- Checkmarx Documentation
- Checkmarx One
- Release Notes
- Previous Multi-Tenant Releases
- Older Versions
- Releases of July 2023
Releases of July 2023
Version 2.90 | Released on July 25
ChatGPT integration with IaC Security in VS Code
IaC is now integrated with ChatGPT, providing developers with natural language processing capabilities directly within the VS Code editor. This allows developers to analyze and understand code, get fix suggestions, and more.
The AI Guided Remediation feature is implemented as part of the Checkmarx VS Code extension. Users can access ChatGPT directly from the IDE to ask questions about code explanations, debugging, and fixing code errors. The feature is available for both the IaC Security results in Checkmarx One and for KICS Realtime scanning results.
For more information see AI Security Champion.
Eclipse integration enhancement: Direct scans in IDE
We have enhanced our Eclipse integration by adding support for scanning directly within the IDE. By running scans within Eclipse, developers can identify vulnerabilities at an early stage and mitigate the risk of security breaches.
Our Eclipse plugin now supports both Eclipse 2022 and 2019, ensuring compatibility across different versions of the IDE.
Furthermore, our Eclipse plugin encompasses all sub-features related to scans, providing comprehensive support for various types of security testing.
Ability to display Policy Management results via CLI
This release introduces a new feature that allows users to display Policy Management results via the command-line interface (CLI). With this enhancement, users can now receive immediate feedback on whether their scan violated the project policy.
The scan create method has been enhanced to include validation for policy violations. When initiating a scan, the system automatically checks if any policies have been violated.
After the scan is completed, the system invokes the Policy API and retrieves the status value. The status value can have the following states:
Completed - Indicates that the evaluation of the scan against the policy has been completed.
Evaluating - Indicates that the system is currently evaluating the scan against the policy.
Queued - Indicates that the scan has been queued for evaluation against the policy.
None - Indicates that the project does not have a policy attached to it.
To provide users with real-time updates on the scan's evaluation status, the system will continuously poll the status value until it reaches either Completed or None. This ensures that users can stay informed about the progress of their scan and promptly address any policy violations identified.
SAST upgrade to 9.5.5
The SAST scanner in Checkmarx One has been upgraded to version 9.5.5. This upgrade brings a range of improvements and enhancements to the scanner, providing a better experience and increased performance.
Resolved Issues
Scan results API pagination issue has been resolved, providing consistent results.
Scan Configuration data no longer moves between positions during scans.
Tenant name is no longer converted to lowercase, maintaining the original case.
The behavior of the Project update API endpoint (PUT) has been fixed.
Cursor re-positioning for Feedback Apps Input Fields (Description, Name) has been addressed.
Customers can now create Jira issues successfully without any errors.
GitHub clubbing no longer groups files in different paths inaccurately.
Azure clubbing now correctly groups files in the appropriate paths.
The CLI now scans without issues when the target project shares a name prefix with others.
API Token Refresh functionality has been resolved and works as expected.
Checkmarx One now prevents the creation of Presets with duplicated names via CxSAST Imports.
SCA Realtime scan returns accurate results without showing zero results.
SBOM Generation no longer encounters a 404 error.
Scan Runner - Upload Endpoint no longer returns a 400 error.
SCA + Exploitable Path scans now use SAST results correctly when executed after an only-SAST scan.
SAST correlation - SAST polling now stops polling when exceptions occur.
Checkmarx One multi and single tenant - broken links (Find best package version) no longer display an empty screen.
BFF New Global Inventory page now correctly displays Risk Score in CSV Reports for Risks.
Version 2.89 | Released on July 9
Mandatory rotation of service account passwords
To maintain a robust security posture, Checkmarx One now enforces the mandatory rotation of passwords for service accounts. This applies specifically to the OAuth Client ID and Secret used as a service account. The frequency of password rotation for all client secrets, including the existing ones, has been set to 100 days, but can be customized based on user preferences and settings.
This feature is especially useful in scenarios where developers have left the organization, but their secret ID, defined in the pipeline, remains active. By periodically rotating the service account password, we can mitigate the risk of unauthorized access and ensure that only authorized individuals can perform actions like Checkmarx One scanning.
To keep users informed and prompt them to take action, we have implemented an email notification system. When it's time to replace the secret service account, an email will be sent to the user, providing a clear notification and instructions on how to update the service account's credentials.
SAST Remediation Advice in Eclipse IDE
SAST Remediation Advice is now available in the Eclipse IDE. This enables developers to receive actionable guidance on addressing security vulnerabilities directly within their Eclipse environment.
