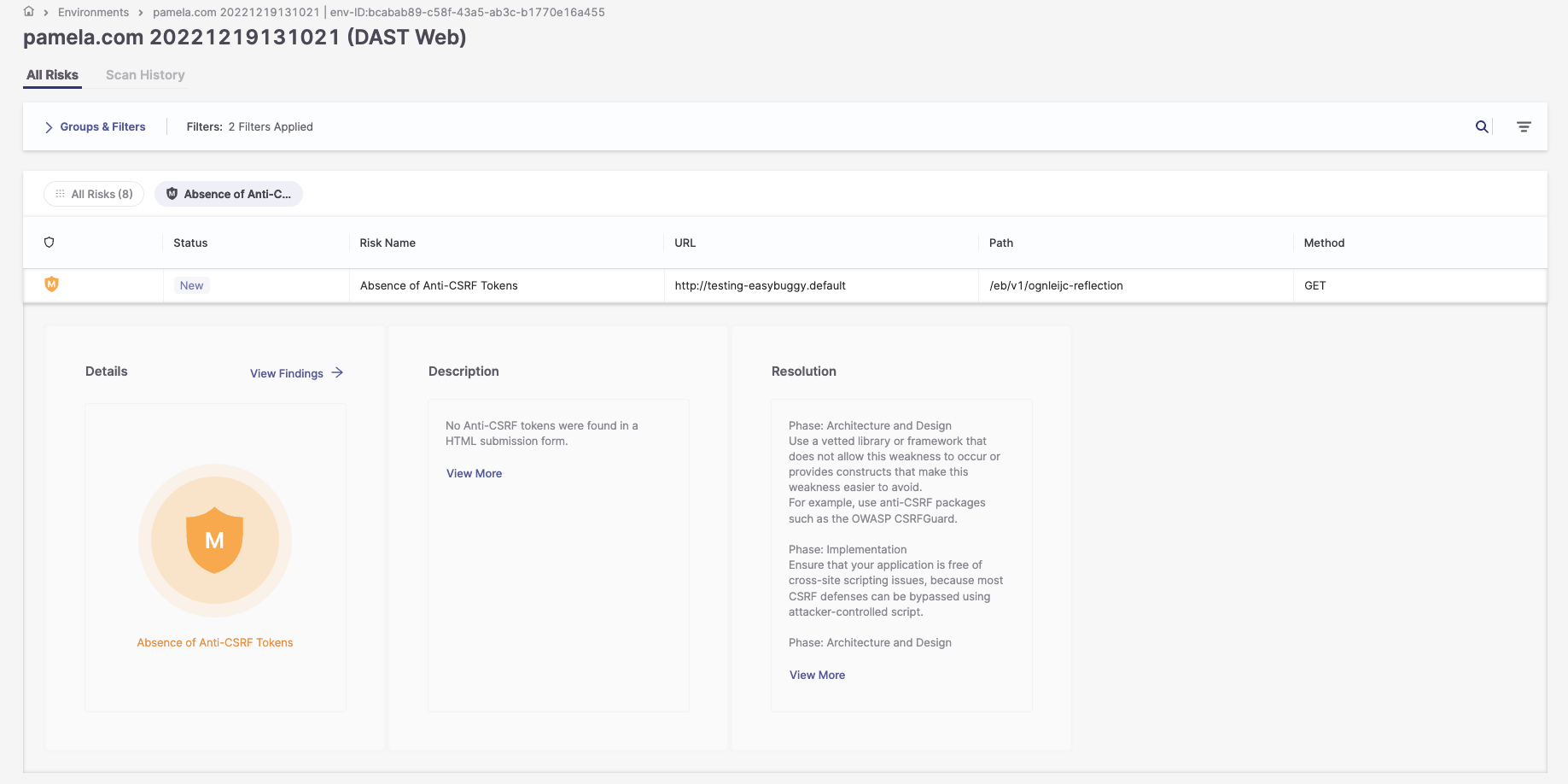
To access more information regarding the risks:
