Getting to Know the CxOSA Viewer
Once you have logged into the CxSAST application, the CxSAST web interface is displayed. To access the CxOSA Viewer, select a project from the Consolidated Project State screen, click the Actions button and select Open CxOSA Viewer from the drop-down. The CxOSA web interface includes navigation icons for each of the relevant modules:
 | Project State – Provides access to the consolidated project state. For more information about this subject, see Consolidated Project State for CxOSA. | |
|---|---|---|
 | OSA Settings – Provides access to CxOSA scan settings. For more information about this subject, see OSA Settings. | |
| Scan History – Provides access to the CxOSA scan history. For more information about this subject, see Scan History, below. | |
 | Management and Orchestration – Provides access to Management and Orchestration. For more information about this subject, see Management and Orchestration. |
CxOSA Project View
The CxOSA Project view displays the unique project name (top left), the scan type and the date and time the displayed scan started and ended (top right).
An open Source Analysis report can be viewed by clicking on the Open Report  icon (top right). For more information about this subject, see Generating a CxOSA Scan Results Report.
icon (top right). For more information about this subject, see Generating a CxOSA Scan Results Report.
You can edit the current project by clicking on the Edit Project  icon (top right). For more information about this subject, see Creating and Configuring CxOSA Projects.
icon (top right). For more information about this subject, see Creating and Configuring CxOSA Projects.
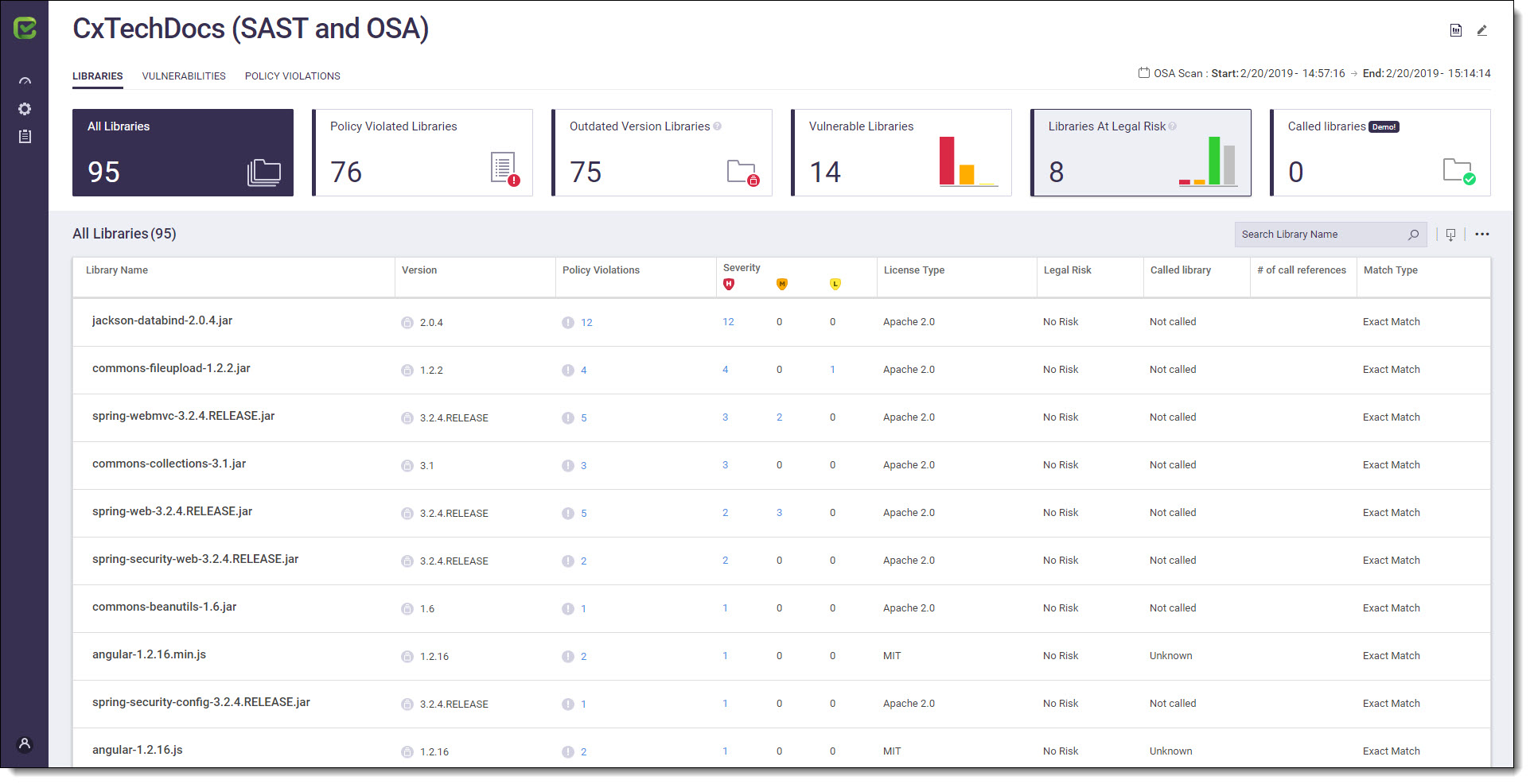
The Project View consists of the following information tabs: Libraries, Vulnerabilities and Policy Violations. Clicking on a tab displays the relevant view.
For more information about these subjects, refer to Libraries View, Vulnerabilities View, and Policy Violations View.
Scan History View
The Scan History view allows the user to review results of past CxOSA scans (rather then being able to review only the results from the last scan). It helps the user to monitor the current situation and trends, providing a better perspective of the cadence of their security work. To display the Scan History view, click the Scan History navigation icon. The CxOSA Scan History view is displayed.
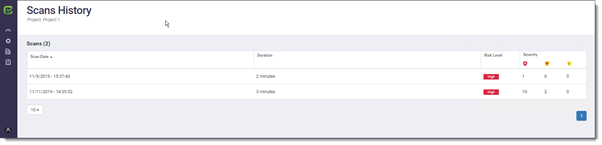 |
The Scans History View consists of the following information columns: Scan Date, Duration, Risk Level and Severity. Clicking on a Scan Date column or Severity sub-columns sorts the information accordingly.
Open Source Analysis Report
The Open Source Analysis report can be viewed by clicking on the Open Report  icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
Libraries View
The Libraries view allows you to explore all the project's libraries. The Libraries list provides a list of all those libraries associated with the project. You can filter libraries in the Libraries list by All Libraries, Policy Violated Libraries, Outdated Version Libraries, Vulnerable Libraries, Libraries At Legal Risk
and Called Librariesby clicking on the relevant Dashboard Filter.
