GitLab Cloud
This flow uses pre-configured settings that enable you to authenticate with GitLab cloud using your login credentials. This flow is available for multi tenant Checkmarx accounts using GitLab cloud environments. We offer an alternative self-hosted flow that involves submitting a GitLab Application ID and Application Secret.
The Self-Hosted flow must be used for:
Checkmarx One single tenant accounts
Repos hosted on-prem.
Organizations that prefer to use an Application ID and Secret
Setting up the Integration and Initiating a Scan
To integrate your GitLab organization with Checkmarx One, perform the following:
In the Applications and Projects home page, click on New > New Project - Code Repository Integration.
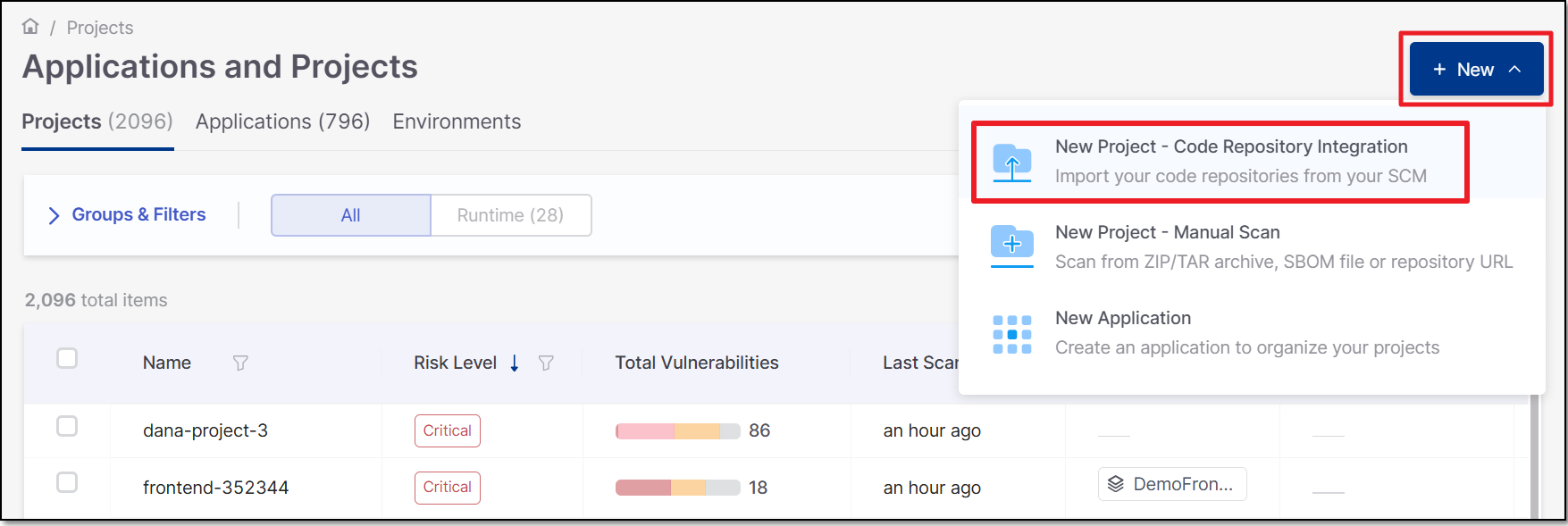
The Import From window opens.
Select Cloud-hosted >GitLab >Next.
For first-time use, you will be prompted to log in to your GitLab account.
