- Checkmarx Documentation
- SAST/SCA Integrations
- CI/CD Plugins
- Jenkins Plugin
- Reviewing Scan Results
Reviewing Scan Results
Scan results activated by Jenkins are displayed in the Jenkins web interface and the CxSAST interface, as explained in Navigating Scan Results in CxSAST. The results are saved in Jenkins and, if defined, can be sent by email as a Jenkins post-scan action, as explained in Setting up Scans in Jenkins.
Notice
The synchronous mode, as defined in Setting up Scans in Jenkins, enables viewing scan results in Jenkins. If cleared (asynchronous mode), the build's scan results are not displayed. A link to the scan results in the CxSAST web application is provided with the build results. In this case, any results displayed in Jenkins are from the previous successful scan.
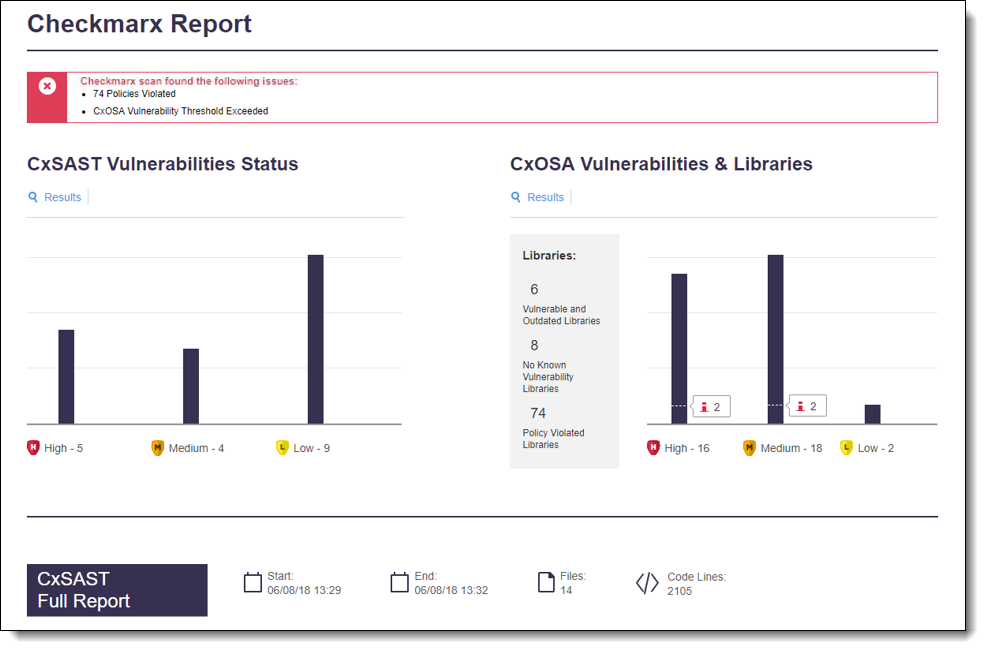 |
The Checkmarx SAST Security Vulnerabilities Trend graph is displayed in the Jenkins Job/Project dashboard. It provides the number of found vulnerabilities for each severity level and by the last recent builds. A graphical side-by-side summary of the CxSAST results can also be viewed in the Jenkins Job/Project dashboard under Checkmarx Report. Summaries and full reports can be viewed per application and consist of the elements listed and explained below.
Notice
The results displayed in the Checkmarx report depend on which scan options were enabled during the scan configuration.
Every report summary has a status bar indicating if the code sample has passed or failed the scan.
Red lists issues found (exceeded threshold value or violation of one or more policies):

Green indicates a passed scan:
 |
This section illustrates and explains report summaries for each application.
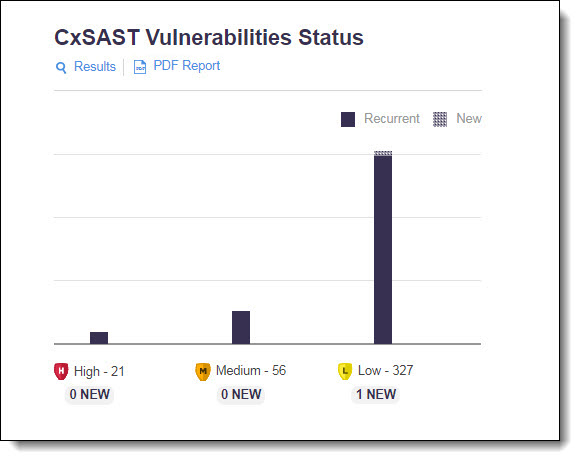
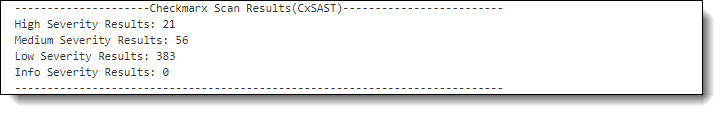
This graph represents the status and severity of security vulnerabilities discovered during a scan, as listed in the table below.
