- Checkmarx Documentation
- SAST/SCA Integrations
- CI/CD Plugins
- Bamboo Plugin
- Configuring a Scan Task in Bamboo
Configuring a Scan Task in Bamboo
The Atlassian Bamboo workflow uses the concept of a 'plan' with 'jobs' and 'tasks' to configure and order the actions in the workflow. A task is generally a small unit in a workflow, such as a source code checkout, running a script, or parsing test results.
In our case, a task is a Checkmarx scan configured from within Atlassian Bamboo.
Notice
The Bamboo plugin scan user must have permissions for both the Scanner and Reviewer roles.
To access the Atlassian Bamboo account:
Enter the Base Bamboo URL. The Build Dashboard window is displayed.
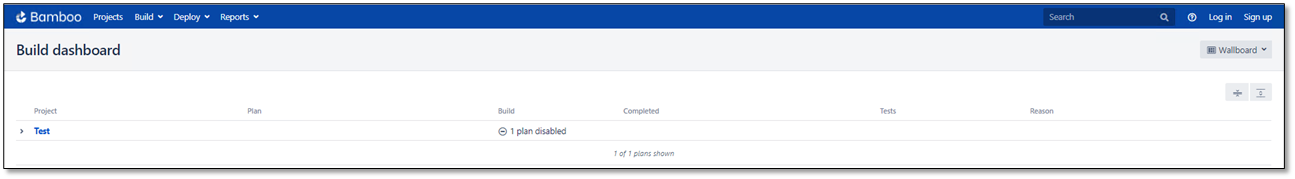
To create a plan:
Click
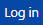 and provide your username and password to log in. The Create menu becomes available.
and provide your username and password to log in. The Create menu becomes available.
Refer to Creating a plan in the Bamboo documentation for further information.
To add a Checkmarx scan task to an existing plan:
Notice
You select the global settings if you want to use pre-configured defaults for your scan. These global settings must be set up as explained before you can start configuring this task.
In the line of the respective project, click Edit
 .
.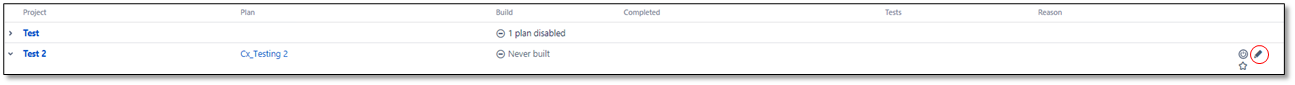
The plan's content (list of jobs) appears.
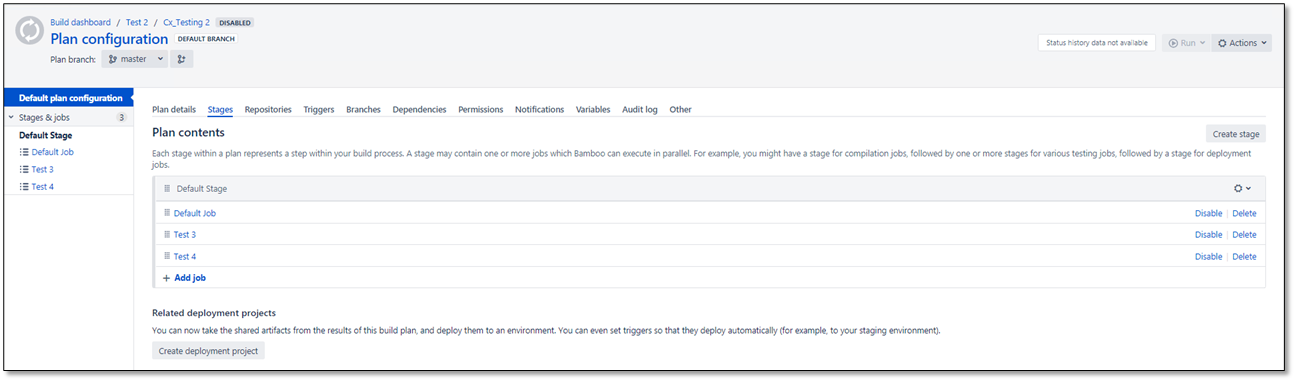
Select the job to which you want to add the task, for example, to
 Test 4. You are asked to add a task.