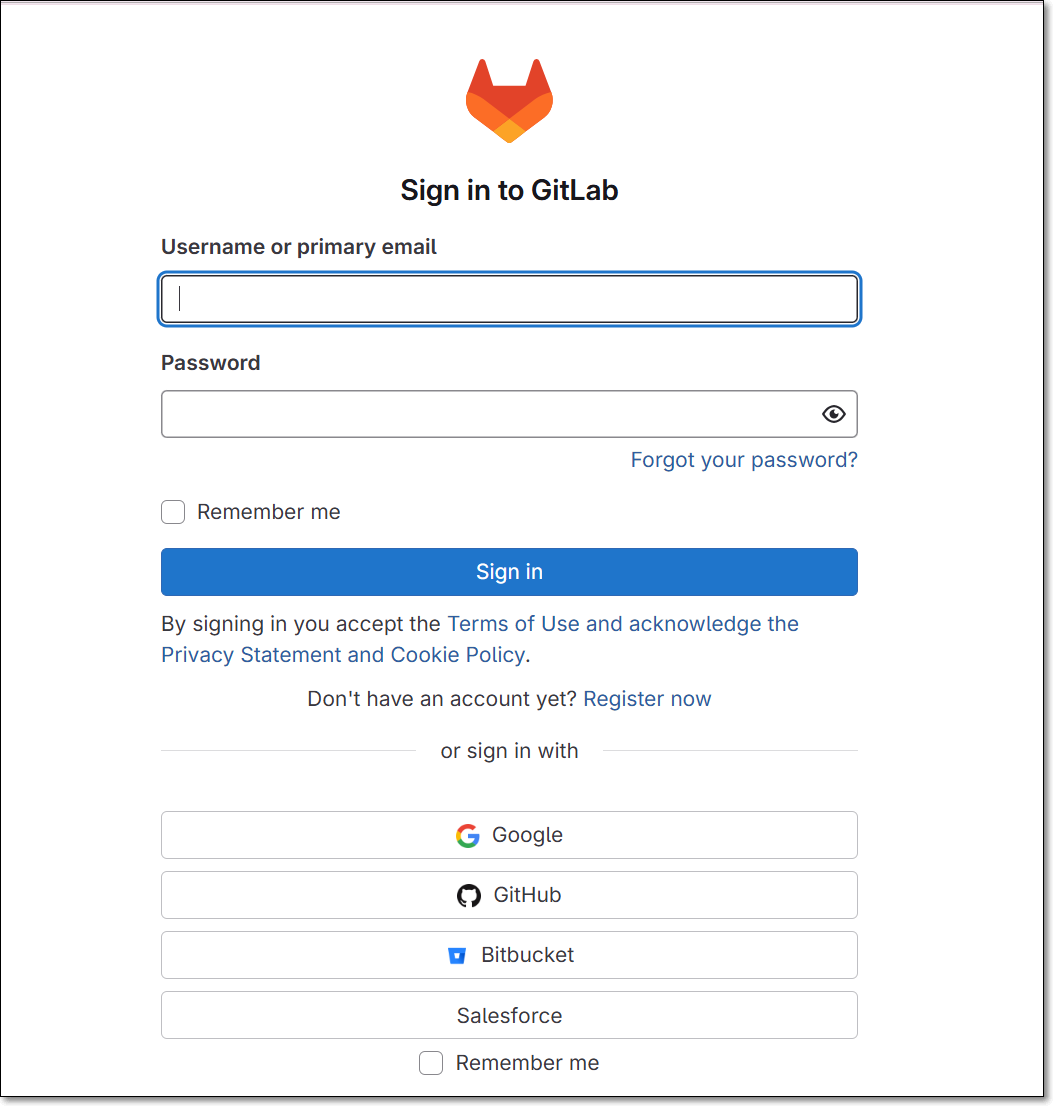
Select the GitLab User/Organization or Group (for the requested repository) and click Select Organization.
The screen contains the following functionalities:
Search bar - Users need to type at least 3 characters of the organization name (GitLab limitation). The search is not case sensitive.
Infinite scroll - For enterprises with a large amount of organizations.
Note
In case you selected GitLab User skip step 5.
Select Repositories inside the GitLab organization and click Select Repositories.
If the organization contains active repositories, suggested repos will be presented and selected automatically. For additional information see Suggested Repositories.
Note
A separate Checkmarx One Project will be created for each repo that you import.
There can’t be more than one Checkmarx One Project per repo. Therefore, once a Project has been created for a repo, that repo is greyed out in the Import dialog.