Label | Description | |
|---|---|---|
 | Recurrent | The status of a vulnerability is recurrent if it was already discovered in a previous scan. |
 | New | The status of a vulnerability is new if it was discovered for the first time or re-opened after being resolved in a previous scan. |
 | Default Threshold | Indicates the default threshold setting. |
 | High | Indicates the number of high-severity vulnerabilities. |
 | Medium | Indicates the number of medium-severity vulnerabilities. |
 | Low | Indicates the number of high-low vulnerabilities. |
 | Results | Provides a link to the code viewer in CxSAST. Refer to Navigating Scan Results for additional information. |
 | PDF Report | Provides a link to the CxSAST report in PDF format. |
 |
The CxSCA summary provides information about the distribution of security issues for the job/project and consists of the following:
For a summary report: CxSCA risk report summary is displayed in Jenkins (Future Release). The CxConsole displays the URL for viewing the full scan report in the CxSCA web server.
For a Full Scan Report, log in to the CxSCA web browser and navigate to the URL of the full scan report. When you run a scan from Jenkins, Zip is displayed in the Scan Method column of the Scan History tab.
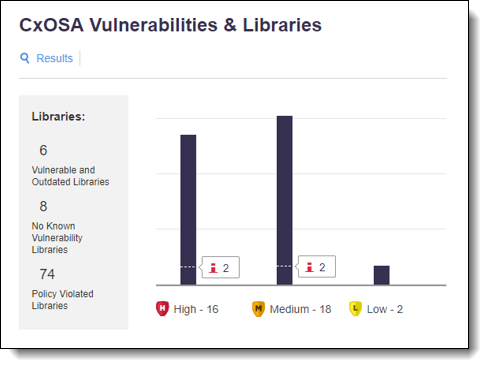
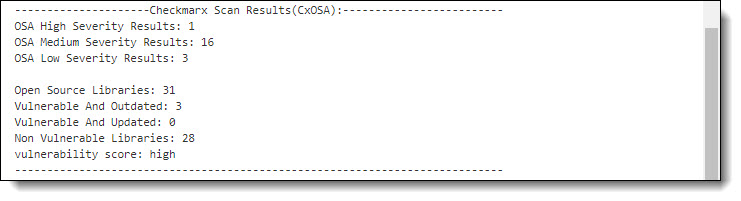
The CxOSA summary provides information about the security vulnerabilities and the library status, as listed in the table below.
Label | Description | |
|---|---|---|
 | Default Threshold | Indicates the default threshold setting. |
 | High | Indicates the number of high-severity vulnerabilities. |
 | Medium | Indicates the number of medium-severity vulnerabilities. |
 | Low | Indicates the number of high-low vulnerabilities. |
 | Results | Provides a link to the CxOSA Viewer in CxSAST. |
 |
