- Checkmarx Documentation
- Checkmarx SAST
- SAST User Guide
- Scan Results
- Scan Results Example
Scan Results Example
The following is an example of the scan results showing an SQL Injection vulnerability.
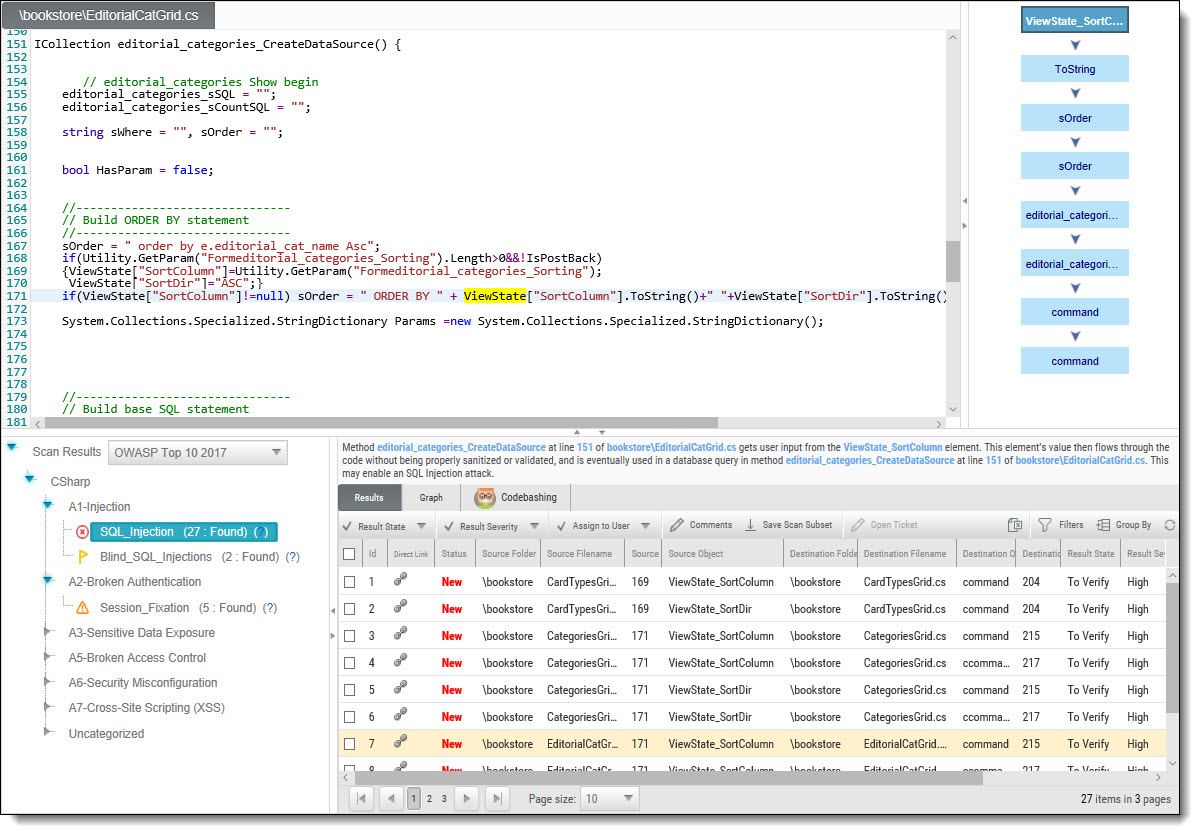
An SQL_Injection vulnerability exists when user input is used in the syntax of an SQL query. Since those inputs could be interpreted as SQL syntax rather than user input, a user could manipulate the input in such a way as to alter query logic, potentially bypassing security checks and modifying the database, including the execution of system commands.
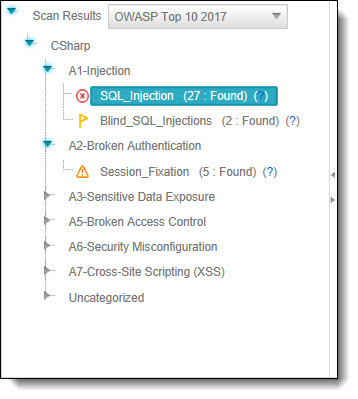
The Queries pane (bottom-left) shows that 27 instances of the SQL_Injection vulnerability were found.