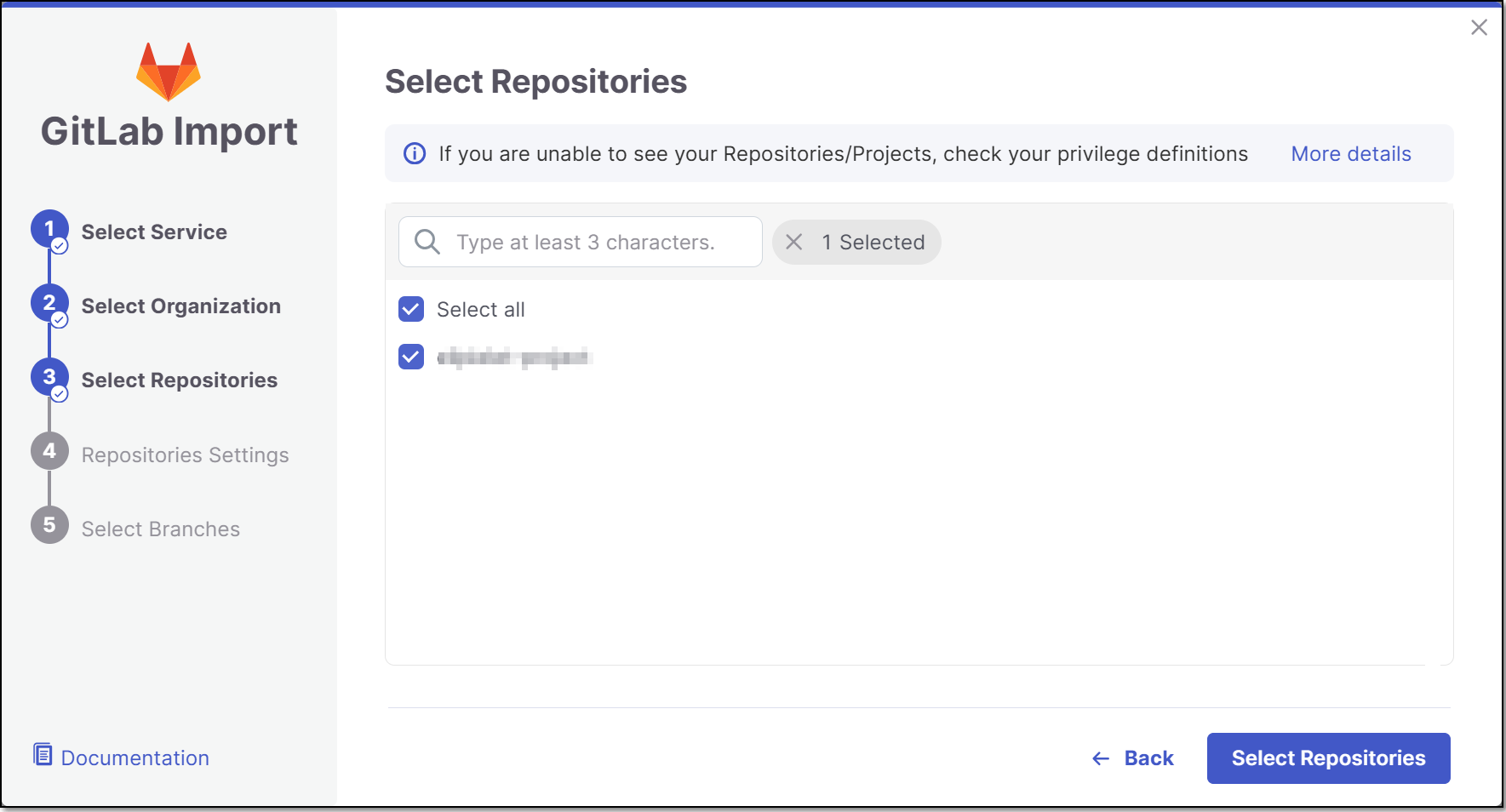
In the Repositories Settings step, you can optionally adjust the settings as follows:
If the project has multiple repositories, click All Repositories Settings to adjust the settings for all repositories, or select a specific repository, to adjust the settings for that repository.
