Vulnerability Details
The vulnerability details window can be accessed through the Vulnerabilities or Project KPIs pages.
The information presented for the vulnerabilities depends on whether it was accessed through Vulnerabilities or Project KPIs. All the applied filters are inherited from the dashboard's main screen.
Vulnerability KPIs
Open Vulnerabilities List
The open vulnerabilities list displays the following details for each vulnerability:
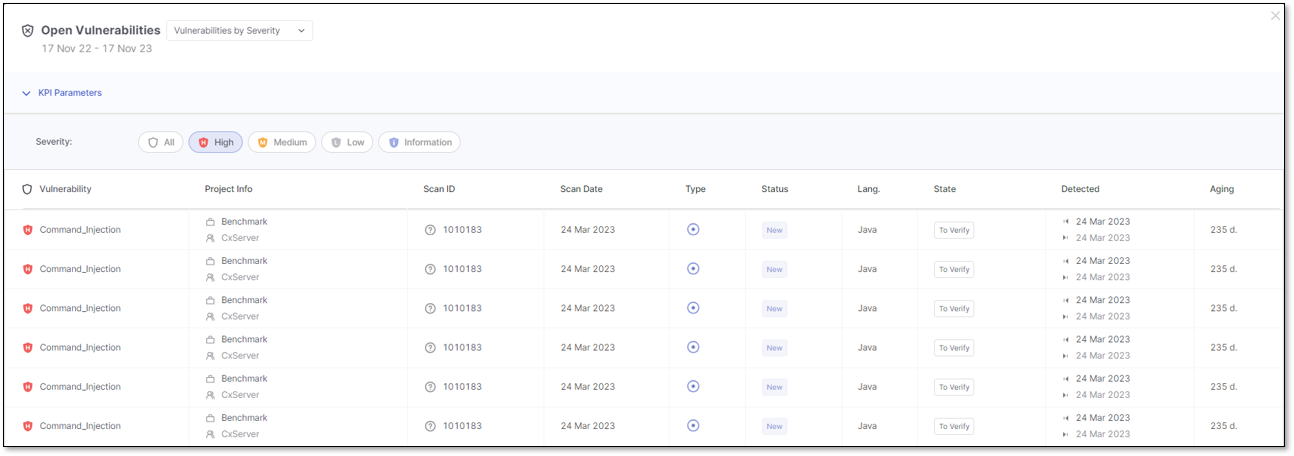 |
Severity and Vulnerability Name
The Vulnerability Name is interactive; clicking it opens a new page with a detailed description.
Project Information, including:
 Project Name
Project Name Team Name
Team Name
Scan Identifier
The Scan ID is interactive; clicking on it opens a new page featuring the Results Viewer, which directs you to the specific result.
By hovering over the ? additional details are available for:
CWE
Similarity ID
Query Path
Query Version
Scan Date
Scan Type
 represents a full scan
represents a full scan represents an incremental scan
represents an incremental scan
Status (new or recurrent)
Language
State
Detected
First Detection Date
Last Detection Date
Vulnerability aging, measured in days
Vulnerabilities by Severity
When the Vulnerabilities by Severity KPI triggers the Open Vulnerability details window, the applied filter for the list of vulnerabilities is based on the Severity level.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the severity selected in Vulnerabilities by Severity KPI.
Click on the severity level to highlight it in blue and apply the severity level filter. Click again to remove the filter and its highlight.
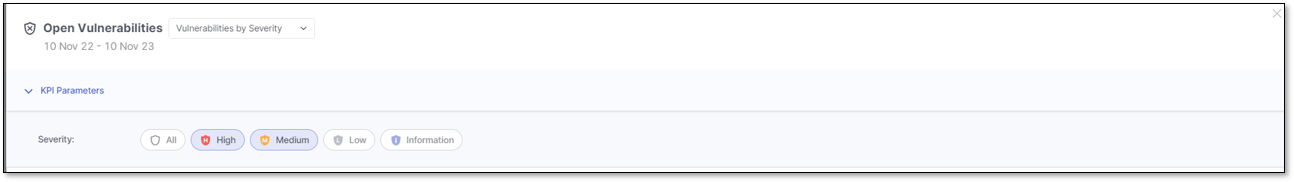 |
In the image above, the applied filters include High and Medium vulnerabilities, while Low and Information vulnerabilities are excluded.
