- Checkmarx Documentation
- Checkmarx One
- Checkmarx One CLI Tool
- Checkmarx One CLI Commands
- utils
utils
The utils command is used for performing various Checkmarx One utility functions.
Usage
./cx utils [command]
Help
- ---help, -h
Help for the health-check command.
Utility Commands
utils can be used with the following commands:
completion
The completion command is used for performing CLI command auto completion.
The auto completion supports 4 command line types: bash, zsh, fish, and powershell.
Notice
Auto completion is enabled only for the current session. Once the session is closed you need to configure it again.
Usage
./cx utils completion --shell [bash|zsh|fish|powershell]
Flags
- ---help, -h
Help for the health-check command.
- --shell, -s (Required)
The type of shell [bash/zsh/fish/powershell]
Examples
Bash Auto Completion
To configure auto completions for each session, execute the following:
# load and export a set of Environment Variables for the completion command: $ source <(./cx utils completion -s bash)
# Load completion for each Linux session: $ ./cx utils completion -s bash > /etc/bash_completion.d/cx
To configure auto completions for each session, execute the following:
# load and export a set of Environment Variables for the completion command: $ source <(./cx utils completion -s bash)
# Load completion for each MAC session: $ ./cx utils completion -s bash > /usr/local/etc/bash_completion.d/cx
zsh Auto Completion
To configure auto completions for each session, execute the following:
# Enable auto completion for the environment: $ echo "autoload -U compinit; compinit" >> ~/.zshrc
# To load auto completion for each session, execute once:
$ ./cx utils completion -s zsh > "${fpath[1]}/_cx"# start a new shell for this setup to take effect
fish Auto Completion
To configure auto completions for each session, execute the following:
# Configure auto completion: $ ./cx utils completion -s fish | source
# To load auto completion for each session, execute once: $ ./cx utils completion -s fish > ~/.config/fish/completions/cx.fish
PowerShell Auto Completion
# load and export a set of Environment Variables for the completion command: $ PS> .\cx.exe utils completion -s powershell | Out-String | Invoke-Expression
# To load auto completion for each session, execute: $ PS> .\cx.exe utils completion -s powershell > cx.ps1
# source this file from your PowerShell profile
env
The env command retrieves the configured environment variables.
Usage
./cx utils env [flags]
Flags
- ---help, -h
Help for the env command.
Examples
Using the env command
uaer@laptop:~/ast-cli$ ./cx utils env
Detected Environment Variables:
cx_proxy_auth_type:
cx_client_id:
cx_client_secret:
cx_apikey:
cx_branch:
cx_timeout:
cx_base_uri:
cx_tenant:
http_proxy:
sca_resolver:
cx_base_auth_uri:contributor-count
The contributor-count command enables users to count unique contributors from different SCM repositories, for the past 90 days.
Usage
./cx utils contributor-count [command]
Flags
- --help, -h
Help for the contributor-count command.
Global Flags
The contributor-count command does not support all global flags. The following flags are supported.
- --debug
Debug mode returns detailed logs, including the username of each of the contributors and the repos to which they contributed.
- --proxy-auth-type <string>
Proxy authentication type (basic or ntlm).
- --proxy-ntlm-domain <string>
Window domain when using NTLM proxy.
- --proxy <string>
Proxy server to send communication through.
- --timeout <string> (Default: 5 seconds)
Timeout for network activity.
github
The github command retrieves the number of unique contributors for the provided GitHub repositories or organizations. Contributors are found by visiting all repositories and comparing the author property of each commit. Bots are counted as contributors if their commits do not have “type” as “Bot” (dependabot is correctly excluded).
The user's email is used as the unique identifier for counting distinct users. Contributors who commit from accounts with different emails will be counted as distinct contributors.
Notice
This command returns a breakdown of unique contributors per repo as well as the total number of unique contributors. When a particular user contributes to several different repos, this is counted as a single contributor for the total count. Therefore, the total count will not necessarily be equal to the sum of the individual repos.
Usage
./cx utils contributor-count github [flags]
Flags
- --format <string> (Default: table)
The output format for the response. Possible values are
json,listortable(default).- --help, -h
Help for the github command.
- --orgs <strings>
List of organizations to scan for contributors. Comma separated list.
- --repos <strings>
List of repositories to scan for contributors. Comma separated list.
- --token <string>
GitHub Personal Access Token (PAT). Requires “Repo” scope and organization SSO authorization, if enforced by the organization.
- --url <string>
The API base URL. Default: https://api.github.com/
Examples
PS C:\Users\ast-cli> cx utils contributor-count github --orgs checkmarx --token <token> Name UniqueContributors ---- ------------------ ... Checkmarx/ast-cli 1 Checkmarx/kics 2 ... Total unique contributors N
PS C:\Users\ast-cli> cx utils contributor-count github --repos ast-cli,kics --orgs checkmarx --token <token> Name UniqueContributors ---- ------------------ Checkmarx/ast-cli 1 Checkmarx/kics 2 Total unique contributors 3
azure
The azure command retrieves the number of unique contributors for the provided Azure DevOps repositories, projects, and organizations.
