Adding a New SAML Identity Provider in Access Control
Once the SAML Service Provider application has been created, and you have added users to the application, you can now add a new SAML Identity Provider in Access Control.
Notice
The information provided in the Identity Provider Setup Instructions page at the end of Creating a SAML Service Provider Application for OKTA is used to add a new SAML Identity Provider in Access Control.
To add a new SAML Identity Provider in Access Control:
In the Access Control portal, navigate to the SAML Identity Provider settings (Access Control > Settings > SAML Settings > Identity Provider).
Click Add Identity Provider. The Identity Provider definition page is displayed.
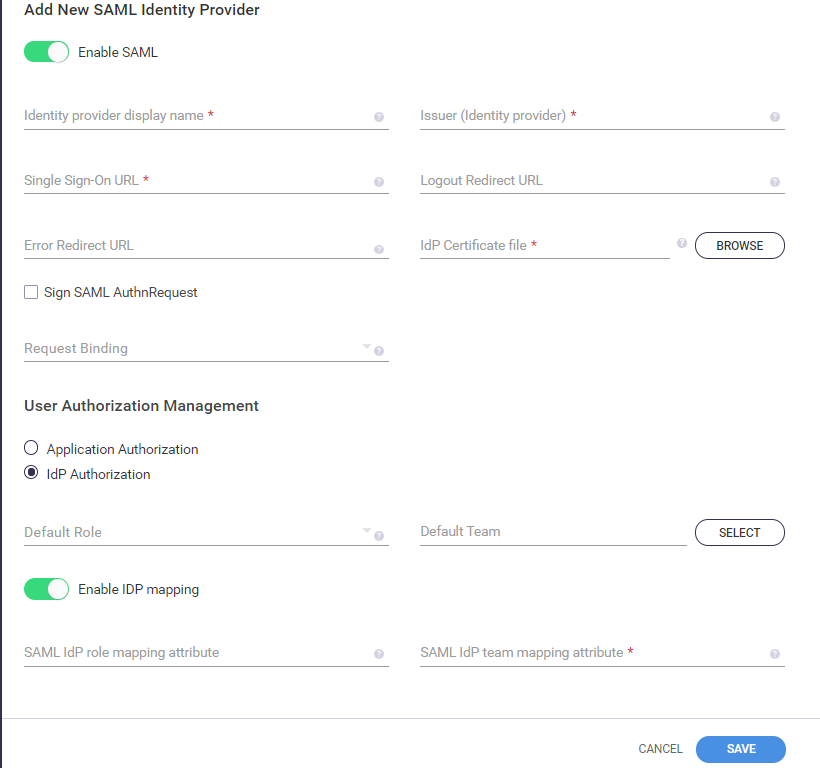
Enter the relevant information in the respective fields as outlined in the table. The information on the parameters are provided on the Identity Provider Setup Instructions page.
Once completed, click <Save> to save the changes.
Field | Description |
|---|---|
Enable SAML | Toggle to enable/disable SAML |
Identity provider display name | Enter the display name of the SAML Identity Provider Server. Example: CxAccessControl |
Issuer (identity provider) | The unique identifier of the Identity Provider Server, which is usually contained in the URL of the Identity Provider. This parameter is provided by the Identity Provider Setup information under ‘Identity Provider Issuer’. Example: https://srvl.idpname.com/mypageUnlink |
Single Sign-On URL | The Identity Provider Server login location to where SAML requests will be sent. This parameter is provided by the Identity Provider Setup information under ‘Identity Provider Single Sign-On URL’. Example: https://srvl.idpname.com/app/checkmarxdev/sso/saml |
Logout Redirect URL | The location to where logout instances will be redirected. Example: https://srvl.idpname.com/apps |
Error Redirect URL | The location to where error instances will be redirected. |
IdP Certificate File | This is the public key (X.509 certificate) and is provided by the Identity Provider Setup instructions under ‘Download Certificate’ The certificate will be used to validate the SAML assertion from the Identity Provider. |
Browse | Browse for Identity Provider certificate file location and navigate to the Identity Provider certificate file (.cert) that was downloaded from the Identity Provider Setup instructions. |
Sign SAML AuthnRequest | Select to sign the SAML AuthnRequest NoticeAfter upgrading SAST 9.0, make sure to modify the link for the Sign-On URL for the SAML server from http{s}://{server}:{port}/CxRestAPI/auth/samlAcs to http{s}://{server}:{port}/CxRestAPI/auth/identity/samlAcs. Otherwise the access link to the SAML server is broken as the login page of the SAML server cannot be reached. |
Request Binding | Click the Request Binding dropdown arrow and select the SAML binding protocol to use when sending the request: HTTP-Redirect or HTTP-Post |
User Authorization Management | Presents two options to select from – if the user authorization teams and roles will be controlled by the SAML Identity Provider, or by the Access Control Application.
NoticeThe teams and roles assigned per user in the SAML Identity Provider must exist in Access Control prior to the assignment, otherwise the user won’t be assigned those teams/roles, and the user won't be able to log in to Checkmarx products. |
Default Role | Select the default role from the dropdown list to be assigned to newly created SAML-based users. |
Default Team |
|
Enable IDP Mapping | You can enable this setting tomap SAML IDP team and/or role attributes with the attribute listed in the identity provider. |
SAML IdP role mapping attribute | This is not a mandatory field. This is used to map the role attribute or field with the configured attribute of the identity provider. We can use the Access Control Swagger API ' /SamlIdentityProviders/{samlProviderId}/RoleMappings'API to map multiple Access Control Roles with the values of the role attribute that is passed during logon from the identity provider. To understand how to configure multiple role attributes, refer to the example below, involving team attributes. |
SAML IdP team mapping attribute | This is a mandatory field. It is used to map the team attribute or field with the configured attribute of the identity provider. We can use the Access Control Swagger API ' /SamlIdentityProviders/{id}/TeamMappings' to map multiple Access Control Teams with the values of the team attribute that is passed during logon from the identity provider. For example: We can use the API "/SamlIdentityProviders/{id}/TeamMappings" in the following manner, to configure 'AC_TEAM_ONE' and 'AC_TEAM_TWO', with the values of the team attribute ( 'IT' and 'Sales') passed during logon: [ { "teamFullPath": "/CxServer/CompanyOne/AC_TEAM_ONE", "samlAttributeValue": "IT" }, { "teamFullPath": "/CxServer/CompanyOne/AC_TEAM_TWO", "samlAttributeValue": "Sales" }, { "teamFullPath": "/CxServer/CompanyTwo/AC_Dev_Team", "samlAttributeValue": "IT" } ] |