Test 4. You are asked to add a task.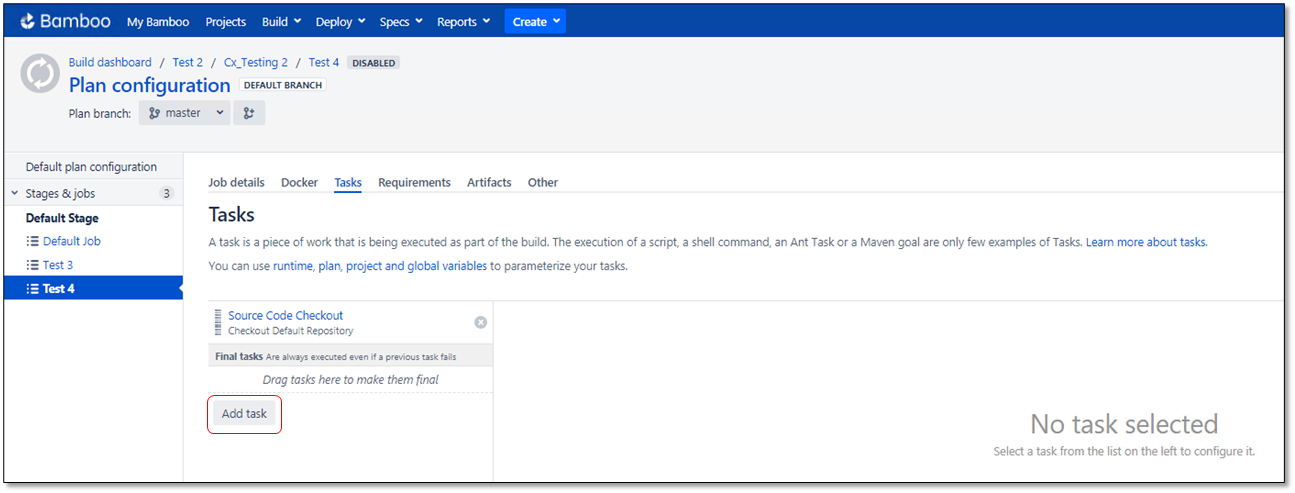
Click <Add Task>. The Task Types window is displayed.
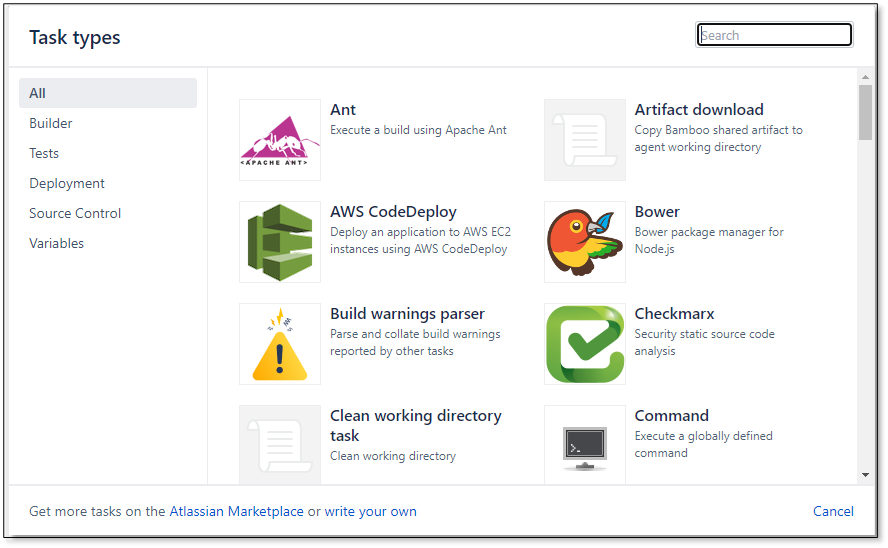
Select the
 Checkmarx task. The Checkmarx Task Configuration dialog is displayed.