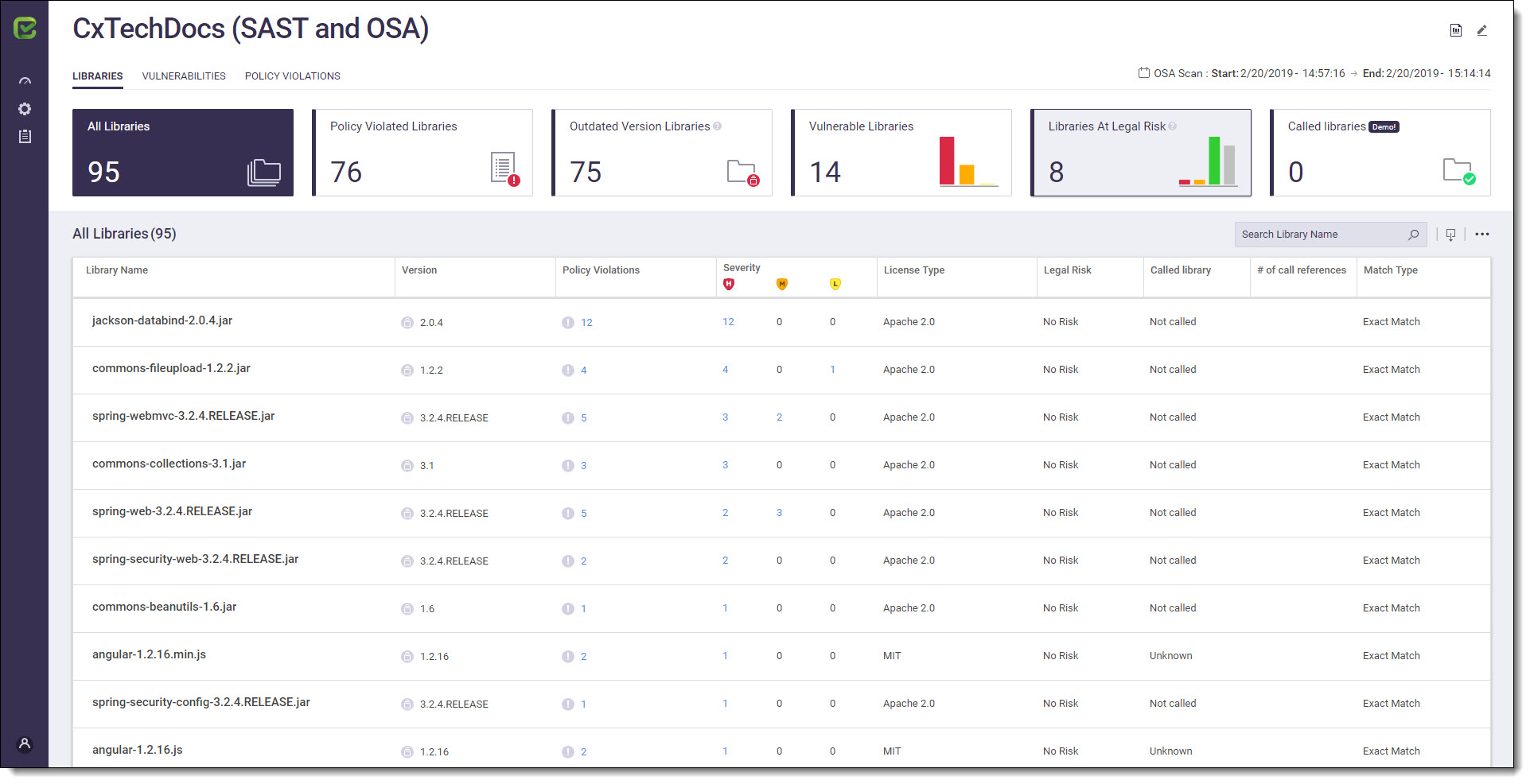 |
The Libraries List includes the following project libraries information:
Item | Description |
|---|---|
Library Name | Name of the library. Clicking on the library link displays additional library status information. For more information about this subject, see Library Status, below. |
| |
| |
You can search for a specific library using the  tool. | |
Version | This represents the library version being used. The |
Policy Violations | This represents the number of policy rule violated libraries. The |
Severity | Distribution of the vulnerable libraries by severity. |
 High – Vulnerable libraries stated with a high severity. | |
| |
| |
Clicking on a severity link displays the vulnerabilities associated with this library. For more information about this subject, see Vulnerabilities View. | |
License Type | This represents the license type associated to the library. The |
Legal Risk | This represents the possible legal risk level with regards to Copyright, Copyleft, Patent and Royalty, Linking and OSD Compliance. Possible risk states are high, medium, low or no risk. Additional information about legal risk is provided when drilling down to a specific library. |
Called Library | View the status (Called, Not Called or Unknown) |
# of call references | Number of aggregated library references detected in the source code. Hover over the number with the mouse to explore library call references. |
Match Type | Libraries that were not found using the SHA-1 Hash, will be matched by the provided filename. Possible values are:
|
Library Status
Clicking on the library link in the Project Libraries list displays additional library status information.
