- Checkmarx Documentation
- Checkmarx One
- Checkmarx One User Guide
- Global Inventory
Global Inventory
SCA Inventory and Risks
SCA Global Inventory Overview
The SCA Global Inventory and Risks page displays a comprehensive list of all packages identified in your account, along with their associated risks and license information. This includes details such as vulnerabilities, outdated versions, and policy violations. By aggregating information across all Projects, the Global Inventory helps you prioritize remediation by showing which risks and vulnerable packages impact multiple Projects, making it easier to coordinate efforts across development teams.
With the addition of bulk triage actions in the Global Inventory, managing these risks at scale has become even more efficient. You can now select multiple items and triage them all at once across the Packages, Vulnerabilities and Malware, and Licenses tabs. For example, if you determine that a particular package is not a concern, you can search for all its instances in the Packages tab and mark them all as Muted with a single action. This capability streamlines large-scale triage workflows and saves time by enabling consistent decisions to be applied across the entire tenant.
Notice
For projects with a "primary" branch, Global Inventory shows data based on the last scan of the primary branch. If there is no primary branch, then data is based on the last scan of any branch of the project. Therefore, you should be aware that if different branches of a project rely on different open source packages, Global Inventory will not show comprehensive data for all branches.
 |
The Global Inventory & Risks page is accessed in Checkmarx One by clicking on the Resources  > SCA Inventory and Risks in the main navigation.
> SCA Inventory and Risks in the main navigation.
The screen includes three tabs:
Packages (default) – shows info about all of the packages used in all the Projects in your organization.
Vulnerabilities and Malware – shows info about all of the vulnerabilities, operational and legal risks across all the Projects in your organization.
Licenses - shows info about all of the licenses that are associated with the open source packages used by your projects.
There is an Export option that enables you to export a csv file for the info that is shown on each of the Global Inventory & Risks tabs. The csv reflects the data currently shown in the table, as per the applied filters.
Header Bar
The header bar shows information about the filters applied to the items displayed on the page. It also includes two action buttons: Recalculate and Manage States.
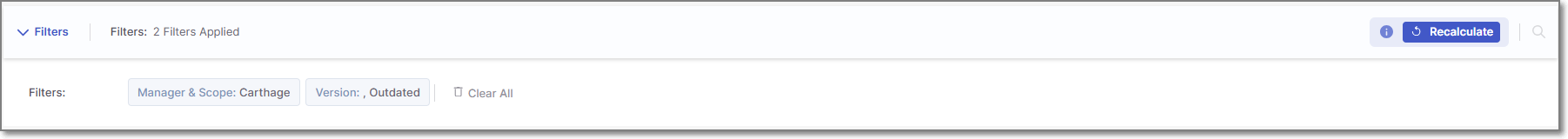
The following table describes the items in the Header Bar
Item | Description | Possible Values |
|---|---|---|
Filters | A list of the filters applied to the items displayed. Click on the arrow next to the word Filters to display the selected filters. | Version: Outdated |
Recalculate
| Click to reevaluate the risks associated with the dependencies in your project. See Recalculating SCA Scan Results TipThe recalculation will apply to the Projects associated with the packages, vulnerabilities or licenses that you have selected. For example, in the packages tab, if you have selected three packages, only the Projects associated with those three packages will be recalculated. | - |
Manage States (Not shown in picture) | When you select items in the display, the Manage States button appears in the header bar. Click on the button to open the Edit Results side panel, where you can manage the states of all selected items at once. |
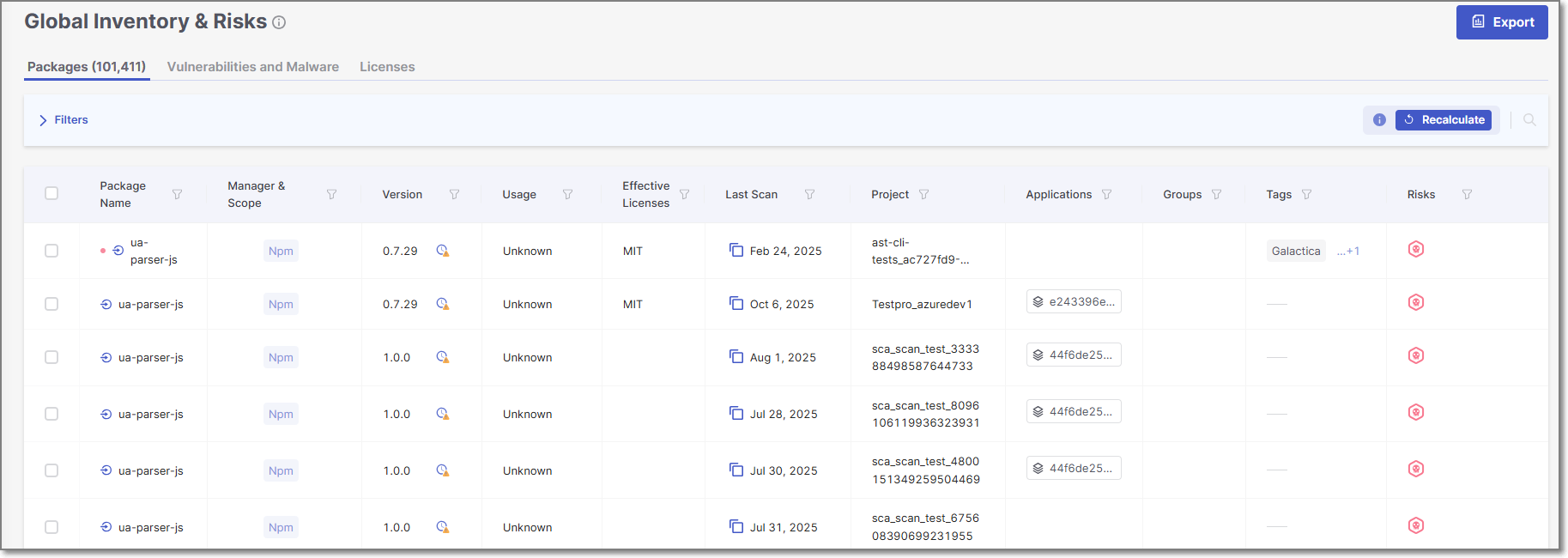
Global Inventory and Risks Page - Packages Tab
The Global Inventory & Risks Packages tab shows detailed info about the packages identified by the scans of all of your Projects. This info includes policy violations, vulnerabilities, outdated versions, etc. The total number of packages is shown in parentheses in the tab title.
