Setting Up SSO with OKTA and SAML
Codebashing supports single sign-on using SAML 2.0 with OKTA as an identity provider. OKTA is cloud-based and enables web login using existing user credentials and is compatible with many applications.
This document provides a step-by-step guide for configuring single sign-on using OKTA and SAML 2.0.
Prerequisites
To set up OKTA to login to the Codebashing platform, you need:
Free or fully paid access to a Codebashing account.
Access to an active OKTA account.
Creating a Service Provider Application in OKTA
The connection between OKTA and Codebashing is defined by using a service provider application in OKTA.
To create a service provider application in OKTA:
Log in to your OKTA administration account using your username and password. The Launch Apps screen is displayed.
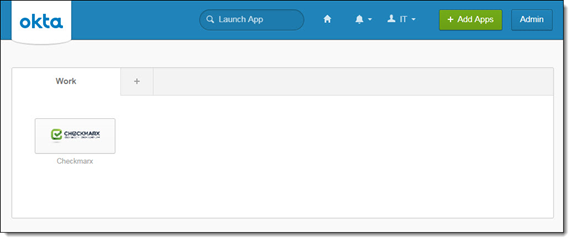
Click <Admin>. The OKTA Dashboard screen is displayed.
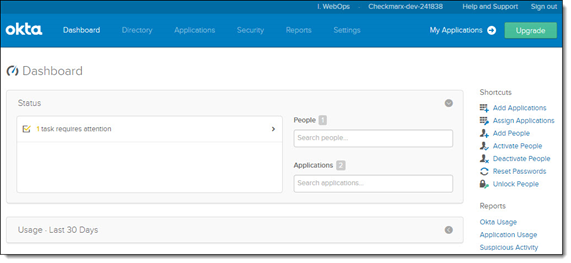
Select the Applications tab and choose Applications. The Applications screen is displayed.
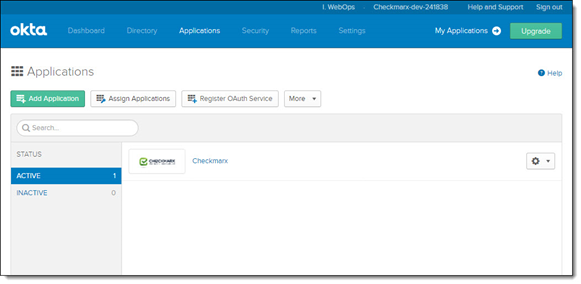
Click <Add Applications>. The Add Application screen is displayed.

Click <Create New App>. The Create a New Application Integration screen is displayed.
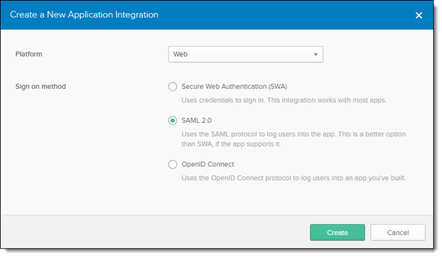
For Platform, select Web and select SAML 2.0.
Click <Create> to continue. The Create SAML Integration screen is displayed.
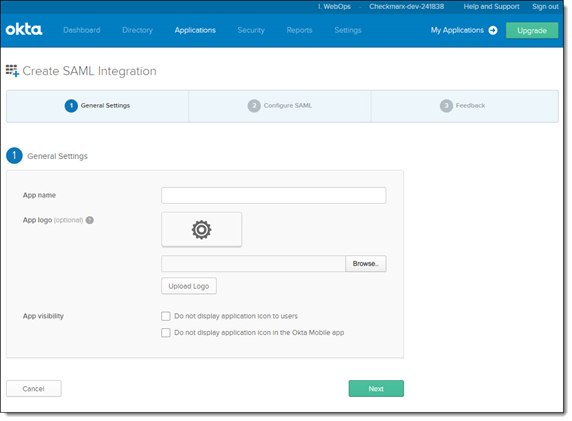
Enter Codebashing under App Name.
Click <Browse> and navigate to your preferred logo.
Click <Upload Logo> and define the App visibility settings accordingly.
Click <Next> to continue. The SAML Settings screen is displayed.