Clicking (  ) takes you to Codebashing, where you can learn more about the selected vulnerability, why it happens, and how to eliminate it.
) takes you to Codebashing, where you can learn more about the selected vulnerability, why it happens, and how to eliminate it.
Codebashing™
Codebashing provides developers with a new in-context learning platform that sharpens the skills they need to fix vulnerabilities and write secure code. This new approach makes AppSec learning an engaging experience, more effective, with a fast learning curve.
Codebashing is currently available as a free limited edition to all users. This version includes a free edition of Codebashing covering:
Lessons: SQL Injection (SQLi), Cross-site scripting (XSS), XML Injection (XXE)
Languages: Java, .Net, PHP, Node.JS, Ruby, Python
The full and paid version will include over 20+ lessons and additional languages:
Lessons: Session fixation, Use of insufficiently random values, Reflected XSS, Command Injection, DOM XSS, Directory (Path) Traversal, Privileged Interface Exposure, Leftover Debug Code, Session Exposure in URL, User Enumeration, Horizontal Privilege Escalation, Vertical Privilege Escalation, Authentication Credentials in URL, Cross Site Request Forgery (POST), Cross Site Request Forgery (GET), Click Jacking, Insecure URL Direct.
Languages: Scala, C/C++.
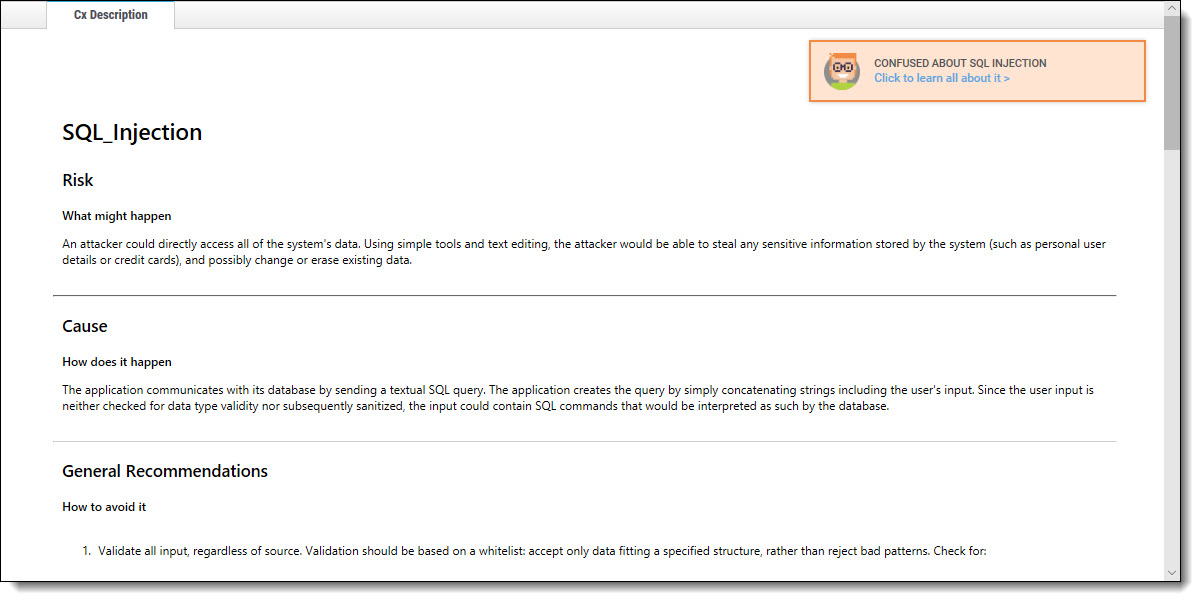
Clicking (?) displays full general information for the SQL_Injection, including risk, cause, and recommendations with code examples.
Selecting a specific instance of the vulnerability in the Results pane (bottom, center, and right) displays the instance's code details at the top of the pane, and displays the path of component code elements in the Path pane (top-right). The Path pane shows all the code elements leading from the user input to the SQL query. Selecting each element in turn displays and highlights the element in the code context in the Source Code pane (top, left, and center). The vulnerability needs to be eliminated somewhere along that path.