Notice
If a package is used by multiple Projects, a separate record (row) is shown for each instance.
You can search for Package Name, , License, and Project using the search box. You can also set filters and sort by several key column headers.
You can export the data on this page as a CSV file. There is an option to export all data or only data shown based on the current filters.
Click on a specific row to open the Package Details page for that package in the Risk Report for the Project. For more information, see Package Details Page.
Notice
You can only open the Package Details page for packages that were identified in Projects which are assigned to your Team.
 |
Notice
You may need to scroll horizontally to view all columns.
The following table describes the info shown in the Packages tab of the Global Inventory & Risks page.
Item | Description | Possible Values | |
|---|---|---|---|
Package Name | The name of a package used in one or more of the Projects in the organization. Next to the package name, an icon is shown indicating how the package is used by the Project. TipIf the package name is used in more than one Project, it will appear on the list multiple times, one time for each Project that uses it. | e.g., javax.annotation:javax.annotation-api
| |
Manager and Scope | Shows labels that Checkmarx applied to the package. There is a label indicating the package manager used for package resolution. In addition, the label “Test” is applied to all packages that have the word “test” in their file path. Additional labels are applied to special types of dependencies. |
| |
Version | The version of the package. Hover over the display to show the date of your version, and (if available) the version number and date of the latest version as well as the number of new versions since your most recent update. If the version is outdated, an | e.g., 2.0.0
| |
Usage (for Projects with Exploitable Path activated) | Indicates whether or not this package is used (called) by your project’s source code. |
| |
Effective Licenses | Shows all effective licenses that you have that are associated with this package. For multiple effective licenses, hover over the display to show all licenses. | e.g., GPL 2.0, Apache 2.1 | |
Last Scan | Last scan date of the primary branch of the Project containing the package. TipIf the Project has no primary branch, the date will reflect the last scan of the Project. Click on the | e.g., May 17, 2024 | |
Project | The name of the Checkmarx One Project where the package was identified. TipIf a package is used by multiple Projects, a separate record (row) is shown for each instance. | e.g., Demo01 | |
Applications | The application/s to which the Project containing this package belongs. |
| |
Groups | The group/s to which the Project containing this package belongs. | ||
Tags | Shows both the scan tags and project tags associated with the most recent scan in which the package was identified. | e.g., Branch:v0.1.2 | |
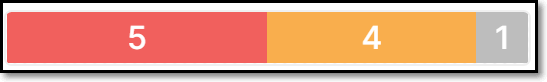
Risks | A color coded bar graph indicating the number of vulnerabilities of each severity level. Malicious Packages and Suspected Malware are indicated by the malicious icon For Muted and Snoozed packages, the color coded bar is replaced with the muted or snoozed icon. TipYou can apply a filter to show only packages that contain risks of a specific severity level. You can also apply filters to show only packages of a specific state (e.g. Monitored, Muted or Snoozed). | e.g.,
| |
Secure Version | Indicates whether or not a remediated version (i.e, a version with no vulnerabilities) of this package exists. |
| |
Context Menu (top right of table) | |||
Export CSV
| Click on this option to download all of the information in this table (other than Violates Policies and Relation) as a CSV file. TipYou can customize the report content by specifying which sections to include and applying the sorting and filters of the current display. | ||
Global Inventory and Risks Page - Vulnerabilities and Malware Tab
The Vulnerabilities and Malware tab shows detailed info about all of the risks identified by the scans of all of your Projects. This info includes risk type, ID, publication date, etc. The total number of risks is shown in parentheses in the tab title.
Notice
If a risk applies to multiple Projects, a separate record (row) is shown for each instance.
You can search for ID, Package, and Project using the search box. You can also set filters and sort by column headers (except for Project).
You can export the data on this page as a CSV file. There is an option to export all data or only data shown based on the current filters.
Click on a specific row to open the Vulnerability Details page for that vulnerability in the Scan Results page for the Project. For more information, see Risk Details Page.
Notice
You can only open the Vulnerability Details page for packages that were identified in Projects which are assigned to your Team.
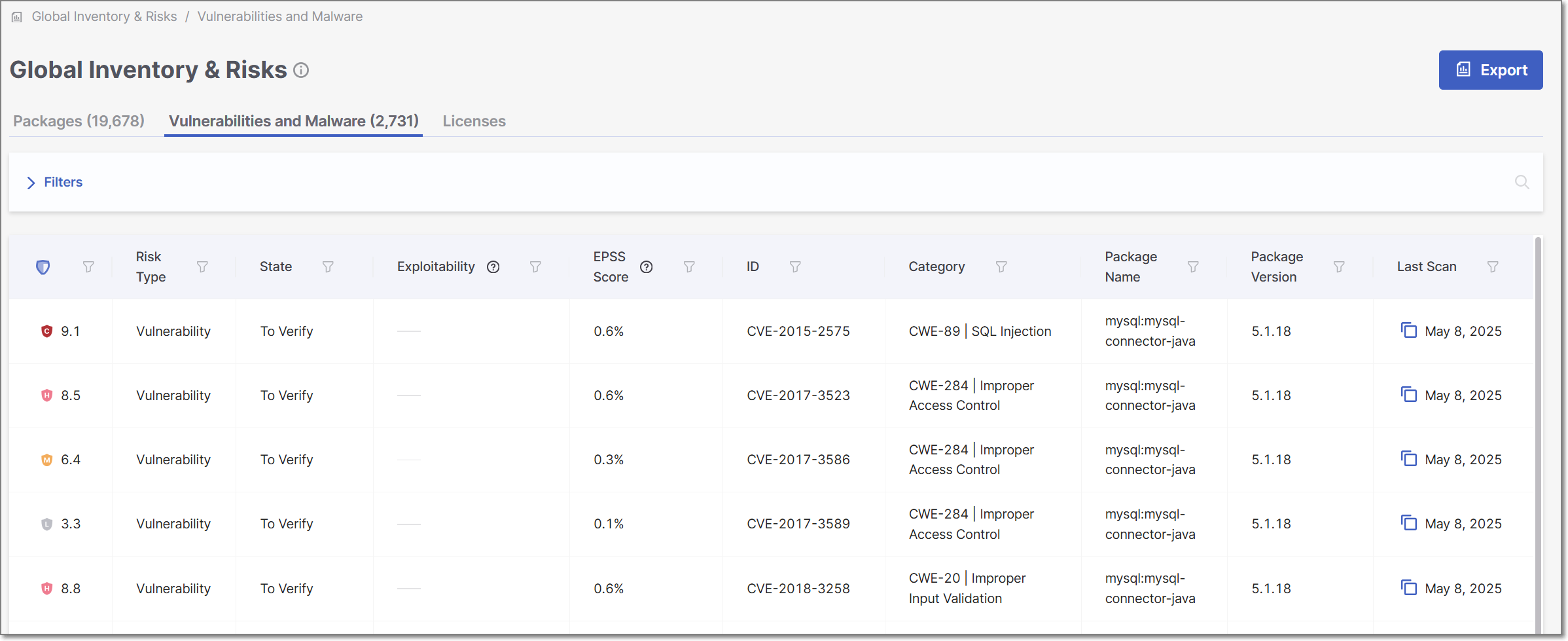 |
The following table describes the info shown in the Vulnerabilities and Malware tab of the Global Inventory and Risks page.