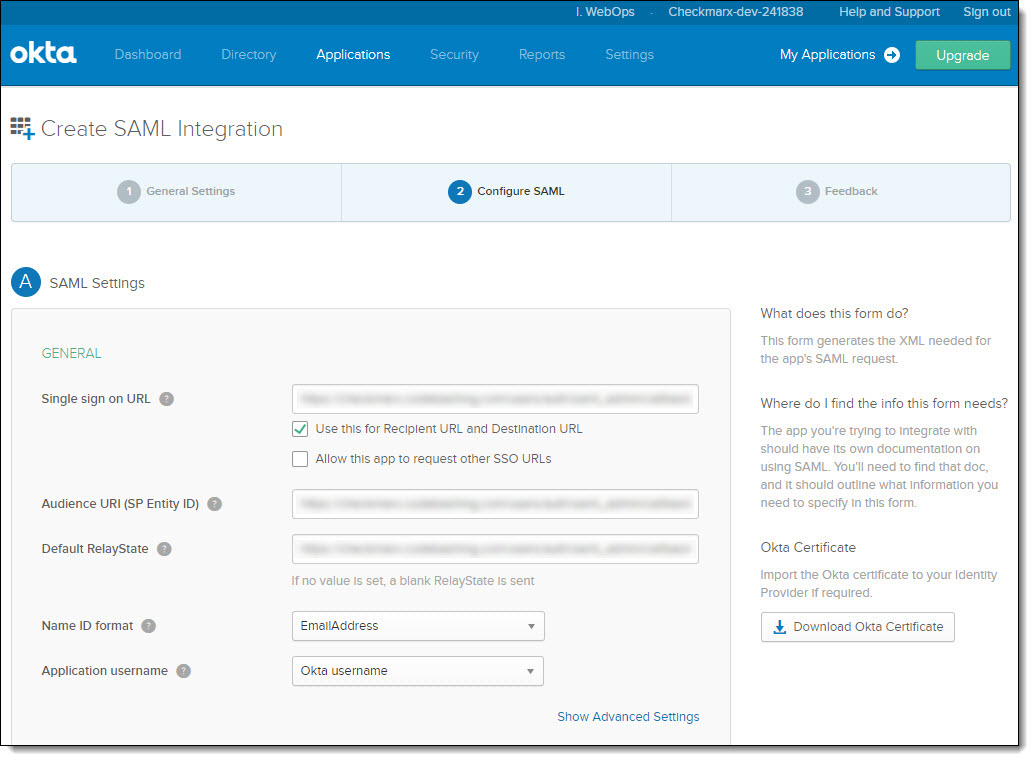
Add the relevant URLs to the following fields:
Single sign-on URL – https://<CB tenant name>.codebashing.com/users/auth/saml/callback
Audience URI (SP Identity ID) – https:// <CB tenant name>.codebashing.com/
Default RelayState – https://<CB tenant name>.codebashing.com/users/auth/saml/callback
Note
Replace the <CB tenant name> in the URL with your Codebashing tenant name, for example, Checkmarx.
Click the Name ID format drop-down and select EmailAddress.
Click <Next> to continue. The Feedback screen is displayed.
On the Feedback screen, select I'm an Okta customer adding an internal app , and click <Finish>. The New Application screen is displayed.
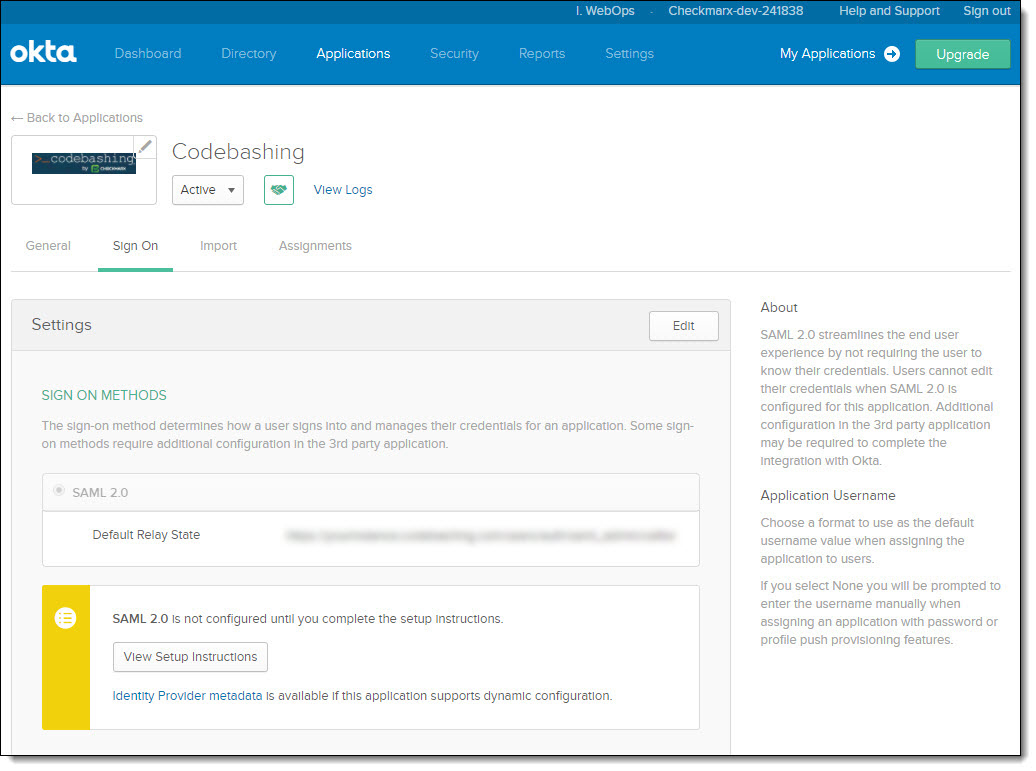
Note
The configuration of Codebashing is performed by the Checkmarx CloudOps team and the relevant information is stored in order to complete the configuration process.
Click the Identity Provider metadata link. The metadata.xml file is downloaded to your default download folder.
Send this metadata file to Checkmarx via a Tech Support ticket in order to complete the configuration of Codebashing.
