- Checkmarx Documentation
- Checkmarx One
- Checkmarx One User Guide
- Managing Projects
- Configuring Projects
Configuring Projects
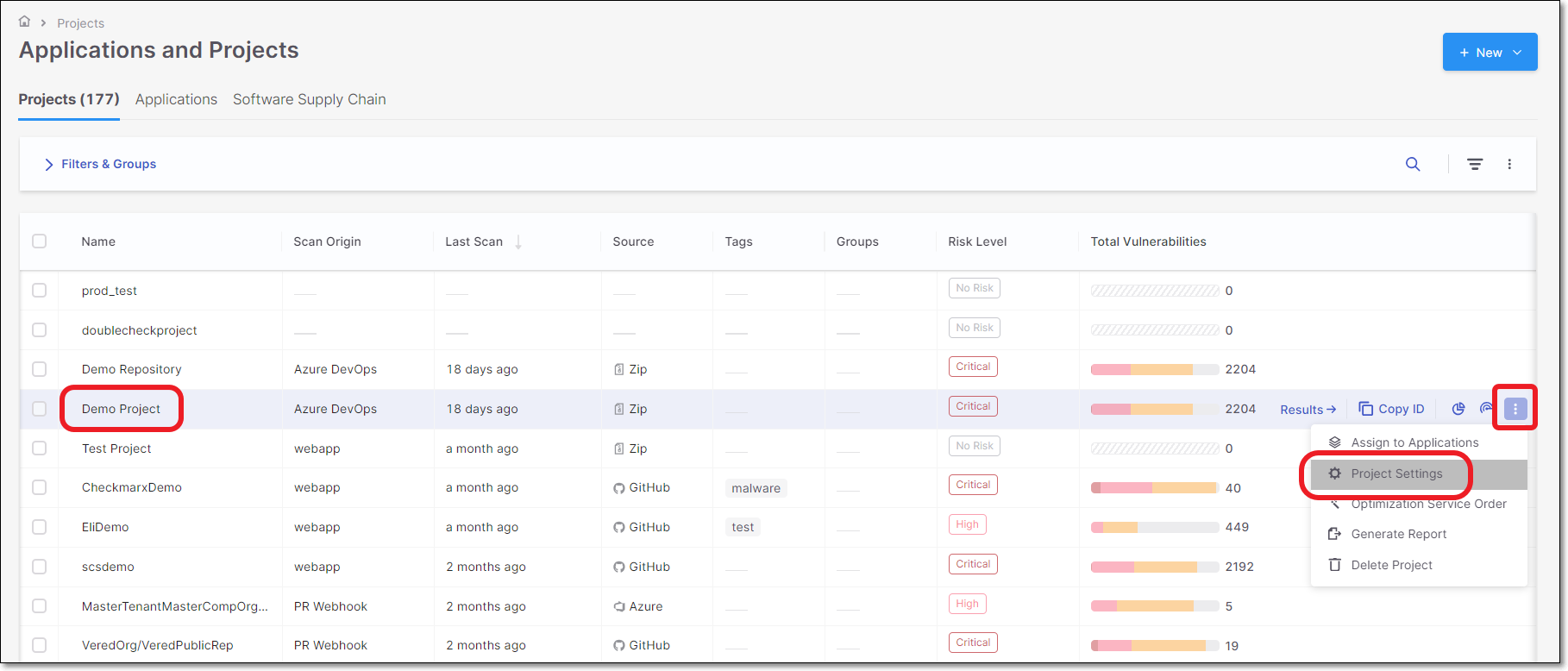
Open Project Settings
In the Applications and Projects home page, click on Actions icon →Project Settings.
 |
General Settings
The General section of Project Settings contains the following basic settings for the project:
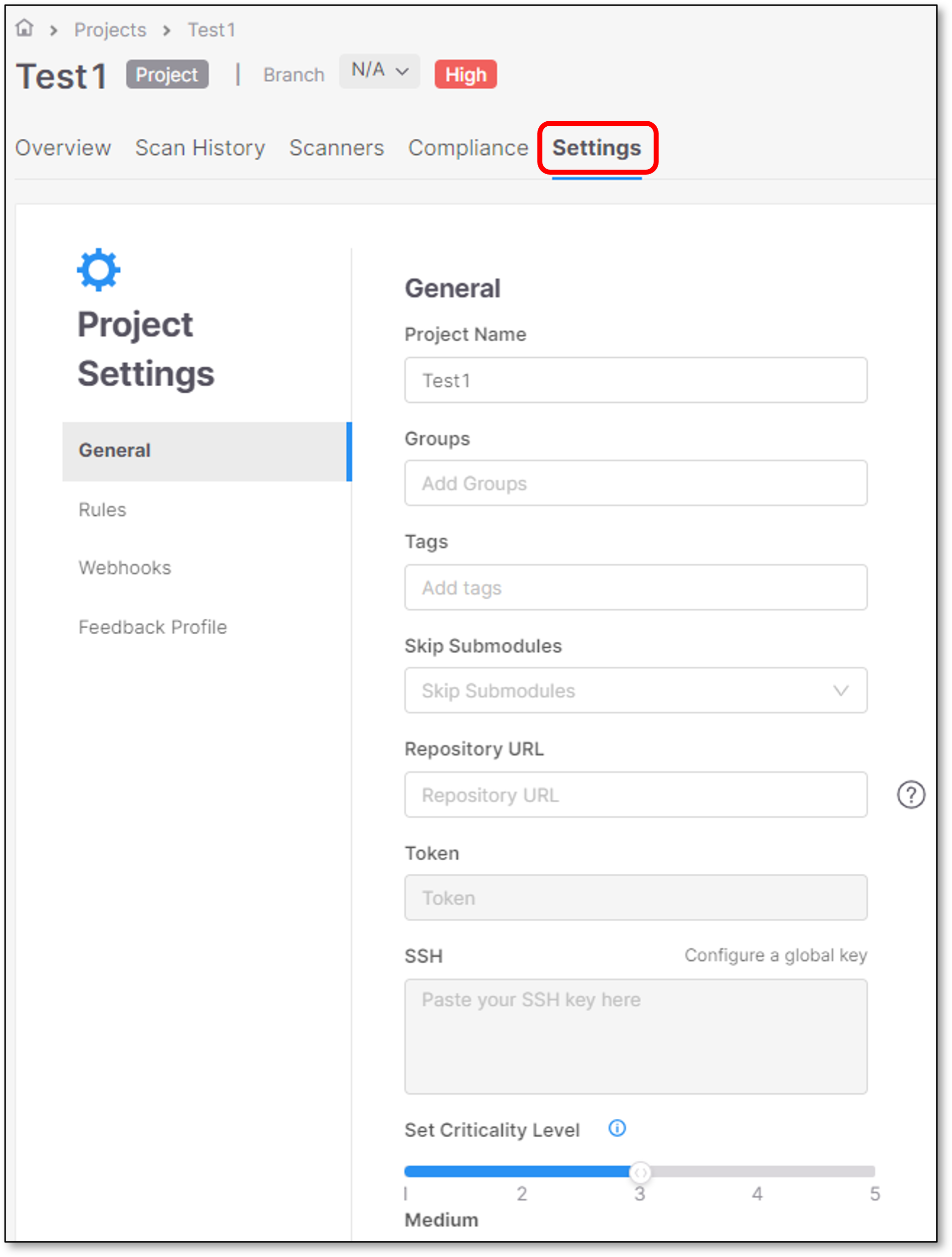 |
Project Name - The name of the project that you assigned.
