- Checkmarx Documentation
- Checkmarx SAST
- SAST User Guide
- System Management
- Scan Setting
- Preset Manager
Preset Manager
Presets are predefined sets of queries you can select when Creating, Configuring, and Branching Projects. Predefined presets are provided by Checkmarx, and you can configure your own. You can also import and export presets.
To open the Preset Manager:
Go to Settings > Scan Settings > Preset Manager. The Presets Manager window is displayed.
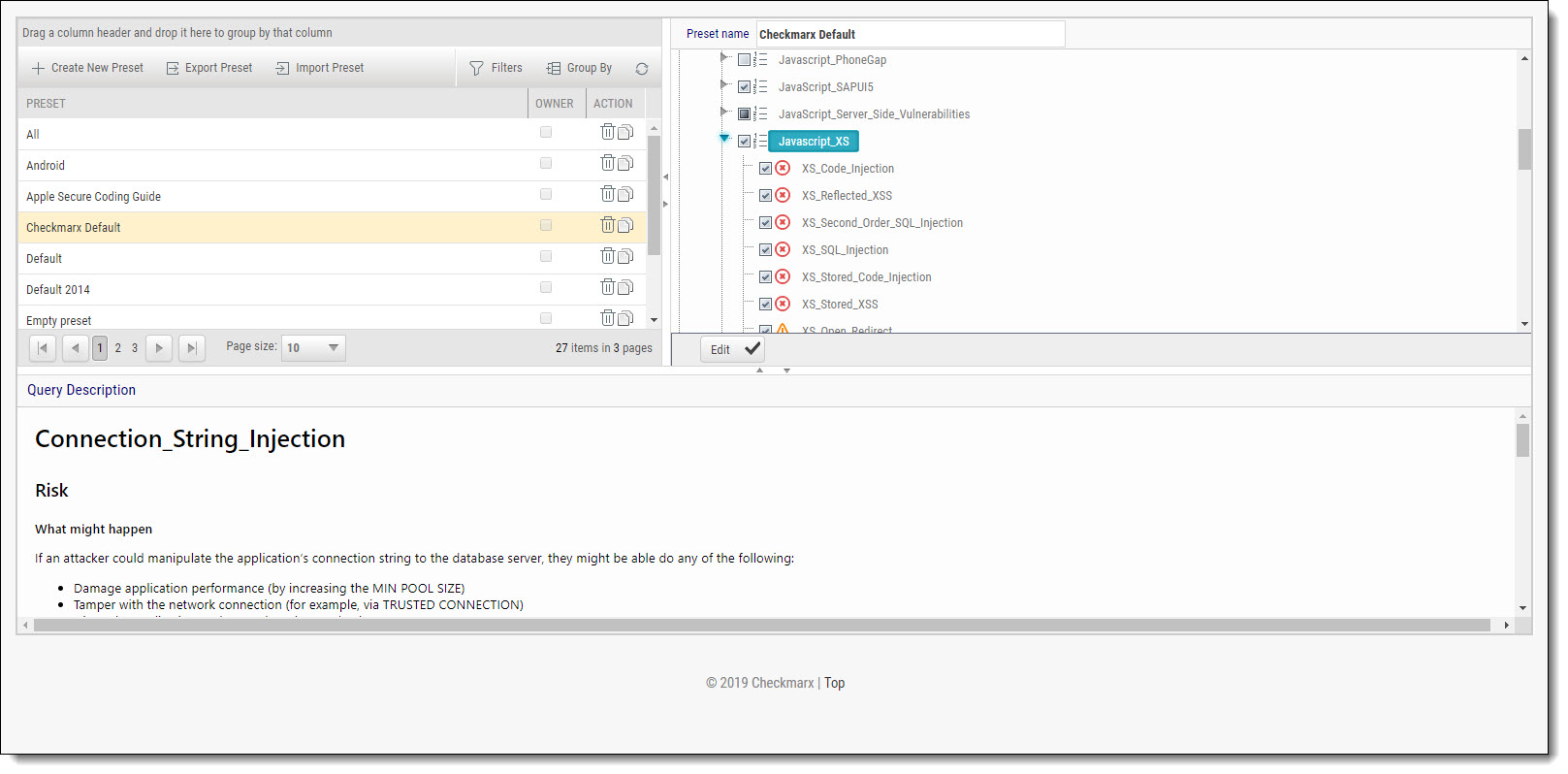 |
Notice
You can quickly create a new preset based on an existing one (duplicate) by selecting a Preset from the Preset pane and clicking  .
