Checkmarx One JFrog Plugin
Overview
The Checkmarx One JFrog plugin analyzes each of the open source packages in your JFrog artifactory, comparing them against our Software Composition Analysis (SCA) vulnerability database in order to identify security risks and license requirements. The findings are added as "cx" properties to each artifact, enriching the metadata displayed in the Artifactory UI. This provides seamless risk visibility within your DevOps workflow, helping you to identify and address vulnerabilities early in the development process.
The plugin allows you to configure compliance thresholds, so that artifacts exceeding these thresholds are automatically marked as non-compliant. Based on configuration, the plugin can enforce policies that block the download and use of such artifacts, helping prevent the consumption of insecure components.
Notice
Risks identified by this plugin are shown only in the artifactory itself, they are not synced with the Checkmarx One platform and corresponding projects are not created in your Checkmarx One account.
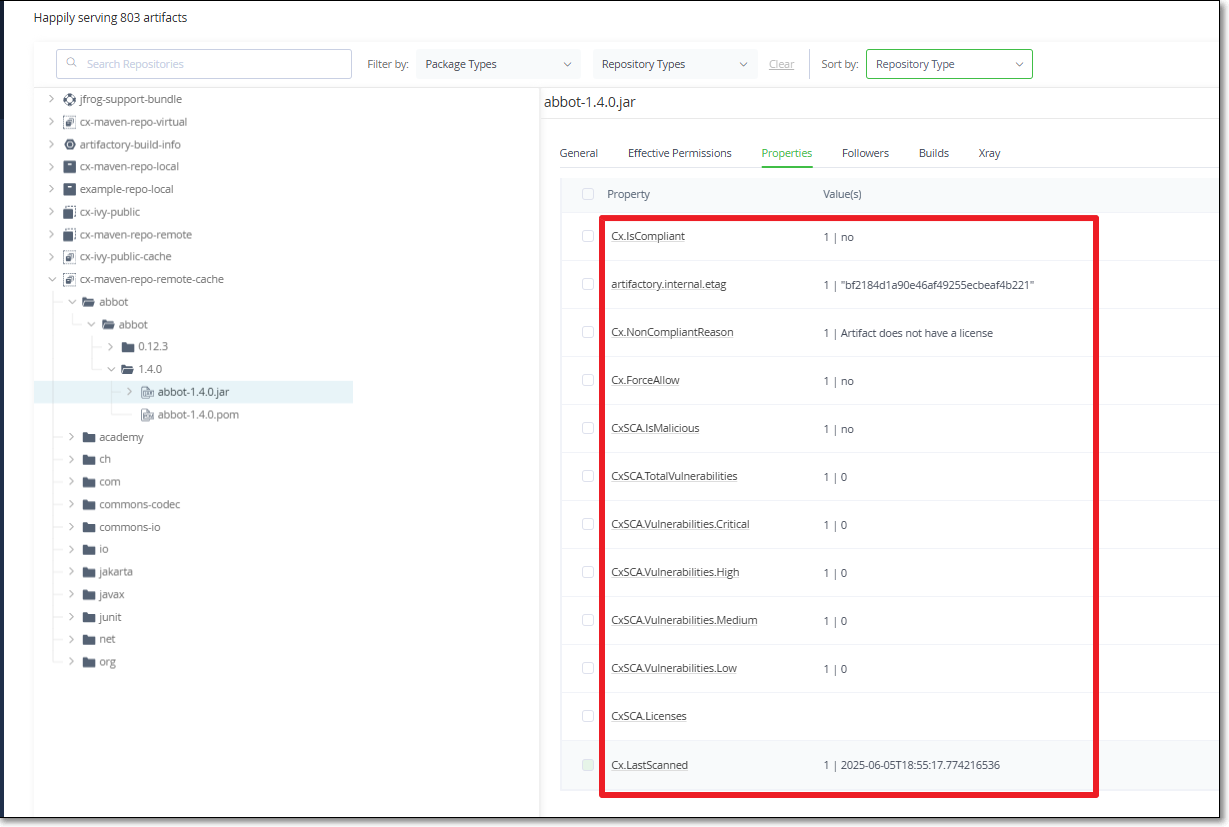
Analyzing Artifacts
There are 3 ways in which artifacts are analyzed, causing the "cx" properties to be populated:
Manual scan - An administrator can manually trigger a scan of all artifacts in the system or of specific repositories. An initial manual scan should be run as part of the installation process.
