SAST Scanner
Overview
Checkmarx's Static Application Security Testing (SAST) scanner examines your application's code. It looks for common security weaknesses by analyzing the code's structure and how data flows through the application. The goal is to catch vulnerabilities early in the software development lifecycle, allowing developers to address security concerns before the application is run in production.
SAST builds a logical graph of the code's elements and flows without needing to build or compile a software project's source code. SAST then queries this internal code graph. SAST includes an extensive list of hundreds of pre-configured queries for known security vulnerabilities for each programming language. Using the Query Editor, you can configure your own additional queries for security, QA, and business logic purposes.
The input to SAST's scanning and analysis is the source code, not binaries, so no building or compiling is required, and no libraries need to be available. The code doesn't even need to be able to compile and link properly. Consequently, SAST can run scans and generate security reports at any given point in a software project's development life cycle.
Key Features
Fast Scan Configuration
Fast Scan configuration aims to find the perfect balance between thorough security tests and the need for quick and actionable results. There’s no need to choose between speed and security.
Fast Scan mode decreases the scanning time of projects up to 90%, making it faster to identify relevant vulnerabilities and enable continuous deployment while ensuring that security standards are followed. This will help developers tackle the most relevant vulnerabilities.
While the Fast Scan configuration identifies the most significant and relevant vulnerabilities, the In-Depth scan mode offers deeper coverage. For the most critical projects with a zero-vulnerability policy, it is advised also to use our In-Depth scan mode.
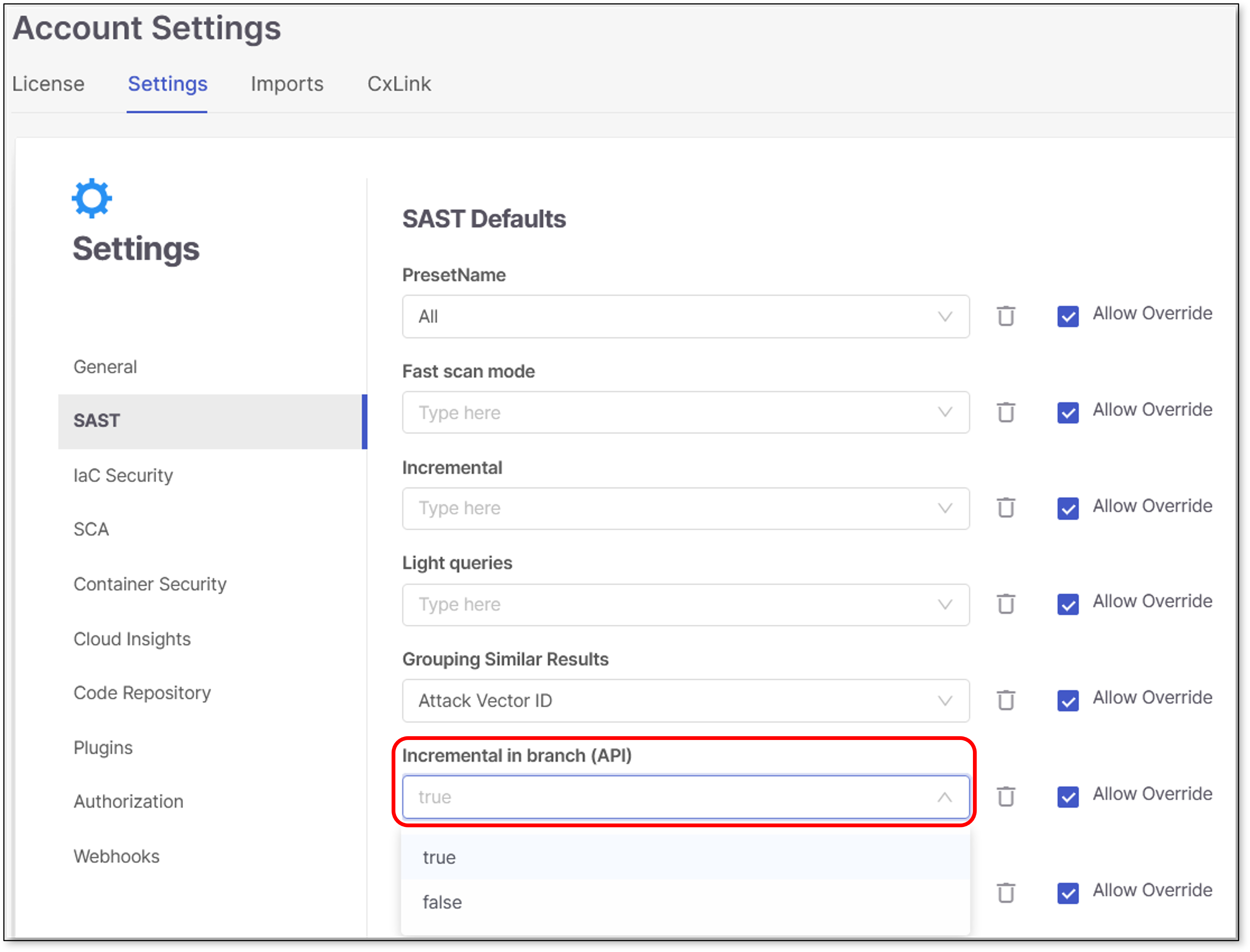
Fast Scan mode is activated by default. It can be deactivated manually on the Tenant (Account), Project or Scan level.
Warning
To expedite the results retrieval, the scanning process has been optimized to reduce the number of stages and flows involved in the scan. With this enhancement, the queries related to ASPM are not executed and results won’t be generated when utilizing this mode.
You may also notice impact on the API Security scanner results.
Fast Scan limitations
Fast Scan is not advised for CPP, JS and Kotlin.
Faster scans are achieved at the expense of comprehensive results.
Differences in scan results are expected due to the methodology used by Fast Scan. It explores fewer flows compared to the "in-depth" mode, which may result in some vulnerabilities being missed or unique findings that differ from the standard scan.