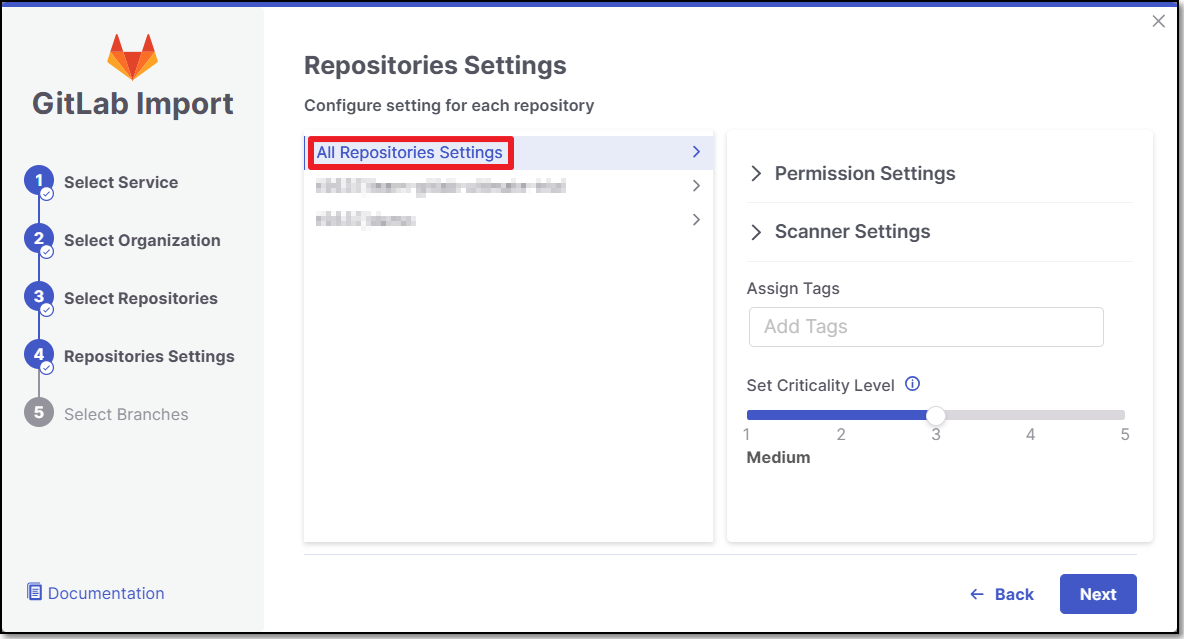
Expand the Permissions Settings and adjust the following settings:
Scan Trigger: Push, Pull request - Automatically trigger a scan when a push event or pull request is done in your SCM. (Default: On)
Pull Request Decoration - Automatically send the scan results summary to the SCM. (Default: On)
SCA Auto Pull Request - Automatically send PRs to your SCM with recommended changes in the manifest file, in order to replace the vulnerable package versions. (Default: Off)
Expand the Scanner Settings and enable the toggle for each scanner you want to use (SAST, SCA, IaC Security, Container Security, API Security, OSSF Scorecard, Secret Detection) for your repositories. At least 1 scanner must be selected for each repository.
Protected Branches (when a specific repository is selected): Specify the branches to be designated as "Protected Branches".
Notice
Specifying a branch as a Protected Branch affects three main areas: scan triggering (for PR and push), policy violation detection, and Feedback App notifications.
COMING SOON: You can also use a wildcard symbol "*" to designate which branches are protected. The wildcard can be used before the string, after the string, or both. All branches that match the wildcard pattern will be treated as protected branches.
Examples:
*→ all branchesrelease*→ branches that begin with "release"*release→ branches that end with "release"* release *→ branches that contain "release" anywhere in the name
Note
For additional information about Protected Branches see About Protected Branches
Add SSH key (when a specific repository is selected).
Assign Tags: Add Tags to the Project. Tags can be added as a simple strings or as key:value pairs.
Set Criticality Level: Manually set the project's criticality level.
Click Next.
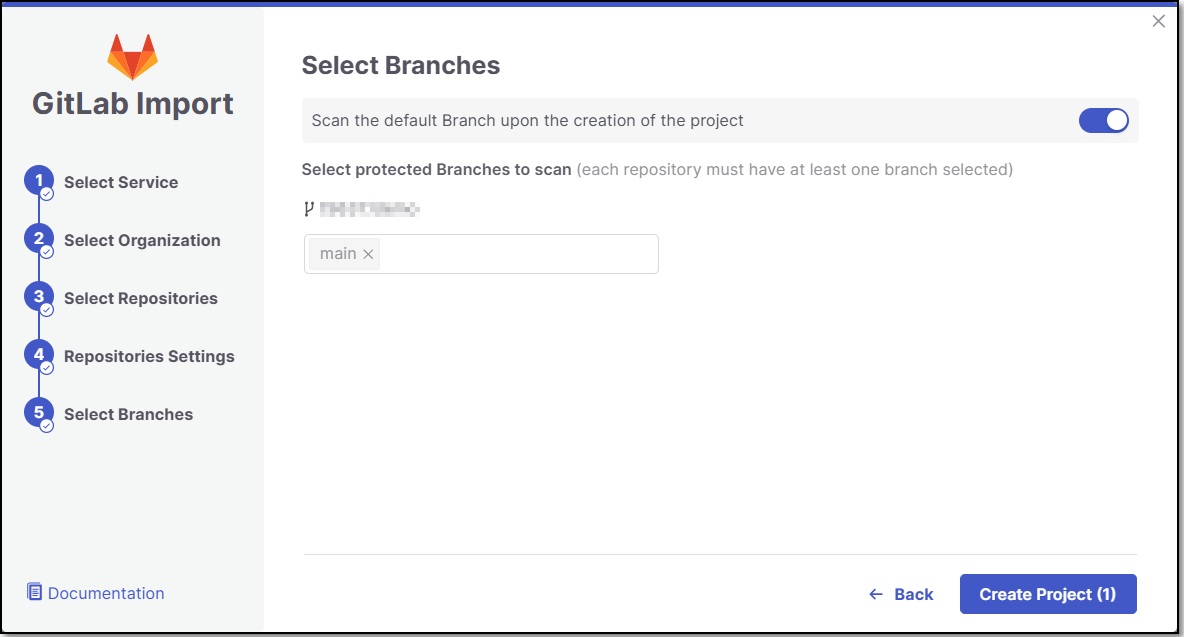
In the Select Branches screen you can decide whether to enable the "Scan the default Branch upon the creation of the project" feature.