This section illustrates and explains the full reports for each application.
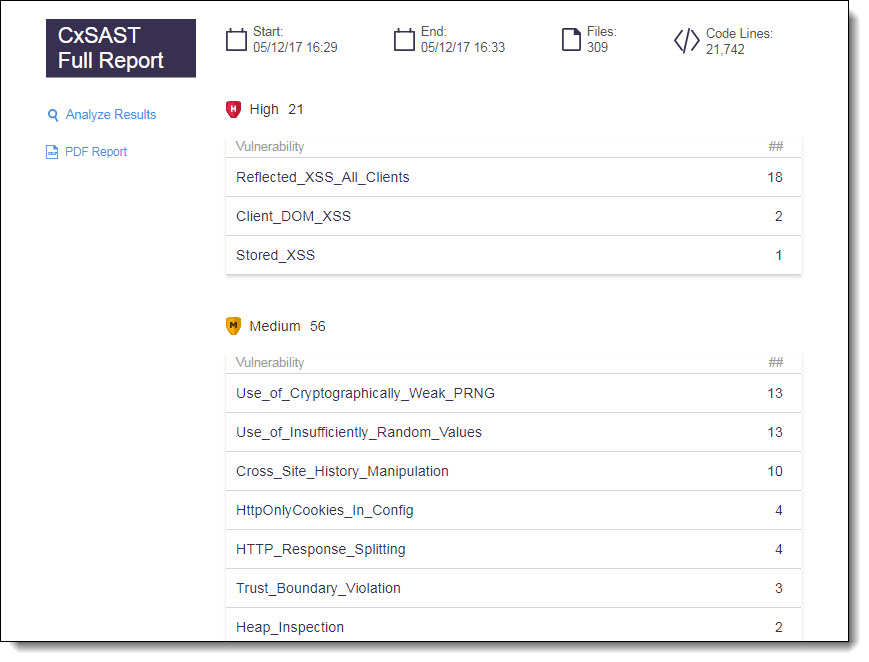
The full report on CxSAST provides information about the distribution of security issues for the job/project and is divided into the following categories:
Item | Description |
|---|---|
Report Criteria | Provides the following information:
|
Query Severity | The vulnerabilities will be organized by query severity. |
Analyze Results | Provides a link to the code viewer in CxSAST. Refer to Navigating Scan Results for additional information. |
PDF Report | Provides a link to the CxSAST report in PDF format. |
 |
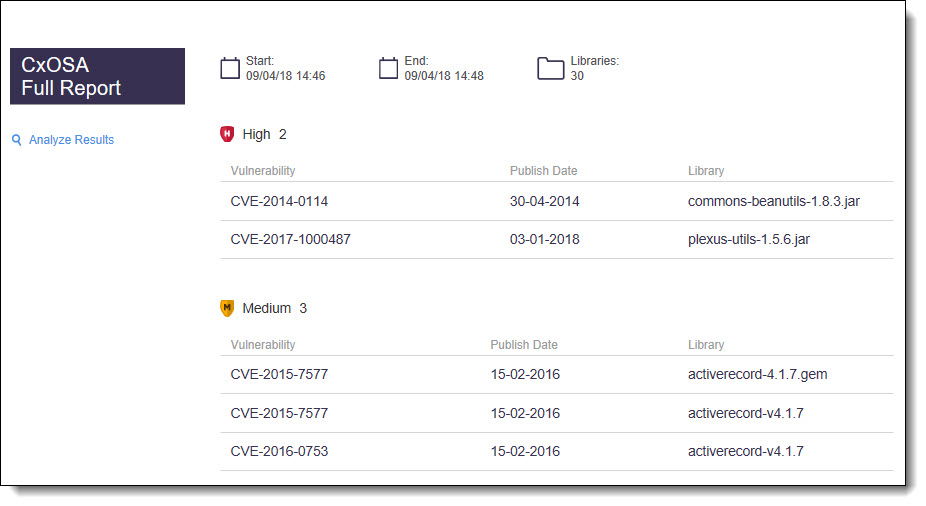
The full report on CxOSA provides information about the distribution of security issues for the job/project and is divided into the following categories:
Item | Description |
|---|---|
Report Criteria | Provides the following information:
|
Vulnerability Type | Provides a list of the vulnerabilities found, the distribution of the vulnerabilities by type (high, medium and low) and the number of vulnerability instances for each type. |
Analyze Results | Provides a link to the CxOSA Viewer in CxSAST. |
 |
Notice
Not Exploitable vulnerabilities are not aggregated in the global summary. In coordination with this, the CxOSA Full Report displays Not Exploitable vulnerabilities with a strike-through.
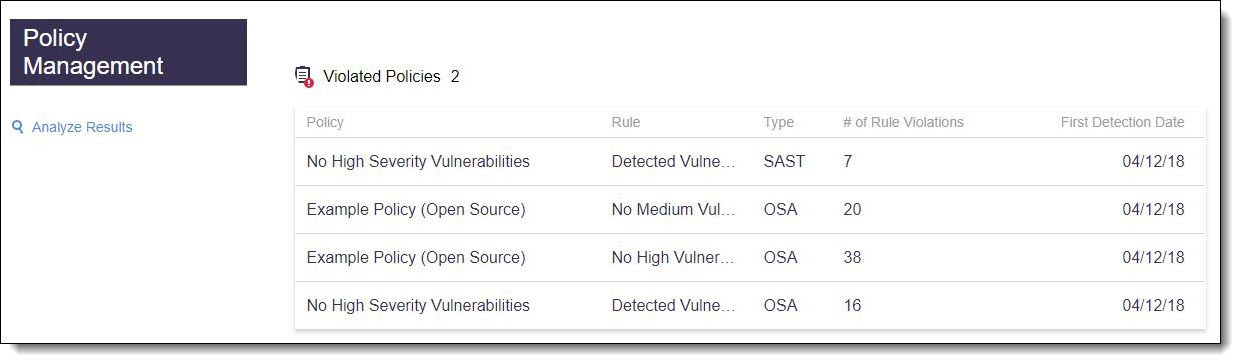
If the build failed due to CxOSA and/or CxSAST policy violations, a unified report is displayed showing the following information:
Number of violated policies
Names of violated policies
Names of respective rules violated
Type of scan used
Number of instances of a violated rule
First detection date
 |
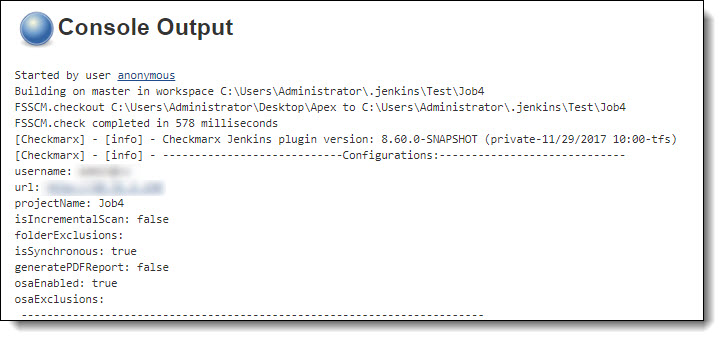
A textual summary of the results can be viewed in the Console Output (Build # > Console Output).
 |
 |
 |
 |