Adding repositories - When a user tries to add an artifact from a remote repository, if it doesn't yet have "cx" properties in JFrog, then it is automatically analyzed and the "cx" properties are populated.
Continuous evaluation - The plugin has a scheduled cron job that runs in the background to update the "cx" properties of your artifacts based on the latest vulnerability data in the Checkmarx SCA database. By default, these evaluations run once an hour. You can adjust this by editing the properties file as described below.
Notice
Analysis and enforcement are performed only on the artifact being downloaded. The plugin does not scan or enforce policy on transitive dependencies of that artifact.
Main Features
Validates the compliance of open source packages by analyzing licenses, identifying vulnerabilities, and detecting malicious components.
Evaluates artifacts against user-defined policies to ensure compliance with security standards related to malicious packages, vulnerabilities and licenses.
You can whitelist licenses approved by the organization. Any artifact with a license not included in this list will be flagged as violating the license compliance threshold.
Provides configurable policy enforcement to prevent the download and use of non-compliant artifacts, with actionable remediation feedback.
The plugin supports artifact scanning for specific user-defined repositories. One or more JFrog repository keys can be configured via the properties file to limit the scope of the scan.
The plugin includes a scheduled cron job that runs periodically in the background to coninuously evaluate risks related to your artifacts.
You can also periodically trigger manual scans of all artifacts within the configured repositories.
Prerequisites
Self-hosted JFrog Artifactory, version 7.90.14+
A Checkmarx One account
Important
Anyone with a valid Checkmarx One user account can use this plugin. There are no specific account permissions required.
To set up the integration you will need to provide the following account info:
Base URL of your Checkmarx One environment
Base Authentication URL of your Checkmarx One authentication server
Tenant name of your Checkmarx One tenant account
API Key - See Creating an API Key for Checkmarx One Integrations
Limitations
Properties are set on the main package artifact, not on sub-artifacts
Properties are applied to the artifact in the JFrog cache, not in the remote repository
Supported Package Managers
The plugin supports only projects that use the following package managers:
Bower, CocoaPods, Composer, Go, Gradle, Ivy, Maven, Npm, Nuget, Pypi, Sbt
Download Links
Download the latest version of the plugin here.
Installing and Configuring the Plugin
To install and configure the plugin:
Download the plugin using the above link.
Extract the archive.
The extracted folder contains a "plugins" folder with the following items:
checkmarxSecurityPlugin.groovycxsupplychainsecurity-plugin.propertieslib >
artifactory-checkmarx-security-core.jarlib >
checkmarxSecurityPlugin.version
Open the
cxsupplychainsecurity-plugin.propertiesfile.Configure access to your Checkmarx One account by entering your account info (see Prerequesites above) in the relevant properties as follows:
cxsca.api-key- API Keycxsca.cxurl- Base URLcxsca.base-auth-url- Base Authentication URLcxsca.tenant- Tenant name
The plugin is configured to run as-is, using default settings. You can edit the settings to adjust the following configurations, as described in Adjusting Property Configurations below:
Adjust thresholds for non-compliance (Default: Only malicious packages are non-compliant)
Block usage of non-compliant artifacts (Default: Not blocked)
Add or remove allowed licenses (Default: Allow only MIT,Apache 2.0,BSD 3,ISC,Zlib)
Specify repos for scanning (Default: All repos are scanned)
Adjust the analysis schedule (Default: every hour)
Once the configuration is completed, save the changes to apply them.