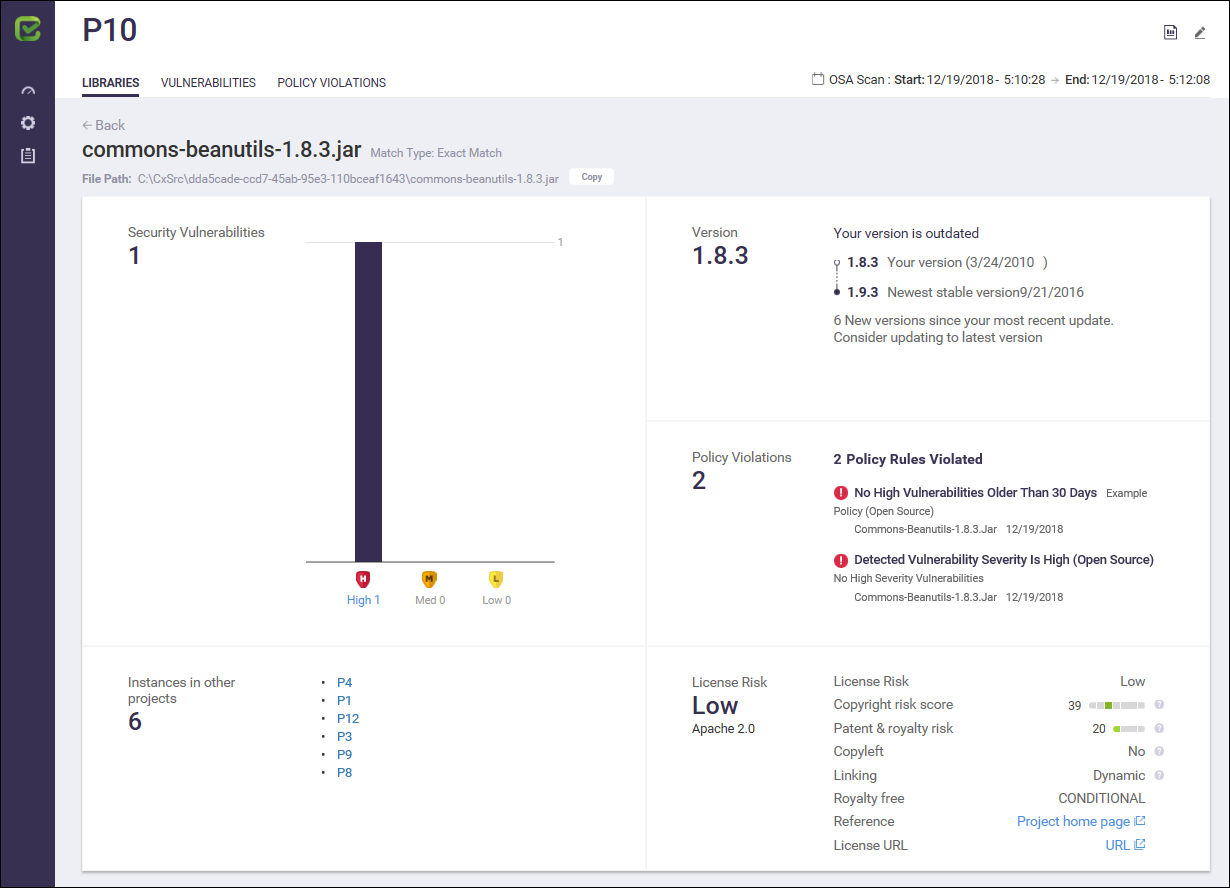 |
The Library Status includes the following information:
Item | Description |
|---|---|
Library File Name | Name of the library file |
Match Type | Libraries that were not found using the SHA-1 Hash, will be matched by the provided filename. Possible values are:
|
File Path | This represents the full path of the detected library, providing the actual location of the open source components. May contain more than one file path. Click Copy to save the path to your clipboard. NoticeFile Path works for Zip file upload of open source components. Currently is not supported for upload from plugins. |
Security Vulnerabilities | This represents the severity (High Medium, Low) of security vulnerabilities discovered in the library. |
Clicking on a severity link displays the vulnerability(s) associated with this library. For more information about this subject, see Vulnerabilities View. | |
Instances in other projects | This represents instances of the same library being used in other projects. Provides an active link to the other project. |
Version | Details regarding the version being used and the latest stable version available with release dates and the number of stable versions released in between both versions. A 'version is up to date' label is displayed when the version is up to date. |
Policy Violations | This represents the policy violation associated with the library status. Information includes the number of policy violations, the rule that triggered the policy violation and the detection date of the policy violation. |
License Risk | This represents the possible legal risk level with regards to licensing. Possible license risk states are: High, Medium, Low or No Risk. Also displayed is the following license compliance information: |
License Risk - Low, Medium, High or Unknown | |
Copyright Risk Score - range according to score level (0 – 100)
| |
Patent & Royalty Risk - range according to score level (0 – 100)
| |
Copyleft - Full (CopyLeft on modifications as well as own code that uses the OSS), Partial (CopyLeft applies only to modifications) or No (not a CopyLeft license). | |
Linking – Viral (will substantially infect the code linked to this OSS), Non Viral (will not affect the licensing of the linking code) or Dynamic (dynamic linking will not infect). | |
Royalty Free - Yes, No or Conditional | |
Mouse over each compliance result | |
Reference - Clicking on the Reference link provides a downloadable reference, e.g., XML file (.pom) | |
License URL - Clicking on the License URL link takes you directly to the official license web page. |
Open Source Analysis Report
The Open Source Analysis report can be viewed by clicking on the Open Report  icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
Vulnerabilities View
Clicking on the Vulnerabilities tab displays the Vulnerabilities view. The Vulnerabilities view allows you to explore all the vulnerable libraries associated with the selected project.
 |
The Vulnerabilities view includes the following vulnerable libraries information:
Item | Description |