SAST Remediation Advice provides comprehensive information on identified vulnerabilities, along with specific recommendations on how to remediate them and with practical code samples to implement secure coding practices.
New field in user and OAuth Client creation forms
This release features an update to the user creation form and the OAuth Client creation form, introducing a new field called Other. This new field serves as a space where any additional information or details about the user can be provided.
IAM version displayed
The version of IAM is now prominently displayed in the user interface (UI) and is also accessible through the API. This information provides transparency and helps users stay informed about the specific IAM version they are using.
Ability to retrieve all policy violations
With the latest enhancement to Checkmarx One plugins, both for CI/CD integration and command-line interface (CLI), all policy violations detected during scans are now displayed. This ensures that no violations go unnoticed, enabling users to take immediate action to address them.
New Data Store service for analytics
This version introduces a new service called analytics-datastore developed as an interface for storing and retrieving data from our new analytics storage in PostgreSQL.
Resolved issues
Selected "Applicable Compliance" switching automatically after a few secs
Selecting both repos with same name (self-hosted Bitbucket)
Application's projects are hidden if there is a scrollbar
Unable to submit support requests with Scanner > API Scanner
Unchecking detector from filtered list in presets unchecks all detectors
Same project is listed more than once when filtering on tag key/tag value
Fuzzy Search for protected branches doesn't load correctly
Audit trail does not report IP addresses
API response in "lastAccess" attribute is not reflecting "last access" timestamp
Configuration values not always saved for the scan
Can't target scan to internally hosted GitHub repo from UI
Maven resolver is not excluding dependencies correctly
API Security Release Notes
Enhanced API Security assessment for IaC and API Security license holders
IaC customers who hold both an IaC license and an API Security license, API-related risks will be shown in the API Security Result Viewer. It takes API Security assessment to the next level by providing in-depth details for each identified risk, including their association with specific endpoints.
Customers who hold only an IaC license will see a comprehensive overview of potential security gaps related to API endpoints in the IaC scan results. While the level of detail provided may be more generalized in this case, it still delivers valuable information that enhances the overall security posture.
Custom state management for API Documentation risks