Item | Description | Possible Values |
|---|---|---|
Risk Level | The severity level of the vulnerability, based on its CVSS score in the NVD. |
|
Risk Type | The type of risk. Risks associated with Malicious Packages are listed in the table as "Suspected Malware". You can set a filter to show only the specified risk types. | Vulnerability, Suspected Malware |
State | Indicates the state of the vulnerability. |
|
Exploitability | Shows which exploitability indicators apply to this vulnerability. |
|
EPSS Score | EPSS - The EPSS (Exploit Prediction Scoring System) is a score provided by First for vulnerabilities. The score is an estimate of the likelihood for a vulnerability to be exploited. The score is presented as a percentage indicating the likelihood of this vulnerability to be exploited within the next 30 days. Hovering over the score will display a percentile indicating the ranking of this risk relative to other vulnerabilities. | e.g., 1.6%, 87th percentile |
ID | The ID of the CVE listing. The ID consists of the CVE prefix followed by the year that the CVE was discovered and the serial counter for that year's CVE listings. TipVulnerabilities discovered by the Checkmarx Vulnerability Research Team which are net yet catalogued as CVEs, are indicated by the “Cx” prefix. | e.g., CVE-2019-12384 |
Category | The category of the vulnerability. For CWEs, the CWE is given as well as a brief description of the vulnerability. | e.g., CWE-89|SQL Injection, Malicious, Chainjacking etc. |
Package Name | The name of the package in which the vulnerability was identified. | e.g., com.fasterxml.jackson.core:jackson-databind |
Package Version | The version of the package in which the vulnerability was identified. | e.g., 2.9.8 |
Last Scan | The date of the latest scan in which this vulnerability has been detected. | e.g., Jun 9, 2024 |
Project | The name of the Project in the organization that has the risk. TipIf a risk applies to multiple Projects, a separate record (row) is shown for each instance. | e.g., Demo01 |
Applications | The application/s to which the Project containing this vulnerability belongs. |
|
Groups | The group/s to which the Project containing this vulnerability belongs. | |
Detection/Publication | Click on the desired header to alternate between the detection and publication dates.
| e.g., Jun 24, 2019 |
Secure Version | Indicates whether or not a remediated version of the package where this vulnerability was identified exists. TipIn the context of the Risks tab, a version is considered secure as long as this particular vulnerability is remediated, even if the package has other vulnerabilities. |
|
Context Menu (top right of table) | ||
Export CSV | Click on this option to download all of the information in this table (in addition to Risk Level) as a CSV file. TipYou can customize the report content by specifying which sections to include and applying the sorting and filters of the current display. | - |
Global Inventory and RIsks Page - Licenses Tab
The Licenses tab shows info about all of the licenses that are associated with the open source packages used by your project.
You can search for License Name, Package Name, and Package Version using the search box. You can also set filters and sort by column headers (except for Project).
You can export the data on this page as a CSV file. There is an option to export all data or only data shown based on the current filters.
Click on a specific row to open the Licenses page for that license in the Scan Results page for the Project. For more information, see License Details Page.
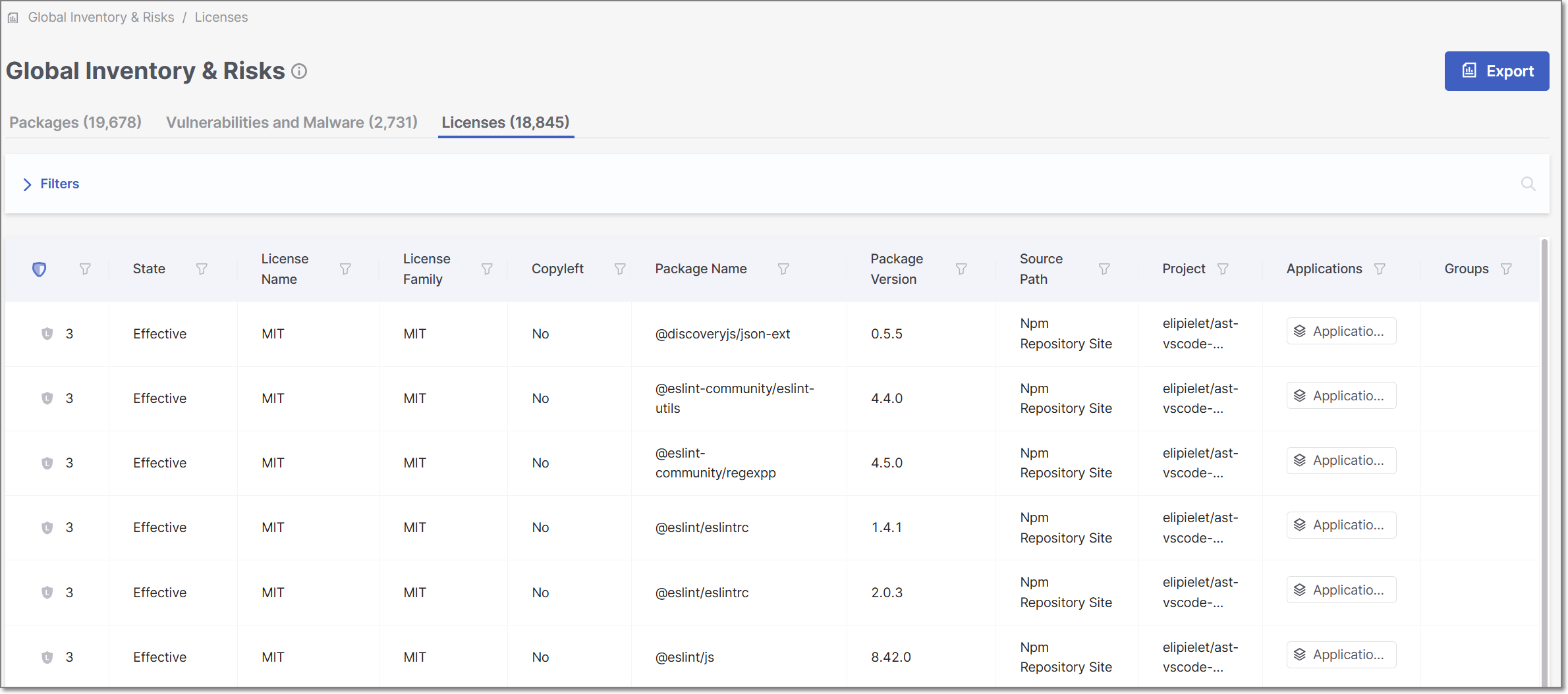 |
The following table describes the info shown in the Licenses tab of the Global Inventory & Risks page.