Vulnerabilities by Status
When the Vulnerabilities by Status KPI triggers the Open Vulnerability details window, the applied filter for the list of vulnerabilities is based on the Status.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the status selected in Vulnerabilities by Status KPI.
Click on the status to highlight it in blue and apply the status filter. Click again to remove the filter and its highlight.
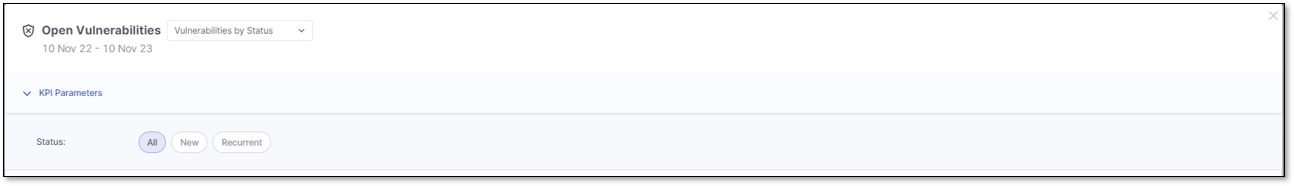 |
In the image above, the applied filters include All available statuses.
Vulnerabilities by State
When the Vulnerabilities by State KPI triggers the Open Vulnerability details window, the applied filter for the list of vulnerabilities is based on the State, including custom states.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the state selected in Vulnerabilities by State KPI.
Click on the state to highlight it in blue and apply the state filter. Click again to remove the filter and its highlight.
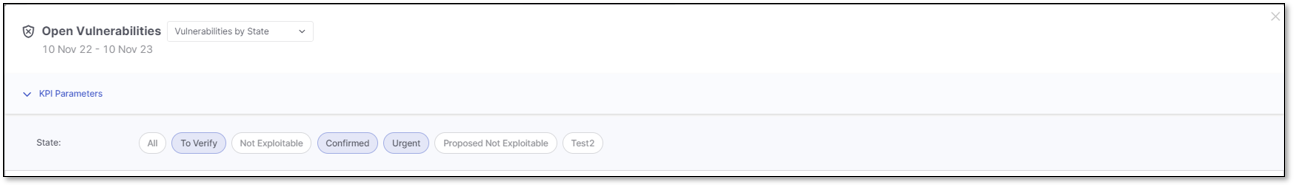
In the image above, the applied filters include Confirmed, Urgent, and To Verify vulnerabilities, while others are excluded.
Vulnerabilities by Severity and State
When the Vulnerabilities by Severity and State KPI triggers the Open Vulnerability details window, the applied filter for the list of vulnerabilities is based on the severity and state.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the severity and state selected in Vulnerabilities by Severity and State KPI.
Click on the severity and/or state to highlight it in blue and apply the severity and/or state filter. Click again to remove it and its highlight.
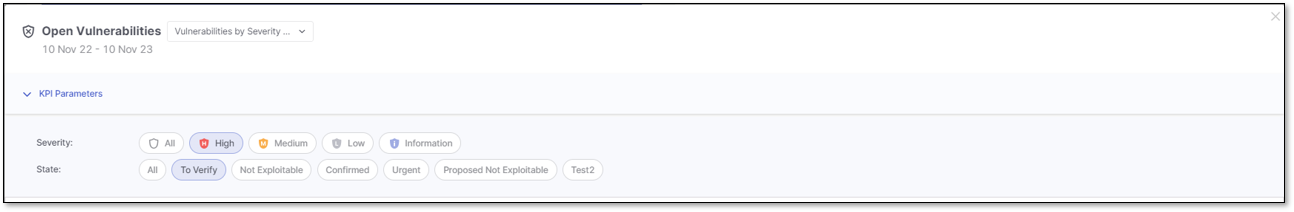
In the image above, the applied filters include To Verify (State) and High (Severity), while others are excluded.