Groups (optional) - This setting allows you to assign groups to a project.
When a group is assigned to a project, all members of that group are able to perform various actions in the project, including scanning source code and viewing results.
Project Tags (optional) - Assign tags to a project.
Tags are very useful for projects filtering purposes.
Tags have no dependencies in any other component, and it is possible to configure any required value.
Tags are not shared across projects.
For example: Projects A and B contain Test tag. Upon a change in project A tag, project B will not be affected and will remain with the same Test tag.
Tags can be used for overriding Jira feedback app fields values. For additional information see Fields Override.
Tags can be configured in two different formats:
key - <string>
key:value - <key string:value string>
Tags values can be updated by clicking the tag and updating its value.
Notice
The max. allowed characters per tag is 250, including the entire string (key or key:value). Commas are not allowed as part of a tag.
Skip Submodules (optional) - Enable this option to skip scanning repository submodules during project scans. By default, this option is set to
false.Repository URL - The repository URL from which the source code for this project is scanned by default. This value can be added when creating a Manual Scan project that scans coder from a Repository URL.
Token - The default token for private repository URLs.
SSH - Create and add your SSH key.
Set Criticality Level - This is a user-controlled attribute that reflects how you perceive the importance of the project in your organization. It does not affect any automated risk or vulnerability calculations. The following options are available: None, Low, Medium (the default), High, and Critical.
The criticality level appears in the Project Overview page.
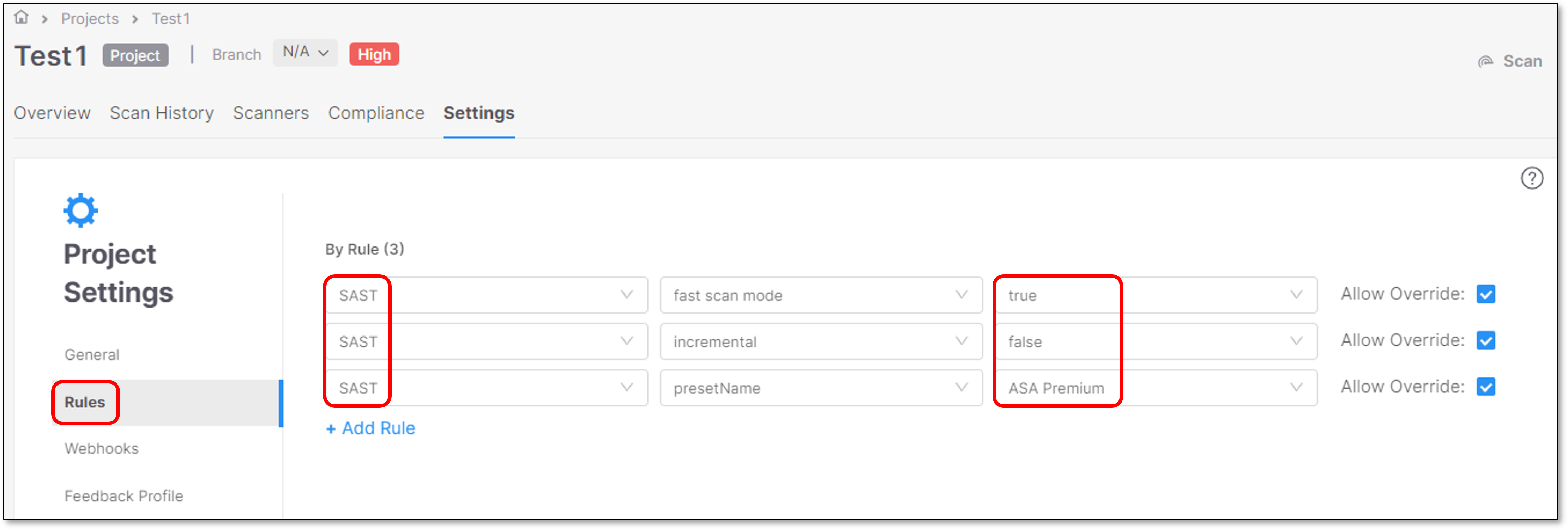
Project Rules
Project Rules allow the user to set parameters on the Project level.
Project configuration parameters are higher than the same parameter’s configuration via Configuring Scanner Default Settings.
This means that the parameters will apply to all the scans in the project.
Limitations
API Security does not support project rules at present.
Parameters that are configured via Configuring Scanner Default Settings are inherited to the Project Settings only, if the user configured them to Allow Override.
In case that Allow Override isn’t enabled for a specific parameter in the Configuring Scanner Default Settings, it won’t appear as an option on the Project Settings level.
"Allow override" is selected by default for all the rules under Project Settings.
It isn’t possible to configure the same parameter twice (in any configuration level).
Each scanner has a different set of parameters.
Notice
Clicking the
 icon clears the configuration field.
icon clears the configuration field.Checking
 allows overriding the same parameter in a higher level of configuration.
allows overriding the same parameter in a higher level of configuration.For more information, refer to Configuring Projects Using Config as Code Files.
Global Settings:
 |
Inherited Settings:
 |
If a greyed-out defaultConfig.xml file appears in the Project Settings, it indicates that customized settings for the default configuration were implemented at the tenant level with the intention of improving scan results or to assist in troubleshooting issues. Once these settings are established, they are automatically applied to every project. For additional information, reach out to support or contact your Product Account Manager (PAM) directly.
To add a new rule click + Add Rule.