|---|---|
Filter By | Using the filtering tool allows you to filter vulnerabilities according to single or multiple selections. |
Library Name – Filter by library name | |
State – Filter by vulnerability state. Filtering options: To Verify, Not Exploitable, Confirmed, Urgent, Propose Not Exploitable | |
Comment – Filter by user defined comment | |
Detection Date – Filter by specific date | |
Code Usage – to filter vulnerabilities in the vulnerabilities list according to source code usage (Called, Not Called or Unknown) | |
Reset – Reset the filter to its pre-defined state | |
Vulnerable Libraries List | Lists all the vulnerable libraries according to the selected severity type |
| |
| |
| |
 Low – Vulnerable libraries stated with low severity | |
Clicking on a severity type displays only those vulnerable libraries associated with the selected severity. All vulnerabilities listed here are in relation to the vulnerable library selected. | |
Vulnerability Actions | Clicking on one of the Action options (far right) or selecting a check-box in the Vulnerable Libraries List enables you to perform certain actions on the selected libraries/vulnerabilities. |
| |
| |
 Change Severity – Change the severity of the selected vulnerability(s). For more information about this subject, see Managing Vulnerabilities. | |
Vulnerability Status | Represents the vulnerability according to the current selection and includes all related information about the vulnerability. |
Vulnerability – This represents the name of the vulnerability (e.g., CVE-2015-4852). | |
Severity – This represents the severity of the vulnerability: | |
| |
| |
 Low – Vulnerabilities stated with low severity. | |
10 – This represents vulnerability score. | |
| |
| |
 – This represents the current version of the vulnerable library | |
 – This represents the date and time and that the vulnerability was first discovered. | |
| |
Description | Displays comprehensive information about the selected vulnerability, including risk details, a description of the cause and mechanism and may provide, if available, an active link to additional information about the vulnerability. |
Vulnerability Recommendations | Displays recommendations for avoiding the vulnerability. |
Library Information | Provides an active link to additional information about the vulnerable library. For more information about this subject, see 4PLibraries View. |
Versions | Provides details regarding the library version being used and the latest stable version available with release dates and the number of stable versions released in between versions. |
Match Type | Libraries that were not found using the SHA-1 Hash, will be matched by the provided filename. Possible values are:
|
Instances in other projects | This represents instances of the same library being used in other projects. Provides an active link to the other project. |
Managing vulnerabilities is available for single or multiple vulnerabilities and can be achieved from the Vulnerabilities View. For more information about this subject, see 4PManaging Vulnerabilities.
