Integrating the Checkmarx Vulnerability Integration
Once all the integrations are activated, scheduled tasks invoke the integrations automatically daily and are chained to run in sequence. Each Checkmarx application vulnerability integration is intended to provide complete data retrieval. Running them out of order requires ServiceNow and Application Vulnerability Response expertise and could result in incomplete data.
If the three integrations are not chained for execution, they will need to be run manually in this order for SAST and SCA:
Checkmarx Application List Integration
Checkmarx Scan Summary Integration
Checkmarx Application Vulnerable Item Integration
Checkmarx Application List Integration
Click Integrations.
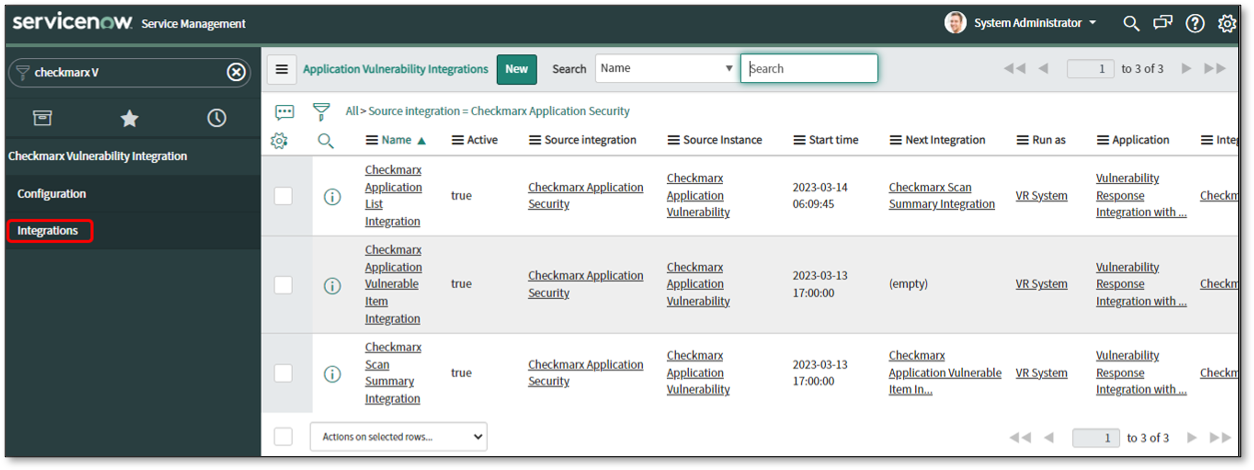
Click Checkmarx Application List Integration.
Click on the calendar icon to select a date and time. The Integration will import project details created in the CxSAST/ CxSCA portal after the specified Start Date and Time.
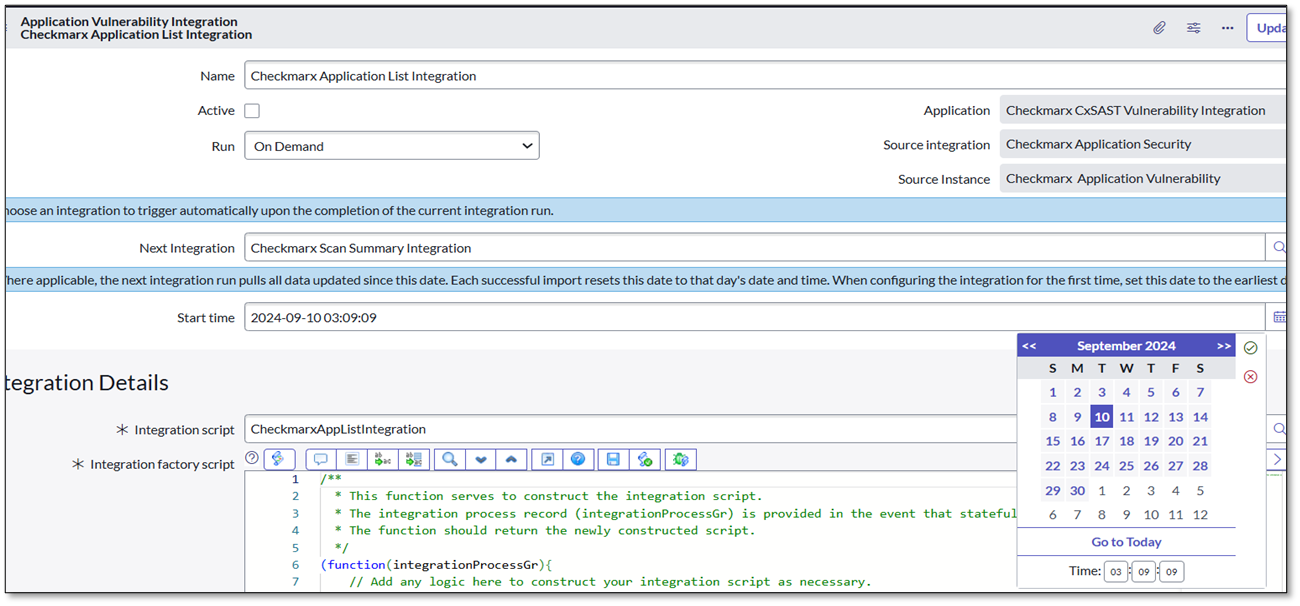
Click Execute Now if the run is not scheduled and is On Demand or Integration needs to be performed manually.