Assigning Users to the Service Provider Application in OKTA
Once the connection between OKTA and Codebashing has been defined, users can be assigned to the service provider application in OKTA.
To assign users to the service provider application in OKTA:
From the Applications screen, click on your application. The Assignments screen is displayed.
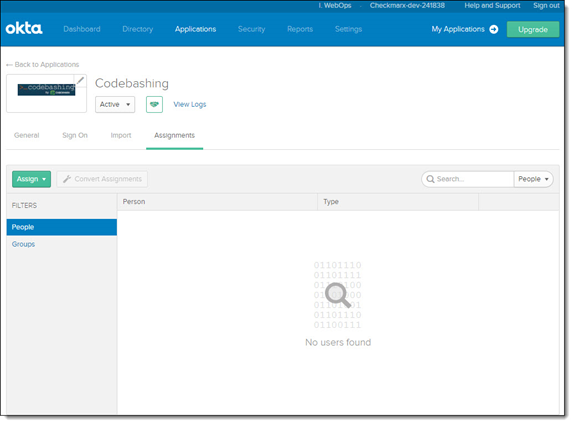
Click <Assign> and select People. The Assign <Application> to People screen is displayed.
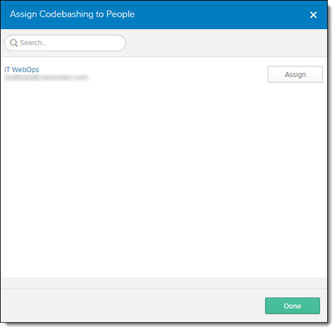
Assign each user to the application by clicking <Assign>.
Click <Save> and go back to assign the next user.
Click <Done> to save the changes.
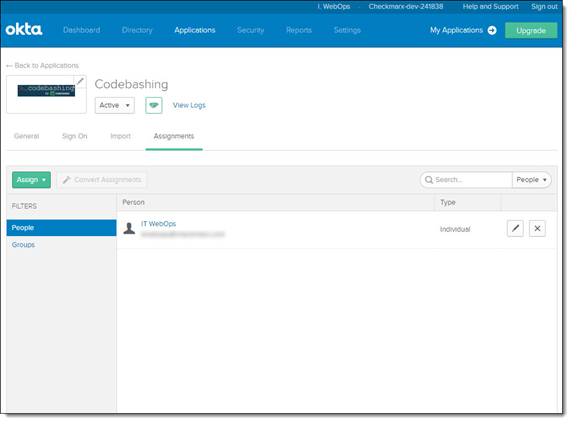
Confirm that each user has been assigned to the application.
Testing Single Sign-On with OKTA
To test single sign-on with OKTA:
Access https://<CB tenant name>.codebashing.com and click Login. You will be redirected to your organization's OKTA login page when accessing the platform externally or to a login popup when accessing it internally.
Enter your credentials to access the platform.