Scanners Parameters Configuration Options
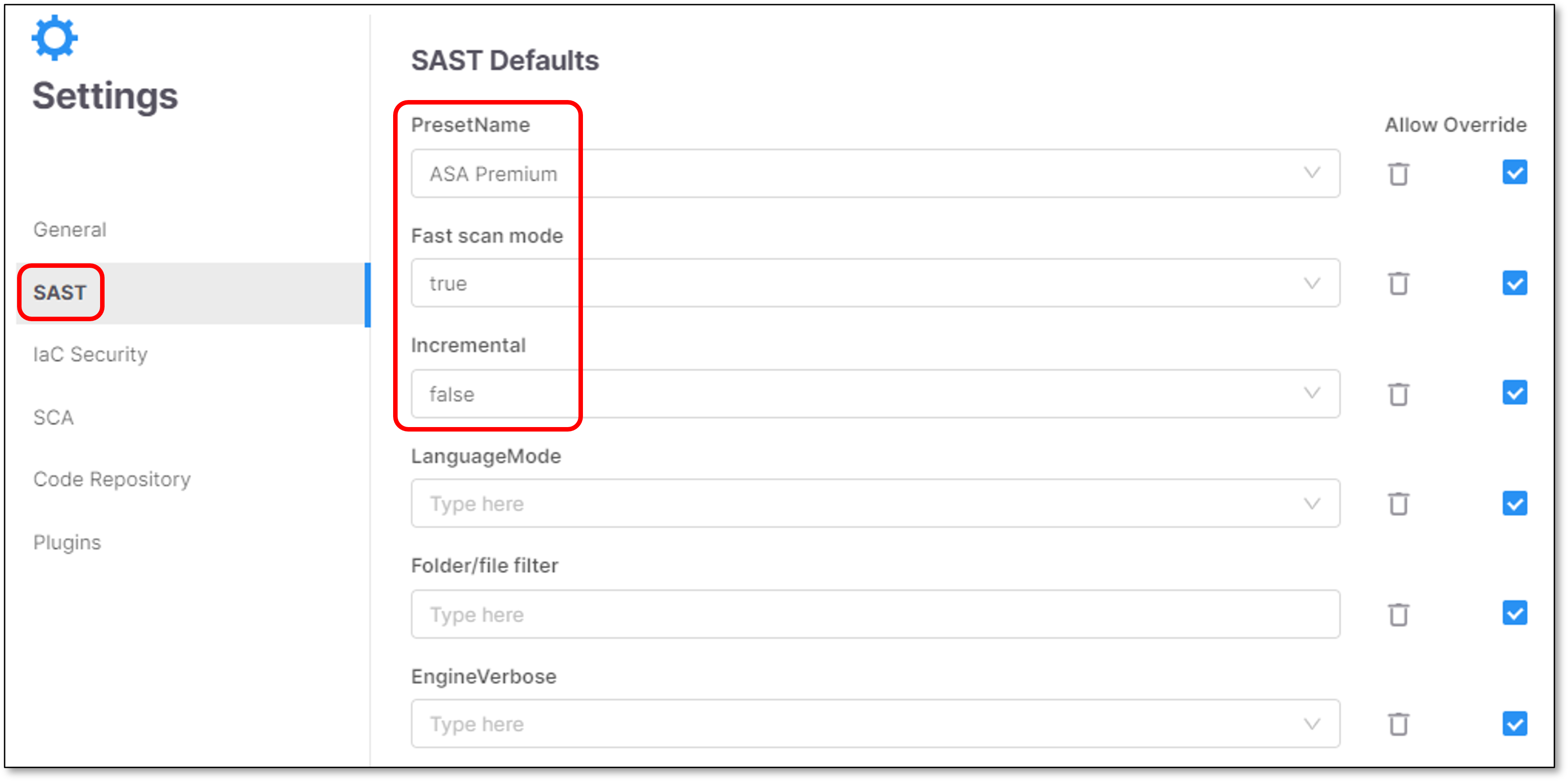
SAST Scanner Parameters
The table below presents all the optional parameters for the SAST scanner and their optional values.
Notice
There is an additional configuration option for filtering, which compliance results to show. This can currently only be configured via REST API. See API documentation.
Parameter | Values | Notes |
|---|---|---|
PresetName | All the available SAST Presets that exist in the system |
|
Fast scan mode | true / false | By default, the Fast Scan mode is set to true. For more information, refer to Fast Scan Mode. |
Light queries | true/false | Determines whether the scan should be performed using light queries or standard queries. Light Queries are simplified versions of standard queries focusing on the most urgent vulnerabilities, helping you spot threats faster. For more information, refer to Light Queries.
|
incremental | true / false | Determines whether the scan should be performed incrementally or as a full scan.
|
Recommended exclusions | true / false | Determines whether the system should automatically exclude certain files and folders from the scan. Enabled by default. By default, recommended exclusions is set to true.
|
LanguageMode | primary / multi | For more information, see: Specifying a Code Language for Scanning Supported Code Languages and Frameworks:
NoteBy default, the languageMode is Multi. |
Folder/filter filter | Allow users to select specific folders or files to include or exclude from the code scanning process. |
|
EngineVerbose | true / false |
|
Results scope level | Project / Application | When you triage SAST results (change state, severity, comments), by default the adjustment applies only to identical results within that Project. You can adjust this setting to apply changes to all identical results in the entire Application. |
Threshold for Incremental Scans (%) | 0.5 - 10 (intervals of .5) | When running an incremental scan, if the changes from the previous scan exceed the threshold, a full scan is run. By default the threshold is 7%. Use this configuration to set a custom threshold. For more information, see Adjusting the Incremental Scan Threshold. |
Incremental in branch (API) | true / false | When working with branches within Checkmarx GitHub Integration, if you open a pull request to merge into the master branch, you could run a faster incremental scan instead of a longer full scan. This capability is activated by configuring this setting to true. By default, it is false, so that only scans of the main branch are run as incremental. For more information, see Result Sco. |
ASA Premium Preset
ASA Premium Preset is a part of the SAST collection of presets.
This Preset is available only for Checkmarx One. Its usage is described in the table below.
Preset | Usage | Includes vulnerability queries for.... |
|---|---|---|
ASA Premium | The ASA Premium preset contains a subset of vulnerabilities that Checkmarx AppSec Accelerator team considers to be the starting point of the Checkmarx AppSec program. The preset might change in future versions. The AppSec Accelerator team will remove old/deprecated queries or include new and improved queries in a continuously manner. | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, Kotlin (non-mobile only), Perl, PHP, PLSQL, Python, Ruby, Scala, VB6, VbNet, Cobol, RPG and VbScript coding languages. |
ASA Mobile Premium | The ASA Mobile Premium preset is a dedicated preset designed for mobile apps. The ASA Premium Mobile preset contains a subset of vulnerabilities that Checkmarx AppSec Accelerator team considers to be the starting point of the Checkmarx AppSec program. The preset might change in future versions. The AppSec Accelerator team will remove old/deprecated queries or include new and improved queries in a continuously manner. | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, Kotlin (non-mobile only), Perl, PHP, PLSQL, Python, Ruby, Scala, VB6, VbNet, Cobol, RPG and VbScript coding languages. |
Fast Scan Configuration
Fast Scan configuration aims to find the perfect balance between thorough security tests and the need for quick and actionable results. There’s no need to choose between speed and security.
Fast Scan mode decreases the scanning time of projects up to 90%, making it faster to identify relevant vulnerabilities and enable continuous deployment while ensuring that security standards are followed. This will help developers tackle the most relevant vulnerabilities.
While the Fast Scan configuration identifies the most significant and relevant vulnerabilities, the In-Depth scan mode offers deeper coverage. For the most critical projects with a zero-vulnerability policy, it is advised also to use our In-Depth scan mode.
Fast Scan mode is activated by default. It can be deactivated manually on the Tenant (Account), Project or Scan level.
Warning
To expedite the results retrieval, the scanning process has been optimized to reduce the number of stages and flows involved in the scan. With this enhancement, the queries related to ASPM are not executed and results won’t be generated when utilizing this mode.
You may also notice impact on the API Security scanner results.
Fast Scan limitations
Fast Scan is not advised for CPP, JS and Kotlin.
Faster scans are achieved at the expense of comprehensive results.
Differences in scan results are expected due to the methodology used by Fast Scan. It explores fewer flows compared to the "in-depth" mode, which may result in some vulnerabilities being missed or unique findings that differ from the standard scan.
Light Queries
Light Queries are simplified versions of existing queries that focus on the most exploitable vulnerabilities. They help you prioritize threats while filtering out uncommon edge cases for clearer analysis. Light Queries are not intended to replace the more robust standard queries but offer an alternative form of analyzing code by focusing on the most immediate threats and readily exploitable weaknesses as quickly as possible. These queries offer a more straightforward way to analyze code, giving you key findings without the complexity. The Light Queries have a more restrictive subset of results regarding inputs and sinks and a broader one regarding sanitizers.
