- Checkmarx Documentation
- Checkmarx SCA
- Checkmarx SCA - User Guide
- Viewing Results
- Viewing the Project Page
- Project Page Tabs
Project Page Tabs
 |
The following sections describe the info shown in each of the tabs on the Project page.
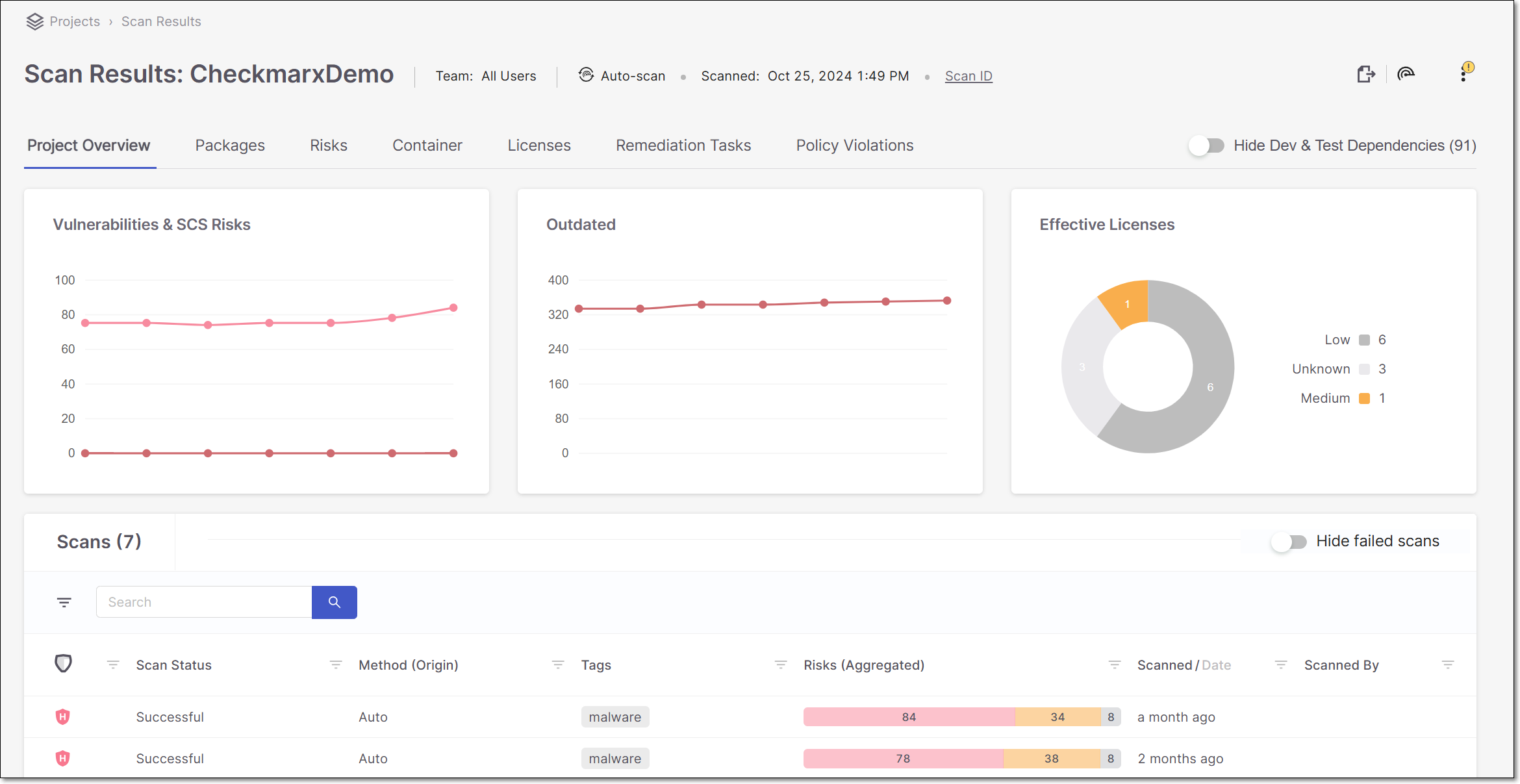
Project Overview
The Overview tab shows the overall status of the Project. The page contains the following sections.
Overview Widgets - these widgets show key info about the Project in a graphical format.
Scans - shows a list of all scans of the Project. For each scan of the project it shows the risk level, status, scan method, vulnerabilities, when it was scanned, and by whom.
 |
Project Overview Widgets
The following table describes the info shown in the Overview widgets.
Item | Description | Possible Values | |
|---|---|---|---|
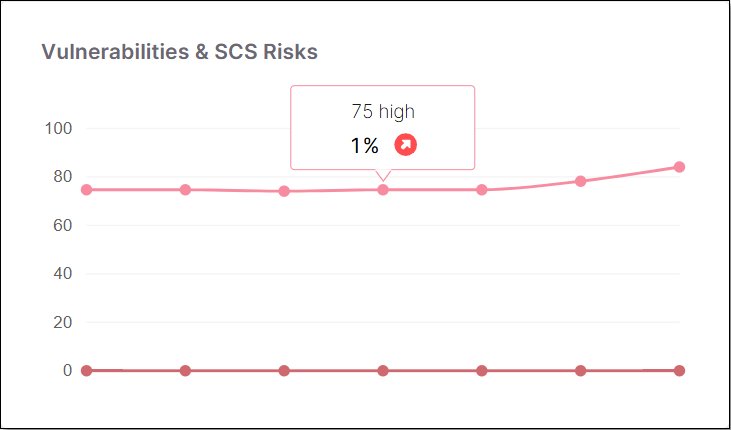
Vulnerabilities & SCS Risks | A line graph showing the number of vulnerabilities and scs risks over time according to severity. Each point on the graph represents a different scan of the project. Hover over a point to see the exact number of vulnerabilities. |
- | |
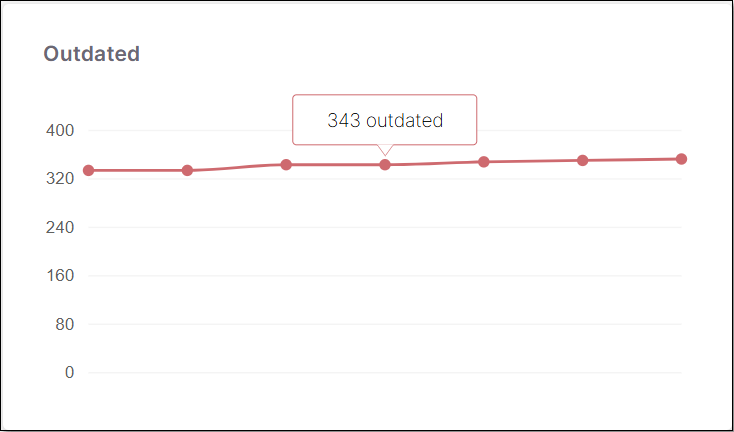
Outdated | A line graph showing the number of outdated packages in the Project over time. Each point on the graph represents a different scan of the Project. Hover over a point to see the exact number of outdated packages. |
- | |
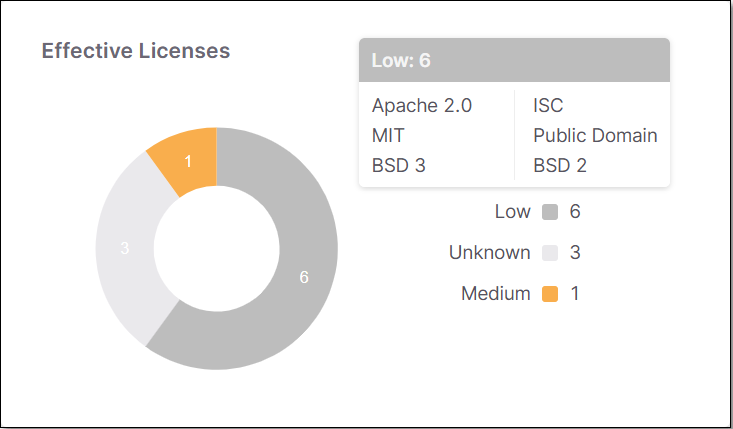
Effective Licenses | A color coded graph indicating the number of distinct legal risks of each severity level. Hover over the graph or the key to show a breakdown of license names within each Legal Risk level. Click on the graph or the key to open the Packages tab of the Scan Results page, filtered by the Legal Risk level you clicked on (high, medium, low, or unknown). | -
|
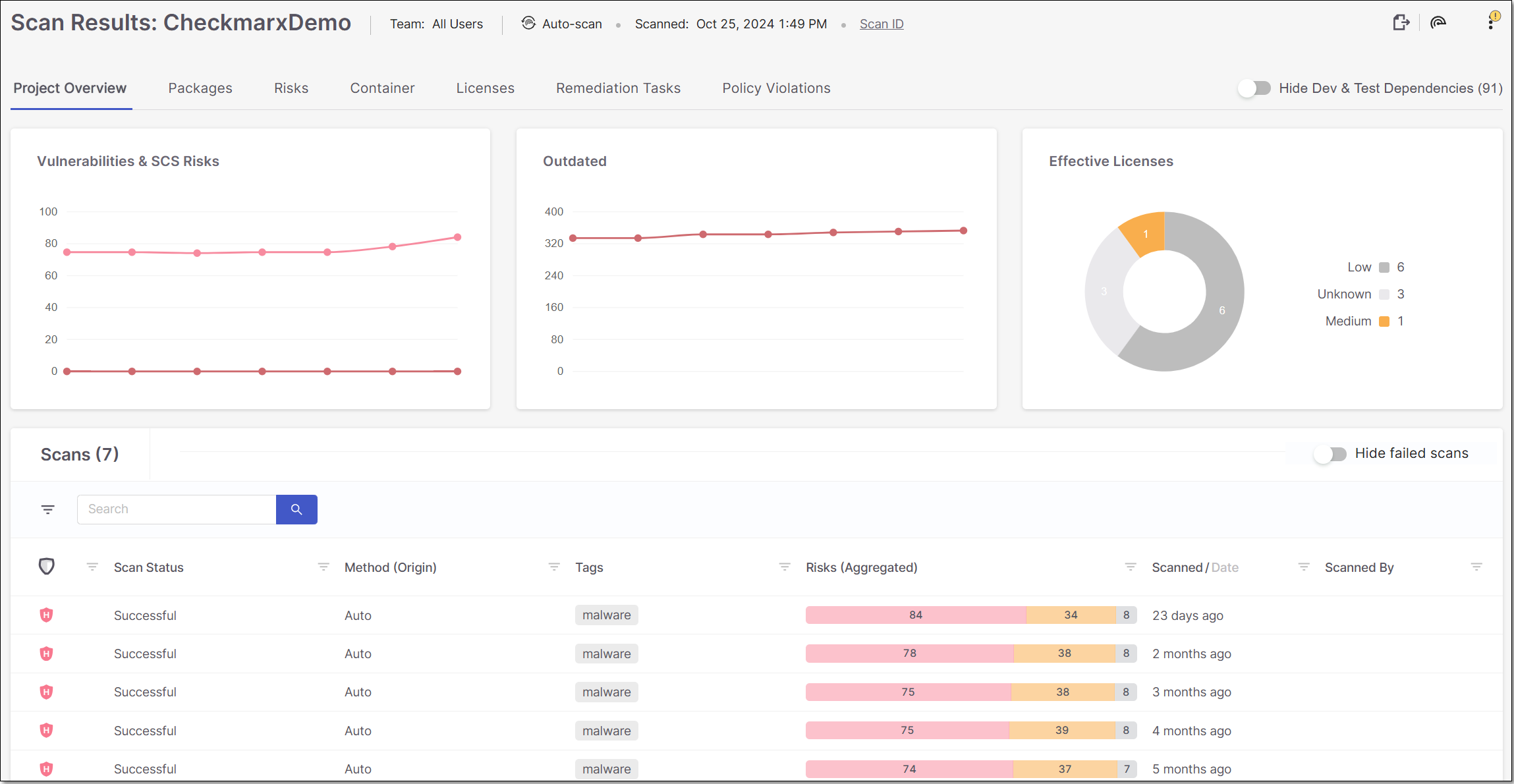
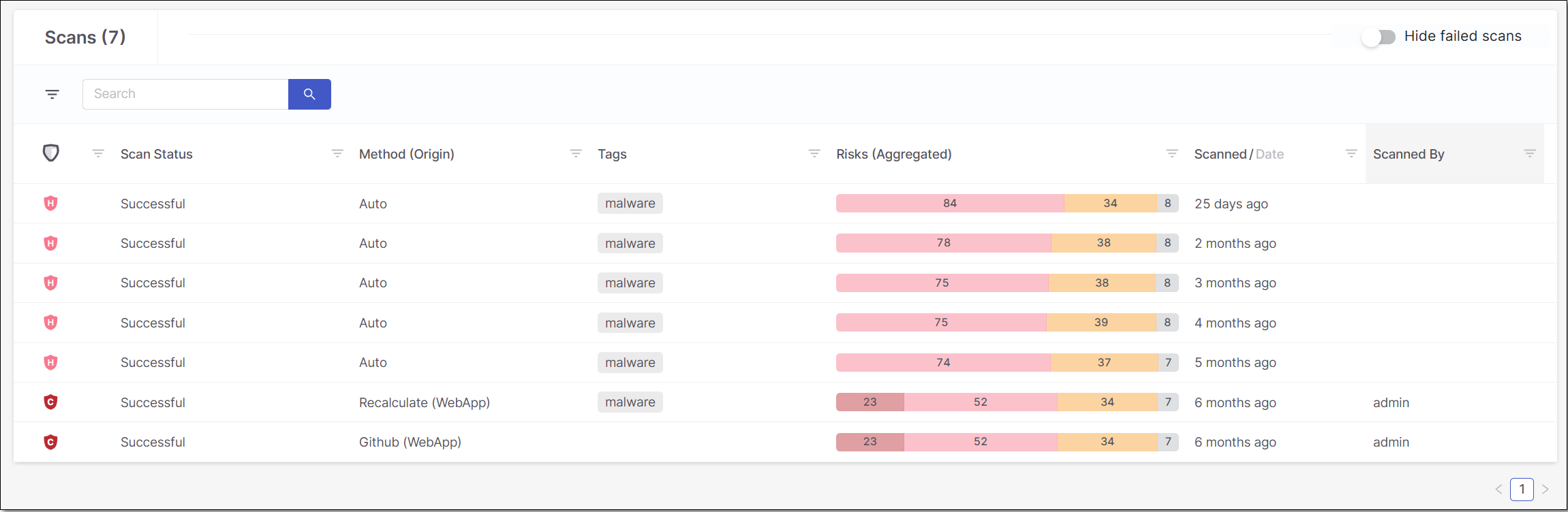
Scans
This section shows a list of all scans that were run on the Project. Each record shows general info about the scan as well as overall results for the scan. You can filter the results by entering a specific value for Scan Method or Scanned By in the search box. You can also sort by column headers and set filters for each column.
You can click on a specific scan to show data for that scan. If you clicked on any scan other than the most recent scan, a message in the header bar indicates that a Newer Report is Available. Click on this message to open the most recent Risk Report for the Project.