The user's email is used as the unique identifier for counting distinct users. Contributors who commit from accounts with different emails will be counted as distinct contributors.
Notice
This command returns a breakdown of unique contributors per repo as well as the total number of unique contributors. When a particular user contributes to several different repos, this is counted as a single contributor for the total count. Therefore, the total count will not necessarily be equal to the sum of the individual repos.
Usage
./cx utils contributor-count azure [flags]
Flags
- --format <string> (Default: table)
The output for the response. Possible values are
json,listortable.- --help, -h
Help for the results command.
- --orgs strings <string>
List of organizations to scan for contributors.
Comma separated list.
- --projects <string>
List of projects to scan for contributors.
Comma separated list.
- --repos <string>
List of repositories to scan for contributors.
Comma separated list.
- --token <string>
Azure DevOps personal access token. Requires "Connected server" and "Code" scope.
- --url-azure <string> (Default: https://dev.azure.com/)
API base URL.
Examples
./cx utils contributor-count azure --orgs <orgs> --token <token>
user@laptop:~/ast-cli$ ./cx utils contributor-count azure --orgs Checkmarx --token 12345678910 Name UniqueContributors ---- ------------------ Checkmarx/public/ast-cli 2 Checkmarx/private/ast-java-wrapper 1 ... ... Total unique contributors 7 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
./cx utils contributor-count azure --orgs <orgs> --token <token> --debug
user@laptop:~/ast-cli$ ./cx utils contributor-count azure --orgs Checkmarx --token 12345678910 Name UniqueContributors ---- ------------------ Checkmarx/public/ast-cli 2 Checkmarx/private/ast-java-wrapper 1 ... ... Total unique contributors 7 Name UniqueContributorsUsername ---- -------------------------- Checkmarx/public/ast-cli User Checkmarx Checkmarx/private/ast-java-wrapper UserCheckmarx ... 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
./cx utils contributor-count azure --orgs <orgs> --projects <projects> --token <token>
user@laptop:~/ast-cli$ ./cx utils contributor-count azure --orgs Checkmarx --projects public --token 12345678910 Name UniqueContributors ---- ------------------ Checkmarx/public/ast-cli 2 ... ... Total unique contributors 5 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
./cx utils contributor-count azure --orgs <orgs> --projects <projects> --token <token> --debug
user@laptop:~/ast-cli$ ./cx utils contributor-count azure --orgs Checkmarx --projects public --token 12345678910 Name UniqueContributors ---- ------------------ Checkmarx/public/ast-cli 2 ... ... Total unique contributors 5 Name UniqueContributorsUsername ---- -------------------------- Checkmarx/public/ast-cli User Checkmarx ... 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
./cx utils contributor-count azure --orgs <orgs> --projects <projects> --repos <repos> --token <token>
user@laptop:~/ast-cli$ ./cx utils contributor-count azure --orgs Checkmarx --projects public --repos asa-cli --token 12345678910 Name UniqueContributors ---- ------------------ Checkmarx/public/ast-cli 2 Total unique contributors 2 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
./cx utils contributor-count azure --orgs <orgs> --projects <projects> --repos <repos> --token <token> --debug
user@laptop:~/ast-cli$ ./cx utils contributor-count azure --orgs Checkmarx --projects public --repos ast-cli --token 12345678910 Name UniqueContributors ---- ------------------ Checkmarx/public/ast-cli 2 Total unique contributors 2 Name UniqueContributorsUsername ---- -------------------------- Checkmarx/public/ast-cli User Checkmarx 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
gitlab
The gitlab command retrieves the number of unique contributors for the provided GitLab groups or projects.
Notice
This command returns a breakdown of unique contributors per repo as well as the total number of unique contributors. When a particular user contributes to several different repos, this is counted as a single contributor for the total count. Therefore, the total count will not necessarily be equal to the sum of the individual repos.
Usage
.\cx.exe utils contributor-count gitlab [flags]
Flags
- --format <string> (Default: table)
The output format for the response. Possible values are
json,listortable.- --groups <strings>
List of group names to scan for contributors.
Comma separated list for more than one names.
If a subgroup is being used, the full path of subgroup is required. Full path includes the names of the parent groups and can be copied from the gitlab urls when the group is opened in the browser.
- --help, -h
Help for the github command.
- --projects <strings>
List of project names to scan for contributors.
Project names should be full path/namespace.
Comma separated list for using more than one project names.
- --token <string>
GitLab OAuth token with at least 'read_api' and 'read_repository' permissions.