To improve the risk assessment process, we have enabled users to change the state management of each API Documentation risk identified by API security in the scan results table. With this enhancement, users can determine the priority and address any false positives or other issues based on their domain knowledge and contextual understanding.
A similar feature has been implemented for risk severity management. Users now have the ability to modify the severity level of each identified risk in the API Documentation, based on their understanding of the potential impact and likelihood.
Customizing API Documentation Risks in the Global Risks section
The capability to manage the severity of each API Documentation risk has been extended to the Global risks section. With this enhancement users can customize and adjust the severity level of individual risks in the Global risks view.
SCA Release Notes
We have introduced several important changes to the the SCA scan results info shown in the Checkmarx One platform.
Warning
The changes discussed in this article relate to the data displayed in the Checkmarx One platform. The content of reports generated by Checkmarx One remain unchanged.
Warning
These changes are being rolled out gradually, so you may not see them yet in your account.
Scan Results - Packages Tab
All Packages Page
The results shown in the All Packages page of the Scan Results screen are now divided by category.
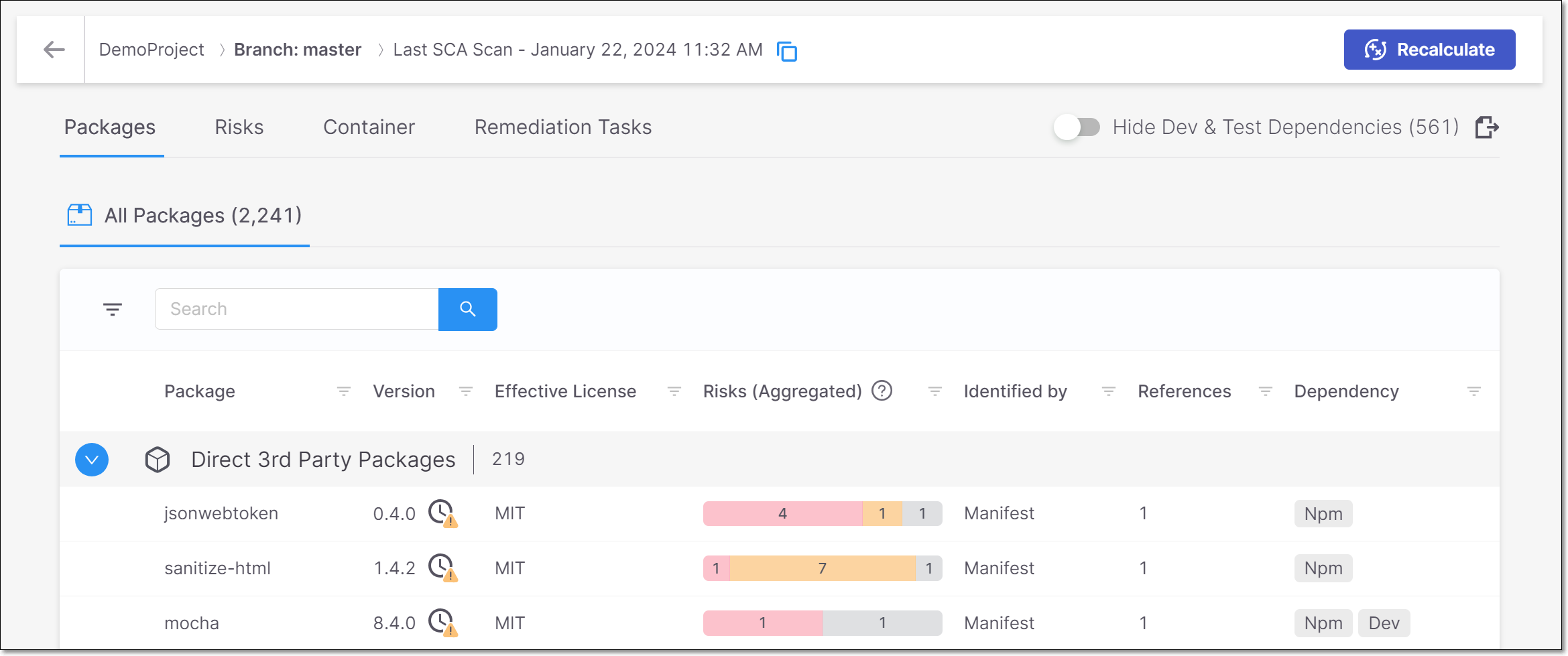
The section heading for each category shows the number of packages identified as well as the number of policy violations for that category.
Notice
For a package that is referenced both directly and transitively, the total number of packages shown at the top of the All Packages tab counts that package only once. Therefore, the total number of packages may be fewer than the total of the Direct packages plus the number of Transitive packages.
Click on a category to expand the display for the results in that category. The following categories are shown:
Direct 3rd Party Packages - Shows all 3rd party packages called directly by your source code.
Transitive 3rd Party Packages - Shows all 3rd party packages called indirectly by your project.
SaaS Providers - Shows all packages used for accessing SaaS services.
All Packages Table
We made the following changes to the columns shown on the Scan Results > Packages > All Packages table.
Added the References column, showing the number of times that the package is referenced. For direct packages that are also referenced transitively, we show separately the number of times that the package is referenced directly (D) and transitively (T).
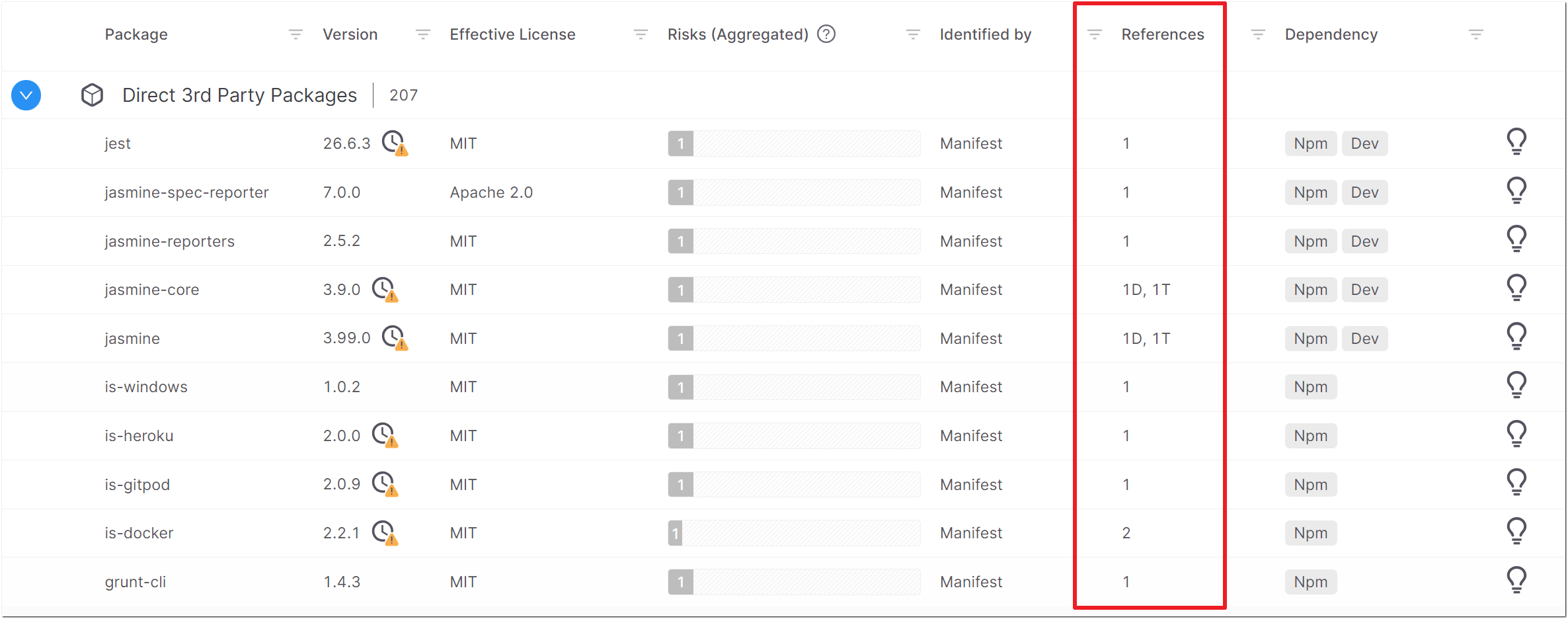
Added the Usage column, indicating whether or not the packaged is used in the source code.
Notice
This column is only shown for scans on which Exploitable Path was run.