Item | Description | Possible Values |
|---|---|---|
Risk Level | Shows the severity level and score indicating the overall risk level associated with this license. TipIf this isn't the effective license for this package, then a high license score doesn't necessarily pose a legal risk. |
|
State | Indicates whether or not this license is the "effective" license for your organization's use of this package. Also, if the package to which the license applies has been muted or snoozed, this is indicated in the State column. |
|
License Name | The name of the license. | e.g., GPL 3.0, MIT etc. |
License Family | The family of the license. | e.g. Apache |
Copyleft | The category of the license. |
|
Package Name | The name of the package in which the vulnerability was identified. | e.g., com.fasterxml.jackson.core:jackson-databind |
Package Version | The version of the package in which the vulnerability was identified. | e.g., 2.9.8 |
Source Path | The source from which the license was identified. | e.g., Manifest File, Npm Repository Site, Official Website, Statically Observed etc. TipThe category "Statically Observed" indicates that the license was identified in the source code (e.g., README files) using regex and other identification methods. |
Project | The name of the Project in the organization that has the risk. TipIf a risk applies to multiple Projects, a separate record (row) is shown for each instance. | e.g., Demo01 |
Applications | The application/s to which the Project containing this license belongs. |
|
Groups | The group/s to which the Project containing this vulnerability belongs. | |
Context Menu (top right of table) | ||
Export CSV | Click on this option to download all of the information in this table (in addition to Risk Score) as a CSV file. TipYou can customize the report content by specifying which sections to include and applying the sorting and filters of the current display. | - |
API Inventory
The Global API Inventory lists all APIs and risks detected during all scans in all projects on the platform. The columns are filterable, and the list can be exported as a CSV (with applied filters).
Note
Total Risk column is split between Critical, High, Medium, and Low in the CSV file.
Follow the instructions below to view the Global Inventory and details on each API:
From the main menu, select Resources
 > API Inventory.
> API Inventory.Select the Inventory tab. The Global API Inventory Table appears as illustrated and listed below.
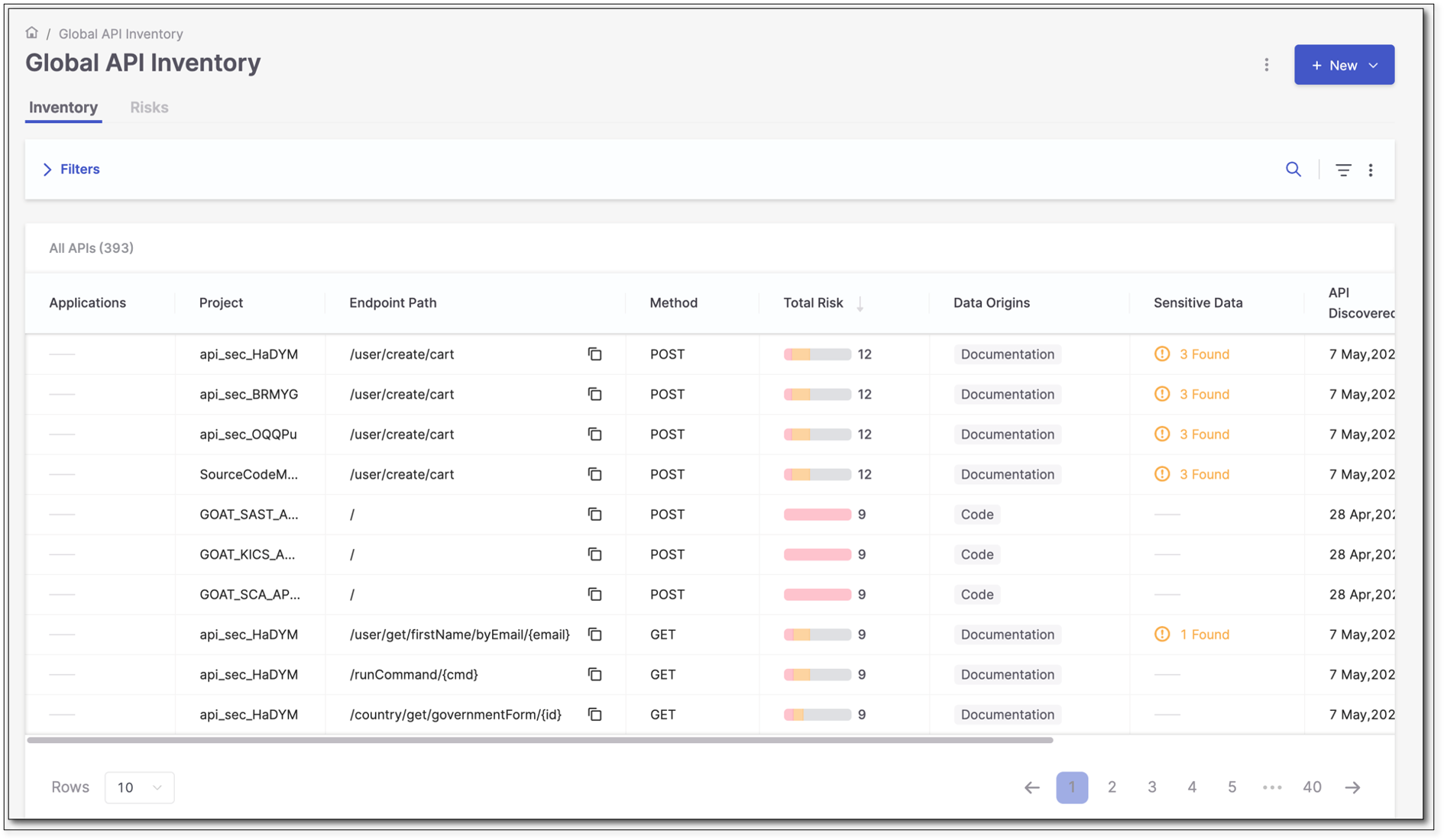
Parameter
Description
Application
The application to which this project belongs. If the project does not belong to any application, this field is marked ----.