Important
Consider the following when Light Queries are enabled:
The Similarity ID, source, and sync remain unchanged whether or not Light Queries are enabled.
When Light Queries are enabled, the scan results are a subset of those from a standard query (i.e., when Light Queries are disabled).
When scanning with Light Queries enabled, the scan will likely get fewer results.
Supported Languages and Detected Vulnerabilities
Light Queries support the following languages:
Java
JavaScript
Client_DOM_XSS
Client_DOM_Stored_XSS
Client_DOM_Code_Injection
Client_DOM_Stored_Code_Injection
Client_DOM_Code_Injection_from_AJAX
Client_DOM_XSS_from_Ajax
C#
The following vulnerabilities are detected in all the above languages when Light Queries are enabled:
SQL Injection
Reflected XSS
Enabling Light Queries
Enable Light Queries under the Account Settings page by setting its value to true. By default, Light Queries are set to false (disabled), and the Allow Override option is enabled.
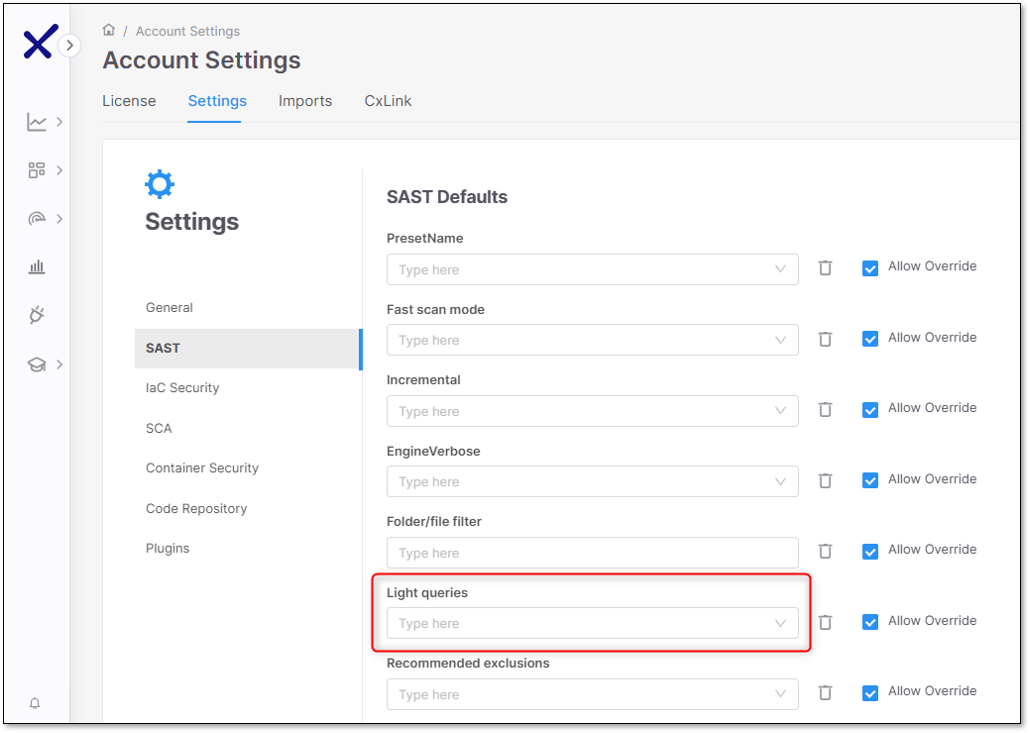
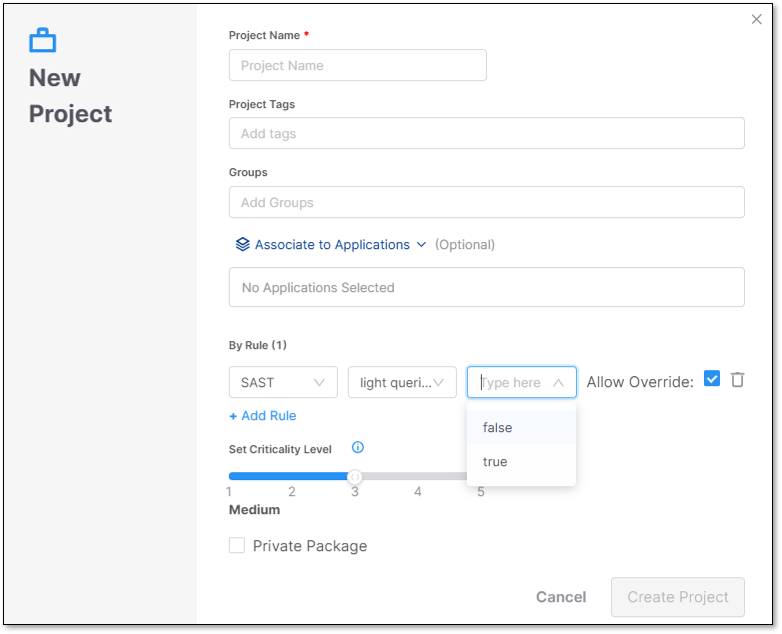
When creating a new project, on the project settings page, you must enable Light Queries as a rule. To add Light Queries as a rule, perform the following:
Click + Add Rule. The scanner, mode, and value dropdown options appear.
Select SAST, light queries, and true for the scanner, mode, and value dropdowns.
Select Create Project when finished.
To delete a rule, click  at the end of the rule's row.
at the end of the rule's row.
IaC Security Scanner Parameters
The parameters that will be defined for the IaC Security scanner will be applied to all the Projects running IaC Security scans.
The table below presents all the optional parameters and their optional values.
Parameter | Values | Notes |
|---|---|---|
Folder/file filter | Allow users to select specific folders or files to include or exclude from the code-scanning process. |
|
Platforms |
| NoticeConfigure one or more platforms, separated by a comma. The parameter means you only want to run scans (queries) for those platforms. For example, Ansible, CloudFormation, Dockerfile WarningAny mistake in the platform characters will cause an error. |
Preset Name | All the available IaC Security Presets that exist in the system | There are no Checkmarx Default Presets now. For more information on IaC presets, see here. WarningThe preset ID for IaC Security must be a valid UUID. Once you create one, you can copy the PresetID from the IaC Presets page. |
SCA Scanner Parameters
The parameters that will be defined for the SCA scanner will be applied for all the Projects that will run SCA scans.
The table below presents all the optional parameters, and their optional values.
Parameter | Values | Notes |
|---|---|---|
Folder/file filter | Allow users to select specific folders or files that they want to include or exclude from the code scanning process. |
|
Exploitable Path | Toggle On/Off | When Exploitable Path is activated, scans that use the SCA scanner will identify whether or not there is an exploitable path from your source code to the vulnerable 3rd party package. Learn more about Exploitable Path. |
Exploitable Path Configuration | Radio button selection | The Exploitable Path feature uses queries in the SAST scan of your project to identify exploitable paths to vulnerable 3rd party packages. Therefore, it is always necessary to run a SAST scan on the project in order to get results for Exploitable Path. Whenever you run a Checkmarx One scan with both the SAST and SCA scanners selected, Exploitable Path uses the results of the current SAST scan for analysis. When you run a Checkmarx One scan with only the SCA scanner selected, Checkmarx One can either use results from a previous SAST scan or it can initiate a new SAST scan (using default settings) that runs the Exploitable Path queries. Select one of the following configurations:
|
New Vulnerability Comparison Mode | Project-Wide (default) or Branch-Based | Determines what is used as the base-line for determining whether or not a vulnerability is a New finding in the current scan.
|
Java Language Version | 8, 11, 17 or 21 | Specify the Java version used for dependency resolution for gradle package manager. This version does not affect Java version used for maven resolution. If not defined, gradle scans will run with Java version 21 by default. |
Python Language Version | 2.7, 3.11, 3.12 or 3.13 | Specify the Python version used for dependency resolution for pip and poetry package managers. Poetry does not support Python prior to version 3, if version 2.7 is supplied, the default version is used instead. If not defined, scans will run with Python version 3.13 by default. |
Container Security Scanner Parameters
Checkmarx One offers robust filter settings to enhance container security by enabling users to configure their scans for precision and relevance. Below is an overview of the four available filter settings, designed to reduce noise and focus on critical vulnerabilities in your scans.