- --url-gitlab <string> (Default: https://gitlab.com)
API base URL.
Examples
C:\Users\ast-cli> .\cx.exe utils contributor-count gitlab --token <token> --groups Checkmarx-ts/cxlite Name UniqueContributors ---- ------------------ ... Checkmarx/CxLite/CxDemo 1 ... Total unique contributors 1
C:\Users\ast-cli>.\cx.exe utils contributor-count gitlab --token <token> --projects Checkmarx/CxLite/CxDemo Name UniqueContributors ---- ------------------ Checkmarx/CxLite/CxDemo 1 Total unique contributors 1
bitbucket
The bitbucket command retrieves the number of unique contributors for the provided Bitbucket repositories, projects and organizations.
Notice
This command returns a breakdown of unique contributors per repo as well as the total number of unique contributors. When a particular user contributes to several different repos, this is counted as a single contributor for the total count. Therefore, the total count will not necessarily be equal to the sum of the individual repos.
Usage
./cx utils contributor-count bitbucket [flags]
Flags
- --format <string> (Default: table)
The output format for the response. Possible values are
json,listortable.- --help, -h
Help for the Bitbucket command.
- --password <string>
App password for Bitbucket authentication. Requires read on "Workspace membership" and "Repositories" permissions.
- --repos <string>
List of repositories to scan for contributors.
A Comma separated list.
- --url-bitbucket <string> (Default: https://api.bitbucket.org/2.0/)
API base URL.
- --username <string>
Username for Bitbucket authentication.
- --workspaces <string>
List of workspaces to scan for contributors.
A Comma separated list.
Examples
./cx utils contributor-count bitbucket --workspaces <workspaces> --username <username> --password <password> --debug
user@laptop:~/ast-cli$ ./cx utils contributor-count bitbucket --workspaces Checkmarx --username cx --password 12345678910 Name UniqueContributors ---- ------------------ Checkmarx/ast-cli 2 Checkmarx/ast-java-wrapper 1 ... ... Total unique contributors 7 Name UniqueContributorsUsername ---- -------------------------- Checkmarx/ast-cli User Checkmarx Checkmarx/ast-java-wrapper UserCheckmarx ... 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
./cx utils contributor-count bitbucket --workspaces <workspaces> --repos <repos> --username <username> --password <password> --debug
user@laptop:~/ast-cli$ ./cx utils contributor-count bitbucket --orgs Checkmarx --repos ast-cli --username cx --password 12345678910 Name UniqueContributors ---- ------------------ Checkmarx/ast-cli 2 Total unique contributors 2 Name UniqueContributorsUsername ---- -------------------------- Checkmarx/ast-cli User Checkmarx 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
bitbucket-server
The bitbucket-server command retrieves the number of unique contributors for the provided Bitbucket Server repositories and projects.
Notice
This command returns a breakdown of unique contributors per repo as well as the total number of unique contributors. When a particular user contributes to several different repos, this is counted as a single contributor for the total count. Therefore, the total count will not necessarily be equal to the sum of the individual repos.
Usage
./cx utils contributor-count bitbucket-server [flags]
Flags
- --format <string> (Default: table)
The output format for the response. Possible values are
json,listortable.- --help, -h
Help for the
bitbucket-servercommand.- --projects <string> (Default: all)
Tip
Not required. However, when you submit
--repos, it is required to also submit--projects.List of projects to scan for contributors.
A comma separated list.
- --repos <string> (Default: all)
List of repositories to scan for contributors.
A comma separated list.
- --server-url <string> (Required)
The URL of your Bitbucket Server instance.
- --token <string> (Default: if no token is provided, then only public projects are searched)
The HTTP access token that you generated in Bitbucket. To learn how to genearte a token, see the section "Create HTTP access tokens" here.
Tip
On older versions of Bitbucket Server this is referred to as a "Personal access token".
For Permissions select, at a minimum:
Project read, and
Repository read.