Project
The project for which the API in this row was discovered.
Endpoint Path
The end path of the resource URL.
Method
The operation that the endpoint performs on resources.
Total Risk
The number of risks found in the selected API.
Data Origins
Indicates where the API was detected. Currently, two data origins are available: Code, Documentation, and Testing.
Sensitive Data
The number of sensitive data attributes for all scans in the listed project.
API Discovered
The date when the API was discovered.
Last Updated
The date when the API was updated last.
Doc
Undocumented APIs present a risk because attackers may use them as an undetectable surveillance and reconnaissance channel.
This column shows whether the endpoint is documented or not:
"-" appears when no documentation file was not scanned.
Yes: The endpoint appears in the scanned document and it is documented.
No: The endpoint appears in the scanned document, but it is not documented.
AuthN
Unauthenticated APIs present a risk because they may allow easy access to confidential information.
This column shows whether the endpoint is authenticated or not.
"-" appears when no documentation file was not scanned.
Yes: The endpoint appears in the scanned document and it is authenticated.
No: The endpoint appears in the scanned document, but it is not authenticated.
Click on the corresponding row to view the details on a specific endpoint.
Additional information appears as illustrated and explained below.
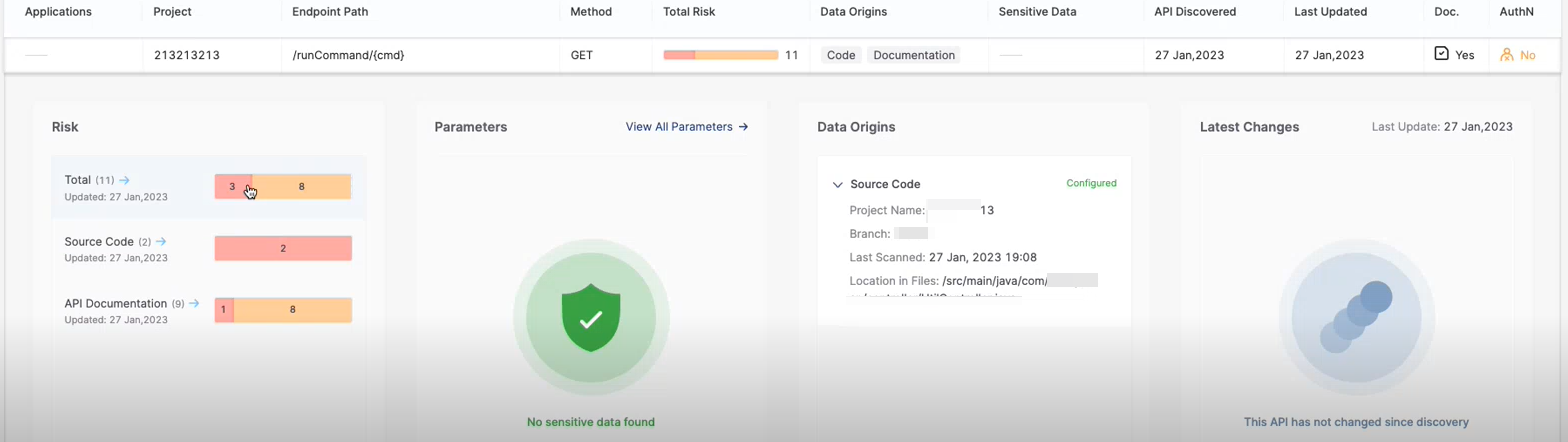
Parameter
Description
Risk
Displays the number and severity of risks detected in the selected API.
This pane may include any or all of the following sections:
Total: The total number of risks found for the current endpoint by the API Security (on the left) and SAST (on the right) scanners.
Source Code: The number of source code risks found by the API Security (on the left) and the number of risks found by the SAST scanner (on the right).
API Documentation: The number of API documentation risks found by the API Security (on the left) and the number of risks found by the SAST scanner (on the right).
If the scan did not include SAST queries, this section will show only the number of API documentation risks.
Clicking on a section opens the relevant risks in the Global Risks table.
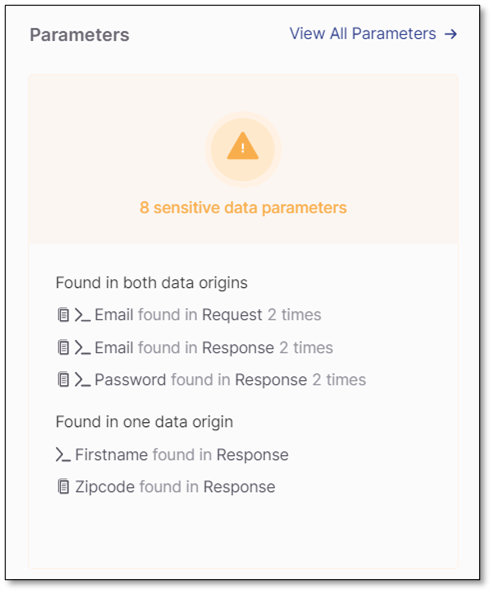
Parameters
Shows the number of occurrences of sensitive data in the code and documentation. To see a list of the sensitive data in the code, click inside the widget.
Sensitive data is a set of data that Checkmarx defines as sensitive. It is not related to the detected vulnerabilities. It simply provides you with an overview of what is potentially vulnerable to threats.
Sensitive parameters are divided into five categories like Name, Personal Data, etc. Each category has a set of parameters defined.