1. Click on the Severity button.
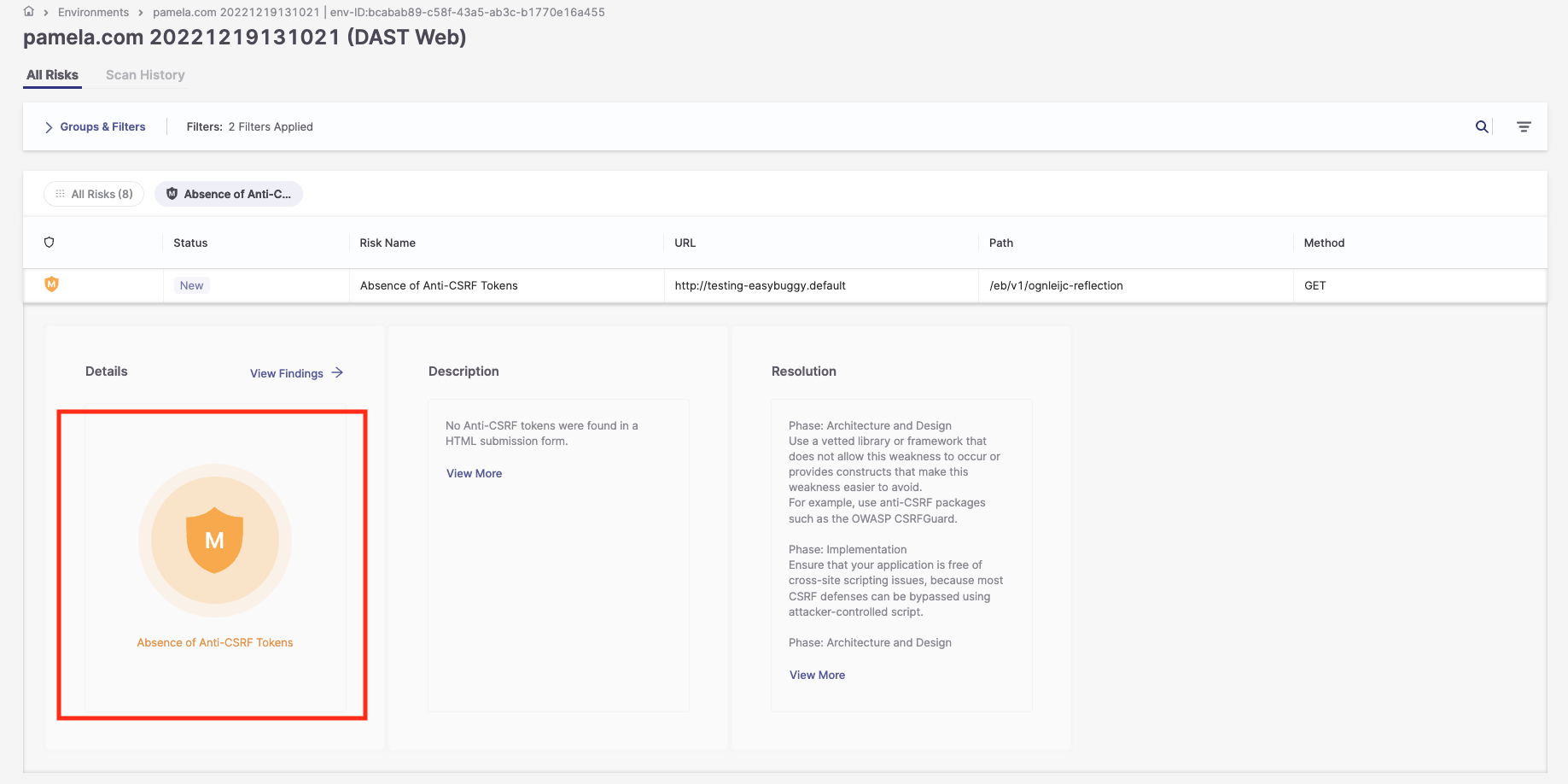
The following additional fields are displayed:
State
Risk level
Compliance
Confidence
Method
Param
URI
Evidence
Attack
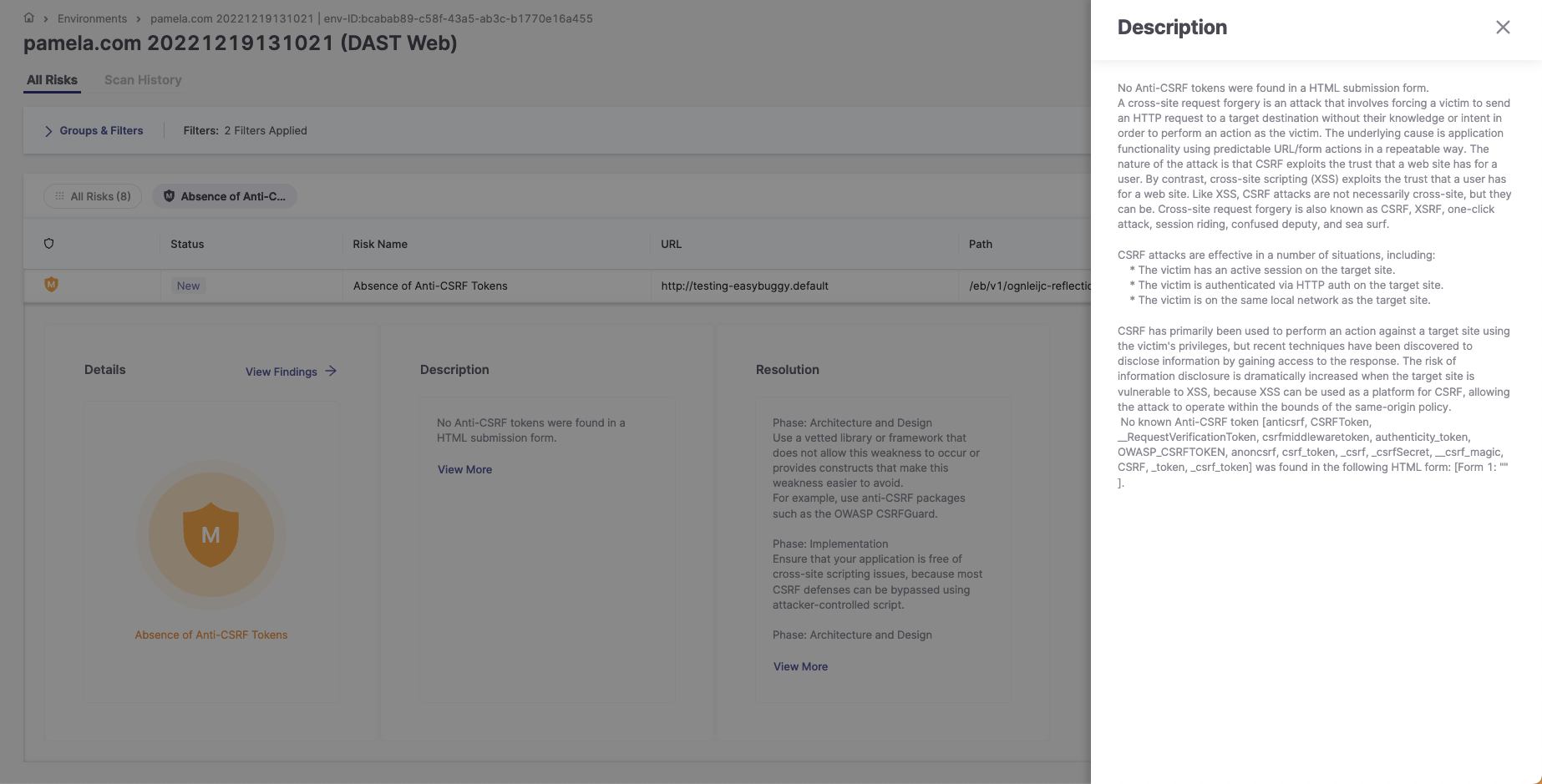
2. In the Description pane, click View More to display a full explanation of the risk.
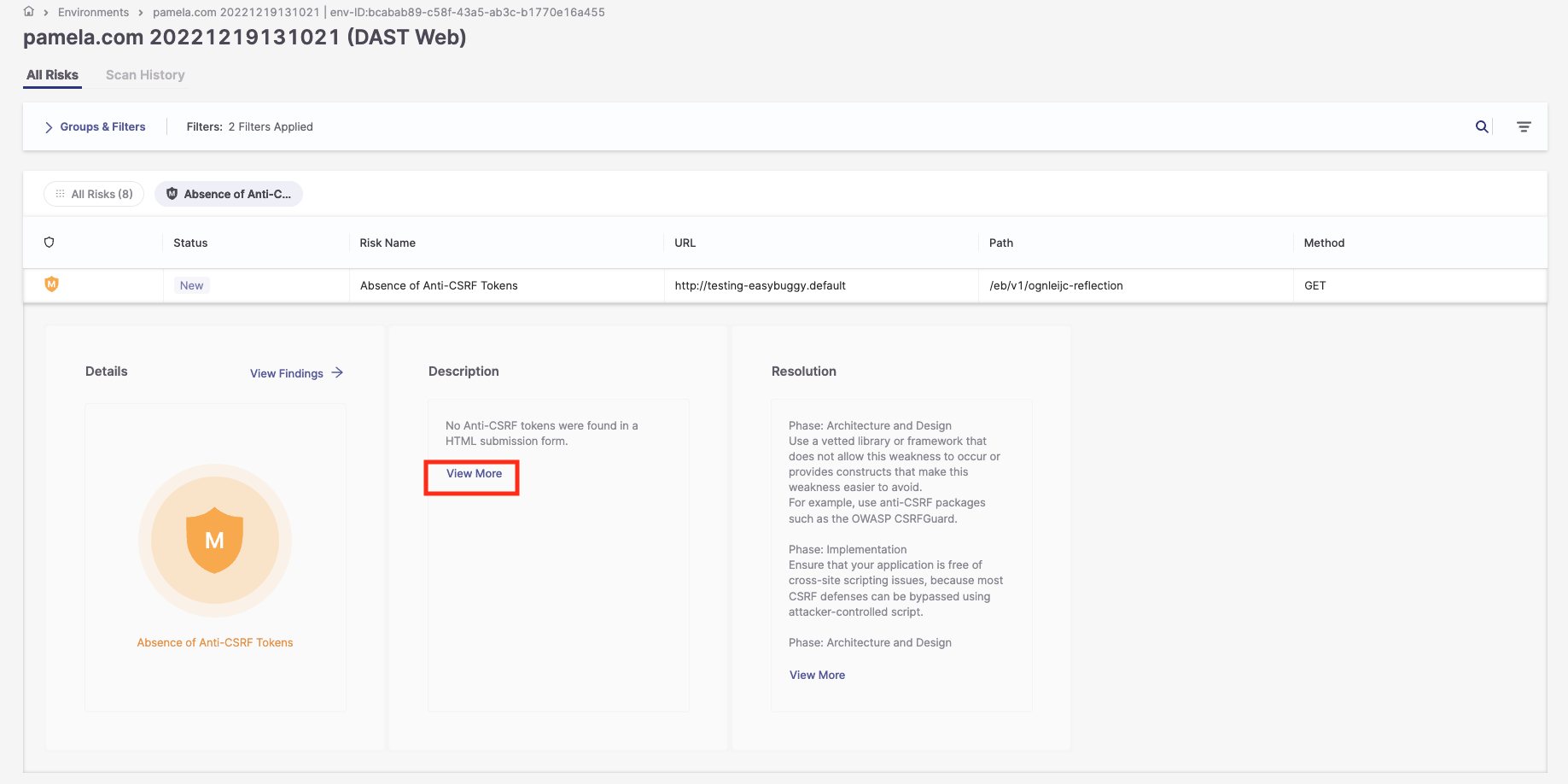
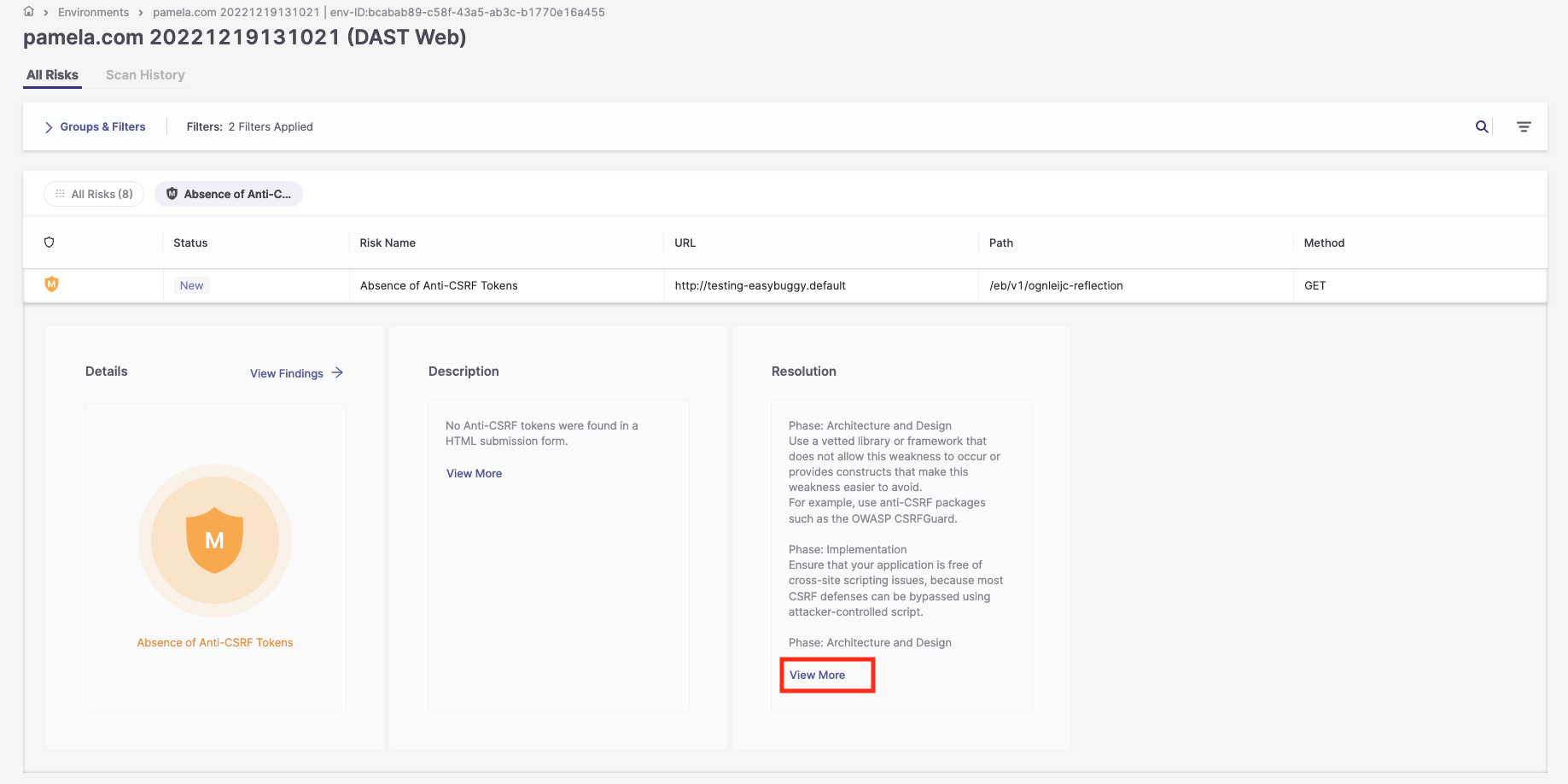
3. In the Resolution pane, click View More to display a full explanation of how to resolve the risk.
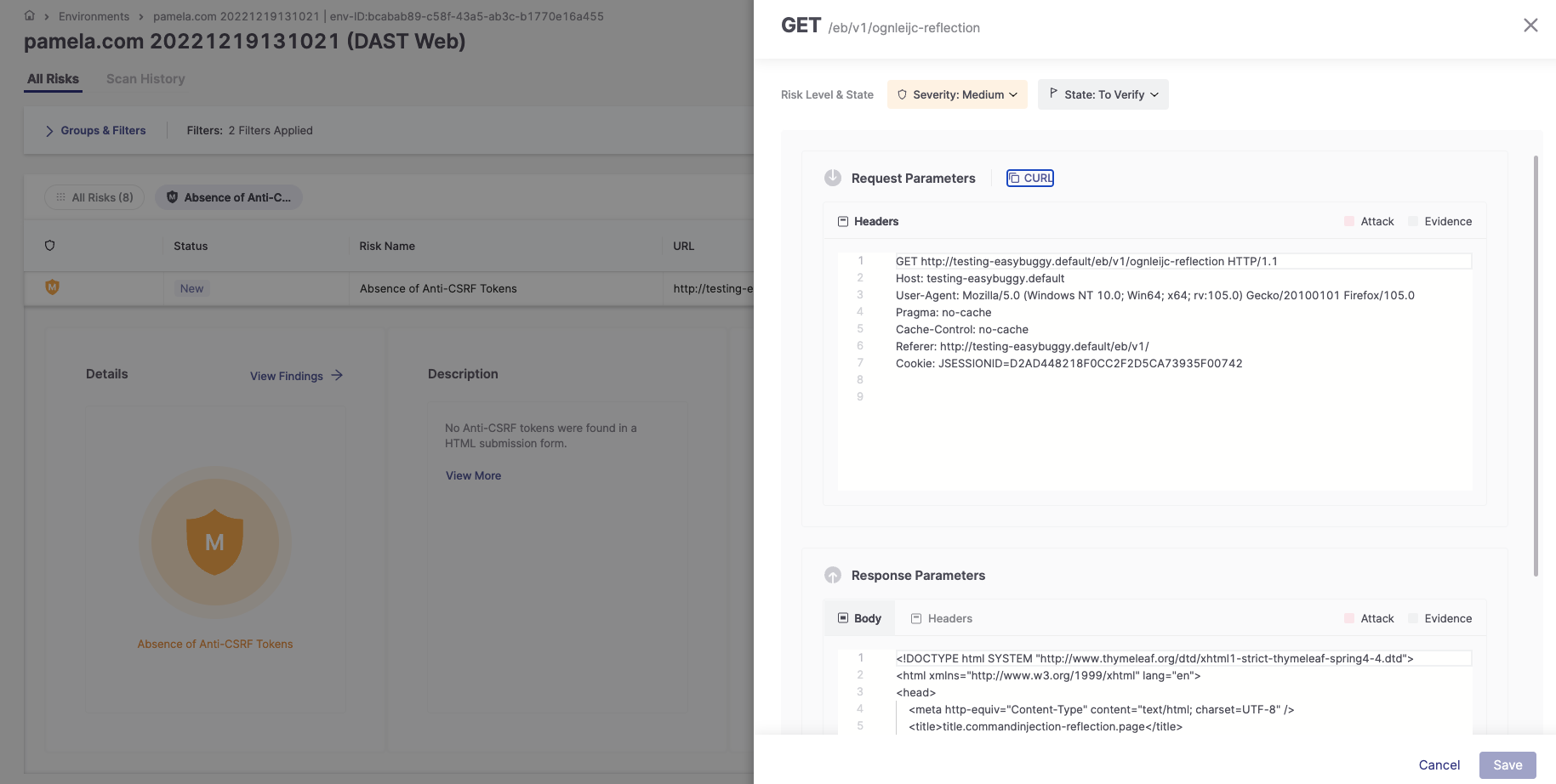
4. Click View Findings to open a side panel with the following information:
Risk Level
Risk State
Request Headers
Response Body and Headers
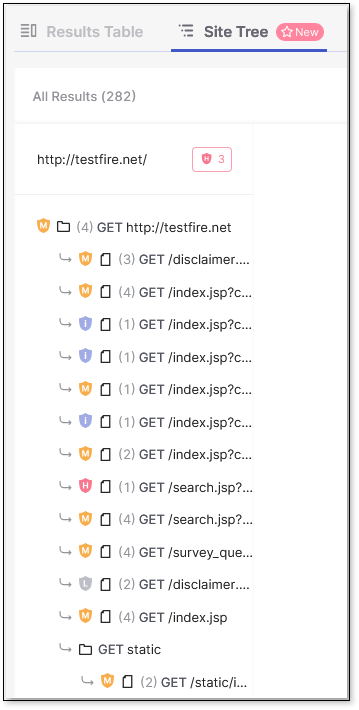
Site Tree View Tab
The Site Tree visually maps your application's structures and scanned paths. It helps you visualize the hierarchy of URLs and their scans, so you can see which parts of the web application were scanned and how they are organized. A new Site Tree is created for each successful scan and appears in the Site Tree tab, separate from the Results Table.
The Site Tree is displayed in a resizable panel, enabling you to adjust the view according to your preference or screen size. Any paths where vulnerabilities are detected are visually marked with severity indicators.
Clicking on a path in the Sites Tree reveals detailed information about that node.
Scan History
The Scan History tab provides access to the results of all successful scans. Similar to adjusting results on the Results Table, you can adjust the severity or status