Added an AppSec Knowledge Center link
 for each package in the table.
for each package in the table.Minor modifications and column rearrangement.
Package Details Page
References
The References section was added, showing the number of direct and transitive references for the package.
Scan Results - Risks Tab
All Risks Table
Added the Exploitability column, showing any exploitability indicators that apply to this vulnerability. Possible indicators:
Exploitable Path - indicates that a path was detected from your source code to the vulnerable method in the package, enabling attackers to exploit the vulnerability.
Tip
Results are only returned if Exploitable Path was activated for this project and the project uses a language that is supported for Exploitable Path.
Known - This vulnerability is cataloged by CISA as a Known Exploited Vulnerability (KEV), indicating that it poses a severe and imminent threat.
PoC - A Proof of Concept (POC) for exploiting this vulnerability is available in the wild, making it easy for threat actors to implement an exploitation of this vulnerability. We draw this info from Offensive Security's Exploit Database.
Added the Category column, showing the CWE ID and a brief description of the CWE.
In the Identified in Package column an indication is now shown for whether this is a direct or transitive dependency (D or T). Results can be filtered by Direct / Transitive.
We changed the method for counting Legal Risk instances. We now count each package that a license applies to as a separate risk instance, as opposed to the previous behavior of counting each license as a single risk instance no matter how many packages the license applies to. Thus, the Identified in Package column now always shows a single package for each risk instance.
Rearranged columns.
Scan Results - Containers Tab
Container Vulnerabilities
We changed the handling of container vulnerabilities for which the Category is "unknown". Instead of treating these as High severity vulnerabilities, we now treat them as Low severity. Also, these vulnerabilities are only shown in the summary table, but you can no longer drill down to view the details page, since there are no details that we can provide.
SBOM Improvements
We have added support for generating SBOM using SPDX v2.2 format. SPDX SBOMs are output in JSON file format.
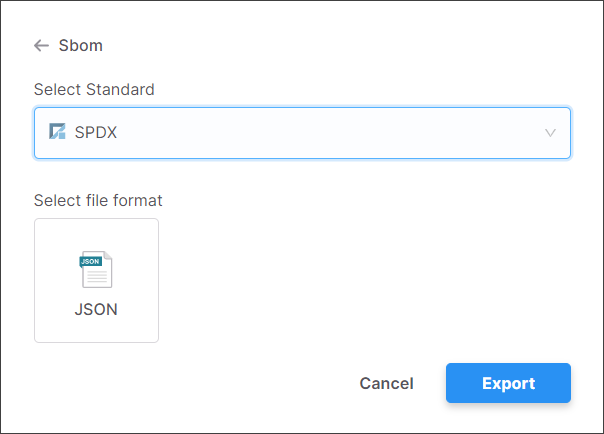 |
In addition, we have improved the quality of the CycloneDX v1.4 SBOMs, making them more compliant with SBOM specifications.
SCA Resolver Releases
We released the following new versions of SCA Resolver:
Notice
The complete changelog, and links to download SCA Resolver are available here.
Version 2.2.11
Fixed a bug related with exploitable path that the file was being generated in an incorrect format.
Version 2.2.9
Improved file handling of large results files.