Name: firstname, surname, familyname, fullname, name
Personal Data: birthday, dob, dateofbirth, phone, mobile, email, socialsecurity, ssn, driverslicense
Address: address, zipcode
Bank: credit, cardnumber, account
Secrets: dcredentials, secret, auth, apikey, pass, pwd, password
If the API was found in both data origins, the API source code and the documentation, this widget shows which warnings appear only in the code, only in the documentation, or in both. The code data origin is iconized as
 , and the documentation data origin is iconized as
, and the documentation data origin is iconized as  .
.
Data Origins
Displays the details of the API data origins. It can be either the API source code, the Swagger file (documentation), both, or DAST tests.
Latest Changes
Lists the changes on this API since it was discovered. It can be one or several of the following:
Structure: Added or removed Response and Request parameters, for example:
Structure | {Parameter} was removed
Structure | {Parameter} was added
Risk: Detected one or more new risks. Risks are characterized by their risk level ( Critical, High, Medium, or Low) and grouped in categories, for example:
Risk | {Number} new {Level} found
Sensitive Data: Flagged parameters as sensitive, for example:
Sensitive Data | {Parameter} was found in {Request or Response}
If the API has not changed since its discovery, the corresponding message will appear.
To view the Global Risks Table for all the listed APIs, follow the instructions below.
To view details and classifications for any listed risk and modify classifications for vulnerabilities detected as part of the risk, refer to the instructions above under Viewing a Risk in Detail for risks listed per API in the Global API Inventory.
To view the Global Risk table:
From the main menu, select Resources
 > API Inventory. The Global API Inventory page appears.
> API Inventory. The Global API Inventory page appears.In the Global API Inventory page, select the Risks tab. The Risks Table appears for all scans per Project and Application to which a specific project may belong.
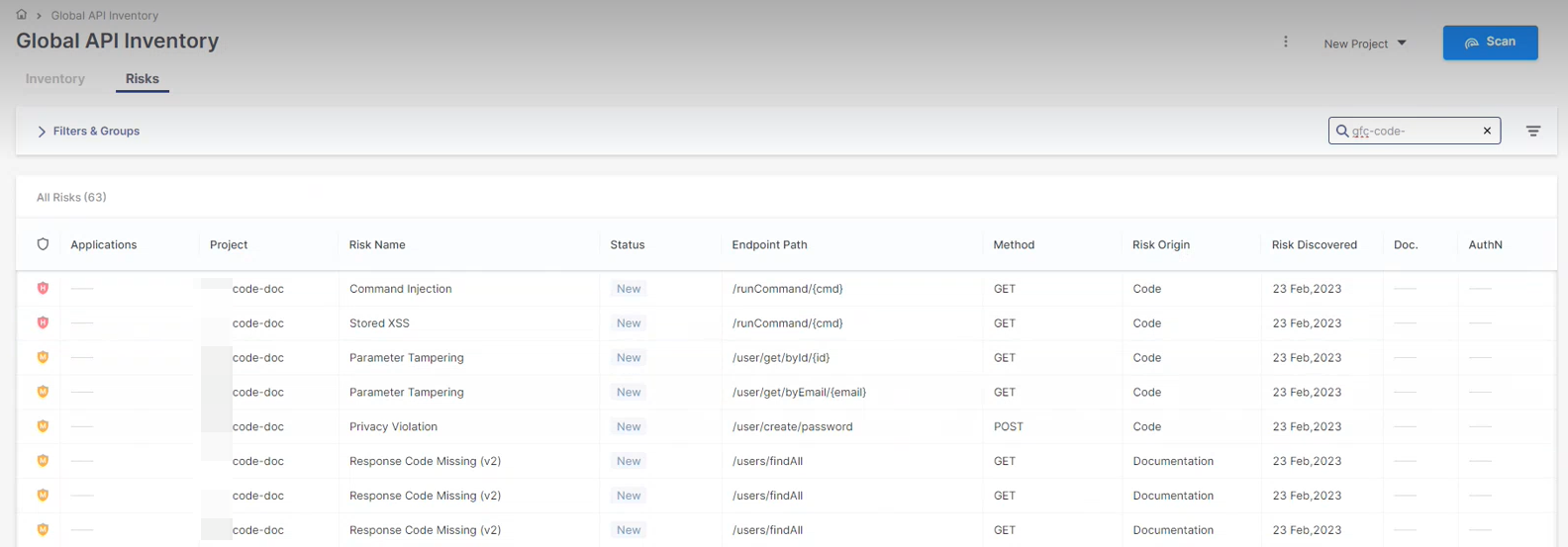
The parameters in the Risks table are listed and explained below.
Parameter
Description
Severity

Indicates the risk severity. Possible severity levels are:Critical, High, Medium, or Low.
Applications
The application to which this project belongs. If the project does not belong to any application, this field is marked ----.
Project
The project for which the risk was detected.
Risk Name
The name of the risk.
Status
Indicates the status of the risk as follows:
 - A newly detected vulnerability.
- A newly detected vulnerability. - The vulnerability has been detected at least once before.
- The vulnerability has been detected at least once before.Endpoint Path
The end path of the resource URL.
Method
The operation that the endpoint performs on resources.
Risk Origin
Indicates where the risk was detected. Currently, three risk origins are available: Code, Documentation, and Testing. To filter the risks by their origin, click on the column header to display a drop-down list, check the required option, and click OK:
Risk Discovered
The date when the risk was detected.
Doc
Undocumented APIs present a risk because attackers may use them as an undetectable surveillance and reconnaissance channel.
This column shows whether the endpoint is documented or not:
"-" appears when no documentation file was not scanned.
Yes: The endpoint appears in the scanned document and it is documented.
No: The endpoint appears in the scanned document, but it is not documented.
AuthN
Unauthenticated APIs present a risk because they may allow easy access to confidential information.
This column shows whether the endpoint is authenticated or not.
"-" appears when no documentation file was not scanned.
Yes: The endpoint appears in the scanned document and it is authenticated.
No: The endpoint appears in the scanned document, but it is not authenticated.
To filter the lists or to display them in ascending or descending order, do the following:
To view list entries in ascending or descending order, point to the relevant header and select Click to sort ascending or Click to sort descending respectively.
To only show specific parameters, for example, a specific status, point to the relevant header, click
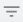 and then select the desired parameter(s) from the filter options.
and then select the desired parameter(s) from the filter options.
You can view the details and classifications of each vulnerability, as explained below. In addition, you are able to modify the classification of one or multiple instances of a detected vulnerability.
To view a risk detected in an API listed in the Global API Risk list:
In the Global API Risks table, click somewhere in the line of the desired API, for example, yev-i62. Details and a link to the risk of the selected API appear.
