- Checkmarx Documentation
- SAST/SCA Integrations
- IDE Plugins
- Visual Studio Plugin
- Reviewing Scan Results in Visual Studio
- Example of Scan Results in Visual Studio
Example of Scan Results in Visual Studio
The following is an example of scan results in Visual Studio showing SQL Injection vulnerability instances. A developer looks at the CxViewer Tree, and sees that the code contains 66 (!) instances of SQL Injection:
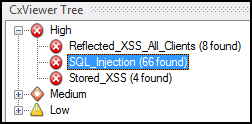
An SQL Injection vulnerability exists when user input is used in the syntax of an SQL query. Since those inputs could be interpreted as SQL syntax rather than user input, a user could manipulate the input in a way as to alter query logic, potentially bypassing security checks and modifying the database, including the execution of system commands and proceeds as follows:
Getting an overview of all 66 instances as illustrated below.
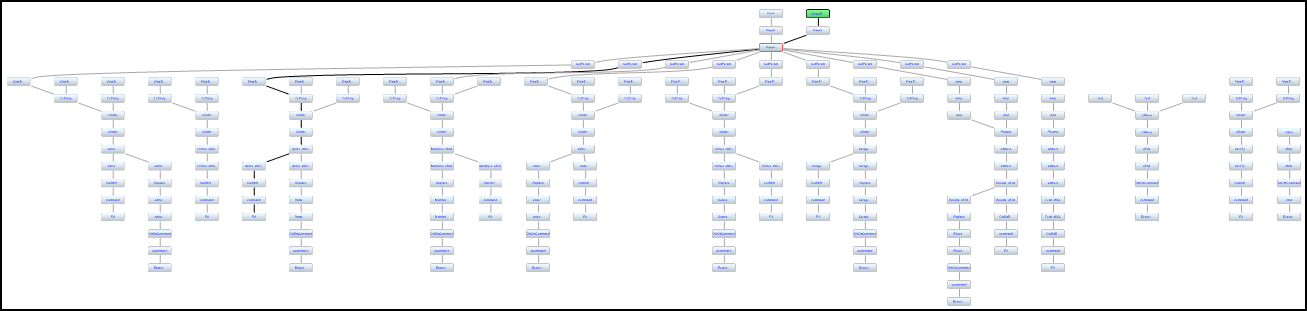
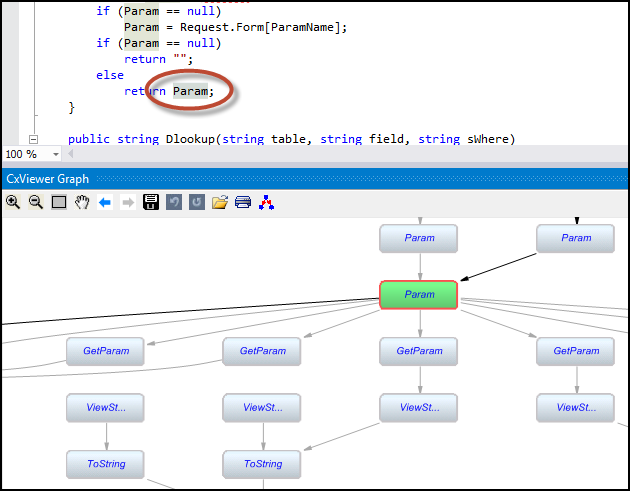
Focussing on the red-bordered element at the top of a large part of the graph. It looks like by securing that point in the code, most of the vulnerability instances get eliminated.
Zooming in on and clicking the red-bordered element, so as to see its code in the context as illustrated below. The developer can now secure the code.