Open Source Analysis Report
The Open Source Analysis report can be viewed by clicking on the Open Report  icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
Managing Vulnerabilities
Managing vulnerabilities can be achieved from the CxOSA Viewer. Managing vulnerabilities is available for single or multiple vulnerabilities and can be achieved using the following actions in the 4PVulnerabilities View.
Adding a Comment to a Vulnerability(s)
Selecting a check-box in the Vulnerable Libraries List enables you to add a comment to a vulnerability. This is useful for defining how to handle the vulnerability.
Once the vulnerability checkbox is selected, click the Add Comment  icon. The Add Comment dialog is displayed.
icon. The Add Comment dialog is displayed.

Type in your comment and click Add. The Comment is displayed in the Vulnerabilities List.
Changing the State of a Vulnerability(s)
Selecting a check-box in the Vulnerable Libraries List enables you to change the state of a vulnerability. This is useful for disregarding false positives or just for defining what vulnerabilities to handle and how to handle them.
Once the checkbox is selected, click the Change State icon. The Change State dialog is displayed.
icon. The Change State dialog is displayed.
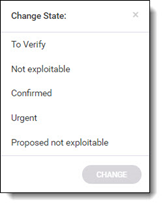
Select the state. The following states can be defined:
State | Description |
|---|---|
To Verify (default) | Vulnerability requires verification, for example, by an authorized user |
Not Exploitable | Vulnerability has been confirmed as not exploitable (i.e., false positive) |
Confirmed | Vulnerability has been confirmed as exploitable and requires handling |
Urgent | Vulnerability has been confirmed as exploitable and requires urgent handling |
Proposed Not Exploitable | Vulnerability has been proposed as not exploitable, for example, as a potential false positive. Vulnerabilities defined with this state remain a potential threat until such a time that the state is changed to 'Confirmed' or 'Not Exploitable' |
Notice
In case the project is assigned to a policy, any change in state will trigger policy recalculation. To shorten the recalculation time, click RECALCULATE.
Changing the Severity of a Vulnerability(s)
Selecting a check-box in the Vulnerable Libraries List enables you to change the severity of a vulnerability. This is useful for defining a new severity to the vulnerability during handling.
Once the checkbox is selected, click the Change Severity  icon. The Change Severity dialog is displayed.
icon. The Change Severity dialog is displayed.
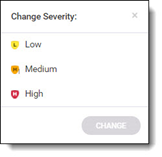
Select the Severity. The following severities can be defined:
Severity | Description |
|---|---|
 Low | Vulnerabilities stated with low severity |
 Medium | Vulnerabilities stated with medium severity |
 High | Vulnerable libraries stated with high severity |
Click Change. The severity of the vulnerability is changed and is displayed in the Vulnerabilities List.
In case the project is assigned to a policy, any change in severity will trigger policy recalculation. To shorten the recalculation time, click RECALCULATE.
Open Source Analysis Report
The Open Source Analysis report can be viewed by clicking on the Open Report  icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
Policy Violations View
Policy Management provides a centralized management console for defining, managing and tracking an organization’s acceptable security risk across all its applications and projects, using unified application security policies across customer/proprietary code and open source components.
A security policy is comprised of customer-defined rules that serve to define compliance, and against which violations occur. After a policy is created, it can then be assigned to one or more projects. Multiple policies can also be defined per project.