Warning
This screen only shows data for 30-50 of the most recent scans (depending on number and timing of failed scans). Data for earlier scans is still stored in the system and can be retrieved via API.
 |
Item | Description | Possible Values | |
|---|---|---|---|
Risk Level | The severity level of the highest vulnerability existing in the package, based on its CVSS score in the NVD. |
For more info see Severity Levels. | |
Scan Status | The current status of the scan. | Scanning, Successful, Failed | |
Method (Origin) | The method that was used to scan the project. |
| |
Tags | The tags assigned to the scan. | e.g., Dev | |
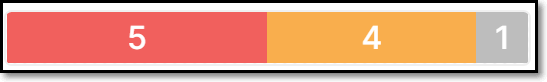
Risks (Aggregated) | A color coded bar graph indicating the number of risks of each severity level. | e.g.,
| |
Scanned/Date | The relative time or complete date that the last scan was performed on your project. Toggle between relative time and date by clicking Scanned or Date in the column header. | e.g., 19 days ago e.g., Jan 28, 2021 11:22 AM | |
Scanned By | The user who initiated the scan. | e.g., admin | |
Action Buttons | |||
Hide failed scans toggle | In the Header Bar there is a Hide failed scans switch that enables you to hide the scans that failed when scanning. Toggle this switch (to the right) in order to hide the failed scans. | - | |
Packages Tab
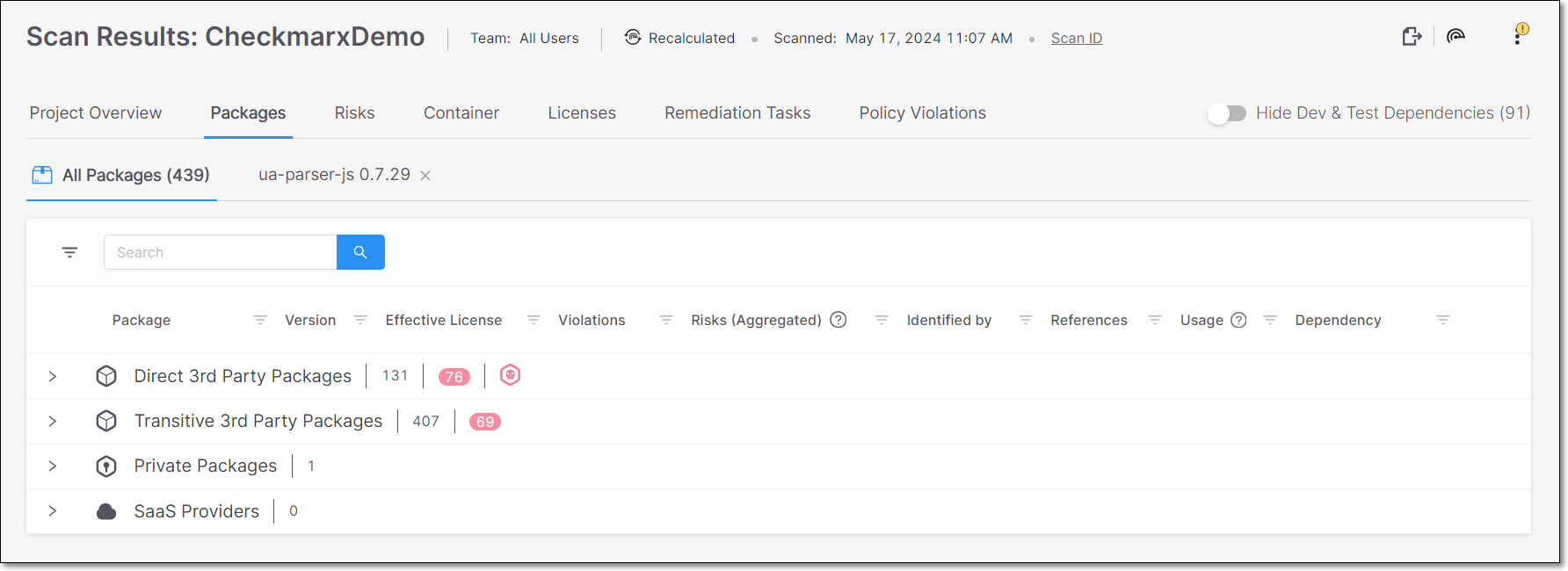
The Packages tab shows detailed info about the packages that were identified in your source code and the vulnerabilities that they contain.
 |
The Packages tab contains sub-tabs that show two types of pages:
All Packages – shows a list of all packages that contain vulnerabilities that were identified by this scan. This tab is accessed by clicking on the Scan Results button on the Project page. The results in this table are divided into the following categories:
Direct 3rd Party Packages - Shows all 3rd party packages called directly by your source code.
Transitive 3rd Party Packages - Shows all 3rd party packages called indirectly by your project.
Private Packages - Shows all private packages identified in your project.
Notice
A “private package” is a package or library developed in-house that is being used across the organization. For example, a logging library that was developed in-house and is used by several different projects. These packages are only visible to the specific collaborators/teams that were granted access.
SaaS Providers - Shows all packages used for accessing SaaS services.
Notice
Alternatively, you can access this page by clicking on Latest Scan Results in the more options menu in the project's row on the Dashboard). In addition whenever you navigate to the Scan Results page, the All Packages sub-tab is shown under the Packages tab.
Package Details – shows detailed info about a specific package. Click on a row in the All Packages sub-tab or in the Project page to access this page.
Notice
Alternatively, you can access this page by clicking on a package in the Global Inventory & Risks > Packages page.
You can navigate between the various tabs that you have opened.
All Packages Page
The All Packages sub-tab shows separate tabs for the different types of packages (Direct 3rd Party Packages, Transitive 3rd Party Packages, Private Packages, and Saas Providers). Each tab shows the overall number of packages of this type as well as the number of policy violations for that category.
Notice
For a package that is referenced both directly and transitively, the total number of packages shown at the top of the All Packages tab counts that package only once. Therefore, the total number of packages may be fewer than the total of the Direct packages plus the number of Transitive packages.
Clicking on a category heading expands that section, to show a list of packages of that type that were identified by this scan of your Project. For each package, info is shown about the risks related to that package. You can search for specific packages using the search box.
You can also sort by column headers and set filters for each column.
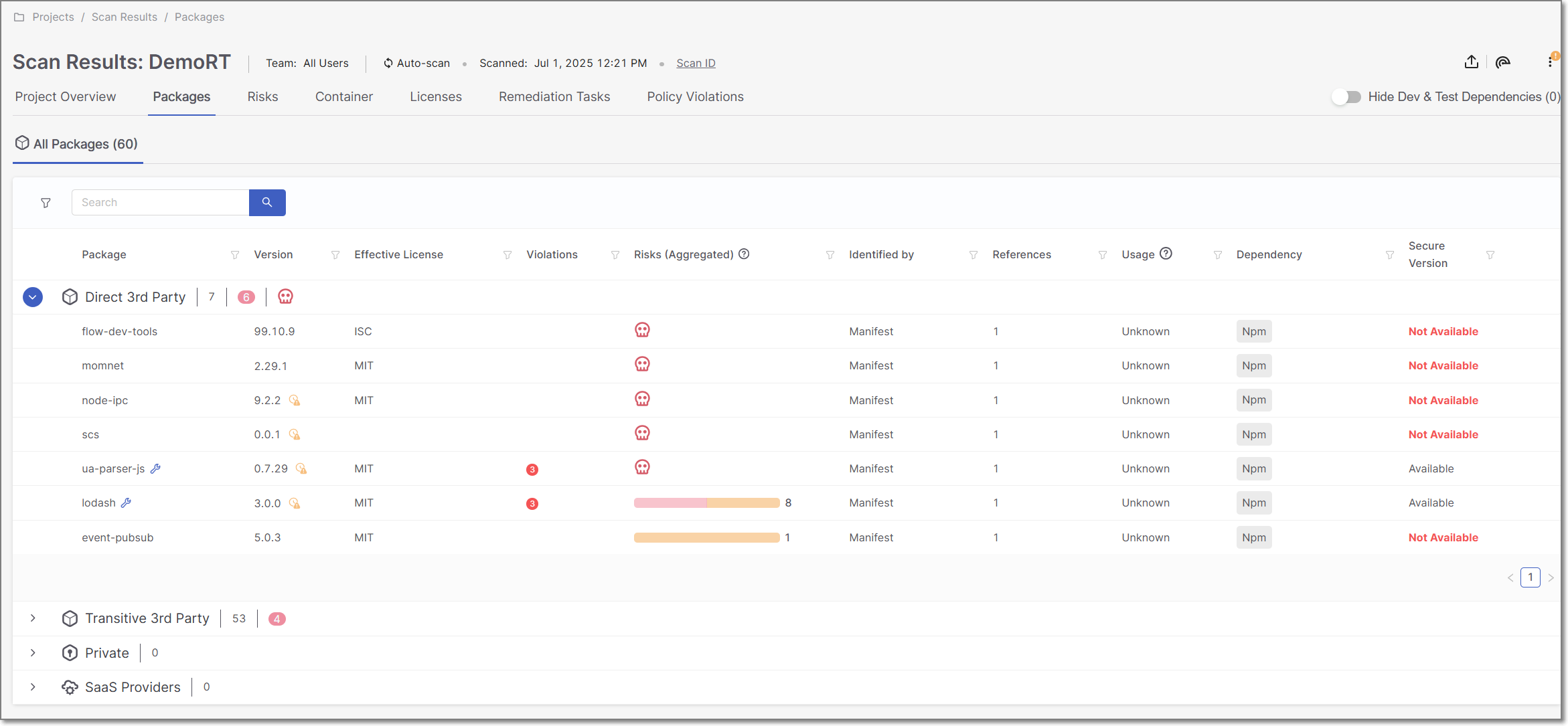 |
The following table describes the info shown for each package identified by this scan.
Item | Description | Possible Values | |
|---|---|---|---|
Package | The name of the package. This column also shows the Clicking on the icon takes you to that item in the Remediation Tasks Tab . | e.g., dom4j:dom4j | |
Version | The version of the package that you are using. This column also shows the Hover over the icon to view additional info about more recent versions. | e.g., 1.6.1 | |
Effective License | Shows all licenses that are associated with this package. For multiple licenses, hover over the display to show all licenses and the associated legal risks. | e.g., GPL 2.0, Apache2.1 | |
Violations | If the package contains risks that violate one or more security policies that apply to the project in which the package was identified, the number of policy violations is shown in red, see Policy Management. | e.g., | |
Risks (Aggregated) | A color coded bar graph indicating the number of vulnerabilities of each severity level. Hover over the bar to view a breakdown of the results by Vulnerability, Legal Risk and Suspected Malware. For a malicious package, the malicious icon TipYou can apply complex filters to show only packages that contain risks of a specific type and of a specific severity. | e.g.,
| |
Identified by | Indicates how the package was identified. |
| |
References | Shows the number of paths that reference this package. TipPackages that are referenced both directly and transitively, are included in the Direct 3rd Party section and the number of direct (D) and transitive (T) paths are given. | e.g., 1D, 12T | |
Usage (for Projects with Exploitable Path activated) | Indicates whether or not this package is used (called) by your project’s source code. |
| |
Dependency | Shows labels that Checkmarx applied to the package. There is a label indicating the package manager used for package resolution. Additional labels are applied to special types of dependencies. |
| |
Secure Version | Indicates whether or not a remediated version (i.e, a version with no vulnerabilities) of this package exists. |
| |
Explore in AppSec Knowledge Center | Click on the |  |
Package Details Page
The Package Details sub-tab shows detailed info about a specific package. The top info pane gives general info about the package, and the separate cards below it show detailed info about various aspects of the risks posed by the package.