Examples
./cx utils contributor-count bitbucket-server --server-url <server-url> --token <token>
user@laptop:~/ast-cli$ ./cx utils contributor-count bitbucket-server --server-url bitbucket.my.com --token MYTOKEN Name UniqueContributors ---- ------------------ CX/ast-cli 2 ... AS/my-project 1 ... ... Total unique contributors 7 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
With Debug
./cx utils contributor-count bitbucket-server --server-url <server-url> --token <token> --debug
user@laptop:~/ast-cli$ ./cx utils contributor-count bitbucket-server --server-url bitbucket.my.com --token MYTOKEN --debug Name UniqueContributors ---- ------------------ CX/ast-cli 2 ... AS/my-project 1 ... ... Total unique contributors 7 Name UniqueContributorsUsername ---- -------------------------- CX/ast-cli user - user.name@checkmarx.com ... AS/my-project user2 - user2.name@checkmarx.com ... 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
./cx utils contributor-count bitbucket-server --projects <projects> --server-url <server-url> --token <token>
user@laptop:~/ast-cli$ ./cx utils contributor-count bitbucket-server --projects CX --server-url bitbucket.my.com --token MYTOKEN Name UniqueContributors ---- ------------------ CX/ast-cli 2 CX/ast-java-wrapper 1 ... ... Total unique contributors 7 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
With Debug
./cx utils contributor-count bitbucket-server --projects <projects> --server-url <server-url> --token <token> --debug
user@laptop:~/ast-cli$ ./cx utils contributor-count bitbucket-server --projects CX --server-url bitbucket.my.com --token MYTOKEN --debug Name UniqueContributors ---- ------------------ CX/ast-cli 2 CX/ast-java-wrapper 1 ... ... Total unique contributors 7 Name UniqueContributorsUsername ---- -------------------------- CX/ast-cli user - user.name@checkmarx.com CX/ast-java-wrapper user2 - user2.name@checkmarx.com ... 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
./cx utils contributor-count bitbucket-server --projects <projects> --repos <repos> --server-url <server-url> --token <token>
user@laptop:~/ast-cli$ ./cx utils contributor-count bitbucket-server --projects CX --repos ast-cli --server-url bitbucket.my.com --token MYTOKEN Name UniqueContributors ---- ------------------ CX/ast-cli 2 Total unique contributors 2 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
With Debug
./cx utils contributor-count bitbucket-server --projects <projects> --repos <repos> --server-url <server-url> --token <token> --debug
user@laptop:~/ast-cli$ ./cx utils contributor-count bitbucket-server --projects CX --repos ast-cli --server-url bitbucket.my.com --token MYTOKEN --debug Name UniqueContributors ---- ------------------ CX/ast-cli 2 Total unique contributors 2 Name UniqueContributorsUsername ---- -------------------------- CX/ast-cli user - user.name@checkmarx.com 2022/03/18 10:30:46 Note: dependabot is not counted but other bots might be considered users.
learn-more
The learn-more command retrieves additional descriptions from the CLI for SAST vulnerabilities.
The command must be run with the attribute query-id, which can be retrieved from a scan’s results and passed to this command.
Usage
./cx utils learn-more --query-id <query-id> --format [json|table|list]
Flags
- --format (Default: list)
The output format for the response. Possible values are
json,listortable.- ---help, -h
Help for the learn-more command.
- --query-id (Required)
The SAST query-id for a vulnerability.
Examples
learn-more command
Default (without format flag)
./cx utils learn-more --query-id 5854466950125120303
QueryID : 5854466950125120303
QueryName : Open_Redirect
QueryDescriptionID : Stored_Open_Redirect
ResultDescription : The potentially tainted value provided by @SourceElement in @SourceFile at line @SourceLine is used as a desti
nation URL by @DestinationElement in @DestinationFile at line @DestinationLine, potentially allowing attackers to perform an open redirection.
Risk : An attacker could use social engineering to get a victim to click a link to the application, so that the user
will be immediately redirected to another site of the attacker's choice. An attacker can then craft a destination website to fool the v
ictim; for example - they may craft a phishing website with an identical looking UI as the previous website's login page, and with a si
milar looking URL, convincing the user to submit their access credentials in the attacker's website. Another example would be a phishing website with an identical UI as that of a popular payment service, convincing the user to submit their payment information.
Cause : The application redirects the user’s browser to a URL provided by a tainted input, without first ensuring that
URL leads to a trusted destination, and without warning users that they are being redirected outside of the current site. An attacker
could use social engineering to get a victim to click a link to the application with a parameter defining another site to which the app
lication will redirect the user’s browser. Since the user may not be aware of the redirection, they may be under the misconception that the website they are currently browsing can be trusted.
GeneralRecommendations :
1. Ideally, do not allow arbitrary URLs for redirection. Instead, create a mapping from user-provided parameter values to legitimate URLs.
2. If it is necessary to allow arbitrary URLs:
* For URLs inside the application site, first filter and encode the user-provided parameter, and then either:
* Create a white-list of allowed URLs inside the application
* Use variables as a relative URL as an absolute one, by prefixing it with the application site domain - this will ensure all redirection will occur inside the domain
* For URLs outside the application (if necessary), either:
* White-list redirection to allowed external domains by first filtering URLs with trusted prefixes. Prefixes must be tested u
p to the third slash \[/\] - `scheme://my.trusted.domain.com/,` to prevent evasion. For example, if the third slash \[/\] is not valida
ted and scheme://my.trusted.domain.com is trusted, the URL scheme://my.trusted.domain.com.evildomain.com would be valid under this filter, but the domain actually being browsed is evildomain.com, not domain.com.
* For fully dynamic open redirection, use an intermediate disclaimer page to provide users with a clear warning that they are leaving the site.