Checkmarx task. The Checkmarx Task Configuration dialog is displayed.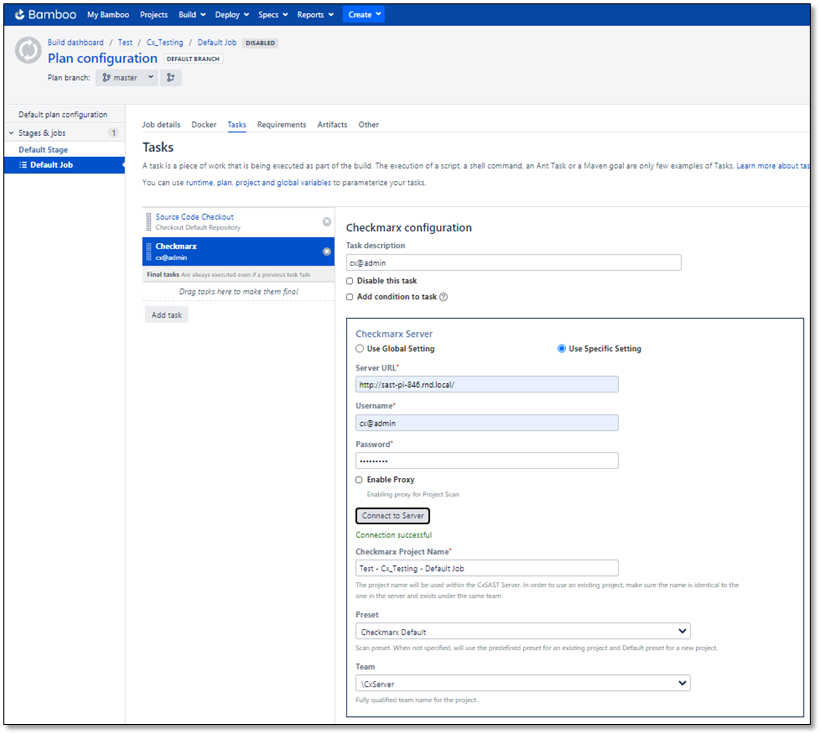
In the Checkmarx Task Configuration dialog, define the Checkmarx Configuration parameters illustrated and listed in the table below.
To save the changes, click <Save>. The Checkmarx Scan Task is displayed in the Plan Configuration dialog.
Parameter | Description |
|---|---|
Task Description | Enter a description for the task. |
Disable this Task | Check to disable this task when the next one is built. |
Add Condition to Task | Check to add a condition to this task. |
Checkmarx Server | |
Use Global Setting | Select Use Global Setting to use the default server credentials. For further information, refer to Configuring the Checkmarx Bamboo Plugin Global Settings. |
Use Specific Setting | Select Use Specific Setting and then enter the server URL and credentials that override the default settings as outlined below. |
Server URL | Enter the Checkmarx Server URL or IP address with or without a port, for example, http://<server-name>, https://<ip address>:port NoticeAvailable only if Use Specific Setting is selected. |
Username | Enter a login username. NoticeAvailable only if Use Specific Setting is selected. |
Password | Enter a login password. NoticeAvailable only if Use Specific Setting is selected. |
Enable Proxy | Check to enable a project scan via a proxy server. |
<Connect to Server> | Click <Connect to Server> and wait until the credentials are validated and the Success status is indicated. NoticeAvailable only if Use Specific Setting is selected. |
Checkmarx Project Name | Enter the relevant project name. The project name is used in the CxSAST Server. To use an existing project, make sure the name is identical to the one in CxSAST, and that the project exists under the same team you define. |
Preset | Select a scan preset for the project. If the preset is not specified, the default preset will be used. NoticeIf the Preset list is not updated or empty, click <Connect to Server> to refresh the list. |
Team | Enter the relevant team name for the project. |
Checkmarx CxSAST Scan | |
Enable SAST Scan | When set to Enabled, the Checkmarx SAST scan settings are available, and the SAST scan for this job/project is initiated. In the existing plans, SAST is enabled by default. |
Use Global Setting | Select Use Global Setting to use the default server credentials. For further information, refer to Configuring the Checkmarx Bamboo Plugin Global Settings . |
Use Specific Setting | Select Use Specific Setting and then enter the server URL and credentials that override the default settings as outlined below. |
Folder Exclusion | Define a comma-separated list of folders to exclude from the scan. Entries in this list are automatically converted to exclude wildcard patterns and appended to the full pattern list provided in the Include/Exclude Wildcard Patterns section. NoticeAvailable only if Use Specific Setting is selected. |
Include / Exclude Wildcard Patterns | Define the include/exclude wildcard patterns as explained in the instructions under the field. NoticeAvailable only if Use Specific Setting is selected. |
Scan Timeout In Minutes | Define the scan timeout threshold. NoticeAvailable only if Use Specific Setting is selected. |
Comment | Enter an optional remark for the Checkmarx CxSAST scan. You may use Bamboo variables, e.g., ${bamboo.buildNumber} or ${bamboo.buildPlanName} as part of the comment. NoticeAvailable only if Use Specific Setting is selected. |
Enable Incremental Scan | Check to enable incremental scan. This scans only new and modified files relative to the project's previous scan. |
Schedule Interval-based Full Scans | Check to enable the scheduling of interval-based full scans and define the required time range. This option enables periodic full scans according to the defined time range when performing incremental scans. For example, this could ensure that daily runs are incremental scans and nightly builds are full scans without separating jobs. NoticeAvailable only if Enable incremental Scan is selected. |