Copy the files from the plugin folder to your installed Artifactory directory at
${ARTIFACTORY_HOME}/var/etc/artifactory/plugins.If your JFrog instance is not configured to reload plugins automatically (this is the default configuration), then you will need to manually reload the plugins using the following command:
curl -u username:password -X POST " https://<JFrogURL>/artifactory/api/plugins/execute/checkmarxSecurityReload
To verify that the plugin has been installed successfully, log in to your JFrog Artifactory instance and navigate to Administrator > Platform Monitoring > Artifactory Logs (i.e., https://<JFrogURL>/ui/admin/artifactory/advanced/system_logs).
The logs should show:
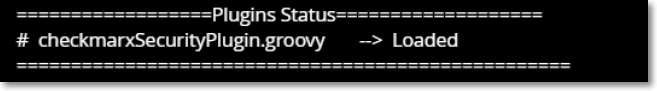
After completing the installation, run an initial analysis of your artifacts using the following command:
Notice
By default, all artifacts are scanned. If you configured specific repositories in the properties file, then only the specified repos are scanned.
Warning
If you didn't configure
cxsca.repositories, the scan will run on all artifacts in all of your repositories. This may take a long time and consume significant system resources. It may be preferable to scan a few remote repositories at a time using the configuration propertycxsca.repositories. Repeat scans for the remaining remote repositories by updating this property. Once you have run an initial scan on all repos, for continuous evaluation you can set thecxsca.repositoriesproperty as empty to scan all repositories, or list all remote repositories that you want to scan on a regular basis.curl -u username:password -X POST "<JFrogURL>/artifactory/api/plugins/execute/scanArtifacts"
Adjusting Property Configurations
After installing the plugin, you can customize your plugin by adjusting the following properties in the cxsupplychainsecurity-plugin.properties file.
Whenever you change a property you must run the following command to update the configuration:
curl -u username:password -X POST "<JFrogURL>/artifactory/api/plugins/execute/checkmarxSecurityReload"
Warning
When you change the cxsca.update-period property, you need to restart the system in order for the change to take effect.
Compliance Thresholds
Property Name | Possible Values | Default | Description |
|---|---|---|---|
cxsca.security.risk.critical.threshold | none, Integer >=0 | none | The max. number of Critical vulnerabilities that will be considered compliant. "none" indicates that critical vulnerabilities will not cause the artifact be considered non-compliant. |
cxsca.security.risk.high.threshold | none, Integer >=0 | none | The max. number of High vulnerabilities that will be considered compliant. "none" indicates that High vulnerabilities will not cause the artifact be considered non-compliant. |
cxsca.security.risk.medium.threshold | none, Integer >=0 | none | The max. number of Medium vulnerabilities that will be considered compliant. "none" indicates that Medium vulnerabilities will not cause the artifact be considered non-compliant. |
cxsca.security.risk.low.threshold | none, Integer >=0 | none | The max. number of Low vulnerabilities that will be considered compliant. "none" indicates that Low vulnerabilities will not cause the artifact be considered non-compliant. |
cxsca.security.allow-malicious | yes/no | no |
|
Block Usage
Property Name | Possible Values | Default | Description |
|---|---|---|---|
cxsca.security.block-by-default | yes/no | no |
This setting does not prevent artifacts from being uploaded to or stored in Artifactory. |
Allowed Licenses
Property Name | Possible Values | Default | Description |
|---|---|---|---|
cxsca.security.allowed-licenses | [License names] | MIT,Apache 2.0,BSD 3,ISC,Zlib | A comma separated list of licenses that are allowed. All other licenses will be considered non-compliant. |
Remote Repositories to be Analyzed
Property Name | Possible Values | Default | Description |
|---|---|---|---|
cxsca.repositories | JFrog repository key | All repositories | If this property is defined, then only the specified repos are analyzed by Checkmarx. Enter a comma separated list of JFrog repository keys for the repos that will be analyzed. |
Continuous Evaluation Frequency
Property Name | Possible Values | Default | Description |
|---|---|---|---|
cxsca.update-period | 1-168 | 1 hour | Specify the number of hours of the interval between evaluations. |
Using the Plugin
Once the plugin is installed and an initial scan has been run, the results are displayed for each scanned artifact as part of the artifact's properties. The data is automatically updated periodically by our continuous evaluation process.