Samples : [{Java protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
String redirectUrl = request.getParameter("redirectUrl");
if (redirectUrl != null) {
response.sendRedirect(redirectUrl);
} else {
response.sendRedirect("/");
}
} Java Servlet Vulnerable to Open Redirection} {Java protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
String redirectUrl = request.getParameter("redirectUrl");
if (redirectUrl != null && redirectUrl.startsWith("https://www.trusteddomain.com/")) {
response.sendRedirect(redirectUrl);
} else {
response.sendRedirect("/");
}
} Whitelisting an Allowed External Domain, Preventing Open Redirection}]Json format
./cx utils learn-more --query-id 5854466950125120303 --format json
[{"queryId":"5854466950125120303","queryName":"Open_Redirect","queryDescriptionId":"Stored_Open_Redirect","resultDescription":"The pote
ntially tainted value provided by @SourceElement in @SourceFile at line @SourceLine is used as a destination URL by @DestinationElement
in @DestinationFile at line @DestinationLine, potentially allowing attackers to perform an open redirection.\n\n","risk":"An attacker
could use social engineering to get a victim to click a link to the application, so that the user will be immediately redirected to ano
ther site of the attacker's choice. An attacker can then craft a destination website to fool the victim; for example - they may craft a
phishing website with an identical looking UI as the previous website's login page, and with a similar looking URL, convincing the use
r to submit their access credentials in the attacker's website. Another example would be a phishing website with an identical UI as tha
t of a popular payment service, convincing the user to submit their payment information.\n\n","cause":"The application redirects the us
er’s browser to a URL provided by a tainted input, without first ensuring that URL leads to a trusted destination, and without warning
users that they are being redirected outside of the current site. An attacker could use social engineering to get a victim to click a l
ink to the application with a parameter defining another site to which the application will redirect the user’s browser. Since the user
may not be aware of the redirection, they may be under the misconception that the website they are currently browsing can be trusted.\
n\n","generalRecommendations":"\r\n1. Ideally, do not allow arbitrary URLs for redirection. Instead, create a mapping from user-provid
ed parameter values to legitimate URLs.\r\n2. If it is necessary to allow arbitrary URLs:\r\n * For URLs inside the application s
ite, first filter and encode the user-provided parameter, and then either:\r\n * Create a white-list of allowed URLs inside th
e application\r\n * Use variables as a relative URL as an absolute one, by prefixing it with the application site domain - thi
s will ensure all redirection will occur inside the domain\r\n * For URLs outside the application (if necessary), either:\r\n
* White-list redirection to allowed external domains by first filtering URLs with trusted prefixes. Prefixes must be tested up to
the third slash \\[/\\] - `scheme://my.trusted.domain.com/,` to prevent evasion. For example, if the third slash \\[/\\] is not validat
ed and scheme://my.trusted.domain.com is trusted, the URL scheme://my.trusted.domain.com.evildomain.com would be valid under this filte
r, but the domain actually being browsed is evildomain.com, not domain.com.\r\n * For fully dynamic open redirection, use an i
ntermediate disclaimer page to provide users with a clear warning that they are leaving the site.\r\n\n\n","samples":[{"progLanguage":"
Java","code":"protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {\n
String redirectUrl = request.getParameter(\"redirectUrl\");\n if (redirectUrl != null) {\n response.sendRedirect(redirectUr
l);\n } else {\n response.sendRedirect(\"/\");\n }\n}","title":"Java Servlet Vulnerable to Open Redirection"},{"progLang
uage":"Java","code":"protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOExceptio
n {\n String redirectUrl = request.getParameter(\"redirectUrl\");\n if (redirectUrl != null \u0026\u0026 redirectUrl.startsWith(\
"https://www.trusteddomain.com/\")) {\n response.sendRedirect(redirectUrl);\n } else {\n response.sendRedirect(\"/\");\n }\n}","title":"Whitelisting an Allowed External Domain, Preventing Open Redirection"}]}]remediation
The remediation command enables you to automatically remediate vulnerabilities for results that came from a specific Checkmarx scanner.
Usage
./cx utils remediation [command]
Flags
- --help
Help for the utils remediation.
kics
The kics command enables you to automatically remediate kics vulnerabilities.
Caution
This feature is currently supported only for Terraform projects.
Usage
./cx utils remediation kics [flags]
Flags
- --engine <string> (Default: docker)
Name in the $PATH for the container engine to run kics. Example: podman
- --kics-files <string> (Required)
Absolute path to the folder that contains the file(s) to be remediated.
- --results-file <string> (Required)
Path to the kics scan results file. This is used to identify and remediate the kics vulnerabilities.
- --similarity-ids <string>,<string> (Default: Remediates all vulnerabilities)
Comma separated list of the similarity ids for the vulnerability instances that you would like to remediate.