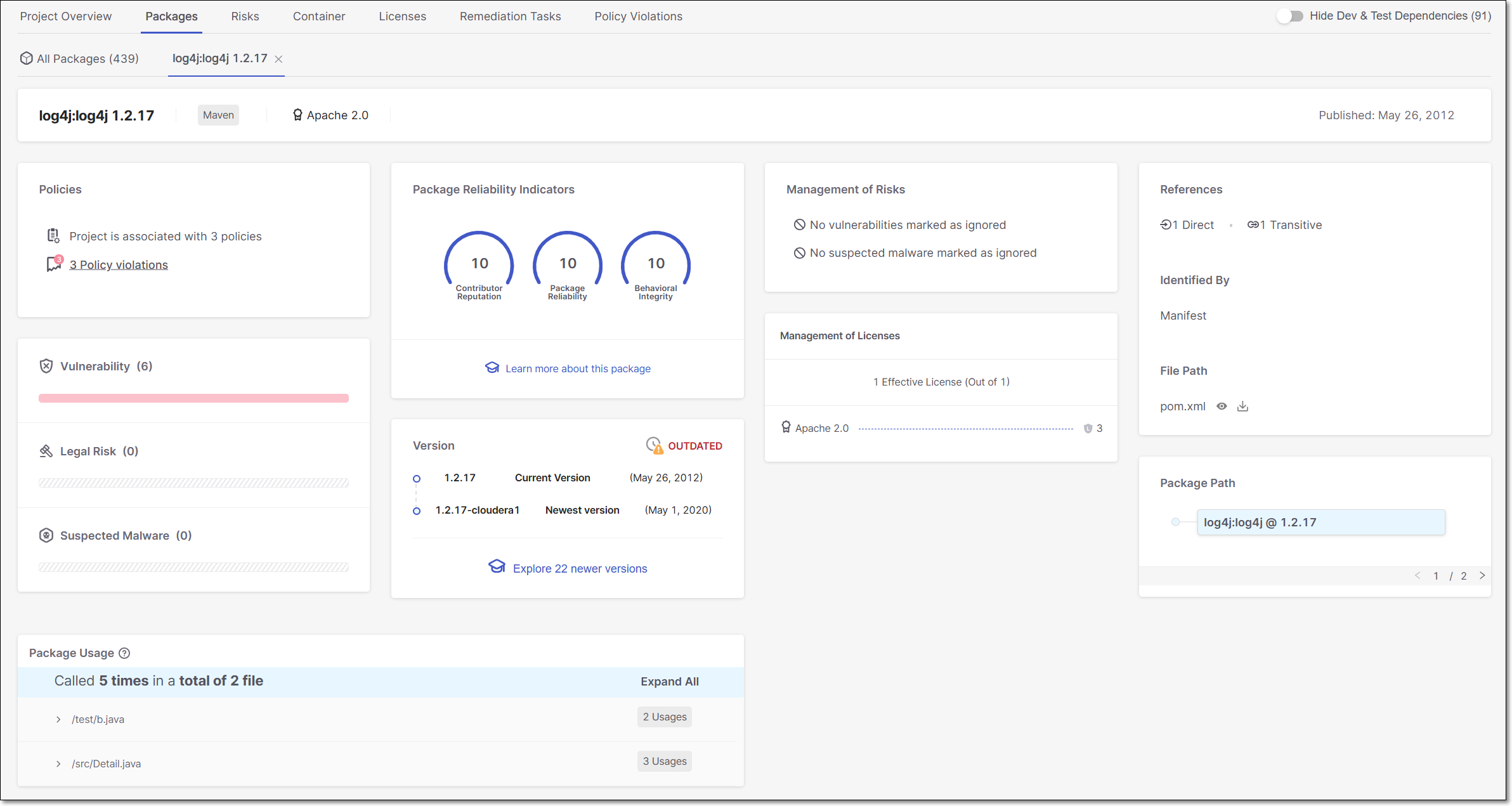 |
Info Pane
 |
Item | Description | |
|---|---|---|
Package | The name and version of the package. | |
Remediation Task
| The Clicking on the icon takes you to that item in the Remediation Tasks Tab . | |
Dependency Type | The type of package manager used for this package. | |
License(s) | Shows all licenses that you have that are associated with this package. | |
Published | The date that this version of the package was published. |
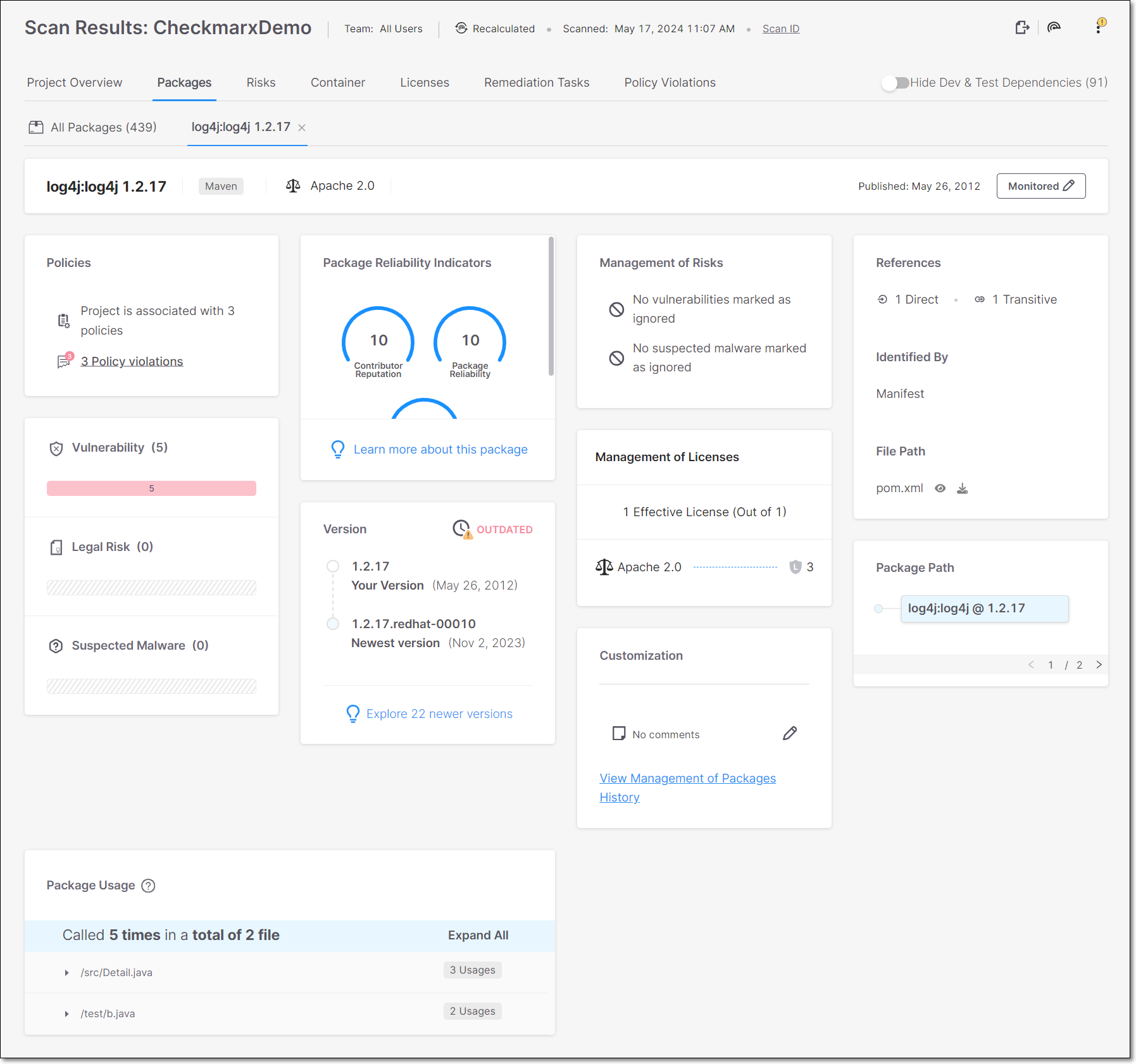
Package Details Sections
 |
Item | Description |
|---|---|
Watch Out! (for malicious packages) | This warning card will be displayed if this version of the package is known to be malicious. |
Policies | The total number of policies this project is assigned to, followed by the number of Policy Violations. |
Vulnerability | The total number of vulnerabilities in this package, followed by a color coded bar graph indicating the number of vulnerabilities of each severity level. |
Legal Risk | The total number of Legal Risks in this package, followed by a color coded bar graph indicating the number of Legal Risks of each severity level. |
Suspected Malware | The total number of Suspected Malware risks affecting this package, followed by a color coded bar graph indicating the number of Suspected Malware risks of each severity level. |
Package Reliability Indicators | Shows gauge widgets representing three risk categories (Reputation, Reliability and Behavior). The scores are given on a scale of 0-10, with 10 indicating the highest level of security. |
Version | Shows the version you are using, the newest version, the number of newer versions released since you last updated and an overall assessment of whether there is a need to update your version. |
Learn More About This Package | Shows a link to the AppSec Knowledge Center for more information about this package. |
Management of Risks | Shows if any vulnerabilities and Suspected Malware risks have been marked as ignored. |
Management of Licenses | Shows the number of Licenses that have been marked as Effective Licenses. In addition, a link is given to view detailed information about this license in the risk details tab. |
References | Shows the number of manifest files that refer to this package and indicates whether it is a direct or transitive dependency. |
Identified By | Indicates how the vulnerable package was identified. Possible values are:
|
File Path | The file path to the manifest file where this package was identified is shown. Click on the icons to view or download the file. |
Package Path | The selected package is displayed in blue. If this is a transitive dependency (i.e., it is accessed via other packages), then the full path by which the package is accessed is shown above it. You can click on any package shown in the path in order to open a new tab showing details for that package. If there are multiple paths to this package, then you can click on the forward and back arrows at the bottom of the pane to view each of the paths. TipFor packages that were identified by binaries (and not by a manifest file), no data is shown for the package path. TipFrequently you can fix the vulnerabilities by updating the transitive packages with their latest versions. |
Package Usage (for projects with Exploitable Path activated) | Shows the places in your code where the vulnerable package is called. Results are grouped by file path. Expand an item to see the line number and node of each place where the package is called. |
Risks Tab
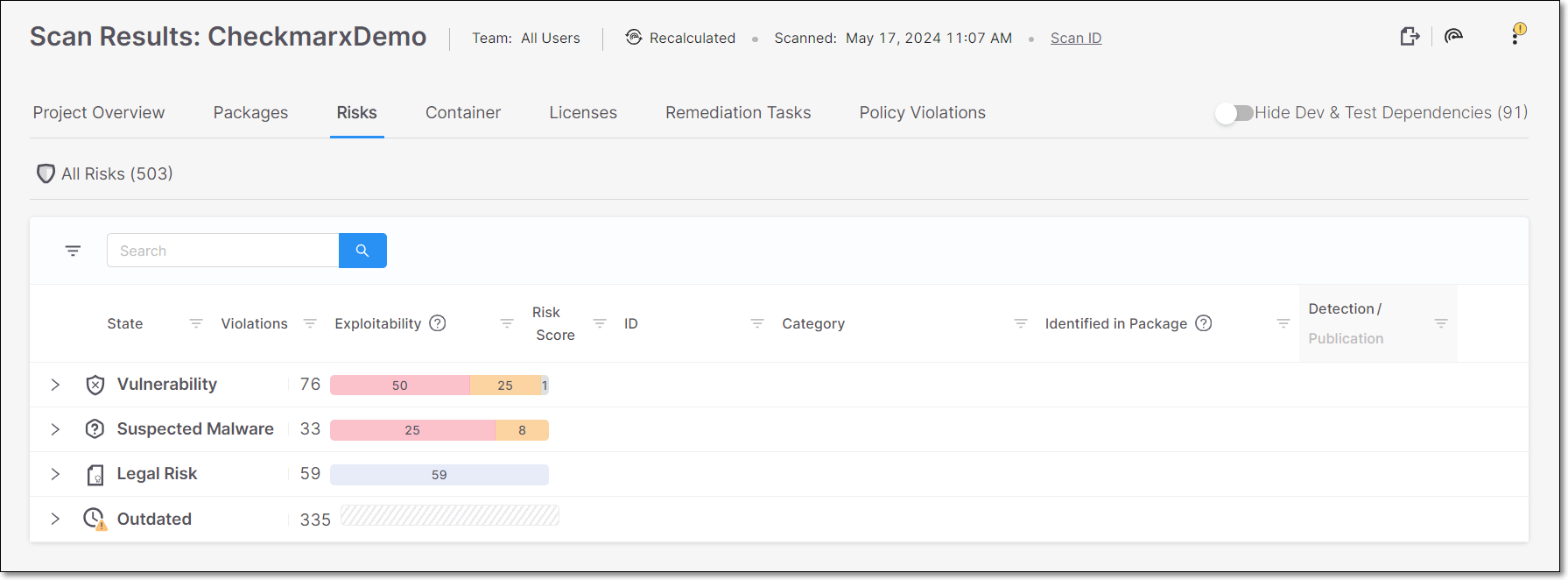
The Risks tab shows info about all of the Risks that are associated with the open source packages used by your project. This includes vulnerabilities (e.g., CVEs), as well as suspected malware risks (e.g., malicious packages), legal risks and outdated packages.
 |
The Risks tab contains sub-tabs that show two types of pages:
All Risks – shows a list of all Risks identified by this scan. This tab is accessed by clicking on the Show All button on the Project page and then selecting the Risks tab. The results on the All Risks tabs are divided into the following tabs:
Vulnerability - shows a list of vulnerabilities in your open source packages that can be exploited by an attacker. This includes vulnerabilities that have been published as CVEs as well as vulnerabilities identified by the Checkmarx Vulnerability Research Team (i.e., Cx). The summary graph shows the total number of vulnerabilities and a breakdown by severity level.
Suspected Malware - shows various types of suspected malware risks that affect the packages in your project, such as packages that are Malicious by design and packages that are vulnerable to ChainJacking attacks etc. The summary graph shows the total number of suspected malware risks and a breakdown by severity level.
Legal Risk - shows all of the Legal Risks relating to the licensing of the packages used in your project. The summary graph shows the total number of legal risks and a breakdown by severity level.
Outdated - shows a list of all packages that have vulnerabilities or suspected malware risks, for which a more recent package version is available.
Risk Details – shows detailed info about a specific Risk. Click on a row in the All Risks tab to access this page.
Notice
Clicking on a Legal Risk opens the Licenses tab filtered for the relevant license.
Notice
Alternatively, you can access this page by clicking on a Risk in the Global Inventory & Risks > Risks page.
Notice
Clicking on a Legal Risk opens the Licenses tab filtered for the relevant license.
The packages listed in the Outdated section aren’t clickable and don’t have a Risk Details page associated with them.
You can navigate between the various tabs that you have opened.
All Risks Page
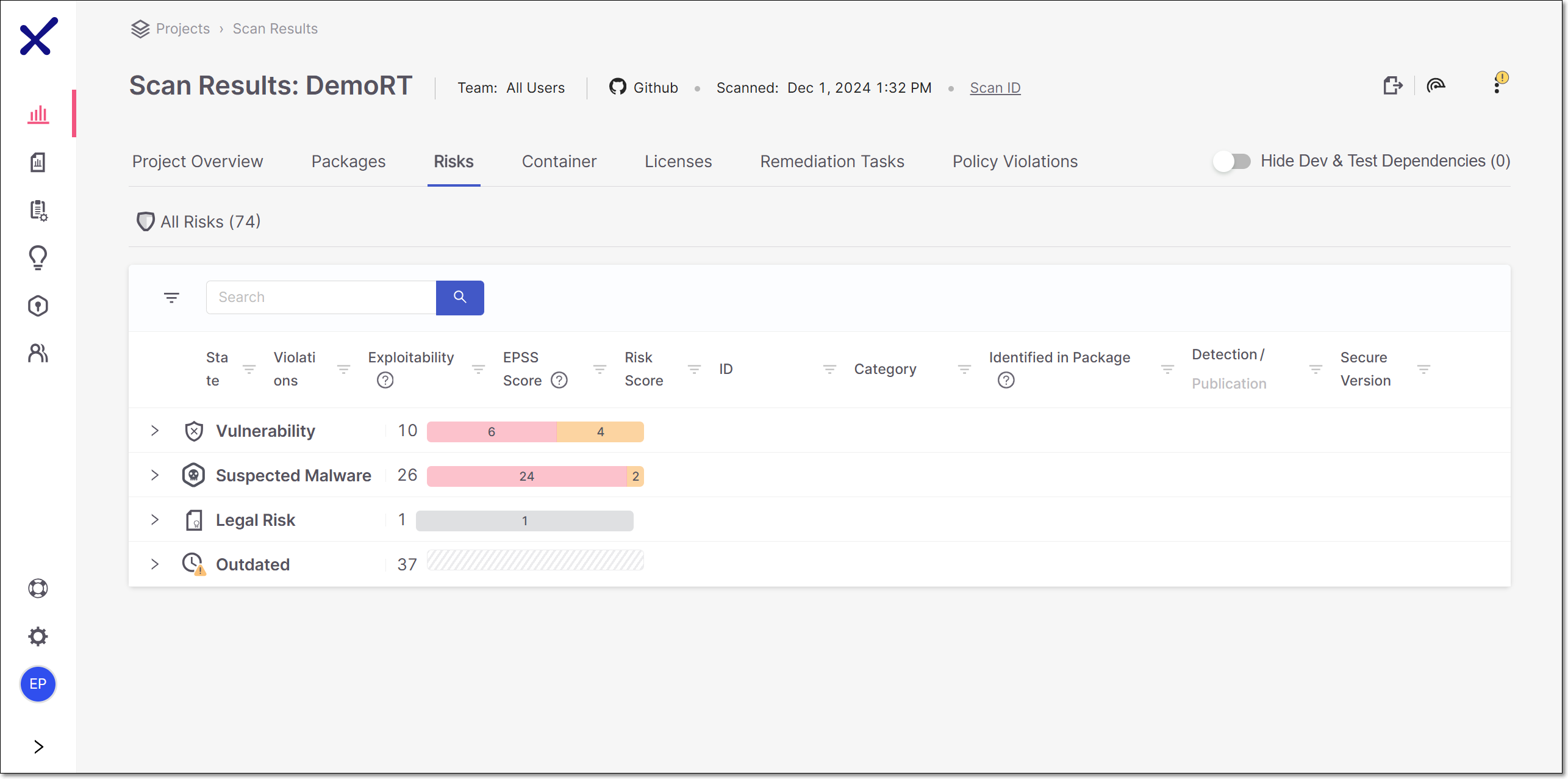
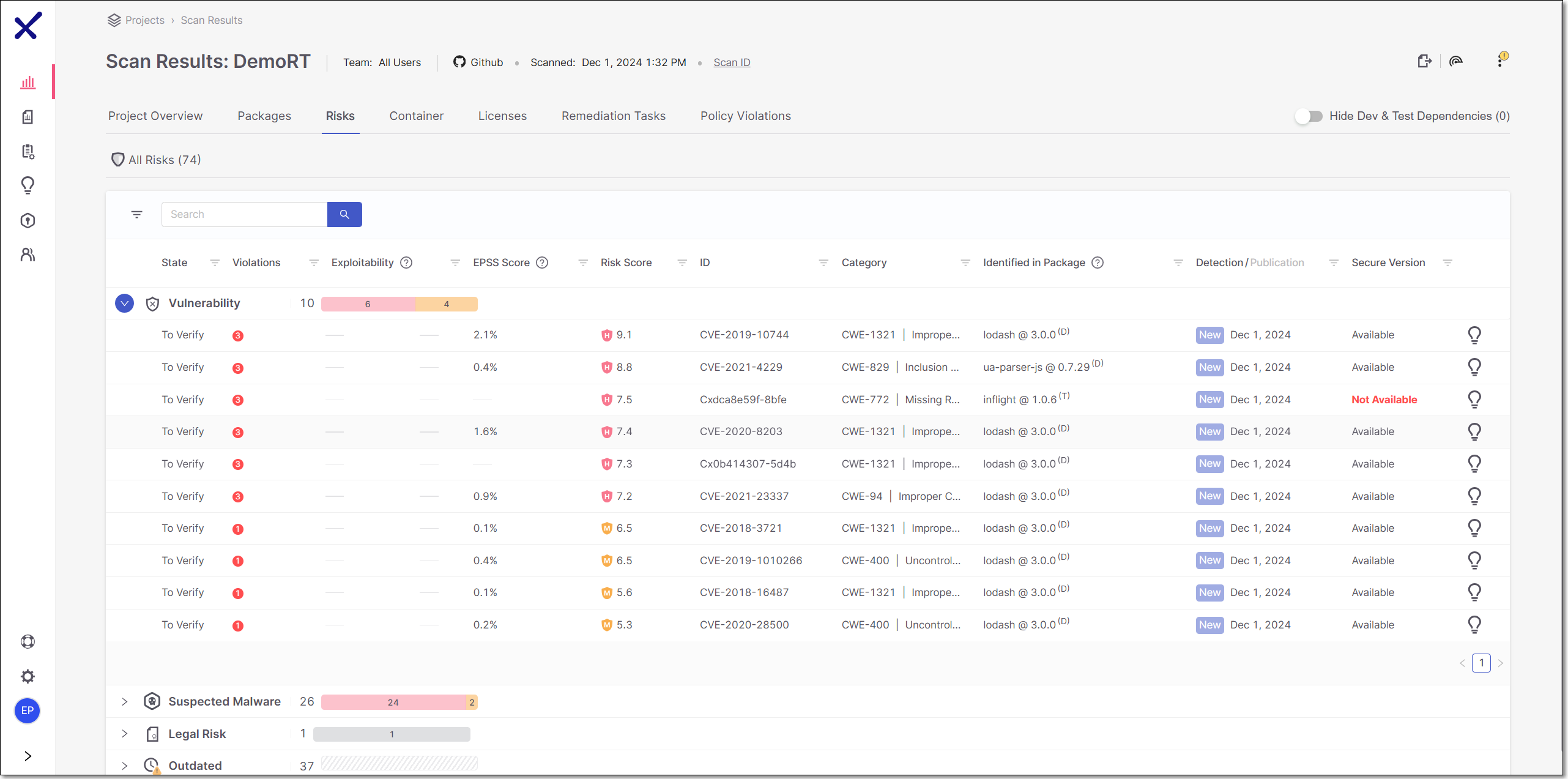
The All Risks sub-tab shows separate tabs for the different types of Risks (Vulnerability, Suspected Malware, Legal Risk and Outdated). Each tab shows the overall number of Risks for this type and the number of Risks for each risk level. Clicking on the arrow on the left of the tab expands a list below it to show all Risks of this type identified by this scan of your Project. For each Risk, info is shown about the nature of the Risk. You can search for specific Risks using the search box.