.
Creating a New Preset
To create a new preset:
From the Preset Manager, click Create New Preset. The Create New Presets window is displayed.
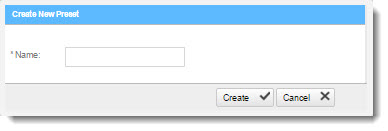
Enter a preset Name and click <Create>.
Select a Coding Language.
Select the Queries to be included in the preset.
Click <Save>.
Modifying an Existing Preset
To modify an existing preset:
From the Preset Manager, select a Preset from the Preset pane and click <Edit>.
Select a Coding Language.
Select the Queries to be included in the preset.
Notice
You can edit a single language, such as Java, selecting and deselecting the queries as needed, and then press Synchronize for all related queries in all languages to be selected.
Click <Save>.
Importing a Preset
To import a preset:
From the Preset Manager, click Import Preset. The Import Preset window is displayed.
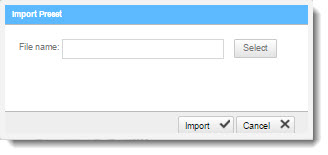
Click <Select>. navigate to the preset (.XML file) and click <Open>.
Notice
If the imported preset has the same name as an existing one, the existing preset will be overridden.
Click <Import>. The Preset is displayed in the Preset pane.
Exporting a Preset
To export a preset:
From the Preset Manager, click <Export Preset> and save the exported preset (.XML file).
Deleting a Preset
To delete a preset:
From the Preset Manager, select a Preset from the Preset pane and click  .
.
Predefined Presets
The following is a list of all the predefined presets provided by Checkmarx with the recommended usage and which vulnerability queries are included:
Preset | Usage | Includes vulnerability queries for... |
|---|---|---|
All | For all application security risks | Apex, ASP, Cobol, CPP, CSharp, Dart, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Swift, Typescript, VB6, VbNet and VbScript coding languages |
Android | For Android-related application security risks | Groovy, Java, and Kotlin coding languages |
Apple Secure Coding Guide | For IOS-related application security risks | ObjectiveC and Swift coding language |
ASA Mobile Premium | The ASA Mobile Premium preset contains a subset of vulnerabilities that the Checkmarx AppSec Accelerator team considers to be the starting point of the Checkmarx AppSec program when scanning mobile applications. The preset might change in future versions. The AppSec Accelerator team will continuously remove old/deprecated queries or include new and improved ones. | CSharp, Java, JavaScript, Kotlin, ObjectiveC, and Swift coding languages |
ASA Premium | The ASA Premium preset contains a subset of vulnerabilities that the Checkmarx AppSec Accelerator team considers the starting point of the Checkmarx AppSec program. The preset might change in future versions. The AppSec Accelerator team will continuously remove old/deprecated queries or include new and improved ones. | Apex, ASP, Cobol, CPP, CSharp, Go, Groovy, Java, JavaScript, Kotlin (non-mobile only), Perl, PHP, PLSQL, Python, RPG, Ruby, Rust, Scala, VB6, VbNet, and VbScript coding languages |
Base Preset | The Base Preset is designed to boost scanning efficiency, prioritizing the swift retrieval of results with pertinent and impactful vulnerabilities. The preset can be used as a starting point and customized to meet your requirements. | APEX, ASP, Cobol, CPP, CSharp, Dart, Go, Groovy, Java, JavaScript, Kotlin, Lua, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Rust, Scala, SQL, Swift, VB6 and VBNet |
Checkmarx Default | The Checkmarx Default preset contains all the vulnerabilities that Checkmarx recommends to scan when unsure which preset to use. | Apex, ASP, Cobol, CPP, CSharp, Dart, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Swift, Typescript, VB6, VbNet and VbScript coding languages |
Checkmarx Express | The Checkmarx preset contains a curated set of High and Medium Java, C#, and JS queries improved by Cx accuracy initiatives. | CSharp, Java, and JavaScript languages |
CWE Top 25 | The Common Weakness Enumeration Top 25 contains the most common and impactful software weaknesses. | Apex, ASP, Cobol, CPP, CSharp, Dart, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Swift, Typescript, VB6, VbNet and VbScript coding languages |
Empty Preset | Empty preset with no vulnerability queries. This can be used to create a new preset from scratch. | Empty |