Examples
Remediating all vulnerabilities
./cx utils remediation kics --results-file <PATH-TO-RESULTS> --kics-files <ABSOLUTE-PATH-TO-FILES>
user@laptop:/AST$ ./cx utils remediation kics --results-file "./results.json" --kics-files "/home/terraform_examples/"
{"available_remediation_count":3,"applied_remediation_count":3}Remediating a specific vulnerability
./cx utils remediation kics --results-file <PATH-TO-RESULTS> --kics-files <ABSOLUTE-PATH-TO-FILES> --similarity-ids <SIMILARITY-ID-LIST>
user@laptop:/AST$ ./cx utils remediation kics --results-file "./results.json" --kics-files "/home/terraform_examples/" --similarity-ids b42a19486a8e18324a9b2c06147b1c49feb3ba39a0e4aeafec5665e60f98d047,40d17ca090c7f7e49e9a8005113dd1b22aac3fcf93add6a302baddfaf449fc03
{"available_remediation_count":3,"applied_remediation_count":1}Remediating using a specific engine
./cx utils remediation kics --results-file <PATH-TO-RESULTS> --kics-files <ABSOLUTE-PATH-TO-FILES> --engine <ENGINE-NAME>
user@laptop:/AST$ ./cx utils remediation kics --results-file "./results.json" --kics-files "/home/terraform_examples/" --engine podman
{"available_remediation_count":3,"applied_remediation_count":3}sca
The sca command is used to automatically remediate sca vulnerabilities.
Usage
./cx utils remediation sca [flags]
Warning
Currently only npm dependency files (package.json) are supported for this functionality.
Flags
- --package-files <string>
Path to input package files to remediate the package version.
- --package <string>
Name of the package to be replaced.
- --package-version <string>
Version of the package to be replaced.
Examples
Remediating a specific package
././cx utils remediation sca --package-files <PACKAGE-FILE-PATHS> --package <PACKAGE-NAME> --package-version <PACKAGE-VERSION>
user@laptop:/AST$ ./cx utils remediation sca --package-files /home/package.json ,/home/src/package.json --package copyfiles --package-version 1.2.1
If you attempt to remediate a package that doesn't exist in your project, you will receive the following response:
Package copyfile not found
If you attempt to remediate a package of an unsupported type, you will receive the following response:
Unsupported package manager file
pr
The pr command decorates pull requests with results from Checkmarx One scans that were triggered by that pull request. The pull request comments show a list of new vulnerabilities that were introduced by the code changes as well a list of vulnerabilities that were fixed by the code changes. This feature is available for all supported SCMs, github, gitlab, azure and bitbucket (both cloud-hosted and self-hosted repos).
Notice
For secured code repository environments, pr decorations can be sent via CxLink using the environment variable CX_LINK_SERVER_HOST.
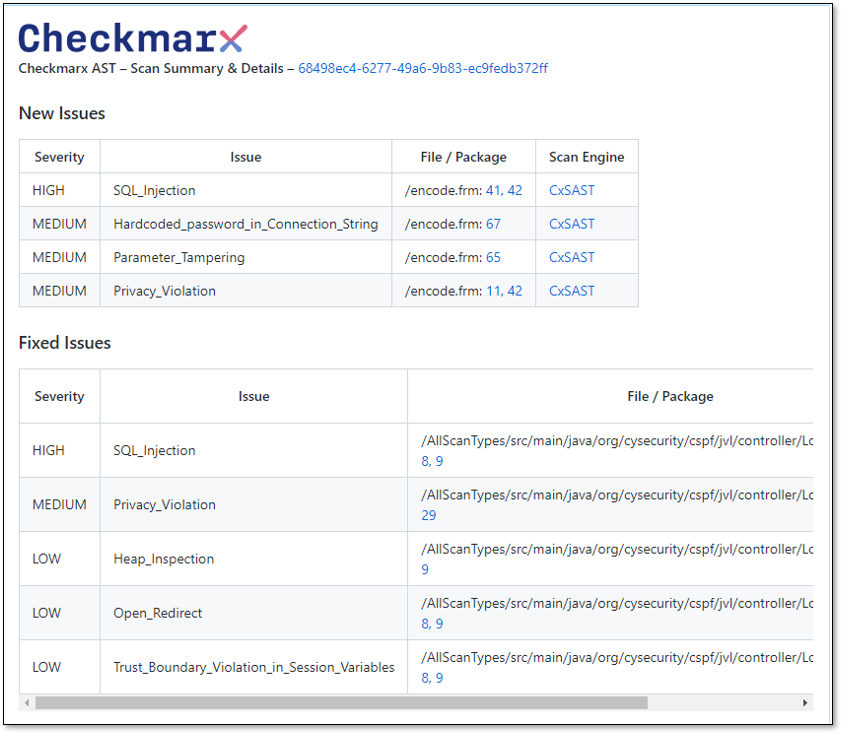
Usage
./cx utils pr [command]
github
The pr github command decorates pull requests in GitHub with results from Checkmarx One scans that were triggered by that pull request. The command must be submitted with a series of required attributes that specify the relevant repo and PR and provide the authentication credentials.