Notice
If a risk affects several packages in your Project, a separate record is listed for each instance of the risk.
You can also sort by column headers and set filters for each column.
 |
Clicking on the arrow on the left of the tab expands a list showing all of the risks of that type.
Notice
Risks that have been marked as Not Exploitable are shown with a strikethrough line and they aren't counted towards the total number of risks. However, changes to the summary counters only take effect when a subsequent scan or scan recalculation is run.
 |
The following table describes the info shown for each risk identified by this scan.
Notice
Not all columns are relevant for each type of risk.
Item | Description | Possible Values |
|---|---|---|
State | Indicates the state of this vulnerability for this project. | For vulnerability or suspected malware risks:
TipWhen the state is set as Not Exploitable, the risk is marked with a strikethrough line and the Risk Details page is grayed out.
|
Violations | Shows the number of violations of security policies that were assigned to this project. | |
Exploitability | Shows which exploitability indicators apply to this vulnerability. |
|
EPSS Score | The EPSS (Exploit Prediction Scoring System) is a risk score provided by First, indicating the likelihood of a vulnerability being exploited. The score is presented as a percentage, representing the likelihood of this vulnerability to be exploited within the next 30 days. Hovering over the score will display a percentile indicating the ranking of this risk relative to other vulnerabilities. | e.g., 2.1% |
Risk Score | Shows the the severity level of the vulnerability based on its CVSS score in the NVD, as well as the precise CVSS score. TipThe Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. |
TipFor Legal Risks, risks with UNKNOWN severity are shown in light grey. For more info see Severity Levels. |
ID | The ID of the CVE listing. The ID consists of the CVE prefix followed by the year that the CVE was discovered and the serial counter for that year's CVE listings. TipVulnerabilities discovered by the Checkmarx Vulnerability Research Team which are not catalogued as CVEs, are indicated by the “Cx” prefix. | e.g., CVE-2020-9488 |
Category | The category of the vulnerability. For CWEs, the CWE is given as well as a brief description of the vulnerability. | e.g., CWE-89|SQL Injection, Malicious, ChainJacking etc. |
Identified in Package | The name and version of the package in which the vulnerability was identified. In addition, an indication is shown for the type of dependency:
Results can be filtered by dependency type. | e.g., loadash @ 4.13.1 (T) |
Detection/Publication | Click on the desired header to alternate between the detection and publication dates.
| e.g., Nov 16, 2020 |
Secure Version | Indicates whether or not a remediated version of the package where this vulnerability was identified exists. TipIn the context of the Risks tab, a version is considered secure as long as this particular vulnerability is remediated, even if the package has other vulnerabilities. |
|
AppSec Knowledge Center | Click on the |  |
Risk Details Page
The Risk Details sub-tab shows detailed info about a specific Risk. The top info pane gives general info about the vulnerability, and the separate cards below it show detailed info about various aspects of the risks posed by the vulnerability.
The different risk types are:
Vulnerability - a vulnerability that can be exploited by an attacker. This includes vulnerabilities that have been published as CVEs as well as vulnerabilities identified by Checkmarx AppSec experts (i.e., Cx).
Suspected Malware - shows various types of suspected malware risks that affect the packages in your project, such as packages that are Malicious by design and packages that are vulnerable to ChainJacking attacks.
Notice
There are no Risk Details pages associated with Legal Risks or Outdated packages. Clicking on a Legal Risk opens the Licenses tab, filtered for the relevant license. Outdated packages aren’t clickable.
Each type of risk shows different cards on the details page. The different cards are described in the tables below.
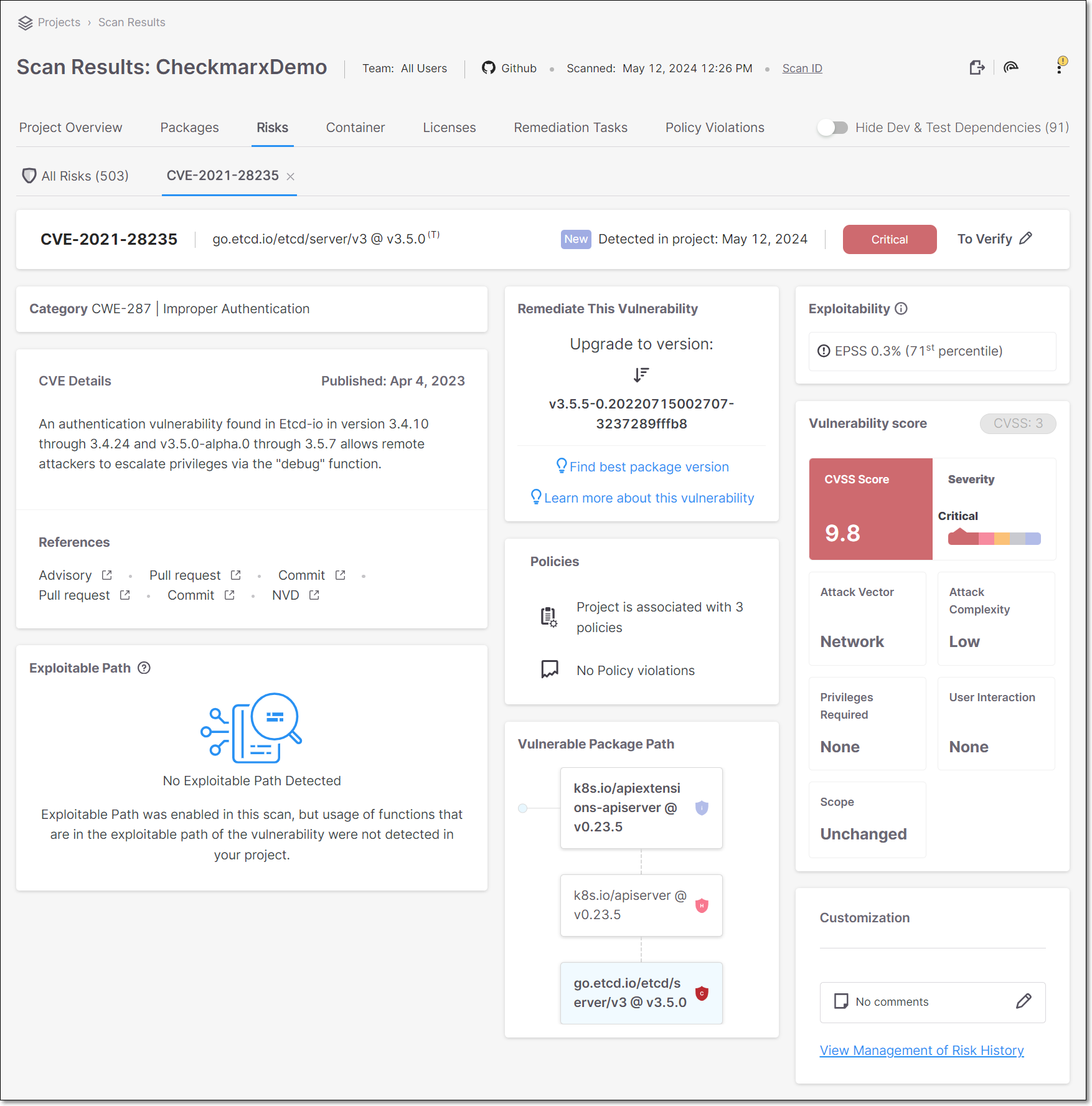 |
Vulnerability Details
Vulnerabilities are risks that can be exploited by an attacker. This includes vulnerabilities that have been published as CVEs as well as vulnerabilities identified by the Checkmarx Vulnerability Research Team (i.e., Cx).
Info Pane
 |
Item | Description | Possible Values |
|---|---|---|
ID | The ID of the CVE listing. The ID consists of the CVE prefix followed by the year that the CVE was discovered and the serial counter for that year's CVE listings. TipVulnerabilities discovered by the Checkmarx Vulnerability Research Team which are net yet catalogued as CVEs, are indicated by the “Cx” prefix. | e.g., CVE-2019-12384 |
Package | The name of the package in which the vulnerability was identified. | e.g., com.fasterxml.jackson.core:jackson-databind 2.9.8 |
Version | The version of the package where the vulnerability was identified. | e.g., 5.1.26 |
Exploitability | Shows which exploitability indicators apply to this vulnerability. |
|
Detected in Project | The date that the vulnerability was first identified in this project. | e.g., May 12, 2024 |
Rating | Shows the severity level of the vulnerability based on its CVSS score in the NVD, as well as the precise CVSS score. |
For more info about SCA risk severity, see here. |
Risk State | This indicates the current state of the vulnerability as determined by your AppSec team. All new risks are initially marked as To Verify. A user with |
TipWhen the state is set as Not Exploitable, the page is grayed out and the risk is marked with a strikethrough line on the All Risks tab. |
Vulnerability Details Sections
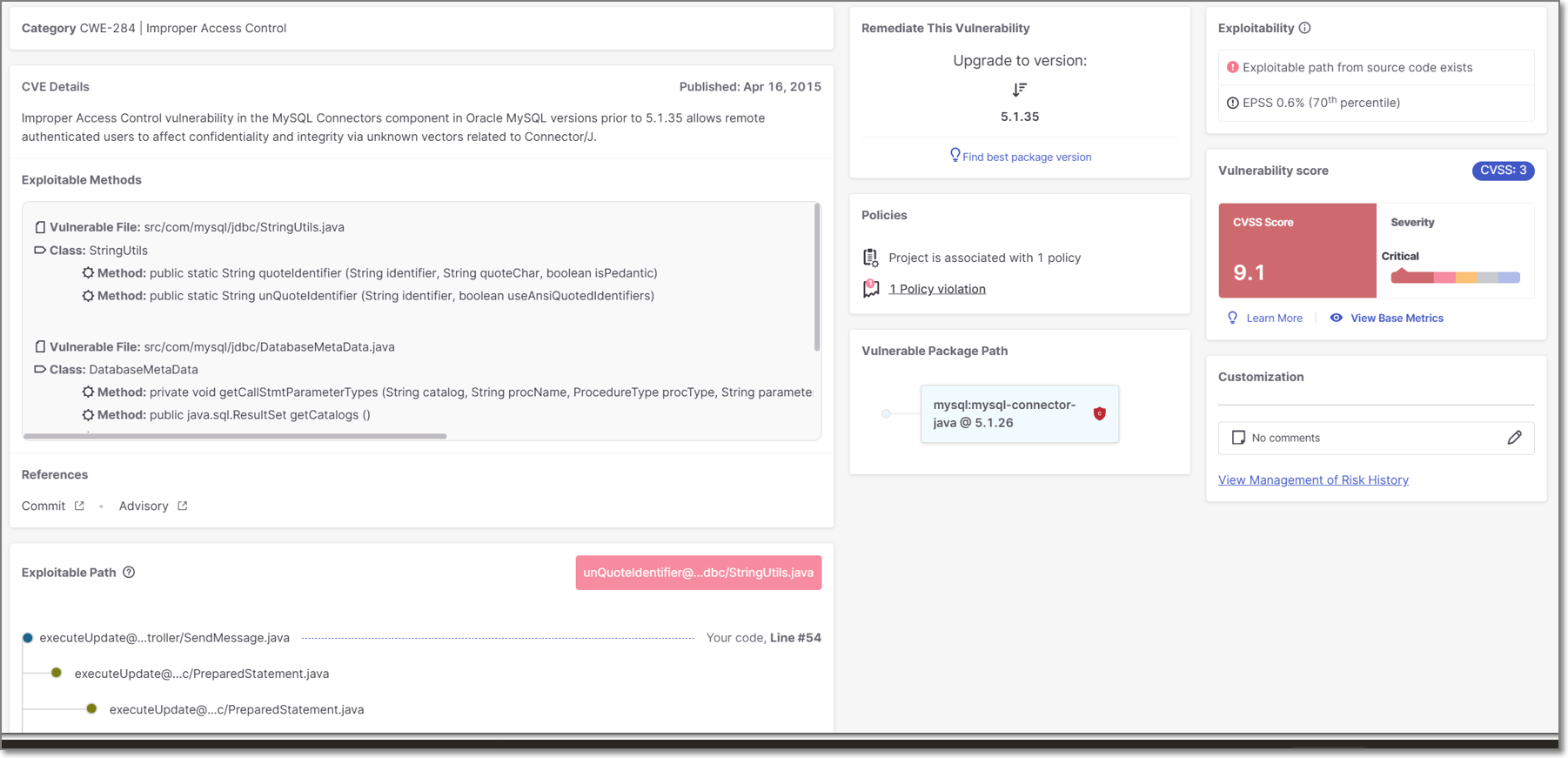 |
Item | Description |
|---|---|
Category | The ID and description of the CWE (Common Weakness Enumeration) listing. The ID consists of the CWE prefix followed by the serial counter. |
CVE Details | A description of the nature of the threat posed by the vulnerability and the date the vulnerabiliity was published in the NVD. |
Exploitable Methods | Details about the vulnerable methods that expose the vulnerability to exploitation. When the relevant details are available, we show the vulnerable file path, class, and method. This visibility increases transparency into how we evaluate exploitable paths, and provides actionable data for cases where full exploitable path analysis is not possible. |
References | Links to external resources about the vulnerability. Links are given for topics such as: Advisory, Commit, Release Notes, Issue etc. |
Exploitable Path | If a path was detected from your source code to the vulnerable method in the package, a map of the path is displayed. |
Remediate this Vulnerability | Recommended steps that should be taken to remediate this vulnerability. If available, a remediated version of the package is recommended for upgrade. Otherwise, the AI Package Finder button is shown that enables you to get AI generated suggestions for non-vulnerable replacement packages. TipThe recommended package version, is the minimum version that does not contain this particular vulnerability. To find the minimum version that doesn’t contain any vulnerabilities, click on Find best package version. |
Policies | The number of Policies the Project is assigned to and the number of Policy violations. |
Vulnerable Package Path | The vulnerable package is displayed in blue. If this is a transient dependency (i.e., it is accessed via other packages), then the full path by which the package is accessed is shown above it. You can click on any package shown in the path in order to open a new tab showing details for that package. TipFrequently, you can fix the vulnerabilities by updating the transient packages with their latest versions. |
Exploitability | Shows which exploitability indicators apply to this vulnerability. (KEV, POC, EPSS and Exploitable Path) |
Vulnerability Score | Shows the CVSS Version, Score, and Severity, as well as the components that make up the CVSS score including: Attack Vector, Confidentiality Impact, Attack Complexity, Integrity Impact, Authentication, and Availability Impact. For a full explanation of the metrics that make up the CVSS score, see CVSS Score Details. |
Customization | Displays comments regarding this vulnerability and a link to view the risk management history. |
CVSS Score Details
The metrics that are used for calculating the CVSS score are different for each version. Therefore, the metrics shown when you click on View Base Metrics on the Risk page differ according to the version. Additional information about CVSS score calculation is available here.