Checkmarx Artifact Properties
For each artifact that has been analyzed by Checkmarx One, the following properties are added to the properties tab of the artifact.
Property Name | Possible Values | Description |
|---|---|---|
CxSCA.TotalVulnerabilities | Integer >=0 | The total number of vulnerabilities identified for the artifact |
CxSCA.Vulnerabilities.Critical | Integer >=0 | The total number of Critical vulnerabilities identified for the artifact |
CxSCA.Vulnerabilities.High | Integer >=0 | The total number of High vulnerabilities identified for the artifact |
CxSCA.Vulnerabilities.Medium | Integer >=0 | The total number of Medium vulnerabilities identified for the artifact |
CxSCA.Vulnerabilities.Low | Integer >=0 | The total number of Low vulnerabilities identified for the artifact |
CxSCA.IsMalicious | yes/no |
|
CxSCA.Licenses | [string] | A list of licenses associated with the artifact |
Cx.LastScanned | Date | The date and time that the artifact was last scanned |
Cx.IsCompliant | yes/no |
|
Cx.ForceAllow | yes/no | You can set this as |
Cx.NonCompliantReason | [string] | For non-compliant artifacts, this shows a list of reasons why this artifact is categorized as non-compliant. |
Exempting Artifacts from Compliance
If you have set thresholds for blocking usage, you can override these thresholds for specific artifacts.
Warning
Once an artifact is exempted, the exemption applies globally to all developers and applications. Because Artifactory does not track which developers or applications consume an artifact, and the plugin does not support granular override rules, all users will be able to download the artifact despite it containing risks of any severity level.
To override the threshold:
Open the properties tab for the desired artifact.
Set the property
Cx.ForceAllowtoyes.
Running Scans Manually
In addition to the analysis that is done in the background according to the plugin configuration, you can also trigger a manual scan from time to time using the following command:
curl -u username:password -X POST "<JFrogUrl>/artifactory/api/plugins/execute/scanArtifacts"
Getting Info About Blocked Artifacts
If a developer tries using an artifact that is blocked from usage due to non-compliance with the plugin thresholds, they will receive an HTTP 403 error. If the developer would like to understand the reason for the blocked usage, they can follow the artifact link displayed in the build console output. They can then view the content of the json response. They can also check the artifact properties to see the value for Cx.NonCompliantReason.
Event Logs
By default, the INFO level event logs from the plugin are written to the artifactory logs. You can access those logs using following URL:
https://<JFrogURL>/ui/admin/artifactory/advanced/system_logs
The following are some common examples of event logs:
Manual Scan Logs
Starting scan of artifacts
Success Log: “Scanning completed for artifacts of all repositories. Total artifacts: {}, Successfully processed: {}, Processing failed: {}.”;
Background Scan Logs
Number of packages to re-scan :{}
Success Log: “Correlation-Statistics: Total artifacts successfully processed: {}, total artifacts failed: {}";
Processing Chunk
Success Log: “Chunk {} statistics: Successfully processed: {}, Failed: {}“
Each Repository
Processing repository: {}
Success Log: Processed: {}, Successful: {}, Failed: {} artifacts in repository: {}
Specific repository configuration not found in artifactory
Repo config not found for key: {}, repoPath={}
Troubleshooting
For troubleshooting purposes, you can change the log level to DEBUG, so that all debug logs are sent to the JFrog logs.
insert the following snippet in
$ ${ARTIFACTORY_HOME}/var/etc/artifactory/logback.xml:<logger name="io.checkmarx" level="debug"/> <logger name="com.checkmarx.plugin" level="debug"/>
View the generated logs in the
artifactory-service.logfile in the$ {ARTIFACTORY_HOME}/var/logfolder, or access them using the system logs URL:https://<JFrogURL>/ui/admin/artifactory/advanced/system_logs
FAQ
Can the CxOne JFrog plugin replace JFrog Curation?
The CxOne JFrog plugin is not a replacement for the JFrog Curation product. JFrog Curation prevents non-compliant artifacts from being added to Artifactory, while the CxOne JFrog plugin operates between the developer workflow and Artifactory, enforcing policy at artifact usage time.