Light Queries
Light Queries are simplified versions of existing queries that focus on the most exploitable vulnerabilities. They help you prioritize threats while filtering out uncommon edge cases for clearer analysis. Light Queries are not intended to replace the more robust standard queries but offer an alternative form of analyzing code by focusing on the most immediate threats and readily exploitable weaknesses as quickly as possible. These queries offer a more straightforward way to analyze code, giving you key findings without the complexity. The Light Queries have a more restrictive subset of results regarding inputs and sinks and a broader one regarding sanitizers.
Important
Consider the following when Light Queries are enabled:
The Similarity ID, source, and sync remain unchanged whether or not Light Queries are enabled.
When Light Queries are enabled, the scan results are a subset of those from a standard query (i.e., when Light Queries are disabled).
When scanning with Light Queries enabled, the scan will likely get fewer results.
Supported Languages and Detected Vulnerabilities
Query Editor
Checkmarx Query Editor complements the SAST scanner by enabling you to easily customize SAST’s analysis queries or configure additional queries for security, quality assurance, and application logic purposes.
Query Editor can adapt SAST’s basic security functionality to non-standard code. It includes intuitive tools for adding code elements to various parts of queries and for locating relevant parts of existing queries and combining them to create your own. This helps eliminate false positives and ensure that all real vulnerabilities are identified. Use it to expand on SAST’s functionality and include queries supporting your specific QA or application logic needs.
Caution
There is a hard limit of 5 sessions of Query Editor that may run at a time and an idle session timeout of 60 minutes.
Note
Common queries cannot be edited in the Query Browser.
For more information about Query Editor, see SAST Query Editor.
Presets
Presets are sets of queries that a user can select in order to be more accurate in the SAST scans results. By using presets, the user triages against the main capabilities that the SAST scanner provides.
Preset management is a new way to control standard/predefined presets. It provides an ability for users to easily create their own presets according to their needs.
Presets are mandatory for the SAST scanner. If no preset is selected for a SAST scan, the default preset that will be used for the scan is ASA Premium.
For more information about Presets, see Preset Management.