The following table provides an overview of the functionality of each filter. Additional details about the usage and syntax for these filters is available in Filter Usage Details.
Filter name | Description | Syntax | Examples |
|---|---|---|---|
Folder/file filter | Specify files and folders to be included (allow list) or excluded from (block list) scans. You can create complex filters that combine include and exclude patterns. |
TipYou can submit multiple items separated by a comma. |
|
Image/tag filter | Include or exclude images by image name and/or tag. |
TipYou can use wildcard (*) at the beginning, end or both. |
|
Package Regex Filter | Prevent sensitive packages from being sent to the cloud for analysis. Exclude packages by package name or file path using regex. TipExcluded packages will nonetheless appear in the scan results. However, no vulnerabilities will be identified in those packages since their info wasn't sent to the cloud for analysis. | Regex |
|
Exclude non-final stages filter | Exclude all images that are not from the final stage of the build process, so that only the final deployable image is scanned. TipOnly supported for Dockerfile images. | True - apply filter False - don't apply filter |
API Security Scanner Parameters
The parameters that will be defined for the API Security scanner will be applied for all the Projects that will run API Security scans.
The table below presents the optional parameters, and their optional values.
Parameter | Values | Notes |
|---|---|---|
Swagger folder/file filter | Swagger folder path or any folder/file type. Allow users to select specific folders or files that they want to include or exclude from the code scanning process. |
|
Secret Detection Parameters
Secret Detection identifies exposed credentials and other sensitive data across your assets, helping prevent leaks that can lead to security incidents.
Parameter | Values | Notes |
|---|---|---|
git commit history | true / false | Controls whether Secret Detection scans Git commit history or not. When set to true, historical commits are scanned in addition to the source code, providing deeper visibility into past secret exposure. When false, only the source code is scanned. |
Filtering Options
Filtering the scanners parameters is based on Glob.
For more information see Glob Tool
For instance:
Exclude all java files: !**/*.java
Exclude all files inside a folder Test: !**/Test/**
Exclude all files under root folder Test: !Test/**
Exclude just the files inside a folder leaving all subfolders content: !**/Test/*
Exclude all JavaScript minified files: !**/*.min.js
Note
The rules follow the same logic at tenant & project level.
Configuration Hierarchy
Scanners parameters configuration work in hierarchy.
During parameters configuration, the system considers the Tenant level as the highest configuration level followed by Project level, Config as Code and Scan level.
Parameters are inherited from one level to the other, starting from Tenant level.
Removing parameters from a lower configuration level can be performed only by deleting the parameter configuration from the higher configuration level. In this case the parameter won't be presented in the lower configuration level.
In case users edit a parameter in a lower configuration level, a  icon will appear at the right. Deleting the parameter can't be performed, as the parameter is inherited from the higher configuration level. This behavior is designed to emphasize that the configuration exist at the Tenant level and it is set with "X" value.
icon will appear at the right. Deleting the parameter can't be performed, as the parameter is inherited from the higher configuration level. This behavior is designed to emphasize that the configuration exist at the Tenant level and it is set with "X" value.
In case using the icon, it might appear that the parameter is deleted, but it is not. In case exiting the page and returning, the parameter will be presented again.
Note
When running a scan, the system considers the Scan level as the highest configuration level, followed by Config as Code, Project level and Tenant level.
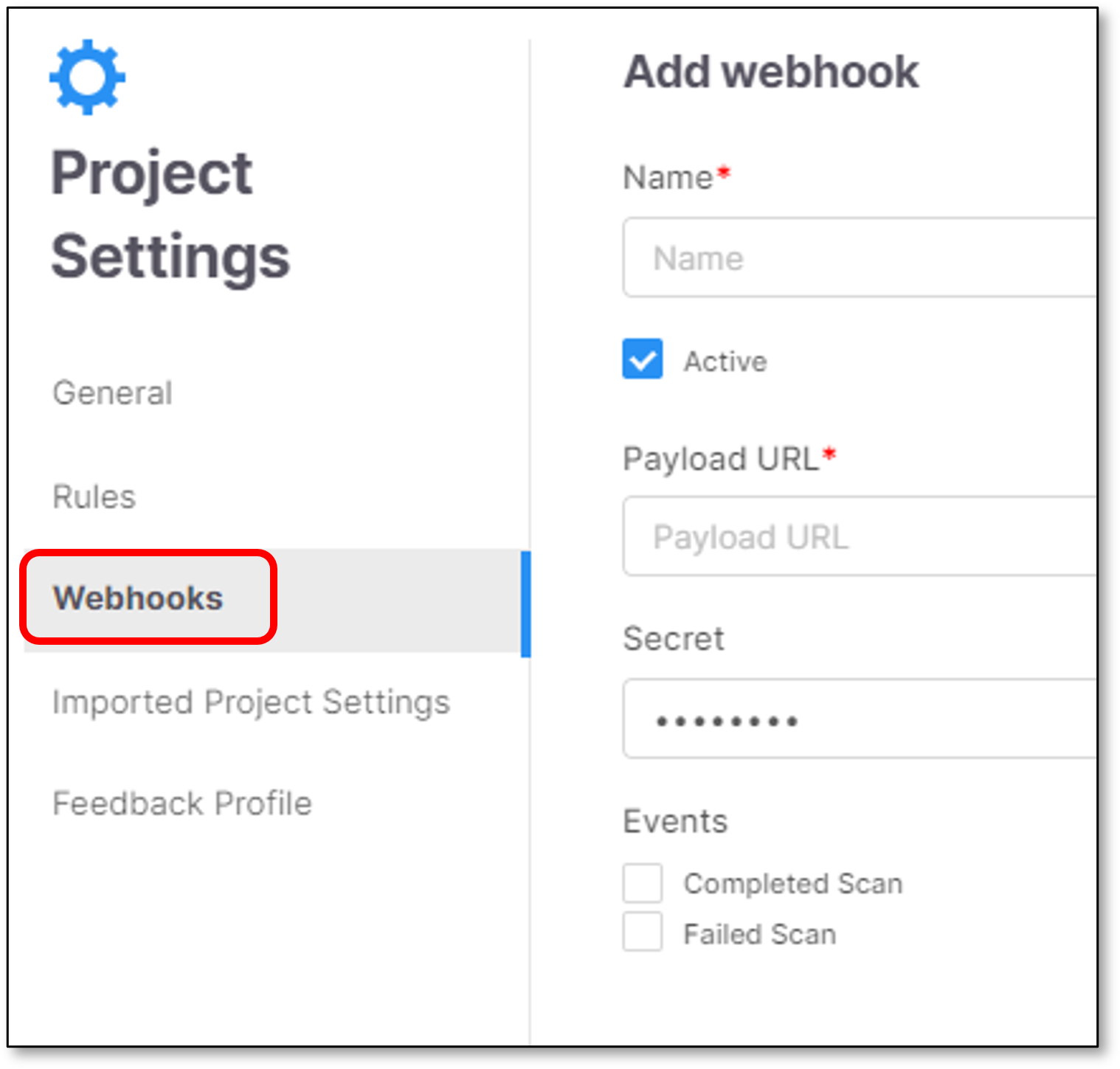
Webhooks
Webhooks configuration provides the user the ability to send post scan events to an external notification service.