Policy Management supports CxOSA rules pertaining to the library, license and vulnerabilities. For more information about this subject, see Policy Management.
Clicking on the Policy Violations tab displays the Policy Violations view. The Policy Violations view allows you to explore all the policy violations associated with the selected project.
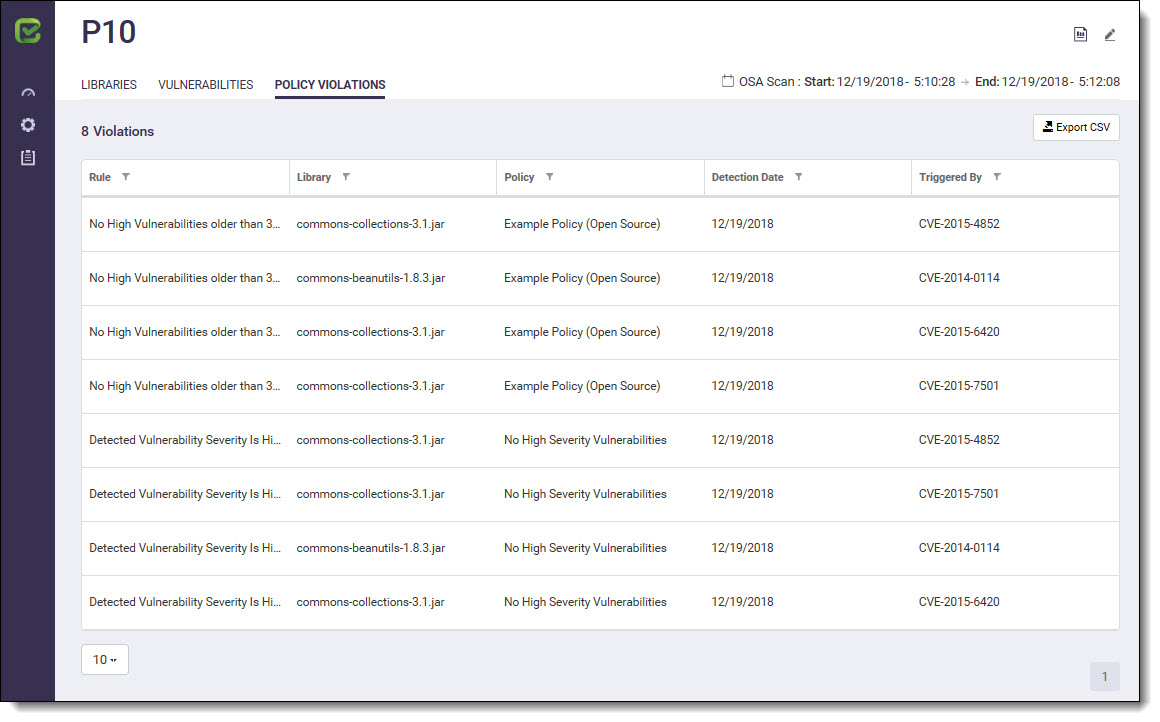
You can filter policy violations in the Violations List by Rule, Library, Policy (example below), Detection Date and Triggered By, by clicking on the filter and selecting the relevant search option(s).
The Violations List includes the following policy violation information:
Item | Description |
|---|---|
# Violations | Number of policy violation associated with the selected project. |
| |
Rule | The rule currently being used in the policy. For more information about this subject, see CxOSA Policy Management. |
Library | This represents the policy violated library |
Policy | The policy currently being used in the project. For more information about this subject, see CxOSA Policy Management. |
Detection Date | Detection date of the policy violation |
Triggered By | The library that triggered the policy violation |
Exporting the Results (.csv)
Once the results become available you have the capability to export the library table to a comma-separated values (.csv) file. Click Export to CSV.
Open Source Analysis Report
The Open Source Analysis report can be viewed by clicking on the Open Report  icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.
icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing. For information about the CxOSA Report, see Generating a CxOSA Scan Results Report.