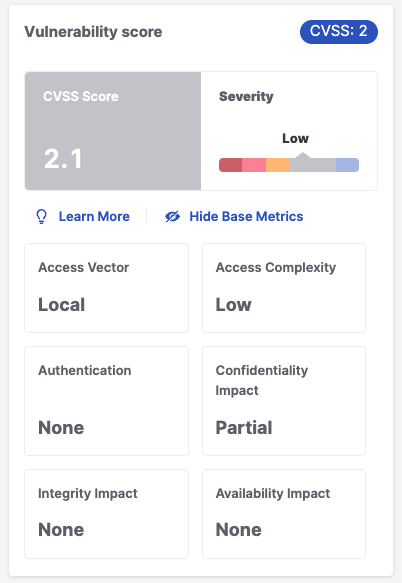
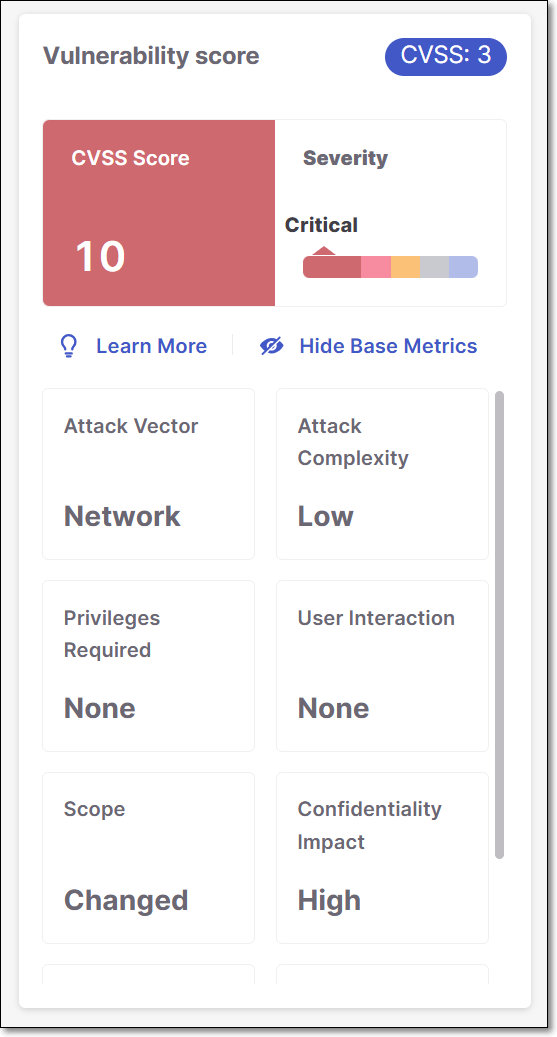
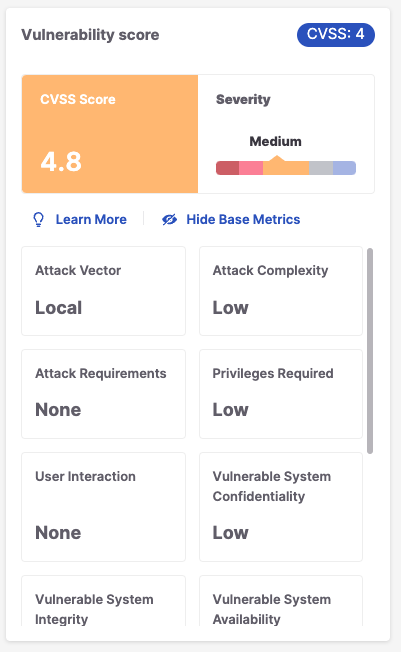
Detailed results for SCA vulnerabilities can be returned using the GET /results API. The results for each SCA vulnerability include a vulnerabilitiesDetails object. The attributes returned for this object differ depending on the CVSS version that is used for that vulnerability. You may need to adjust some of your workflows to accommodate the schema of the new type of results.
CVSS 2.0 | CVSS 3.1 | CVSS 4.0 |
|---|---|---|
"vulnerabilityDetails": { "cvssScore": 2.1, "cveName": "CVE-2015-3010", "cweId": "CWE-200", "cvss": { "score": 2.1, "version": 2, "severity": ["INFO", "NONE", "LOW", "MEDIUM", "HIGH"], "integrity": ["NONE", "PARTIAL", "COMPLETE"], "attackVector": ["LOCAL", "ADJACENT NETWORK", "NETWORK"], "availability": ["NONE", "PARTIAL", "COMPLETE"], "authentication": ["NONE", "SINGLE", "MULTIPLE"], "confidentiality": ["NONE", "PARTIAL", "COMPLETE"], "attackComplexity": ["LOW", "MEDIUM", "HIGH"], "exploitCodeMaturity": "3.9" } } | "vulnerabilityDetails": { "cvssScore": 5.5, "cveName": "CVE-2023-50120", "cweId": "CWE-835", "cvss": { "scope": ["CHANGED", "UNCHANGED"], "score": 5.5, "version": 3, "severity": ["INFO", "NONE", "LOW", "MEDIUM", "HIGH", "CRITICAL"], "integrity": ["NONE", "LOW", "HIGH"], "attackVector": ["NETWORK", "ADJACENT", "LOCAL", "PHYSICAL"], "availability": ["NONE", "LOW", "HIGH"], "confidentiality":["NONE", "LOW", "HIGH"], "userInteraction": ["NONE", "REQUIRED"], "attackComplexity": ["LOW", "HIGH"], "privilegesRequired": ["NONE", "LOW", "HIGH"], "exploitCodeMaturity": "3.9" } } | "vulnerabilityDetails": { "cvssScore": 4.800000190734863, "cveName": "CVE-2024-6064", "cweId": "CWE-416", "cvss": { "score": 4.8, "version": 4, "severity": ["INFO", "NONE", "LOW", "MEDIUM", "HIGH", "CRITICAL"], "attackVector": ["NETWORK", "ADJACENT", "LOCAL", "PHYSICAL"], "userInteraction": ["NONE", "PASSIVE", "REQUIRED"], "attackComplexity": ["LOW", "HIGH"], "attackRequirements": ["NONE", "PRESENT"] "privilegesRequired": ["NONE", "LOW", "HIGH"], "subsequentSystemIntegrity": ["NONE", "LOW", "HIGH"], "vulnerableSystemIntegrity": ["NONE", "LOW", "HIGH"], "subsequentSystemAvailability": ["NONE", "LOW", "HIGH"], "vulnerableSystemAvailability": ["NONE", "LOW", "HIGH"], "subsequentSystemConfidentiality": ["NONE", "LOW", "HIGH"], "vulnerableSystemConfidentiality": ["NONE", "LOW", "HIGH"] } } |
Examples of vulnerabilitiesDetails object for each CVSS version.
CVSS 2.0
"vulnerabilityDetails": {
"cvssScore" : 2.0999999046325684,
"cveName" : "CVE-2015-3010",
"cweId" : "CWE-200",
"cvss" : {
"score" : 2.1,
"version" : 2,
"severity" : "Low",
"integrity" : "NONE",
"attackVector" : "LOCAL",
"availability" : "NONE",
"authentication" : "NONE",
"confidentiality" : "PARTIAL",
"attackComplexity" : "LOW",
"exploitCodeMaturity" : "3.9"
}
}
CVSS 3.1
"vulnerabilityDetails": {
"cvssScore" : 7.5,
"cveName" : "CVE-2024-24265",
"cweId" : "CWE-401",
"cvss" : {
"scope" : "UNCHANGED",
"score" : 7.5,
"version" : 3,
"severity" : "High",
"integrity" : "NONE",
"attackVector" : "NETWORK",
"availability" : "HIGH",
"confidentiality" : "NONE",
"userInteraction" : "NONE",
"attackComplexity" : "LOW",
"privilegesRequired" : "NONE"
}
} CVSSS 4.0
"vulnerabilityDetails": {
"cvssScore" : 4.800000190734863,
"cveName" : "CVE-2024-6064",
"cweId" : "CWE-416",
"cvss" : {
"score" : 4.8,
"version" : 4,
"severity" : "Medium",
"attackVector" : "LOCAL",
"userInteraction" : "NONE",
"attackComplexity" : "LOW",
"attackRequirements" : "NONE",
"privilegesRequired" : "LOW",
"subsequentSystemIntegrity" : "NONE",
"vulnerableSystemIntegrity" : "LOW",
"subsequentSystemAvailability" : "NONE",
"vulnerableSystemAvailability" : "LOW",
"subsequentSystemConfidentiality" : "NONE",
"vulnerableSystemConfidentiality" : "LOW"
}
}Suspected Malware Details
Suspected Malware includes various types of risks that affect the packages in your project, such as packages that are Malicious by design and packages that are vulnerable to ChainJacking attacks.
Info Pane
 |
Item | Description | Possible Values |
|---|---|---|
ID | An internal ID starting with the “Cx” prefix that was assigned to this risk by the Checkmarx Vulnerability Research Team. | e.g., Cx27b685d0-978d |
Package | The name of the package in which the vulnerability was identified. | e.g., com.fasterxml.jackson.core:jackson-databind 2.9.8 |
Version | The version of the package where the vulnerability was identified. | e.g., 5.1.26 |
Risk Level | The severity level of the vulnerability, based on its CVSS score in the CVE database. Malicious (suspected malware) packages are labeled Malicious and the |
For more info see Severity Levels. |
Risk State | This indicates the current state of the suspected malware Risk as determined by your AppSec team. All new risks are initially marked as To Verify. A user with |
TipWhen the state is set as Not exploitable, the page is grayed out and the risk is marked with a strikethrough line on the All Risks tab. |
Suspected Malware Details Sections
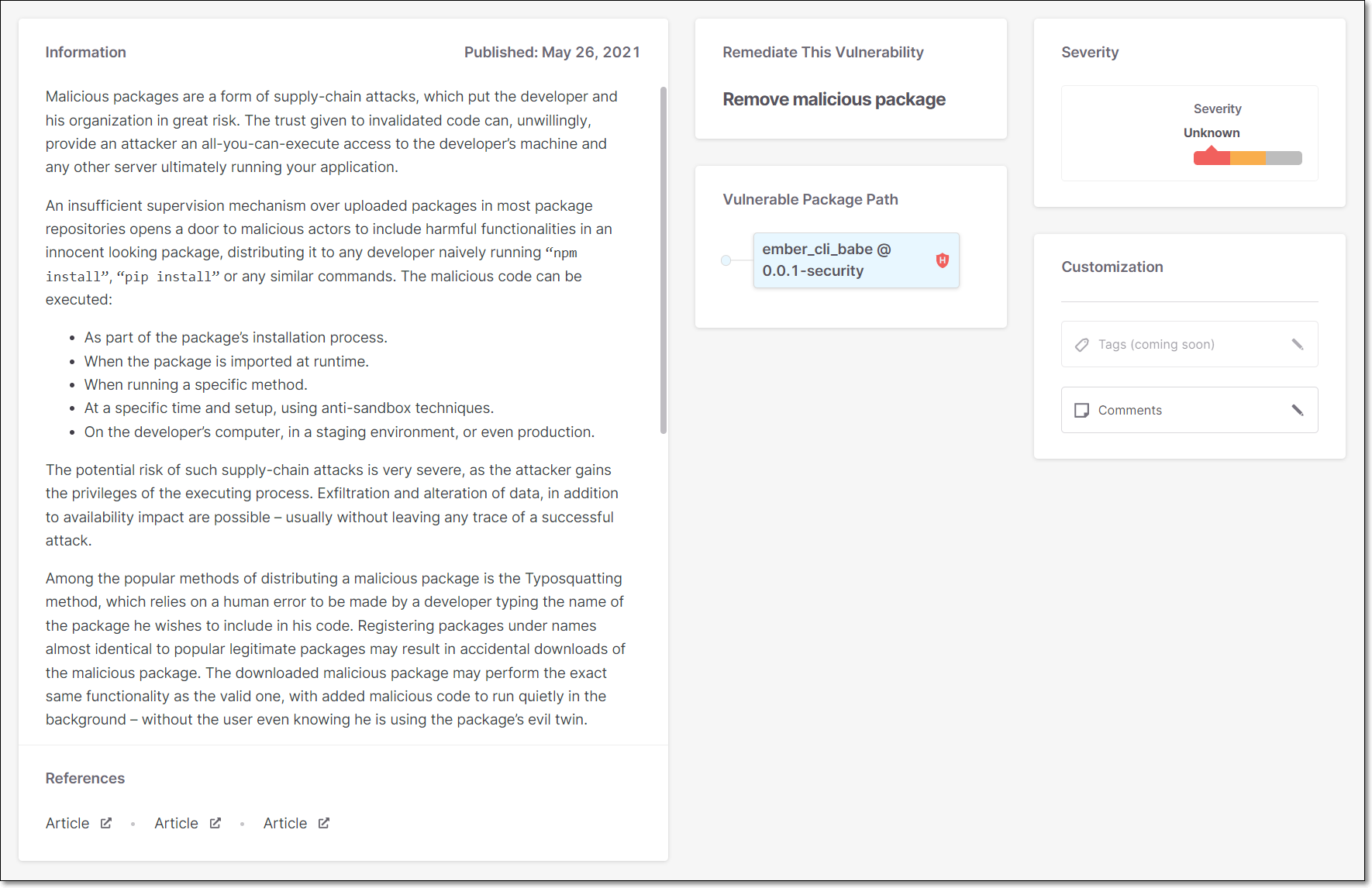 |
Item | Description |
|---|---|
Information | A description of the nature of the threat posed by the suspected malware and the date the suspected malware was published on the NVD. |
References | Links to external resources about the risk. Links are given for topics such as: Article, etc. |
Remediate this Vulnerability | Recommended steps that should be taken to remediate this vulnerability. |
Policies | The number of Policies the Project is assigned to and the number of Policy violations. |
Vulnerable Package Path | The vulnerable package is displayed in blue. If this is a transient dependency (i.e., it is accessed via other packages), then the full path by which the package is accessed is shown above it. You can click on any package shown in the path in order to open a new tab showing details for that package. TipFrequently, you can fix the vulnerabilities by updating the transient packages with their latest versions. |
CVSS/Risk Score | Shows the CVSS Version, Score, and Severity. For a full explanation of the metrics that make up the CVSS score, see section 2 of this article. |
Container Tab
In addition to scanning the packages in your source code itself, Checkmarx SCA also scans the containers (i.e., Docker image files) on which your source code runs. Checkmarx SCA identifies each of the Docker files being used, extracts all layers of each Image file and identifies the packages used by each layer.
The Container tab shows the container packages identified in your project and the vulnerabilities associated with them.