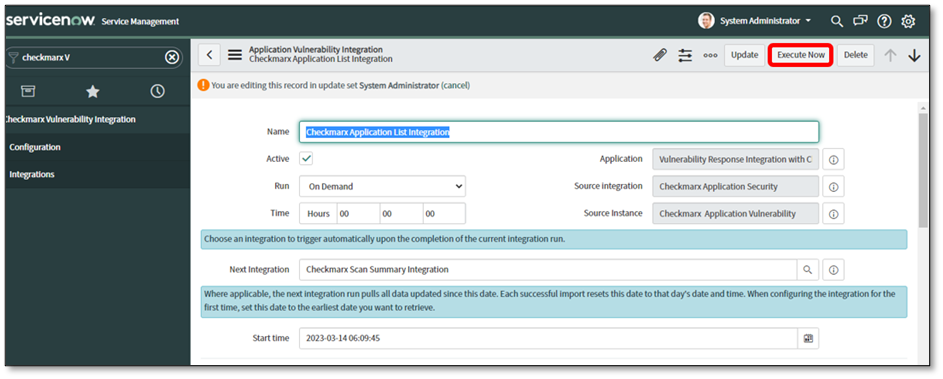
The Application Vulnerability Integrations screen is displayed.
When the plugin shows the State and Substate of Complete and Successful, respectively, the plugin is connected to the Checkmarx instance and pulled into the project list. The first time all the project lists are imported, the plugin will ascertain how many scans there are and pull in the latest ones.
Checkmarx Scan Summary Integration
The steps for integrating the Checkmarx Scan Summary Integration are similar to those above, but a date can be included.
Click Checkmarx Scan Summary Integration, as per point 2 above.
Click on the calendar icon to select a date and time. The Integration will import the scan summary of those Scans created in the CxSAST/CxSCA portal after the specified Start Date and Time if Run was not scheduled and is On Demand or if the integration must be performed manually.
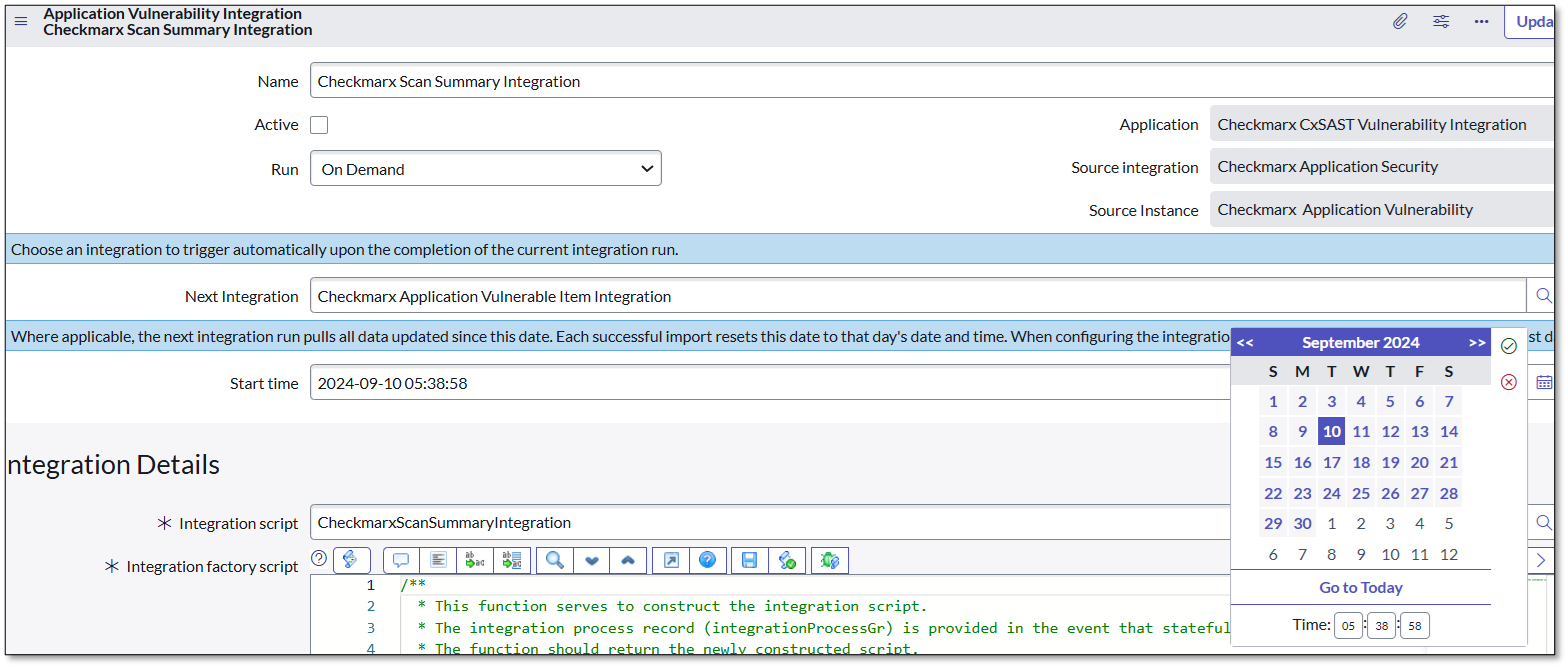
Click Execute Now.