The notifications include the triggered scans Success / Failed statuses.
An example about when each webhook event occurs and what the payload contains can be found in here.
To add a new Webhook click 
The screen includes the following configuration fields:
Note
Mandatory fields are marked with 
Name - Webhook service name.
 - Set the Webhook to be in active state.
- Set the Webhook to be in active state.Payload URL - Webhook service URL.
If we have the following webhook configured in our project settings:
https://webhook.site/ee1283ca-c114-42d1-b93b-10e783f2ed60The request information is the following:
Request:
POST https://webhook.site/ee1283ca-c114-42d1-b93b-10e783f2ed60 HTTP/1.1Headers:
Host: webhook.site
User-Agent: Go-http-client/1.1
Content-Length: 582
Content-Type: application/json
X-Cx-Webhook-Event: scan_completed_successfully OR scan_failed
X-Cx-Webhook-Signature: sha256=Jw9m7mG+MMsawW1UcM7gHH1KCGCejWwIxHv0VNDGOfU=
Accept-Encoding: gzip
Note
The X-Cx-Webhook-Signature is the eventData sent by the scan event encrypted using the sha256 and the secret is the webhook secret.
Body:
Eg. Scan completed successfully with 2 scanners
{ "scanId": "<SCAN_ID>", // eg "000000-0000-0000-0000-000000000000" "projectId": "<PROJECT_ID>", // eg "000000-0000-0000-0000-000000000000 "statusInfo": [ { "name": "general", "status": "Completed", "details": "" }, { "name": "<SCANNER>", // eg “sast”, “iac” "status": "Completed", "details": "", "loc": "<LINES_OF_CODE>" //eg 1503 }, { "name": "<SCANNER2>", // eg “sast”, “iac” "status": "Completed", "details": "", } ], "userAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36" "initiator": "<USER_NAME>", "sourceType": "<SOURCE_TYPE>(GIT/ZIP)" "sourceOrigin": "<SOURCE_ORIGIN>", // eg webapp "branch": "<GIT_BRANCH>", // eg master "mainBranch": "", "projectName": "<PROJECT_NAME>", // eg test "repoURL": "<GIT_REPOSITORY_URL>", // eg "https://github.com/user/repo" "correlationId": "<CORRELATION_ID>" // eg "000000-0000-0000-0000-000000000000" }Eg. Scan failed 1 scanner
{ "scanId": "<SCAN_ID>", "projectId": "<PROJECT_ID>", "statusInfo": [ { "name": "general", "status": "Completed", "details": "" }, { "name": "<SCANNER>", "status": "Failed", "details": "<ERROR_MESSAGE>", // eg "Failed:engine failed: Error in queries compilation: (11187,56): error CS1525: Invalid expression term ')' in ", "loc": <LINES_OF_CODE>, "errorCode": <ERROR_CODE> // eg 1015001 } ], "userAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36", "initiator": "<USER_NAME>", "sourceType": "<SOURCE_TYPE>(GIT/ZIP)", "sourceOrigin": "<SOURCE_ORIGIN>", "branch": "<GIT_BRANCH>", "mainBranch": "", "projectName": "<PROJECT_NAME>", "repoURL": "<GIT_REPOSITORY_URL>", "correlationId": "<CORRELATION_ID>" }Secret (Optional) - Webhook service secret.
Events - Set which scan events will be sent to the Webhook notification service (Completed/Failed scans).
Note
It is possible to configure one or more events.
Mandatory fields are marked with

Click Add
 |
Code Repository Project Settings
The Code Repository Configuration screen allows you to update the settings for any Code Repository Integration project.
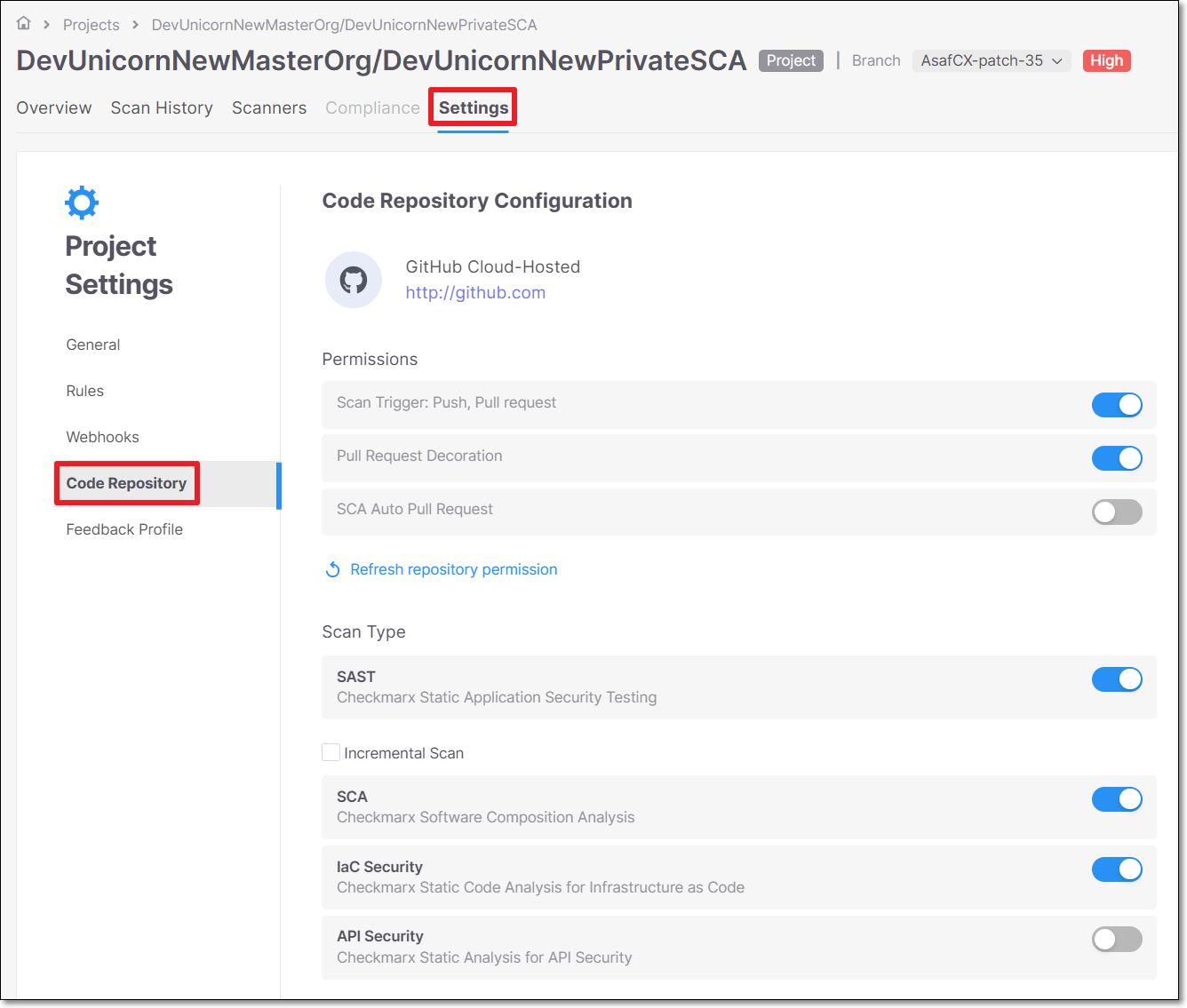
Permissions
Toggle on/off the permissions that you would like to adjust. After activating a new permission, you must click on Refresh repository permission. After making changes, click Save.