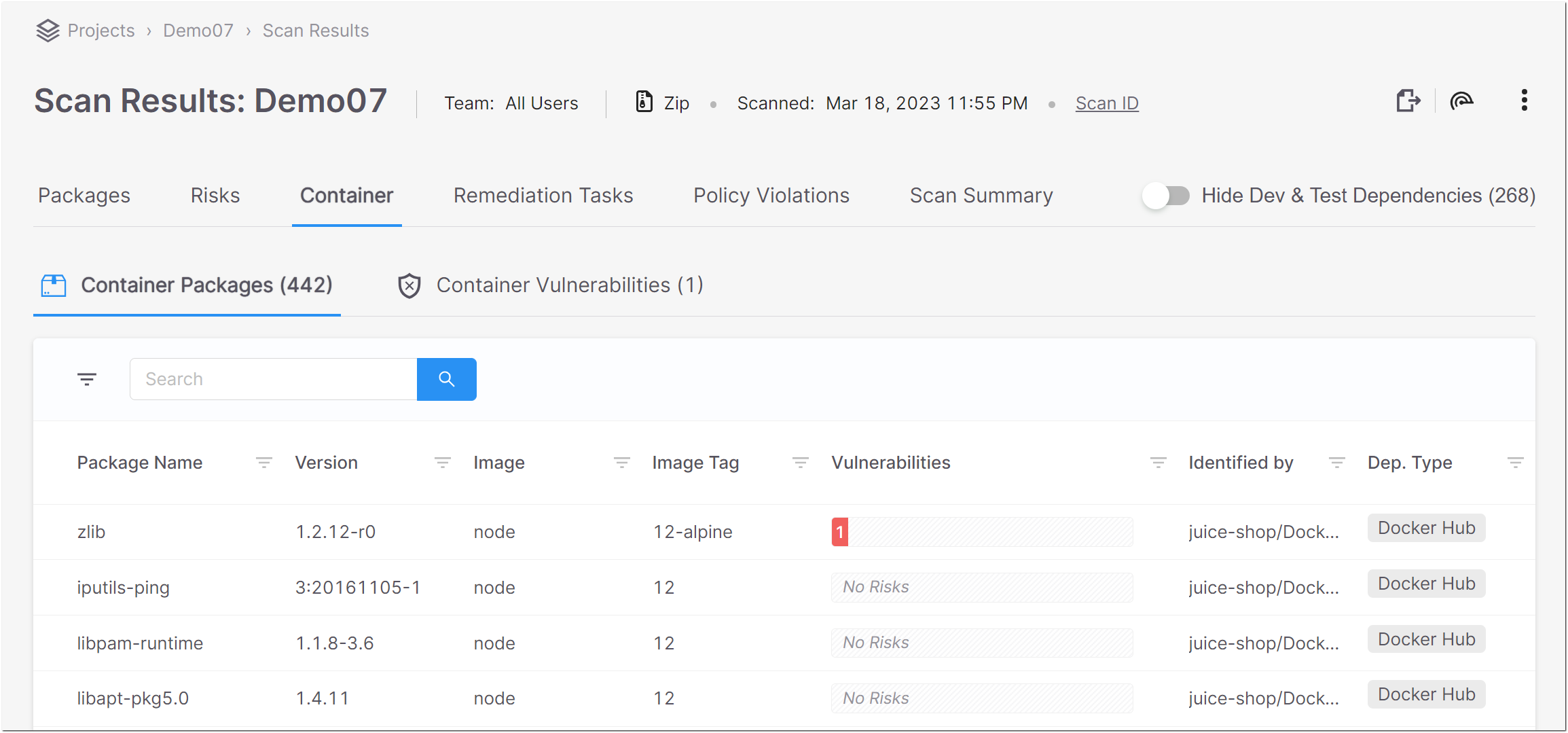
The Container tab contains two sub-tabs:
Container Packages – shows a list of all of the packages identified in the container images.
Container Vulnerabilities – shows a list of all of the vulnerabilities associated with the container packages.
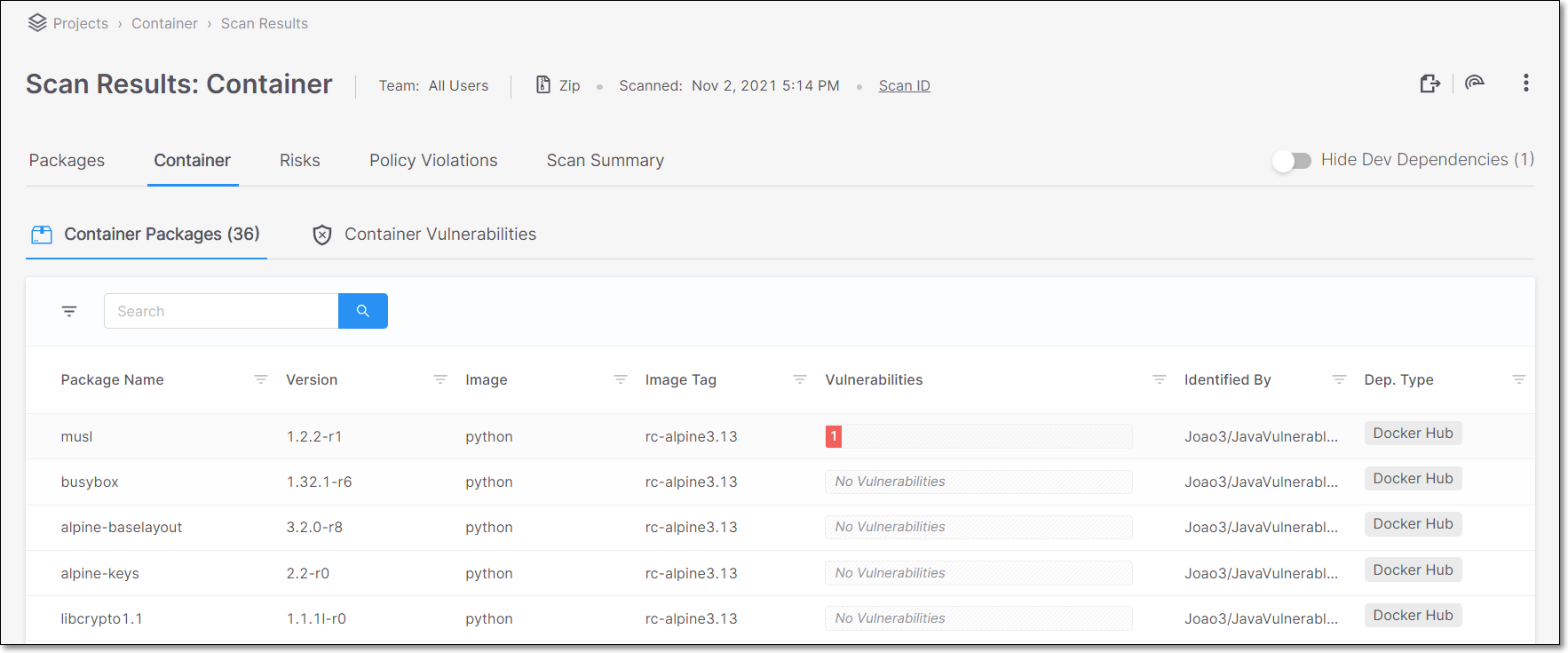
The Container Packages sub-tab shows a list of all of the packages identified in the container images. For each container package, info is shown about the risks related to that package. You can search for specific packages and images using the search box.
You can also sort by column headers and set filters for each column.
 |
The following table describes the info shown for each package identified in the containers.
Item | Description | Possible Values | |
|---|---|---|---|
Package Name | The name of the package. | e.g., musl | |
Version | The version of the package. | e.g., 1.2.2-r1 | |
Image | The name of the image that was scanned. | e.g., python | |
Image Tag | The version of the image. | e.g., rc-alpine3.13 | |
Malicious Package | Indicates whether or not the package is designated as "malicious" in the Checkmarx database. For unsupported package types (e.g., OS related packages), "Unknown" is shown. |
| |
Vulnerabilities | A color coded bar graph indicating the number of vulnerabilities of each severity level. | e.g.,
| |
Identified By | The path to the Docker file in which the specific image is found. (Hover to view the entire path.) | e.g., Joao4/JavaVulnerableLab-dockerfile/JavaVulnerableLab-master/dockerfile1/Dockerfile | |
Dep. Type | The repository in which the image is located. | e.g., Docker Hub |
The Container Vulnerabilities sub-tab shows a list of all of the vulnerabilities associated with the container packages. Detailed information is shown for each vulnerability. You can search for specific vulnerabilities and packages using the search box.
You can also sort by column headers and set filters for each column.
You can click on a vulnerability to open a new tab showing additional info about the vulnerability.
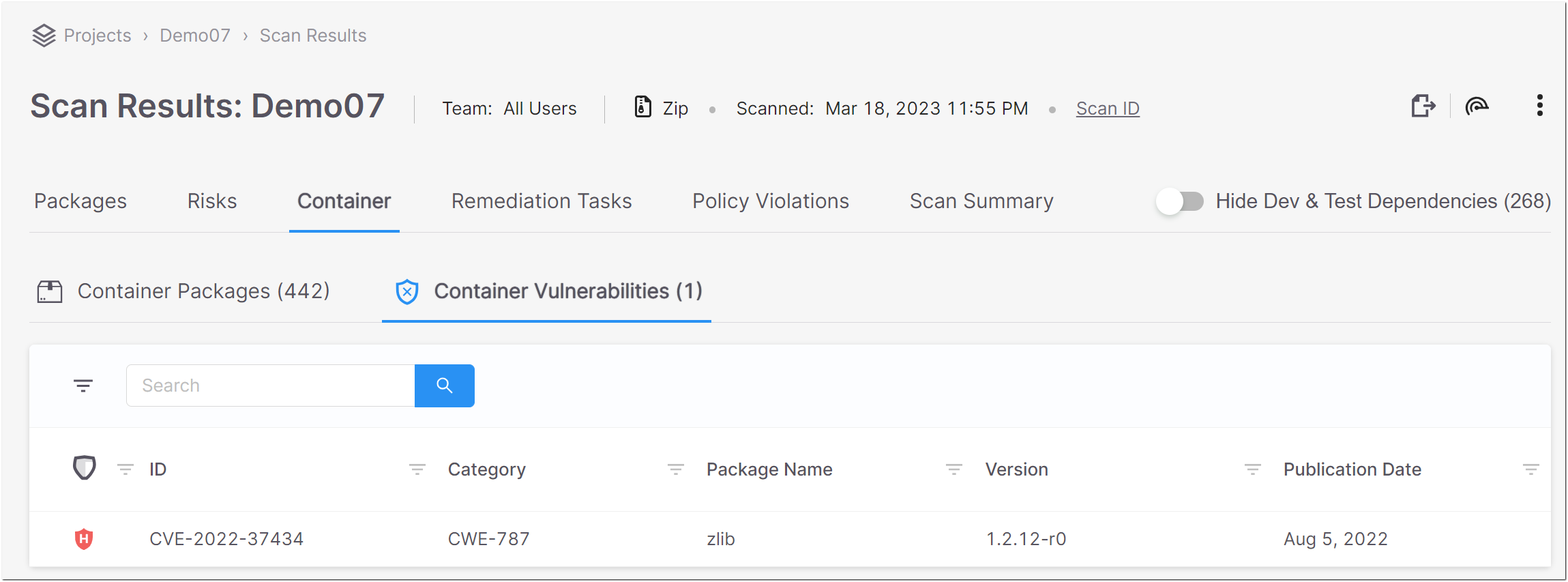
Notice
Container vulnerabilities for which the Category is "unknown" are marked as Low severity. Also, these vulnerabilities are only shown in the summary table, but you can't drill down to view the details page, since there are no details that we can provide.
The following table describes the info shown for each vulnerability that was identified in the containers.
Item | Description | Possible Values |
|---|---|---|
Risk Level | The severity level of the vulnerability. |
For more info see Severity Levels. |
ID | The ID of the CVE listing. The ID consists of the CVE prefix followed by the year that the CVE was discovered and the serial counter for that year's CVE listings. | e.g., CVE-2020-9488 |
Category | The category of the vulnerability. | e.g., CWE-20 |
Package Name | The name of the package in which the vulnerability was identified. | e.g., musl |
Version | The version of the package in which the vulnerability was identified. | e.g., 1.2.2-r1 |
Publication Date | The date the vulnerability was published in the NVD. | e.g., Nov 16, 2020 |
Licenses Tab
The Licenses tab shows info about all of the licenses that are associated with the open source packages used by your project.
Notice
This page shows all licenses, even those that don't pose any particular legal risk. All license that pose a specific legal risk are shown in the Legal Risks section on the Risks tab.
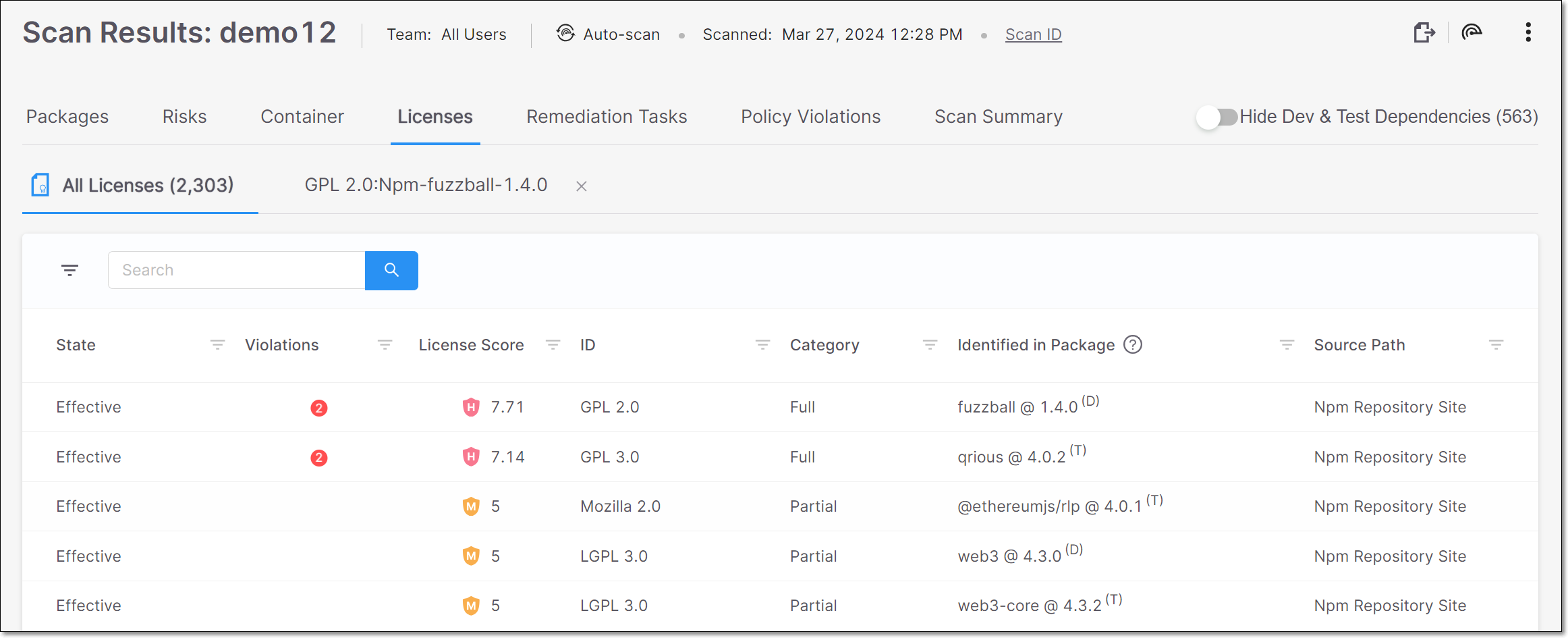
The Licenses tab contains sub-tabs that show two types of pages:
All Licenses – shows a list of all licenses associated with the open source packages identified in this scan.
License Details – shows detailed info about a specific license. Click on a row in the All Licenses tab to access this page.
You can navigate between the various tabs that you have opened.
All Licenses Page
The All Licenses sub-tab shows a list of all licenses associated with the open source packages identified in this scan. A separate row is shown for each license that applies to a particular package version. Therefore, if a license applies to multiple packages or package versions, then a separate row will be shown for each instance.
You can also sort by column headers and set filters for each column.