Top 20 Oldest Vulnerabilities
When the Top 20 Oldest Vulnerabilities KPI triggers the Open Vulnerability details window, the applied filter for the list of vulnerabilities is based on the Vulnerability Name and the Severity level.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the vulnerability name and severity selected in the Top 20 Oldest Vulnerabilities KPI.
Click on the specific vulnerabilities and/or severity to highlight them in blue and apply their filter. Click again to remove it and its highlight.
The displayed list of vulnerabilities to filter is determined by the top 20 oldest KPIs.
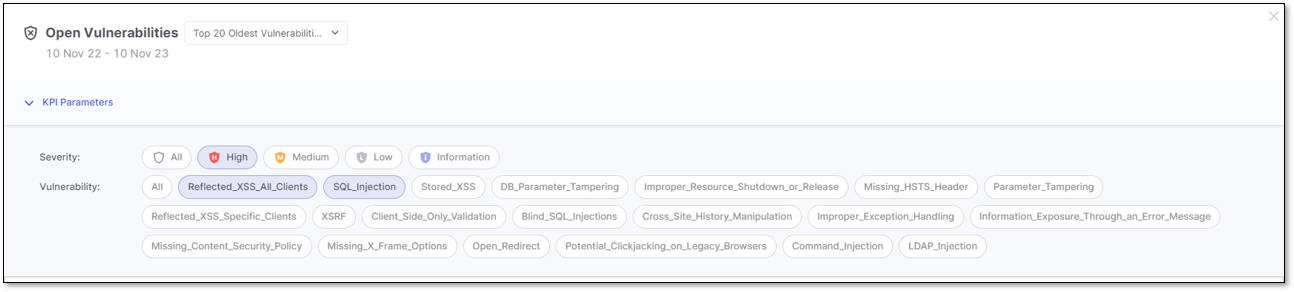
In the image above, the applied filters include Reflected_XSS and SQL_Injection vulnerabilities and High severity, while others are excluded.
Top 20 Vulnerabilities
When the Top 20 Vulnerabilities KPI triggers the Open Vulnerability details window, the applied filter for the list of vulnerabilities is based on the Status.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the vulnerability name and severity selected in the Top 20 Vulnerabilities KPI.
Click on the specific vulnerabilities and/or severity to highlight them in blue and apply their filter. Click again to remove it and its highlight.
The displayed list of vulnerabilities to filter is determined by the top 20 KPIs.
Resolved Vulnerabilities List
The resolved vulnerabilities list shows the following details for each vulnerability:
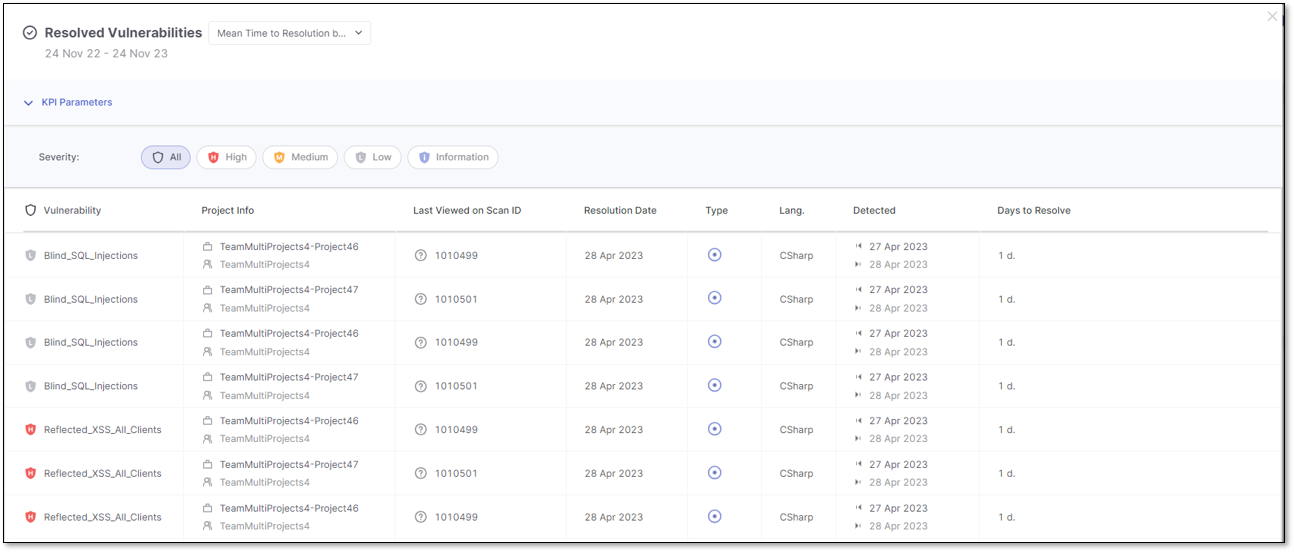
Severity and Vulnerability Name
Project Information:
 Project Name
Project Name : Team Name
: Team Name
Last Viewed on Scan ID, which displays the identifier of the last scan where the result was detected
By hovering over the ? additional details are available for:
CWE
Similarity Id
Query Path
Query Version
Resolution Date
Scan Type
 represents a full scan
represents a full scan represents an incremental scan
represents an incremental scan
Language
Detected
First Detection Date
Last Detection Date
Days to Resolve, measured in days
Mean Time to Resolution
When the Mean Time to Resolution (MTTR) KPI triggers the Resolved Vulnerability details window, the applied filter for the list of vulnerabilities is based on the Severity level.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the severity selected in the MTTR KPI.
Click on the severity level to highlight it in blue and apply its filter. Click again to remove the filter and its highlight.
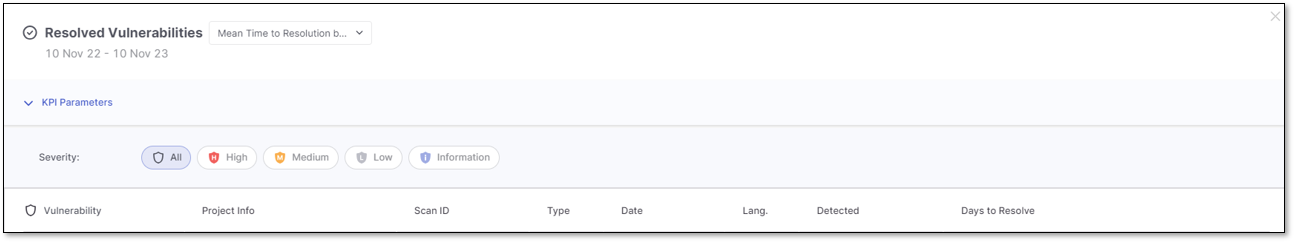
In the image above, the applied filters include the resolved vulnerabilities for all the severity levels.
Project KPIs
Open Vulnerabilities List
The open vulnerabilities list shows the following details for each vulnerability:
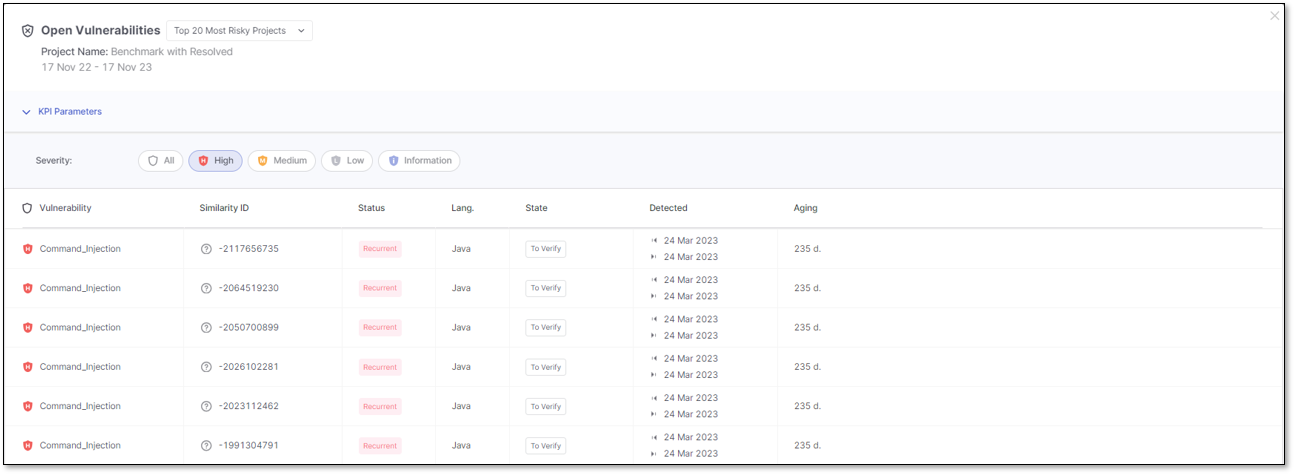
Severity and Vulnerability Name
The Vulnerability Name is interactive; clicking it opens a new page with a detailed description.