of results in Scan History, and any changes will automatically affect other related scans.
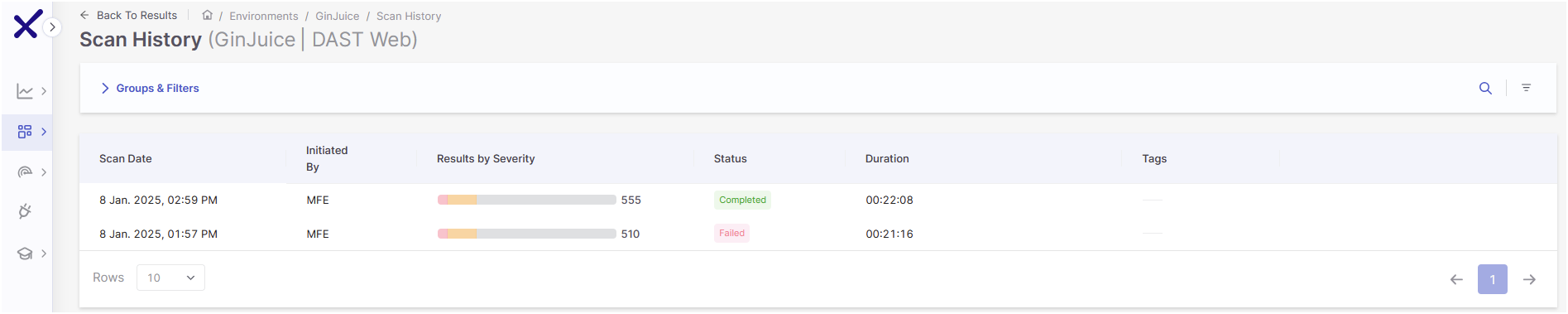 |
After completing a scan, the latest results are displayed in the Results Table, while previous results are moved to and can be viewed in the Scan History tab. No specific role is required to access scan history, and you can access it through the Environment by selecting View on a scan with results. This opens the environment's scan results page, where you can access Scan History via the top-right menu.
 |
There are three statuses for scans: Completed, Failed, and Partial Scans. Completed scans are successful scans, while Failed scans are those scans that failed to run. Partial scans are scans that have been completed but contain errors. Download the scan logs to see what went wrong in the scan by clicking  at the end of the result's row and then Download Scan Log
at the end of the result's row and then Download Scan Log