Usage
./cx utils pr github --scan-id <scan-id> --token <PAT> --namespace <organization> --repo-name <repository> --pr-number <pr number>
Flags
- --code-repository-url (Required only for self-hosted)
The URL of the self-hosted instance.
- --namespace (Required)
SCM namespace for the repository.
- --pr-number (Required)
The pull request number for decoration PR.
- --repo-name (Required)
SCM repository name.
- --scan-id (Required)
The scan ID of the Checkmarx One scan that was triggered by this PR. This can be extracted from the scan result that is obtained after the pull request is scanned.
- --token (Required)
The GitHub OAuth token used for creating the decoration.
Examples
pr github command
./cx.exe utils pr github --scan-id b8e043bc-4c72-4638-ac54-7ac1b40d1234 --namespace jay-nanduri --repo-name testGHAction --pr-number 1 --token <secret-token> 2022/08/31 12:31:43 PR comment created successfully.
gitlab
The pr gitlab command decorates pull requests in GitLab with results from Checkmarx One scans that were triggered by that pull request. The command must be submitted with a series of required attributes that specify the relevant repo and PR and provide the authentication credentials.
Usage
./cx utils pr gitlab --gitlab-project-id <project-id> --mr-iid <mr-id> --namespace <organization> --repo-name <repository> --scan-id <scan-id> --token <OAuth-token>
Flags
- --code-repository-url (Required only for self-hosted)
The URL of the self-hosted instance.
- --gitlab-project-id (Required)
The ID of the project in GitLab.
- --mr-iid (Required)
The internal GitLab ID for the merge request.
- --namespace (Required)
SCM organization name.
- --repo-name (Required)
SCM repository name.
- --scan-id (Required)
The scan ID of the fCheckmarx One scan that was triggered by this PR. This can be extracted from the scan result that is obtained after the pull request is scanned.
- --token (Required)
The GitLab OAuth token used for creating the decoration.
Examples
pr gitlab command
./cx.exe utils pr gitlab --gitlab-project-id 40227565 --mr-iid 19 --namespace tiagobcx --repo-name testProject --scan-id efc148f9-521d-4d60-8540-a36e98c2dd27 --token TOKEN 2023/11/15 09:30:00 gitlab PR comment created successfully.
azure
The pr azure command decorates pull requests in Azure DevOps with results from Checkmarx One scans that were triggered by that pull request. The command must be submitted with a series of required attributes that specify the relevant repo and PR and provide the authentication credentials.
Usage
./cx utils pr azure --scan-id <scan-id> --token <AAD> --namespace <organization> --project <project-name or project id> --pr-number <pr number> --code-repository-url <code-repository-url>
Flags
- --code-repository-url (Required only for self-hosted)
The URL of the self-hosted instance.
- --code-repository-username (Optional)
The username for the repo. This flag can only be used together with
--code-repository-url.- --namespace (Required)
SCM namespace for the organization.
- --pr-number (Required)
The pull request number for decoration PR.
- --project (Required)
The ID or name of the project in Azure.
- --scan-id (Required)
The scan ID of the Checkmarx One scan that was triggered by this PR. This can be extracted from the scan result that is obtained after the pull request is scanned.
- --token (Required)
The Azure token used for creating the decoration.
Examples
pr azure command
./cx.exe utils pr azure --scan-id 91ff85b6-e067-45bd-83f2-c77b895651ed --namespace DefaultCollection --project DemoProject --pr-number 20 --code-repository-url http://ec2-54-160-203-63.compute-1.amazonaws.com/%22 --token TOKEN
bitbucket
The pr bitbucket command decorates pull requests in Bitbucket with results from Checkmarx One scans that were triggered by that pull request. The command must be submitted with a series of required attributes that specify the relevant repo and PR and provide the authentication credentials.
Usage
Cloud-hosted
./cx utils pr bitbucket --scan-id <scan-id> --token <PAT> --namespace <username> --repo-name <repository-slug> --pr-id <pr number>
Self-hosted
./cx utils pr bitbucket --scan-id <scan-id> --token <PAT> --code-repository-url <bitbucket-server-url> --project-key <project-key> --repo-name <repository-slug> --pr-id <pr number>
Flags
- --code-repository-url (Required only for self-hosted)
The URL of the self-hosted instance.
- --namespace (Required only for cloud-hosted)
Bitbucket namespace for the organization.
- --pr-id (Required)
The pull request ID for decoration PR.