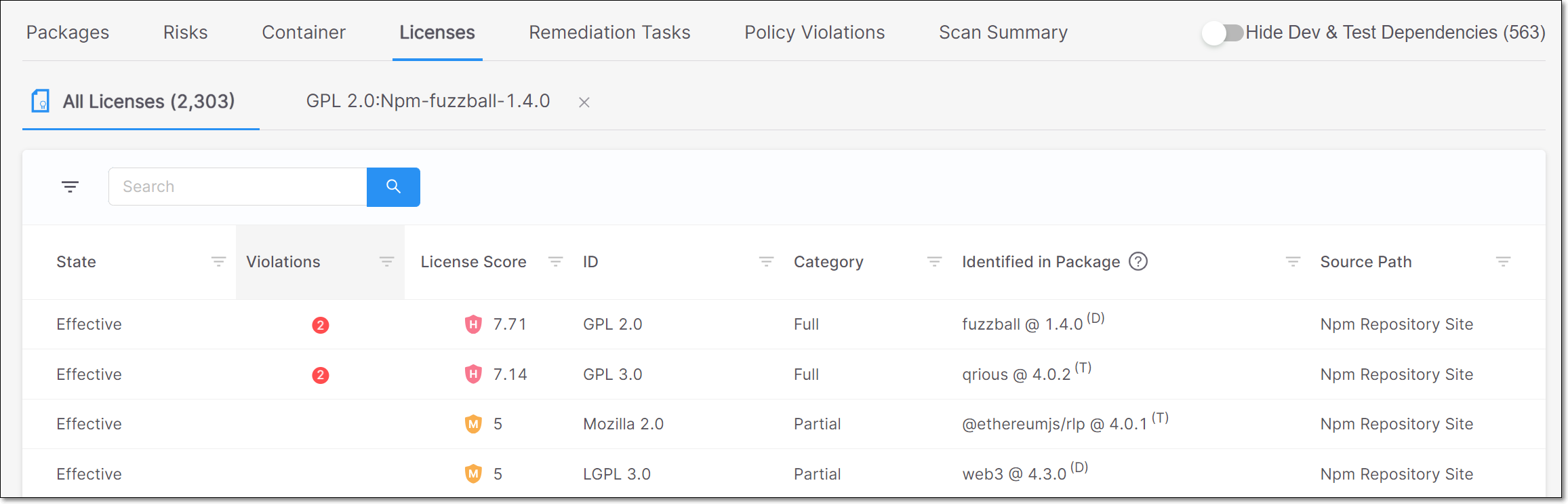
The following table describes the info shown for each license identified by this scan.
Item | Description | Possible Values |
|---|---|---|
State | Indicates whether or not this license is the "effective" license for your organization's use of this package. TipA license that was identified from a reliable source and is the sole license for the package is automatically marked as Effective. Otherwise it is marked as Not Effective by default and it can be manually changed to Effective. |
|
Violations | If the license is associated with one or more Policy violations, then number of policy violations is shown in red, see Policy Management. Hover over the number to view additional details. | e.g., |
License Score | Shows a score indicating the overall risk level associated with this license. TipIf this isn't the effective license for this package, then a high license score doesn't necessarily pose a legal risk. | |
ID | The name of the license | e.g., GPL 3.0, MIT etc. |
Category | The category of the license. |
|
Identified in Package | The name and version of the package that the license is associated with. In addition, an indication is shown for whether this is a direct or transitive dependency (D or T). Results can be filtered by Direct/Transitive. | e.g., loadash @ 4.13.1 (T) |
Source Path | The source from which the license was identified. | e.g., Manifest File, Npm Repository Site, Official Website, Statically Observed etc. TipThe category "Statically Observed" indicates that the license was identified in the source code (e.g., README files) using regex and other identification methods. |
License Details Page
This tab shows detailed information about a specific license, including the Legal Risks relating to the license.
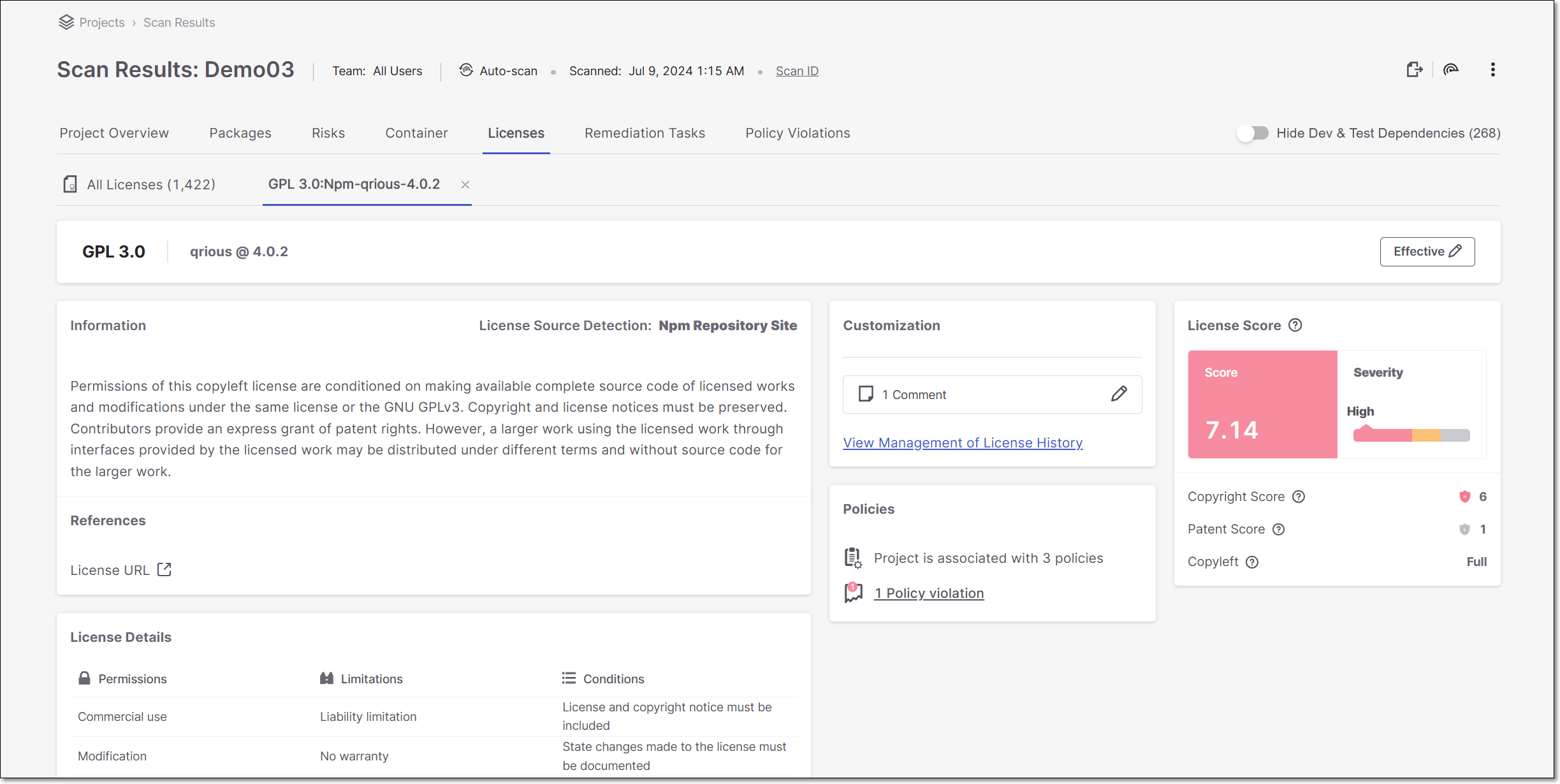
Info Pane
 |
Item | Description | Possible Values |
|---|---|---|
ID | The name of the License. | e.g., MIT |
Package | The name and version of the package that the license is associated with. | e.g., Fuzzball@1.4.0 |
State | The current state of the license. |
|
Legal Risk Details Sections
Item | Description |
|---|---|
Information | The source of the license detection followed by a description of the nature of the threat posed by the legal risk. |
References | Links to external resources about the vulnerability. Links are given for topics such as: License URL, etc. |
Customization | View state changes and comments for this license. An admin user can mark a license as “Effective” for this package (i.e., if they intend to consume this package in accordance with the licensing restrictions of this license.). |
Policies | The number of Policies the Project is assigned to and the number of Policy violations. |
Legal Score | Shows the License Score and Severity, as well as the components that make up the License score including: Copyright Risk, Patent Risk and Copyleft. For an explanation on the calculation of these scores, see below. |
License Details | Additional details about the terms of use of the license. This is divided into sections for Permissions, Limitations and Conditions. |
Understanding the License Score Section
The License Score pane shows the overall License Score and severity as well as information about specific license risk characteristics. The following table explains these items:
Notice
The License Score represents the level of risk associated with using a package under that license. However, the license doesn't pose an actual risk to your project unless you are actually using the package under that license (i.e., it is your Effective license).
Field | Value type and range | Details |
|---|---|---|
Copyright Risk Score | A number between 1 and 7 | The score is defined as follows:
TipThe Legal Risk calculation is based on the copyright risk score, where Level 1-3 is considered as a low risk, Level 4-5 as a medium risk, and Level 6-7 as a high risk. |
Patent Risk Score | A number between 1 and 4 Sometimes represented as multiplications of 20, since in CxOSA is presented on a scale of 1-100 | Ranks the license based on
|
Copyleft | One of the following: Full, Partial, No | Copyleft is a property of the license that means that the package is free to use, but it is forbidden to make it proprietary. A copyleft license is also viral since any work containing a package that has a copyleft-license must also retain this property. The valid values are described as follows:
|
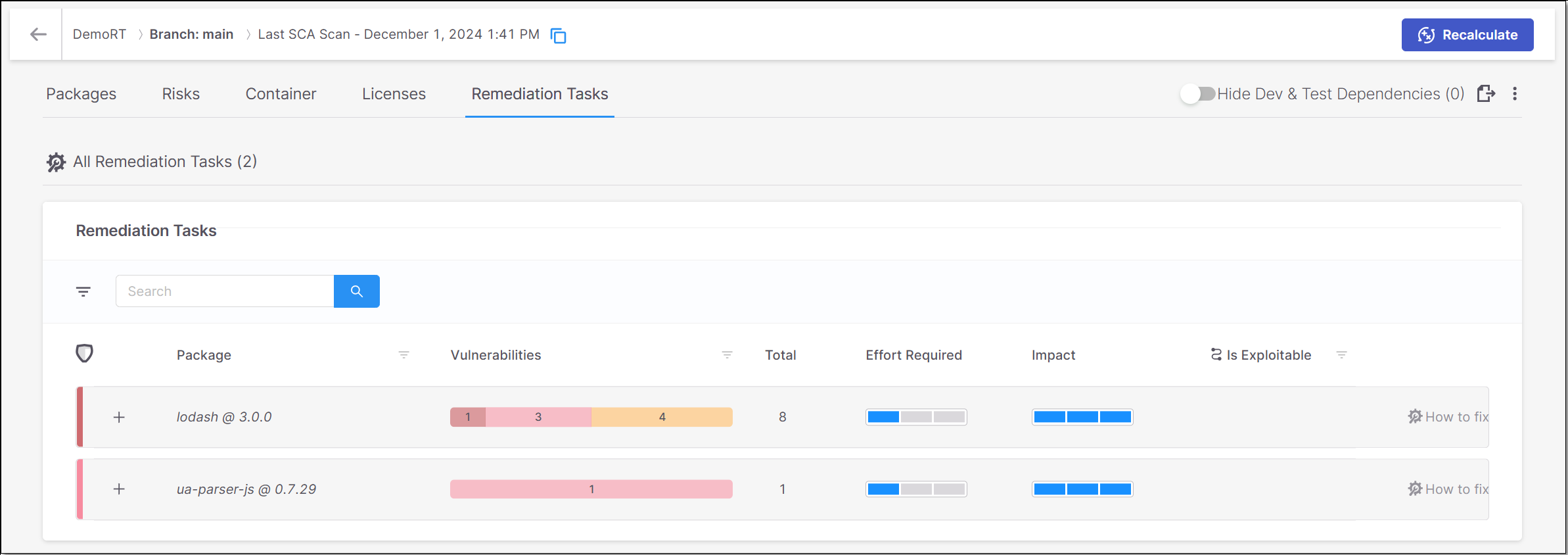
Remediation Tasks Tab
The Remediation Tasks tab shows detailed information about specific remediation tasks that Checkmarx recommends implementing for your Project. These tasks involve replacing vulnerable packages in your project with non-vulnerable versions of those packages.
 |
Notice
Remediation tasks are currently supported only for JavaSript npm packages and for Nuget packages with .csproj manifest files, otherwise this tab isn't shown.
The Remediation Tasks tab contains sub-tabs that show two types of pages:
All Remediation Tasks – shows a list of remediation tasks that are recommended for this Project, with general info about each task.
Task Details – shows detailed info about a specific task. The task details tab is opened by clicking on the How to fix button in a task row in the All Remediation Tasks sub-tab.
You can navigate between the various tabs that you have opened.
All Remediation Tasks
The All Remediation Tasks sub-tab shows a list of remediation tasks that are recommended for this Project.
Notice
Each task relates to a specific direct package in your project.
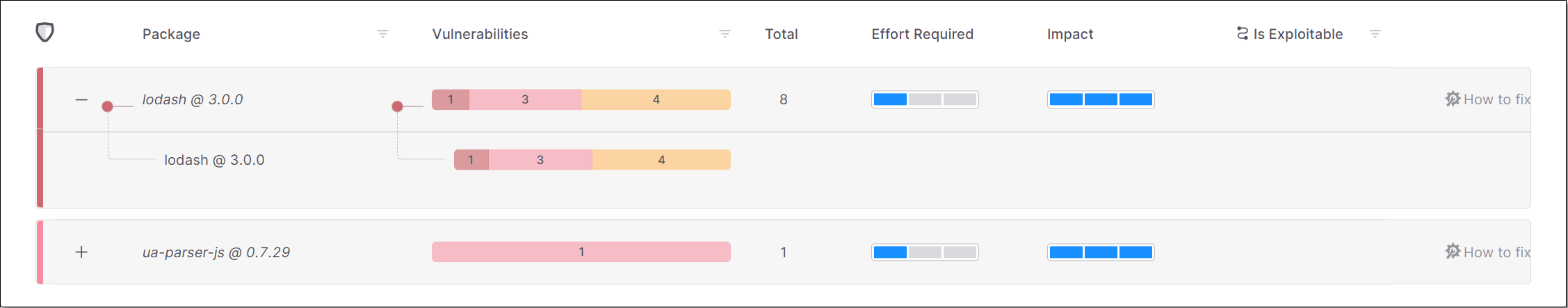
The data shown for each task relates to the vulnerabilities identified in the direct package as well as in the transitive dependencies associated with it. You can click on the “+” button for a task to expand the view of that task to show the transitive dependencies called by the package. The number of vulnerabilities of each severity level is shown for each transitive package.
 |
The following table describes the info shown for each task:
Parameter | Description |
|---|---|
+/- Button | Expand the display to show the transitive packages or collapse the display to show only the direct package. |
Package | The name of the package and its version number. |
Vulnerabilities | The number of vulnerabilities of each severity level in the package. |
Total | The total number of vulnerabilities in the package. |
Effort Required | An assessment of the degree of effort required to implement the recommended remediation task, e.g., if it requires fixing broken API methods. |
Impact | An assessment of the impact that the remediation task will have on your Project, i.e., the extent to which the procedure will remove risks from your Project. |
Is Exploitable | Indicates whether the vulnerabilities in this package are exploitable in the context of your Project. TipThis data is only shown for scans which ran using the Exploitable Path feature. |
“How to fix” button | Click on this button to open a new sub-tab showing details about this remediation task. |
Remediation Task Details
The Remediation Task Details sub-tab shows detailed info about a specific remediation task.
Notice
Each task relates to a specific direct package in your project.
The info on this screen is shown in the following panes.
Overview - shows key metrics for the remediation task.
Summary - shows general info about the remediation task.
Remediation Impact - shows a comparison between the current vulnerabilities and the vulnerabilities that will remain after remediation.
Developer Walkthrough - shows a breakdown of the steps that need to be taken to remediate this package.
Overview
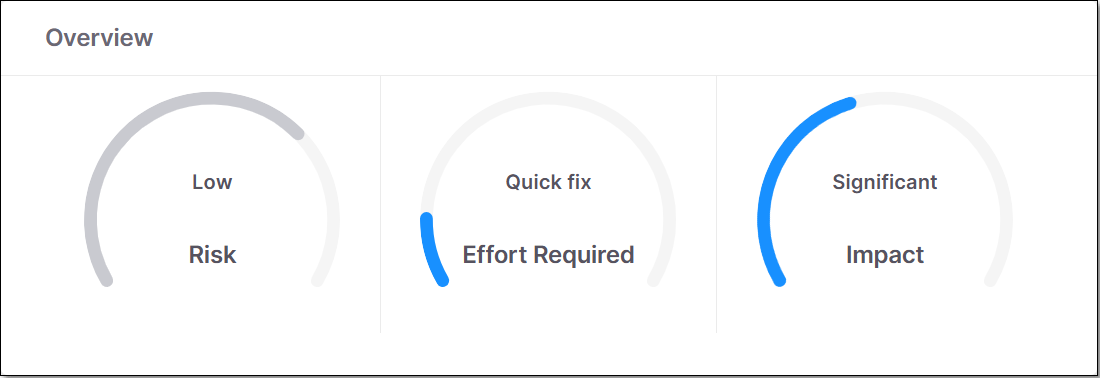 |
This pane shows gauge widgets indicating the overall risk level for the specified package, the effort required to implement the suggested remediation procedure and the impact of remediation.