For PIP, Graphviz is now used instead of the pipdeptree tool.
CLI and Plugins Release of July 2023
Version 2.0.53
Status | Item | Description |
|---|---|---|
NEW | Violated policies | Added information about violated policies to the scan results. This information is shown in the console summary as well as in the Summary HTML and Markdown reports. These results are shown both for For policies that are configured to "break build", when the policy is violated the scan will fail. (The |
NEW | Mask command | Added the |
UPDATED | Scanner selection | By default, the |
FIXED | Risk management | Fixed issue that risk management using the |
FIXED | KICS Realtime scanner | For scans run using |
Version 2.0.52
Status | Item | Description |
|---|---|---|
FIXED | SBOM | Increased the interval between retries when generating SBOM reports. |
Version 2.0.51
Status | Item | Description |
|---|---|---|
FIXED | SBOM | Fixed issue with generating SBOM reports. |
FIXED | SCA Realtime scanner | Fixed issue that SCA Realtime scanner wasn't identifying vulnerabilities in Python projects due to use of incorrect package manager. |
CI/CD Plugins
In July we released the following CI/CD plugin versions.
Improvements and Bug Fixes
Status | Item | Platform | Description |
|---|---|---|---|
NEW | Violated Policies | Azure DevOps, GitHub Actions, TeamCity | Added information about violated policies to the scan summary output. For policies that are configured to "break build", when the policy is violated the scan will fail. (The |
Plugin | Marketplace | Code Repository | Documentation | Changelog |
|---|---|---|---|---|
Azure DevOps | https://marketplace.visualstudio.com/items?itemName=checkmarx.checkmarx-ast-azure-plugin | |||
GitHub Action | https://github.com/marketplace/actions/checkmarx-ast-github-action | |||
TeamCity | https://github.com/CheckmarxDev/checkmarx-ast-teamcity-plugin | |||
Jenkins |
IDE Plugins
In July we released the following IDE plugin version:
Improvements and Bug Fixes
Status | Item | Platform | Description |
|---|---|---|---|
NEW | AI Guided Remediation | VS Code | We added ”AI Guided Remediation” feature, which harnesses the power of Open AI's GPT to help you to understand the vulnerabilities in your code, and resolve them quickly and easily. This feature is currently supported only for IaC Security vulnerabilities. TipThis feature needs to be activated for your tenant account via the web portal Account Settings > Settings > Plugins. This option may not be available yet in some environments. When you initiate an AI chat, we automatically provide the context to GPT so that you can start a conversation about the precise vulnerability instance that you are assessing. TipWhen sending your IaC files to GPT, we protect your sensitive data by anonymizing all passwords and secrets before the content is sent. The query used for identifying sensitive data can be seen here. |
NEW | Documentation and feedback | VS Code | Added a new Documentation & Feedback section to the Checkmarx panel, providing quick links to view our documentation and submit requests for improvements. |
NEW | Run scan from IDE | Eclipse | You can now initiate scans directly from your eclipse IDE. This empowers developers to identify vulnerabilities and remediate them as they code. You can run a new scan on an existing Checkmarx project by simply clicking on the "play" button in the Checkmarx panel. A Checkmarx scan runs on the files in your current workspace. A sanity check is run to verify that the project and branch in your workspace match the project and branch that were scanned for this project. If a mismatch is detected, then a warning message is shown. TipThis feature needs to be enabled for your organization's account by a Checkmarx admin user under Account Settings. |
NEW | SAST results viewer | Eclipse | In the SAST results viewer, we added new tabs with additional info about each vulnerability.
|
NEW | Pre-release versions | Eclipse | We now create nightly pre-release versions of this extension whenever we merge new code. The pre-release version can be installed from Marketplace. |
FIXED | Multiple additional params | Visual Studio | Fixed issue that when submitting multiple additional params, only the first was being processed. |
FIXED | Non-Git project | Visual Studio | Fixed issue that when running a scan from the IDE, if the content in your workspace project isn't a Git project we had been treating it as a mismatched project. |
FIXED | No results project | Visual Studio | Fixed issue that when running a scan from the IDE, if a project didn't have any results (identified risks) we had automatically been treating it as a mismatched project. |
FIXED | Risk Management | VS Code | Fixed issue that risk management (triaging results) hadn't been working for IaC Security risks. |
FIXED | SCA risks triaging | Eclipse | Disabled triaging for SCA risks, because it hadn't been functioning properly. |
FIXED | Thread access | Eclipse | Fixed issues with invalid thread access. |
IDE Plugin Quick Links
Get Latest Version from Marketplace | Changelog | Documentation |
|---|---|---|