Error Handling | For error handling related application security risks | Apex, ASP, CPP, CSharp, Groovy, Java, ObjectiveC, Perl, PHP, PLSQL, Python, Ruby, VB6, and VbNet coding languages |
FISMA | For homeland security application risks according to the 'Federal Information Security Modernization Act' compliance guidelines | Apex, ASP, Cobol, CPP, CSharp, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, Ruby, Scala, Swift, Typescript, VB6, VbNet and VbScript coding languages |
High and Medium | For high and medium-related application security risks | Apex, ASP, Cobol, CPP, CSharp, Dart, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Swift, Typescript, VB6, VbNet and VbScript coding languages |
High, Medium, and Low | For high, medium, and low-related application security risks | Apex, ASP, Cobol, CPP, CSharp, Dart, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Swift, Typescript, VB6, VbNet and VbScript coding languages |
HIPAA | For sensitive patient data-related security risks according to the HIPAA (Health Insurance Portability and Accountability Act) compliance guidelines | Apex, ASP, Cobol, CPP, CSharp, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, Ruby, Scala, Swift, Typescript, VB6, VbNet and VbScript coding languages |
ISO/IEC TS 17961 2013/2016 | For C++ coding standards | C++ coding language |
JSSEC | For Android-related application security risks, according to the JSSEC (Japan's Smartphone Security Association) compliance guidelines | Groovy and Java coding languages |
MISRA_C | For C-related application security risks according to the MISRA (Motor Industry Software Reliability Association) compliance guidelines | C++ coding language |
MISRA C 2012 | This preset aims to improve the MISRA_C preset and includes a set of queries covering the standard C coding guidelines for the Motor Industry. | C coding language |
MISRA_CPP | For C++ related application security risks according to the MISRA (Motor Industry Software Reliability Association) compliance guidelines | C++ coding language |
Mobile | For mobile-related application security risks | CSharp, Groovy, Java, JavaScript, Kotlin, ObjectiveC, and Swift coding languages |
MOIS(KISA) Secure Coding 2021 | MOIS (KISA) Software Secure Coding 2021 from the Ministry of the Interior and Safety (MOIS) and Korea Internet & Security Agency (KISA) | Apex, ASP, Cobol, CPP, CSharp, Dart, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Swift, VB6, VbNet and VbScript languages |
NIST | For the application security risks according to the 'National Institute of Standards and Technology' compliance guidelines. | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, Perl, PHP, PLSQL, Python, Ruby, Scala, Typescript, VB6, VbNet, and VbScript coding languages |
OWASP ASVS | This preset provides a basis for testing web application technical security controls and provides developers with a list of requirements for secure development. | Apex, ASP, Cobol, CPP, CSharp, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Swift, VB6, VbNet and VbScript coding languages |
OWASP Mobile TOP 10-2016 | For the top 10 web application security risks according to the OWASP (Open Web Application Security Project) compliance guidelines for 2016 | CSharp, Groovy, Java, JavaScript, Kotlin, ObjectiveC, and Swift coding languages |
OWASP Mobile TOP 10-2024 | For the top 10 web application security risks according to the OWASP (Open Web Application Security Project) compliance guidelines for 2024 | CSharp, Dart, Java, JavaScript, Kotlin, ObjectiveC, and Swift coding languages |
OWASP TOP 10-2010 | For the top 10 web application security risks according to the OWASP (Open Web Application Security Project) compliance guidelines for 2010 | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, ObjectiveC, Perl, PHP, PLSQL, Python, Ruby, Typescript, VB6, VbNet and VbScript coding languages |
OWASP TOP 10-2013 | For the top 10 web application security risks according to the OWASP (Open Web Application Security Project) compliance guidelines for 2013 | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, ObjectiveC, Perl, PHP, PLSQL, Python, Ruby, Scala, Typescript, VB6, VbNet and VbScript coding languages |