Similarity ID
The Similarity ID is interactive; clicking it opens a new page featuring the Results Viewer, which directs you to the specific result.
By hovering over the ? additional details are available for:
CWE
Query Path
Query Version
Status (new or recurrent)
Language
State
Detected
First Detection Date
Last Detection Date
Vulnerability aging (measured in days)
Vulnerabilities by Project
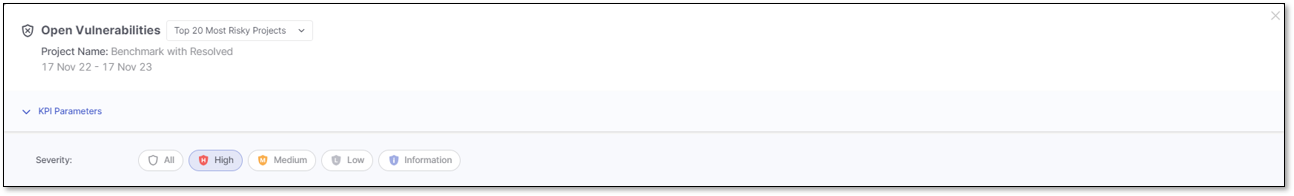
When the Top 20 Most Risky Projects KPI, the Top 20 Least Risky Projects, or the Open Vulnerabilities KPIs trigger the Open Vulnerability details window, the applied filter for the list of vulnerabilities is based on the Severity level.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the project name and the severity selected in the previous KPI.
Click on the severity level to highlight it in blue and apply its filter. Click again to remove the filter and its highlight.
Resolved Vulnerabilities List
The resolved vulnerabilities list below displays the following details for each vulnerability:
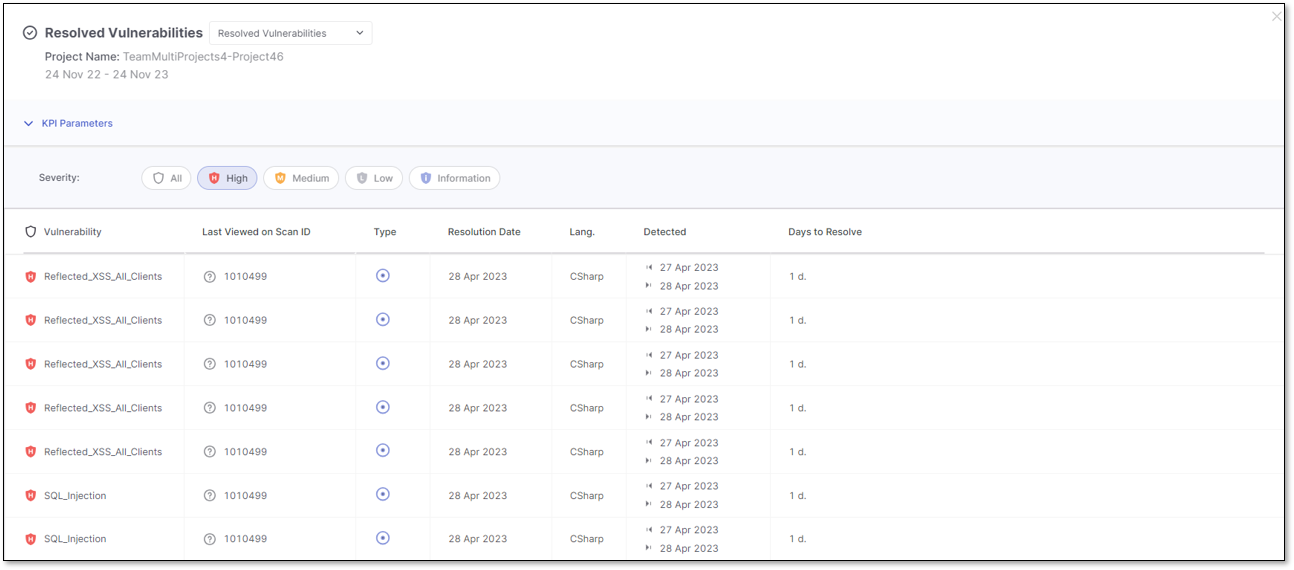
Severity and Vulnerability Name
Last Viewed on Scan ID, which displays the identifier of the last scan where the result was detected
By hovering over the ? additional details are available for:
CWE
Similarity ID
Query Path
Query Version
Scan Type
 represents a full scan
represents a full scan represents an incremental scan
represents an incremental scan
Resolution Date
Language
Detected
First Detection Date
Last Detection Date
Days to Resolve (measured in days)
Resolved Vulnerabilities by Project
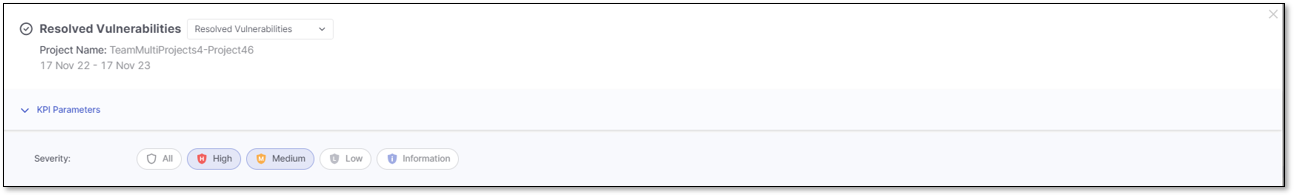
When the Resolved Vulnerabilities KPI triggers the Resolved Vulnerability details window, the applied filter for the list of vulnerabilities is based on the Severity level.
You can narrow down the list of vulnerabilities by setting filters in the KPI Parameters section. By default, the applied filters are inherited from the project name and the severity selected in the Resolved Vulnerabilities KPI.
Click on the severity level to highlight it in blue and apply its filter. Click again to remove the filter and its highlight.
Change between KPIs
As described above, the drop-down list is available in the header of the Vulnerabilities list and enables you to modify the results using various filters.
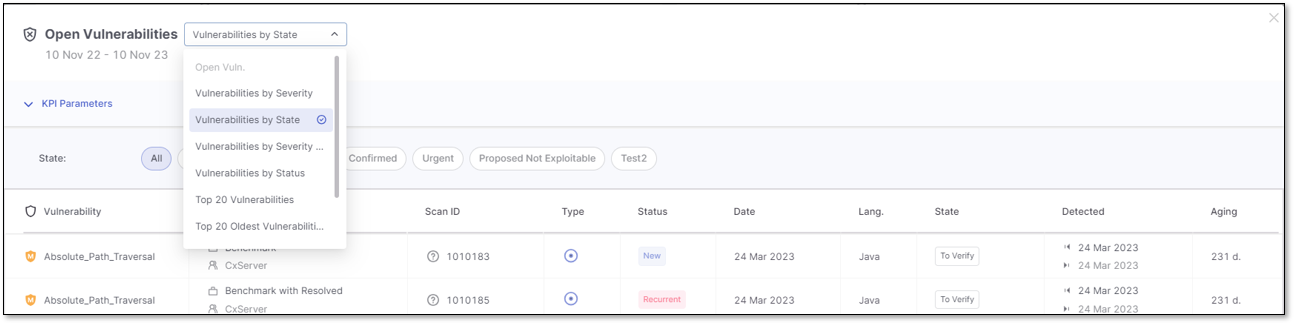
The above image presents the vulnerabilities according to their State, with the currently selected KPI highlighted in blue. To choose a different KPI, select it from the list.