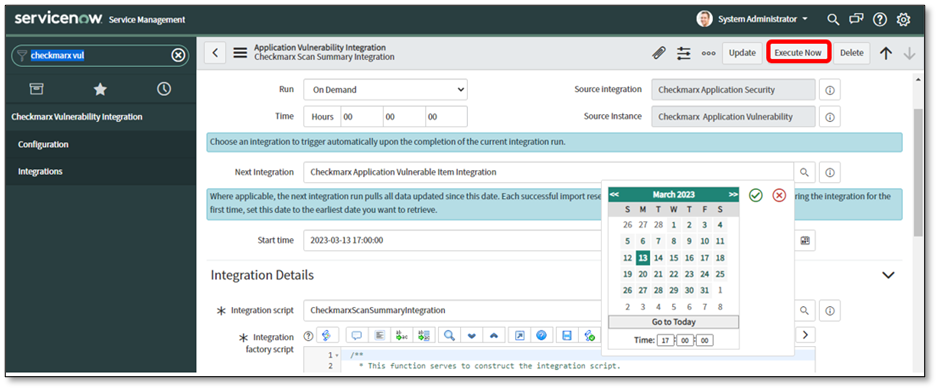
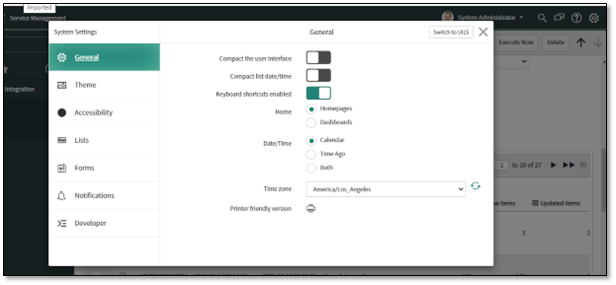
Navigate to the Settings icon to edit the time zone of the Start Time.
Select the dropdown list to select the Time zone.
Note
The integration's selected time from Start Time will be converted to Coordinated Universal Time (UTC), irrespective of the chosen time zone. Checkmarx will use the converted UTC.
Checkmarx Application Vulnerable Item Integration
The steps for integrating the Checkmarx Application Vulnerable Item Integration, SCA Application List Integration, SCA Scan Summary Integration, and SCA Application Vulnerable Item Integration are the same as those for the Checkmarx Scan Summary Integration.
The SNOW plugin will not import any findings marked Not Exploitable in CxSAST. If the vulnerability is already present and later marked Not Exploitable, it will be labeled Closed in SNOW during the next integration run.
To get Fixed findings from the Plugin, compare the old scanId present in ServiceNow with the project's latest ScanID. Any resolved findings will be marked closed.
The integration will import projects, scans, and scan results of scans created in the CxSAST/CxSCA portal after the specified Start Time (configured on the integration page) during the Integration Run.
Note
The integration may not succeed if customizations are made in any fields on your ServiceNow platform.
If a script has been customized and the latest version hasn't been applied, you must revert it to its store version. Follow these steps to revert the script:
In the Application Navigator, search for Script Includes under All.
Under System Definition, select Script Includes.
Search for the modified script (e.g., CheckmarxAppVulItemIntegration, CheckmarxScanSummaryIntegration, CheckmarxUtilBase).
Scroll down to the Version field.
Click on the link for the Store version.
Click Revert to this version.
This is a one-time manual step after the initial update. Future updates will automatically apply without requiring manual reversion.
Any project or scans deleted on the Checkmarx SAST will not be deleted on ServiceNow.
Verifying the Property to Bring Up Closed Vulnerabilities
Navigate to All search sys_properties.LIST.
Navigate to sys_properties_list, and search for property sn_vul.create_closed.
When the system property create_closed (Property name: sn_vul.create_closed) is true, it creates new records in the Closed state and updates those that are Closed.
If the above property is false, the present vulnerabilities will be updated to Closed, but the new Closed findings will NOT be inserted.