OWASP TOP 10-2017 | For the top 10 web application security risks according to the OWASP (Open Web Application Security Project) compliance guidelines for 2017 | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, Perl, PHP, PLSQL, Python, Ruby, Scala, Typescript, VB6, VbNet and VbScript coding languages |
OWASP TOP 10-2021 | For the top 10 web application security risks according to the OWASP (Open Web Application Security Project) compliance guidelines for 2021 | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, Perl, PHP, PLSQL, Python, Ruby, Scala, Typescript, VB6, VbNet and VbScript coding languages |
OWASP TOP 10 API 2019 | For understanding and mitigating the unique vulnerabilities and security risks of Application Programming Interfaces (APIs) according to the OWASP (Open Web Application Security Project) compliance guidelines for 2019. | CSharp, Java, JavaScript, and PHP coding languages |
OWASP TOP 10 API 2023 | For understanding and mitigating the unique vulnerabilities and security risks of Application Programming Interfaces (APIs) according to the OWASP (Open Web Application Security Project) compliance guidelines for 2023. | Apex, ASP, Cobol, CPP, CSharp, Dart, Go, Groovy, Java, JavaScript, Kotlin, Lua, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Typescript, VB6, VbNet and VbScript coding languages |
PCI | For credit card payment application security risks according to the PCI (Payment Card Industry) compliance guidelines | Apex, ASP, Cobol, CPP, CSharp, Go, Groovy, Java, JavaScript, ObjectiveC, Perl, PHP, PLSQL, Python, Ruby, Scala, Typescript, VB6, VbNet, and VbScript coding languages |
SANS Top 25 | For the top 25 web application security risks according to the SANS Technology Institute’s compliance guidelines | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, ObjectiveC, Perl, PHP, PLSQL, Python, Ruby, Scala, Typescript, VB6, VbNet and VbScript coding languages |
SEI CERT | For C++ coding standards | C++ coding language |
STIG | For the application security risks according to the 'Security Technical Implementation Guide' compliance guidelines | Apex, ASP, Cobol, CPP, CSharp, Go, Groovy, Java, JavaScript, Perl, PHP, PLSQL, Python, Ruby, Scala, Typescript, VB6, VbNet and VbScript coding languages |
Top Tier | This preset is designed to be “noise-free” with the highest accuracy and reliability when scanning code for vulnerabilities and security risks. The "Top Tier" is based on the top queries with the highest accuracy. | Apex, ASP, CPP, CSharp, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, RPG, Ruby, Scala, Swift, VB6 and VbNet coding languages |
WordPress | For WordPress-related web application security risks | PHP coding language |
XS | For XS SAP-related application security risks | JavaScript coding language |
XSS and SQLi only | When scanning a new project, The recommended best practice is to focus on the most important vulnerabilities first. | Apex, ASP, Cobol, CPP, CSharp, Go, Groovy, Java, JavaScript, Kotlin, ObjectiveC, Perl, PHP, PLSQL, Python, Ruby, Scala VB6, VbNet and VbScript coding languages |
Base Preset
The Base preset is composed of the following queries:
Language | Package | Query | CWE | Query Id |
|---|---|---|---|---|
CPP | CPP_Buffer_Overflow |
| 170 | 5578 |
CPP_High_Risk |
| 90 | 4022 | |
| 77 | 285 | ||
| 99 | 286 | ||
| 114 | 287 | ||
| 89 | 289 | ||
CPP_Insecure_Credential_Storage |
| 522 | 5503 | |
CPP_Medium_Threat |
| 369 | 1216 | |
| 22 | 321 | ||
| 547 | 323 | ||
CPP_Low_Visibility |
| 359 | 1213 | |
CSharp | CSharp_High_Risk |
| 99 | 425 |
| 90 | 426 | ||
| 89 | 429 | ||
| 89 | 430 | ||
| 79 | 431 | ||
| 643 | 433 | ||
CSharp_Medium_Threat |
| 22 | 468 | |
| 359 | 475 | ||
| 352 | 483 | ||
| 611 | 3685 | ||
| 346 | 5375 | ||
Java | Java_High_Risk |
| 77 | 588 |
| 99 | 589 | ||
| 90 | 590 | ||
| 89 | 593 | ||
| 89 | 594 | ||
| 79 | 595 | ||
Java_Medium_Threat |
| 346 | 5370 | |
| 611 | 3522 | ||
| 611 | 4447 | ||
| 359 | 639 | ||
| 352 | 648 | ||
| 36 | 1670 | ||
Java_Low_Visibility |
| 260 | 5876 | |
JavaScript | JavaScript_Angular |
| 116 | 5266 |
JavaScript_High_Risk |
| 79 | 2560 | |
JavaScript_Medium_Threat |
| 312 | 2725 | |
| 346 | 5404 | ||
JavaScript_Server_Side_Vulnerabilities |
| 23 | 2980 | |
| 89 | 2983 | ||
| 89 | 2984 | ||
| 79 | 2987 | ||
Python | Python_High_Risk |
| 77 | 3101 |
| 99 | 3102 | ||
| 89 | 3105 | ||
| 79 | 3106 | ||
| 89 | 3424 | ||
Python_Medium_Threat |
| 22 | 3115 | |
| 359 | 3116 |


