Enabling TLS 1.3 Support and Blocking Weak Ciphers on CxManager
Notice
TLS 1.1 is being phased out for all major browsers, such as Chrome, Firefox, Safari, and Edge.
Please be aware that CxSAST v9.6. and v9.7 supports TLS 1.3 via the browser and command line but not via a remote database.
TLS (Transport Layer Security) and its now-deprecated predecessor, SSL (Secure Sockets Layer), are cryptographic protocols designed to provide communications security over a computer network. Websites can use TLS to secure all communications between their servers and web browsers. The TLS protocol aims to provide privacy and data integrity between two or more computer applications.
Sensitive data such as user credentials and credit card information must be protected when transmitted over the network, and the ciphers used during secure communications via SSL and TLS 1.1 are too weak. As a rule of thumb, if data must be protected when it is stored, it must also be protected during transmission. Even if high-grade ciphers are supported and used today, some misconfiguration in the server may force users of a weak cipher or no encryption to grant access to the supposedly secure communication channel.
Enabling TLS 1.3 Support
Support for TLS 1.3 can be enabled via the Windows registry on the CxManager host. As explained below, TLS 1.3 can be enabled manually or automatically from the CxManager host.
Notice
TLS 1.3 requires SQL Server 2022 (16.X) or higher. TLS 1.3 is compatible with Windows 11 and Windows Server 2022. TLS is enabled in Windows Server 2022 by default. Ensure that you have TLS 1.3 listed in your registry before proceeding. Older SQL server versions and Windows operating systems do not support TLS 1.3.
It is strongly recommended to disable weak ciphers. The relevant ciphers are listed at the end of this document.
Enabling TLS 1.3 Automatically
1. Download the attached TLS 1.3 .reg to the CxManager desktop.
2. Right-click (on Windows 10 and 11, select More Options), and select Merge.
3. Restart the server.
Enabling TLS 1.3 Manually
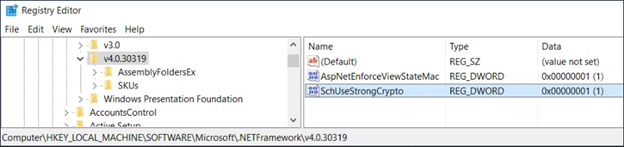
1. Start the Registry editor: Enter regedit in the Windows search field. The Registry Editor appears.
Disabling Weak Ciphers
Contact your administrators or IT personnel to disable the below ciphers.