Scan Trigger: Push, Pull request - Automatically trigger a scan when a push event or pull request is done in your SCM. (Default: On)
Pull Request Decoration - Automatically send the scan results summary to the SCM. (Default: On)
SCA Auto Pull Request - Automatically send PRs to your SCM with recommended changes in the manifest file, in order to replace the vulnerable package versions. (Default: Off)
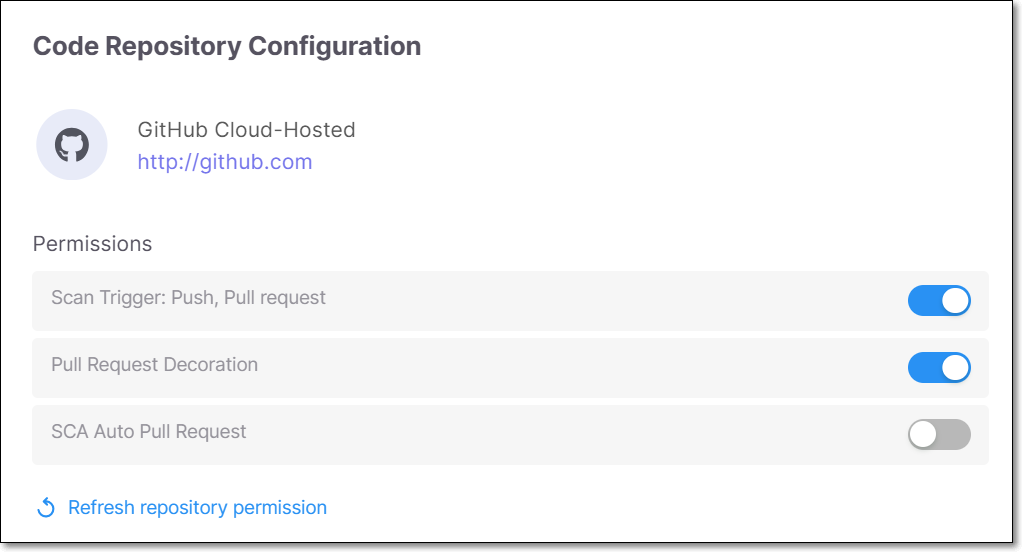 |
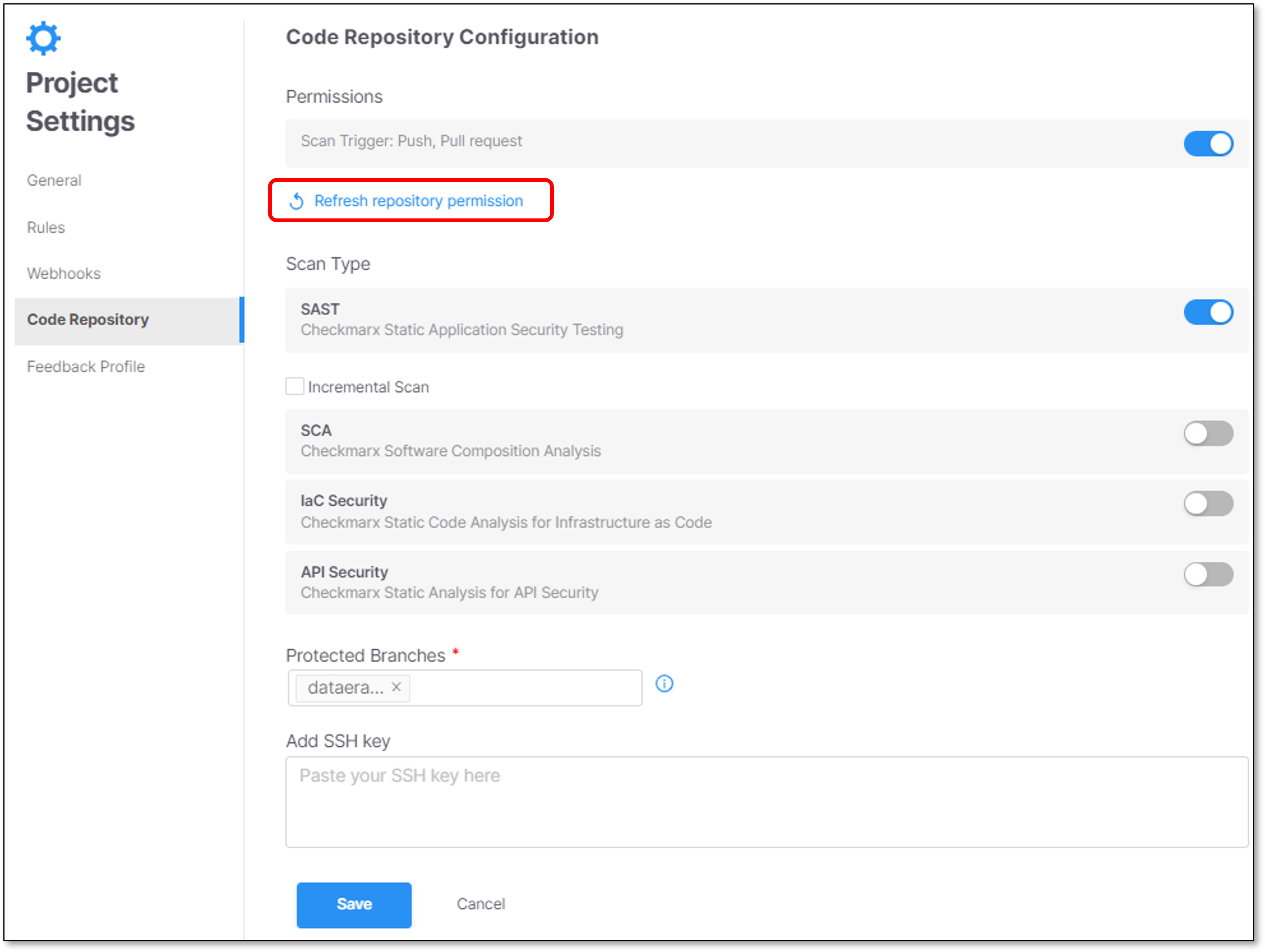
Refresh Repository Permission
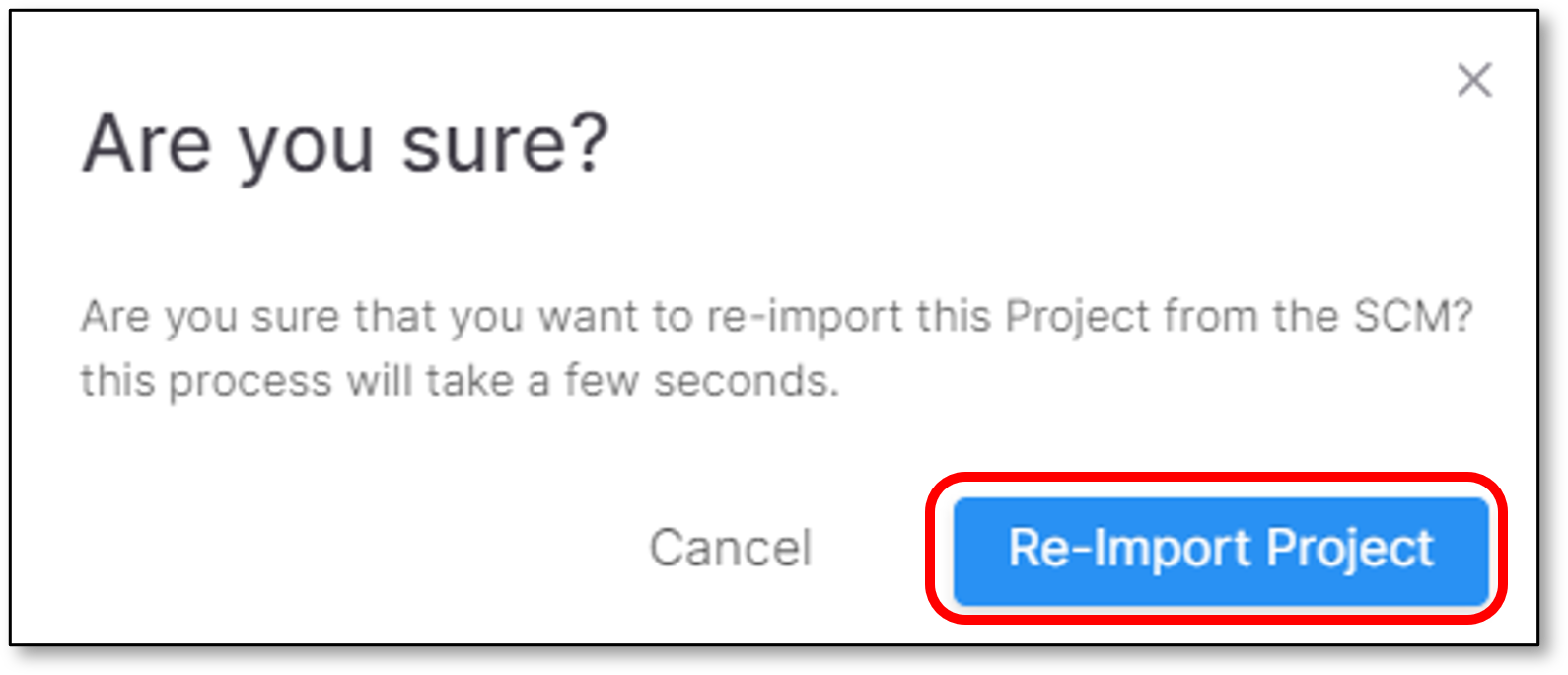
In case that you want to refresh the repository permission, click Refresh repository permission.
 |
A confirmation screen appear. To confirm and continue, click Refresh Project.
 |
Scan Type
Toggle on/off the scanners that will run for this project. After making changes, click Save.
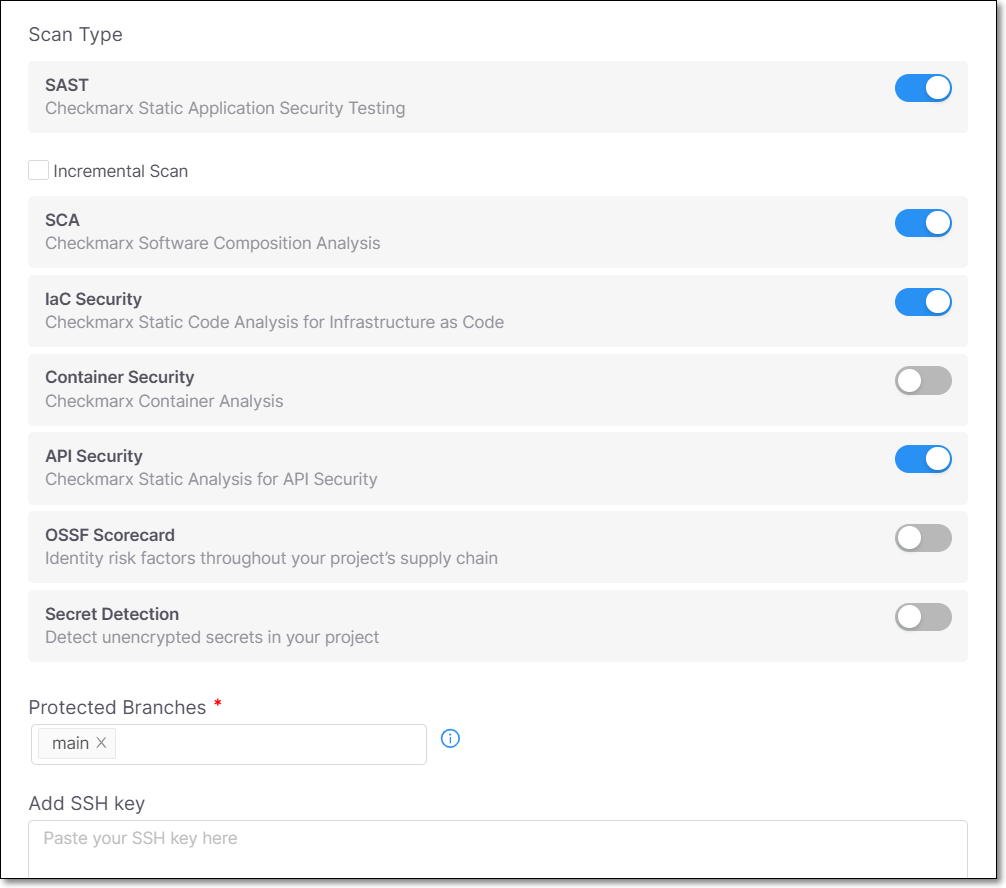 |
In addition, in this section you can configure the following:
SAST Incremental scan - Select this checkbox if you would like SAST scans to run as Incremental scans. For additional info, see Incremental Scans.
Specify Protected Branches - Protected Branches are the repository branches that are configured to be scanned.
COMING SOON: You can also specify a wildcard branch pattern to determine which branches are included in scanning. All branches that match the wildcard pattern will be treated as protected branches.
Examples:
To scan all feature branches, enter
feature/*. Any scan trigger on a branch such asfeature/loginorfeature/apiwill start a scan.To scan all branches with the string prod, enter *prod*
Add SSH key - You can paste your SSH key here. (optional)
Feedback Profile
Feedback Profile screen allows you to update the settings for any Feedback Profile that is created and assigned to a Checkmarx One Project.
For more information see Update an Assigned Profile