Click the Risk Bar
 . The Risks table for this API appears. According to the indicator on the Risks bar, 12 Medium, and 16 Low severity risks have been detected.
. The Risks table for this API appears. According to the indicator on the Risks bar, 12 Medium, and 16 Low severity risks have been detected.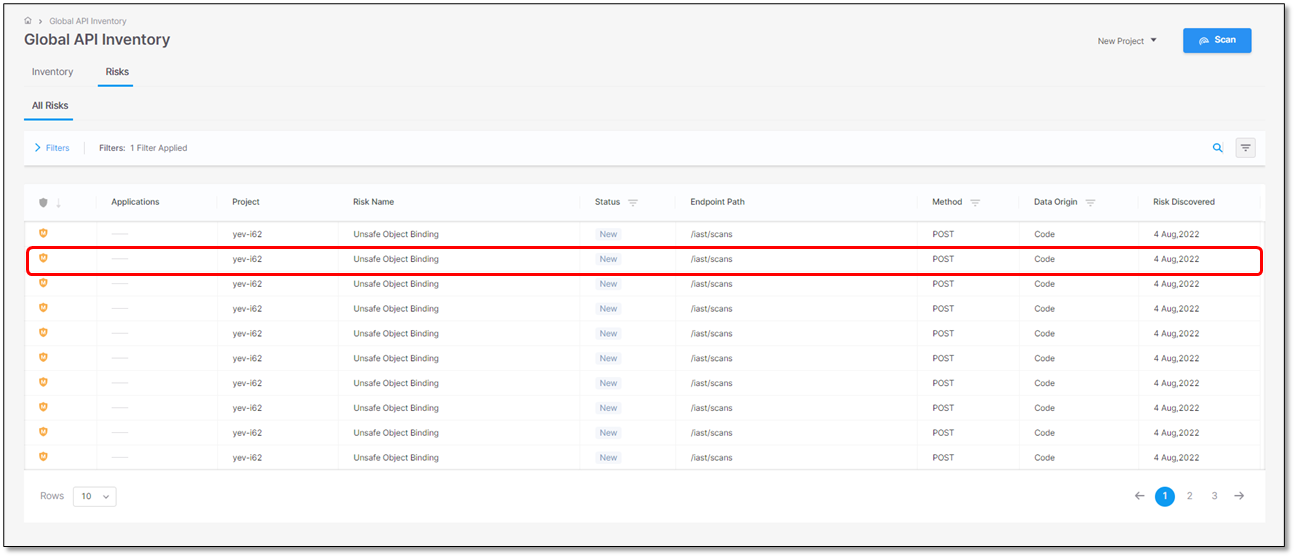
Click somewhere inside the row of the desired risk. Additional information on the selected risk appears.
Click inside the icons for additional information. Details of the risk and the sensitive data with their location are displayed.
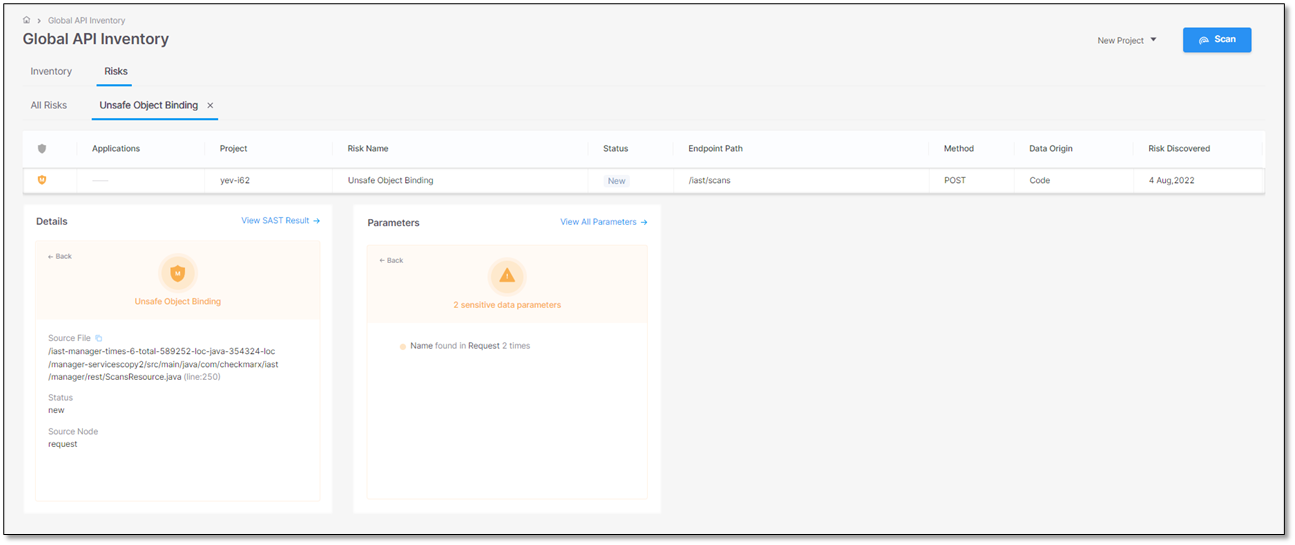
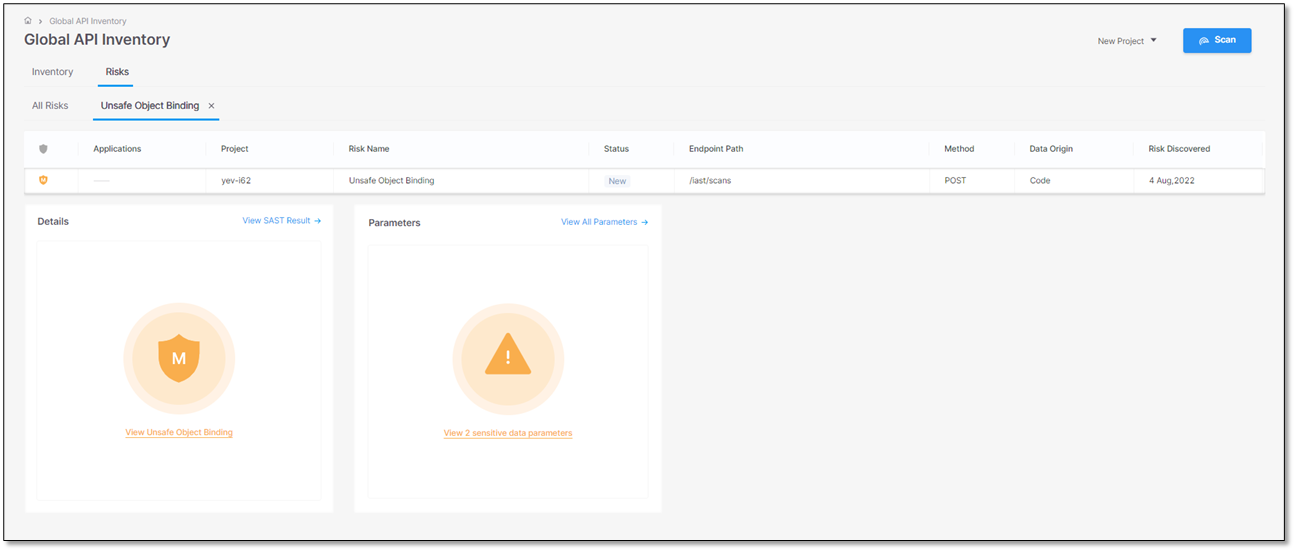
The screen image and the table below illustrate and list the details of an unsafe object binding.