Summary
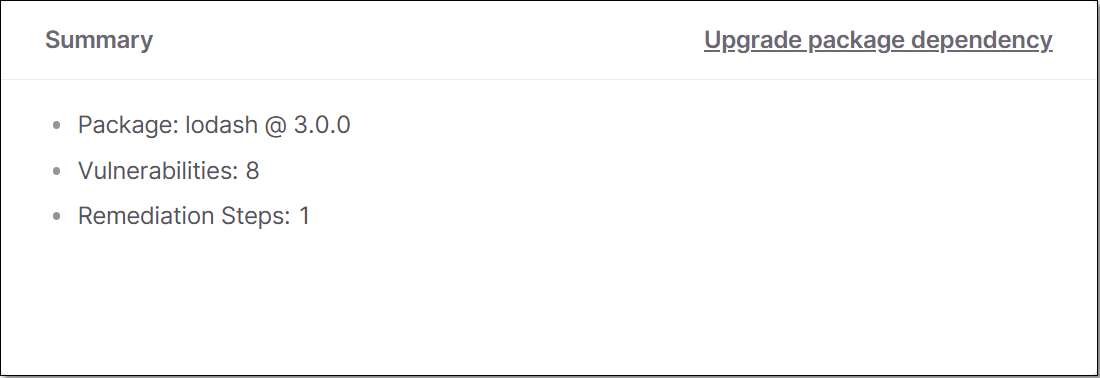 |
This pane shows a summary of the remediation task, including the package name, number of vulnerabilities and total number of remediation steps.
Remediation Impact
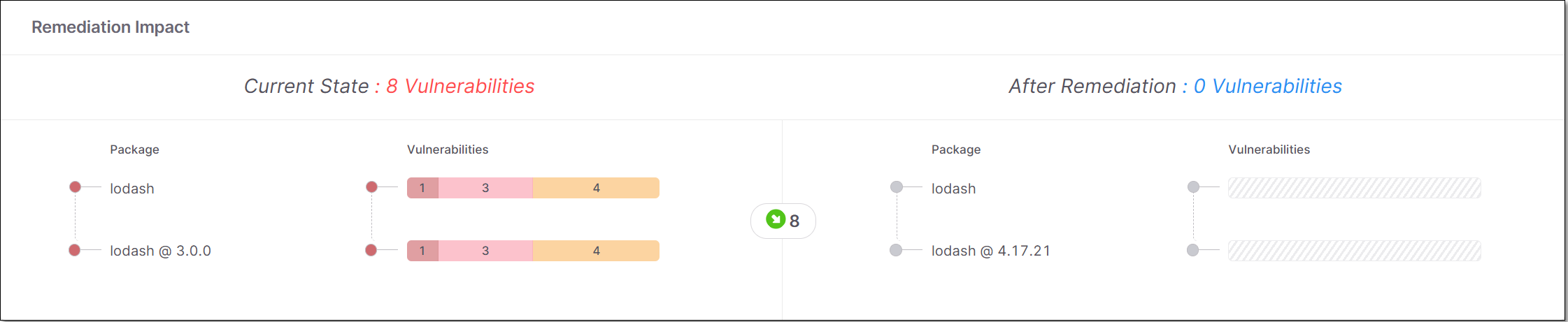 |
This pane shows a side-by-side comparison between the vulnerabilities currently in the direct and transitive dependencies and the vulnerabilities that will remain after remediation.
Note
Checkmarx SCA shows recommendations to upgrade each transitive dependency to the next suitable version, even if the current version doesn't have vulnerabilities. You should use your judgement to decide whether the benefit of upgrading is worth the effort of ensuring compatibility of the new version.
Developer Walkthrough
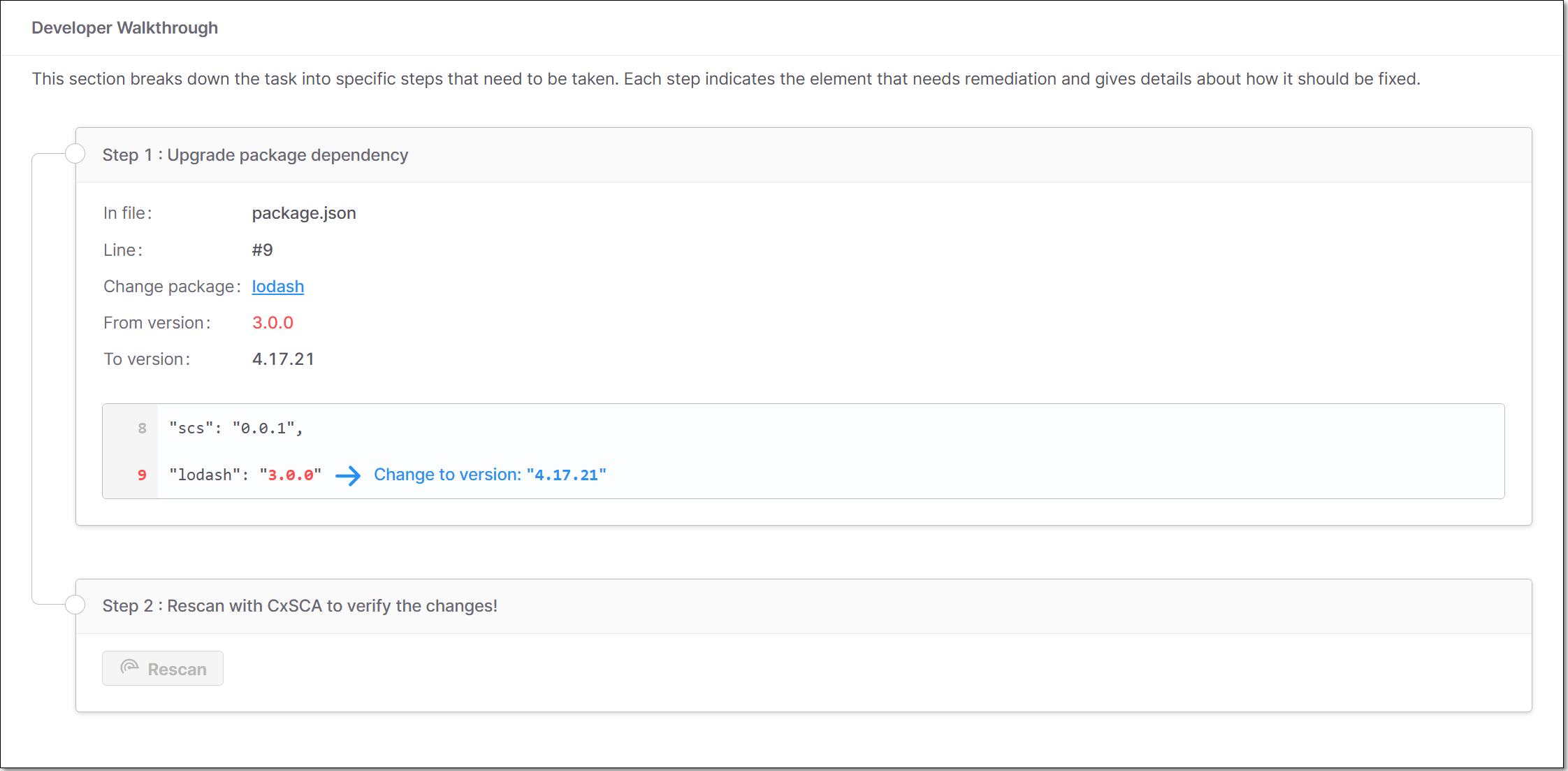 |
This section breaks down the task into specific steps that need to be taken. Each step indicates the element that needs remediation and gives details about how it should be fixed. There are three types of steps:
Upgrade package dependency - indicates the direct package that needs to be upgraded, where it appears in your code, and which version it should be upgraded to.
Add package dependency - indicates a specific version of a package that needs to be added to your manifest file (for transitive dependencies).
Notice
Recommended steps for remediating transitive vulnerabilities are given for each package independently. We recommend a secure version of the package that can be added to the manifest file in order to ensure that only that version will be used.
In some cases it may be possible to remediate transitive dependencies by upgrading the direct dependency to a version that references a newer, secure version. For Maven packages, the Maven repository shows the transitive package versions referenced by each package.
Fix broken API methods - shows each of the API methods that was broken and which upgrade caused the API to break. Fix broken API methods is shown as a sub-step under the “Upgrade package dependency” step that causes the broken method.
Note
Broken methods are only identified in scans for which the Exploitable Path feature is run.
Checkmarx SCA identifies broken API methods by comparing the number of parameters used in the public method for the new package with the number of parameters used for the original package. If the number of parameters is different, then we notify of the need to fix the API method.
Policy Violations Tab
Users can create security Policies in Checkmarx SCA. These Policies comprise a series of rules that define a custom threshold for compliance. These Policies can be applied to Projects so that when a scan identifies risks that exceed the specified threshold, a Policy Violation is registered. For more information about Policies, see Policy Management.
The Policy Violations tab shows info about all Policies that were violated by the scan.
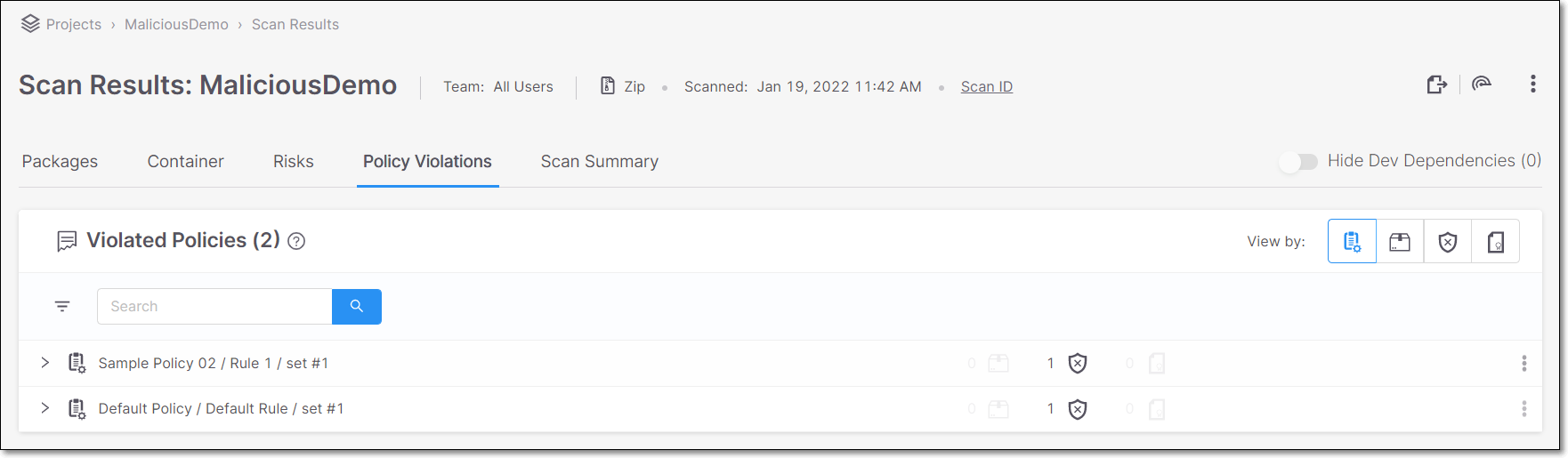 |
The header bar shows the total number of violated Policies. You can search for a specific item using the search box.
The results are grouped by a series of elements in an expandable tree structure. You can change the primary grouping of the Policies to be viewed by Policy’s set of Conditions (default), Package Instance, Vulnerability, Supply Chain, or License.
Clicking on the top level grouping expands the sub-groupings underneath. For example, when results are grouped by Policy Conditions, clicking on a Policy condition shows all of the packages that violate the Policy, and clicking on a package shows the list of vulnerabilities in that package that violate the Policy.
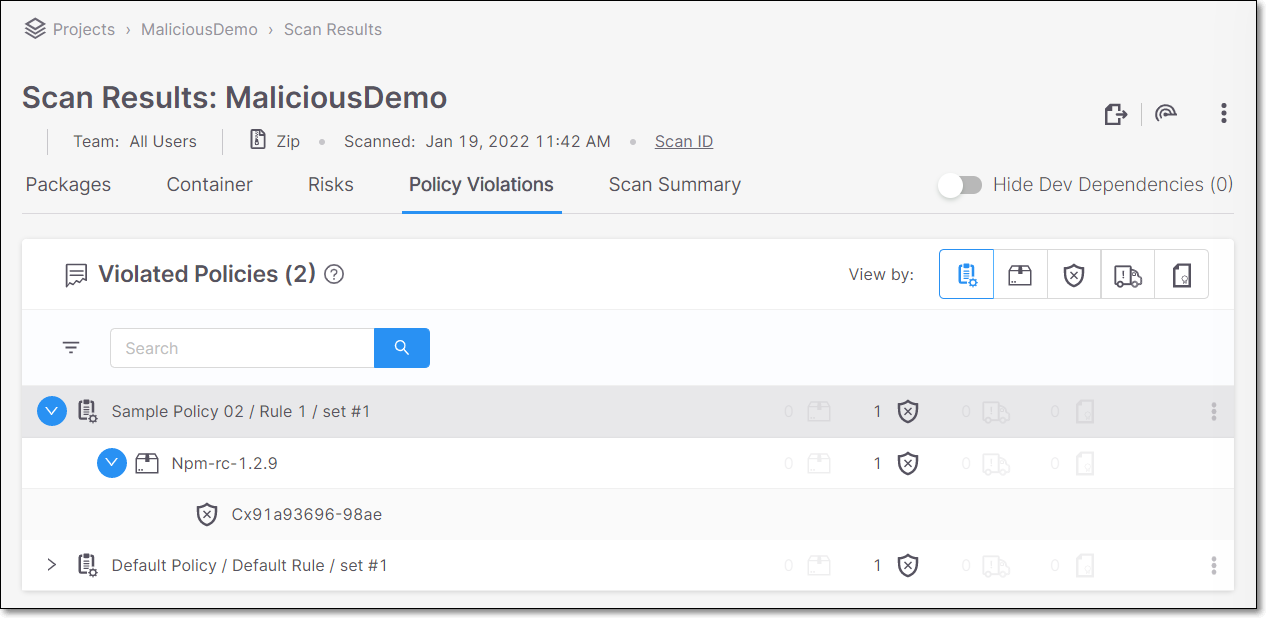 |
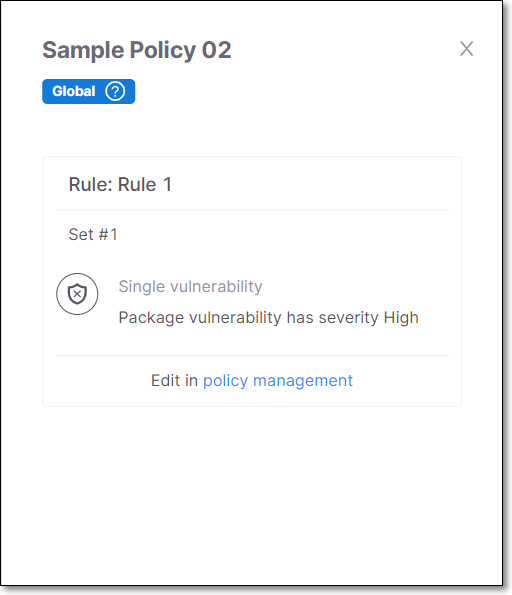
Clicking on a Policy opens a side panel that displays information about the rules that apply to the selected Policy. You can click on Policy Management to edit the Policy rules.
 |