- --project-key (Required only for self-hosted)
The key of the Bitbucket project containing the repository.
- --repo-name (Required)
Bitbucket repository name.
- --scan-id (Required)
The scan ID of the Checkmarx One scan that was triggered by this PR. This can be extracted from the scan result that is obtained after the pull request is scanned.
- --token (Required)
Your Bitbucket personal access token (PAT).
Examples
pr bitbucket command
/cx.exe utils pr bitbucket --scan-id 00f383f6-c618-4973-a576-938a64cee4b5 --token TOKEN --namespace elchananaarbiv --repo-name decoration1 --pr-id 20 --token TOKEN
tenant
The tenant command enables users to retrieve info about the global settings that apply to their tenant account (i.e., the info shown on the Account Settings screen in the web portal). For more information about settings, see Global Account Settings.
Usage
./cx utils tenant [flags]
Flags
- --format (Default: list)
The output format for the response. Possible values are
json,listortable.- ---help, -h
Help for the
tenantcommand.
Examples
Sample Response
C:\ast-cli_2.0.53_windows_x64>cx utils tenant Key : scan.config.sca.filter Value : Key : scan.config.sast.languageMode Value : Key : scan.handler.git.repository Value : Key : scan.config.kics.platforms Value : Key : scan.config.sast.filter Value : *.java Key : scan.handler.git.branch Value : Key : scan.config.sca.ExploitablePath Value : Key : scan.config.sast.defaultConfigId Value : Key : scan.config.plugins.aiGuidedRemediation Value : Key : scan.handler.git.token Value : Key : scan.config.plugins.ideScans Value : true Key : scan.config.apisec.swaggerFilter Value : Key : scan.config.kics.filter Value : Key : scan.config.sast.incremental Value : Key : scan.config.sast.engineVerbose Value : Key : scan.handler.git.sshKey Value : Key : scan.config.sast.presetName Value : Key : scan.config.sca.LastSastScanTime Value :user@laptop:~/ast-cli$ ./cx utils tenant Key : scan.config.sast.defaultConfigId Value : Key : scan.config.kics.filter Value : Key : scan.config.sast.presetName Value : ASA Premium Key : scan.handler.git.token Value : Key : scan.config.sca.LastSastScanTime Value : Key : scan.config.sast.filter Value : Key : scan.handler.git.sshKey Value : Key : scan.config.sca.filter Value : Key : scan.config.sca.ExploitablePath Value : Key : scan.handler.git.repository Value : Key : scan.config.sast.engineVerbose Value : Key : scan.handler.git.branch Value : Key : scan.config.kics.platforms Value : Key : scan.config.sast.languageMode Value : Key : scan.config.sast.incremental Value : Key : scan.config.plugins.ideScans Value :
mask
The mask command enables users to return the secrets identified in an IaC file and show how they will be masked when the file is sent to ChatGPT using the chat command.
Usage
./cx utils mask [flags]
Flags
- ---help, -h
Help for the
maskcommand.- --reult-file (Required)
Specify the file path to the IaC file for which you would like to identify the secrets.
Examples
PS C:\_repos\ast-cli> .\bin\cx.exe utils mask --result-file .\Dockerfile
{"maskedSecrets":[{"masked":"PASSWORD=\u003cmasked\u003e","secret":"PASSWORD=test","line":6}],"maskedFile":"FROM alpine:3.18.2\n\nRUN apk add --no-cache bash\nRUN adduser --system --disabled-password cxuser\nUSER cxuser\n\nPASSWORD=\u003cmasked\u003e\n\nCOPY cx /app/bin/cx\n\nENTRYPOINT [\"/app/bin/cx\"]\n"}
import
The import command is used to import vulnerability results that adhere to SARIF version 2.1.0 format from third-party security tools and services (i.e. the BYOR feature). These imported results are integrated into the Application Risk Management feature, providing organizations with a unified view of their application risk profile and enabling them to make informed decisions to secure their end-to-end application lifecycle.
The command is submitted with the --project-name attribute specifying the name of the Checkmarx One project that these results will be associated with. It is also submitted with the --import-file-path argument specifying the path to the import file.
Usage
./cx utils import --project-name "<project name>" --import-file-path <file path>
Flags
- ---help, -h
Help for the import command.
- --import-file-path ()
The path to the file with the sarif file. This can be a single SARIF file or a zip archive containing several SARIF files.
Make sure that the file conforms to the guidelines described in SARIF File - Specificationst and SARIF File - Limitations.
- --project-name ()
The name of the Checkmarx One Project with which the results will be associated. This must be a Project that has already been created in Checkmarx One. It can be a dedicated Project created for the import or it can be a Project for which Checmarx One scans are run. In order to be able to access the imported results, the Project must be associated with a Checkmarx One Application.
Examples
./cx utils import --project-name "importDemo" --import-file-path .