For each repository, select the protected branches you want to scan during project creation, and then click Create Project.
Tip
If you specified a wildcard pattern in the previous step, it will not appear as an option on this list.
The Project is successfully created in the Applications and Projects home page, and the scan is initiated.
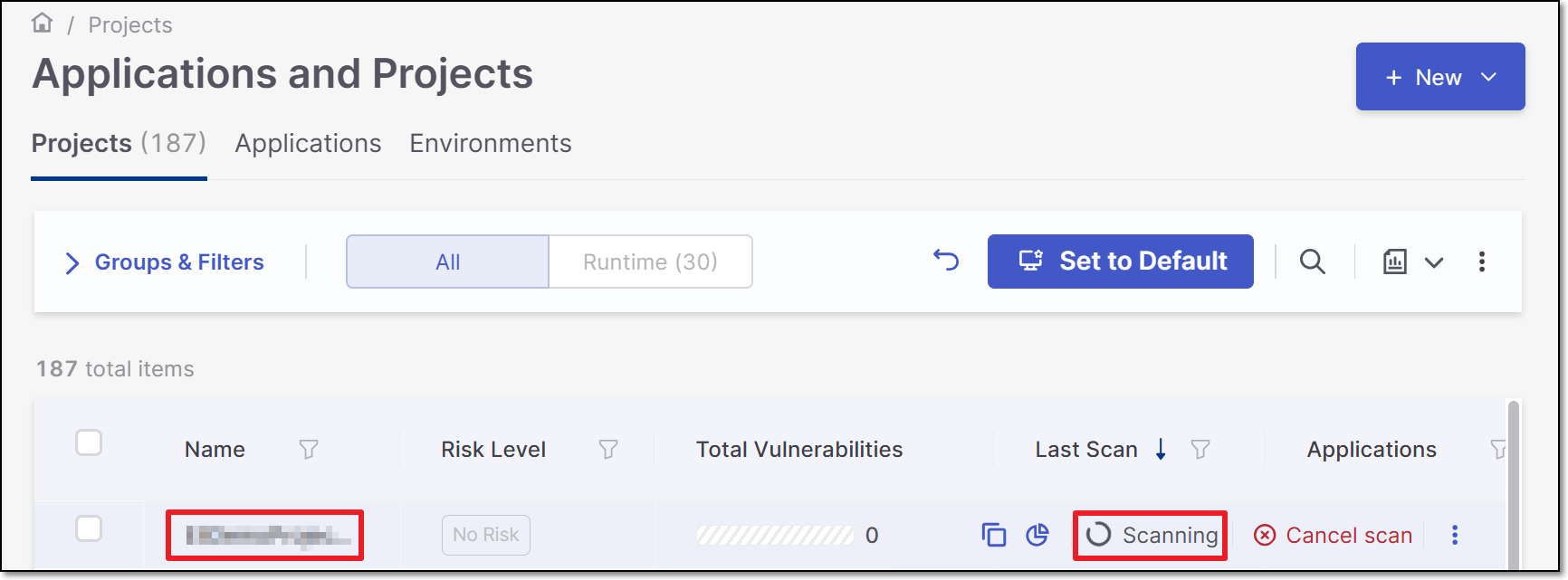
Note
In order to update the scanners see Imported Project Settings