Force Scan | Enabling this parameter forces a SAST server to perform a full scan regardless of whether code changes exist. The Force Scan and Enable Incremental Scan parameters are mutually exclusive. |
Generate CxSAST PDF Report | Check to generate a CxSAST scan result report in PDF format. The scan results include a link to the report. NoticeAvailable only if Enable Synchronous Mode is selected. To generate a PDF on the Bamboo server and remote agent, ensure the following: (Access Edit Artifacts by selecting Actions, Configure plan, Default Job, Artifacts, and then Create Artifact).
|
Dependency Scan | |
Enable Dependency Scan | Check to enable packages from various dependency managers, such as NPM, Nugget, Python, and others, that are being scanned. NoticeTo use this option, NPM, Nuget, and/or Python must be installed on every Bamboo worker and/or orchestrator instance running the job. |
Override Global Dependency Scan Settings | Check to use specific settings for this task. These settings override the global settings. NoticeAvailable only if Enable Dependency Scan is selected. |
Include/Exclude Wildcard Patterns | Define the include/exclude wildcard patterns as explained in the instructions under the field. NoticeAvailable only if Enable Dependency Scan and Override Global Dependency Scan Settings are selected. |
Folder Exclusion | Define a comma-separated list of folders to exclude from the scan. Entries in this list are automatically converted to exclude wildcard patterns and appended to the full pattern list provided in the Include/Exclude Wildcard Patterns section. NoticeAvailable only if Enable Dependency Scan and Override Global Dependency Scan Settings are checked. |
Use CxOSA Dependency Scanner | Select Use CxOSA Dependency Scanner to enable and configure CxOSA scans. |
Use CxSCA Dependency Scanner | Select Use CxSCA Dependency Scanner to enable and configure CxSCA scans. |
Checkmarx Scan CxOSA | These parameters show if Use CxOSA Dependency Scanner has been selected. |
OSA Archive Include Wildcard Patterns | Define the included wildcard patterns as explained in the instructions under the field. |
Execute Dependency Managers 'Install Packages' Command before Scan | Check to enable packages from various dependency managers, such as NPM, Nugget, Go, and others, that are being scanned as part of the CxOSA scan. NoticeTo use this option, NPM, Nuget, and/or Python must be installed on every Bamboo worker and/or orchestrator instance running the job. |
Checkmarx Scan CxSCA | These parameters appear if Use CxSCA Dependency Scanner has been selected. |
CxSCA Web API URL | Enter the server name that interacts with CxSCA using API calls, for example, https://api-sca.company.com . |
Access Control Server URL | Enter the server that hosts the Access Control portal used to access CxSCA, for example, https://platform.company.com . |
CxSCA Web App URL | Enter the URL of the web-based application that serves as the CxSCA user interface, for example, https://sca.company.com . Entering this URL generates a link to a page with CxSCA scan results. If this option is not entered, no such link is generated. |
Account | Enter the CxSCA customer account. |
CxSCA User | Enter the CxSCA user name. |
CxSCA Password | Enter the CxSCA password. |
<Connect to Server> | Click to connect to the CxSCA server. |
Enable SCA Resolver | Enable the SCA resolver utility to perform dependency resolution. For additional information on this utility, refer to Checkmarx SCA Resolver. |
SCA Resolver Path | When using the SCA Resolver utility, define the path to the SCA Resolver folder where ScaResolve.exe resides. Depending on your operating system, the path to ScaResolver is, for example, C:\Users\Installations\ScaResolver-win64 or /opt/ScaResolver-linux64. NoteThis option is available only if Enable SCA Resolver is checked. The plugin will automatically determine values for mandatory arguments to ScaResolver to perform Dependency Resolution and Exploitable Path. These arguments are:
The plugin will also automatically determine the values for the following Exploitable Path parameters:
--sast-result-path and and -r/ –resolver-result-path can be overridden. It can be either a directory or an absolute path. Dependency resolution output and exploitable path results will be saved in the .cxsca-results.json and .cxsca-sast-results.json files respectively. The SCA Resolver Additional Parameters” fields can supply any additional ScaResolver parameters other than the ones described above. For example, to change the log level of ScaResolver, the following value can be provided in this field: --log-level Debug The syntax of the ScaResolver parameter must be exactly what the ScaResolver tool expects. The SCA Resolver configuration settings can be defined globally and overridden at the Plan level. |
Control Checkmarx Scan | |
Use Global Setting | Select Use Global Setting to use the default server credentials. For further information, refer to Configuring the Checkmarx Bamboo Plugin Global Settings . |
Use Specific Setting | Select Use Specific Setting and then enter the server URL and credentials that override the default settings as outlined below. |
Enable Synchronous Mode |
Notice
|
Enable Projects Policy Enforcement | If checked, the build is marked as failed or unstable if the project's policy is violated. NoticePolicies are assigned to a project from within CxSAST. |
Enable CxSAST Vulnerability Thresholds | If checked, you may define thresholds for low, medium, and high severity vulnerabilities above which the build is considered failed. If cleared, no thresholds are defined. NoticeAvailable only if Use Specific Setting is selected. |
CxSAST Critical | Set the threshold for critical severity thresholds. NoteAvailable only if Enable CxSAST Vulnerability Thresholds is checked and if CxSAST Server is 9.7 version and above. |
CxSAST High | Set the threshold for high severity thresholds. NoticeAvailable only if Enable CxSAST Vulnerability Thresholdsis checked. |
CxSAST Medium | Set the threshold for medium severity thresholds. NoticeAvailable only if Enable CxSAST Vulnerability Thresholdsis checked. |
CxSAST Low | Set the threshold for low severity thresholds. NoticeAvailable only if Enable CxSAST Vulnerability Thresholdsis checked. |
Enable Dependency Scan Vulnerability Thresholds | If checked, you may define thresholds for low, medium, and high-severity vulnerabilities in addition to the defined dependencies. Crossing the defined thresholds causes the build to be considered failed. If cleared, no thresholds are defined. |
Dependency scan critical severity vulnerabilities threshold | Set the threshold for Critical severity thresholds. Notice
|
Dependency scan high severity vulnerabilities threshold | Set the threshold for high severity thresholds. NoticeAvailable only if Enable Synchronous Mode and Enable Dependency Scan Vulnerability Thresholdsare checked. |
Dependency scan medium severity vulnerabilities threshold | Set the threshold for medium severity thresholds. NoticeAvailable only if Enable Synchronous Mode and Enable Dependency Scan Vulnerability Thresholdsare checked. |
Dependency scan low severity vulnerabilities threshold | Set the threshold for low severity thresholds. NoticeAvailable only if Enable Synchronous Mode and Enable Dependency Scan Vulnerability Thresholdsare checked. |
Deny new Checkmarx Projects Creation | This parameter only applies to global settings and is unavailable for specific settings. |
Hide Results | This parameter applies to the global settings only and is unavailable for specific settings. |
Notice
If you need to edit the scan task configuration parameters, click the Checkmarx scan task and make the changes.
You can now run your plan according to your current development procedure. Refer to Running a Plan in the Atlassian Bamboo Documentation.