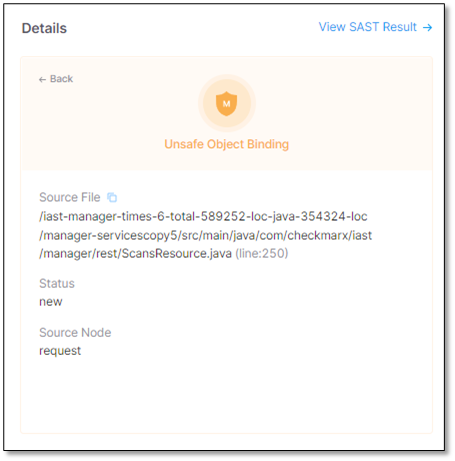
Parameter
Values
Description
Source File
/iast-manager-times-6-total-589252-locjava-354324-loc/manager-servicescopy5/src/main/java/com/checkmarx/iast/manager/rest/ScansResource.java(line:250)
The path and file name of the file with the Unsafe Object Binding.
Status
New
Recurrent. The vulnerability has been detected at least once before
The status of the unsafe object binding
Source Node
The first node (input) of the vulnerable sequence.
The beginning of the attack vector.
To view all the SAST scan results around the Unsafe Object Binding vulnerability:
Under Details, click
 to view the highlighted code vulnerability in detail.
to view the highlighted code vulnerability in detail.Click an instance in the table to view a detailed report and its exact location in the code. In this example, the first detected instance of the 42 detected Stored XSS vulnerabilities has been selected.
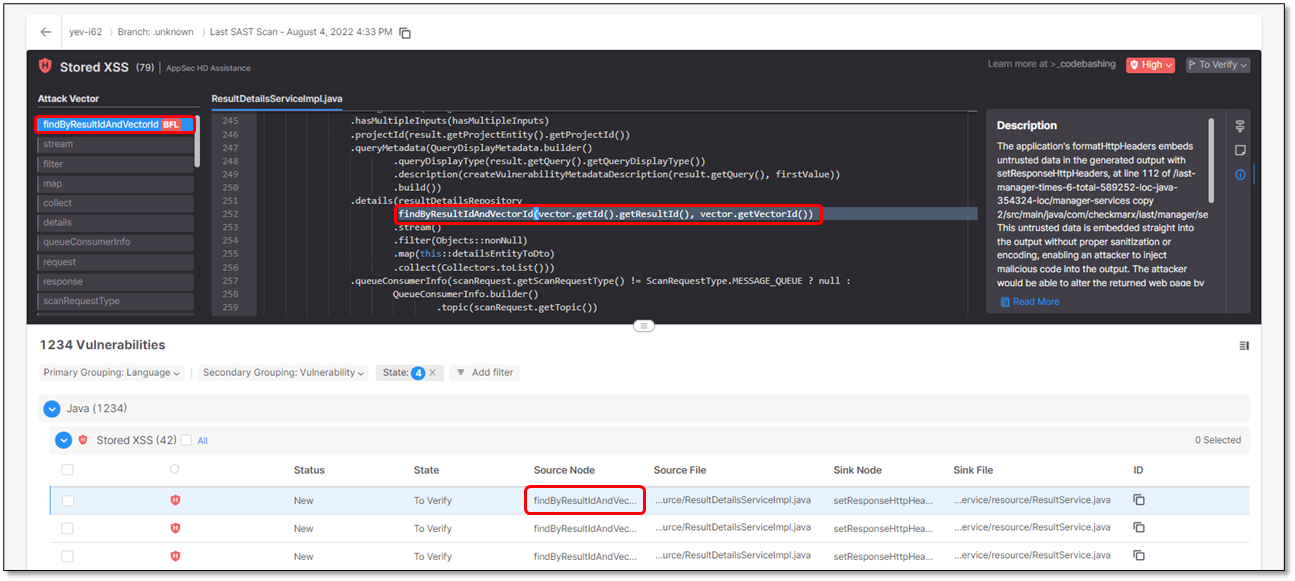
The table below lists and explains the parameters in the list.
Parameter
Description
 (Severity)
(Severity)The severity of the vulnerability:
Critical
High
Medium
Low
Info
Status
Status of the vulnerability:
New
Recurrent. The vulnerability has been detected at least once before.
State
To Verify. The vulnerability has to be verified.
Not Exploitable.
Proposed Not Exploitable
Confirmed. The vulnerability has been verified as a vulnerability.
Urgent. This needs to be urgently addressed.
Source Node
The first node (input) of the vulnerable sequence.
Source File
The file in which the source node is located.
Sink Node
The last node (output) of the vulnerable sequence.
Note
For vulnerabilities that affect a single node, the sink node is identical to the source node.
Sink File
The file in which the sink node is located.
ID
To read the vulnerability ID, point to
 .
.To copy the ID into the clipboard, click
 .
.
To view the exact location of an API documentation vulnerability, click on the vulnerability. The relevant code location will be displayed with the problematic line highlighted.
To modify the classification of one or multiple vulnerabilities:
Select
 the desired vulnerabilities in the list. Options as to what can be modified are illustrated below.
the desired vulnerabilities in the list. Options as to what can be modified are illustrated below.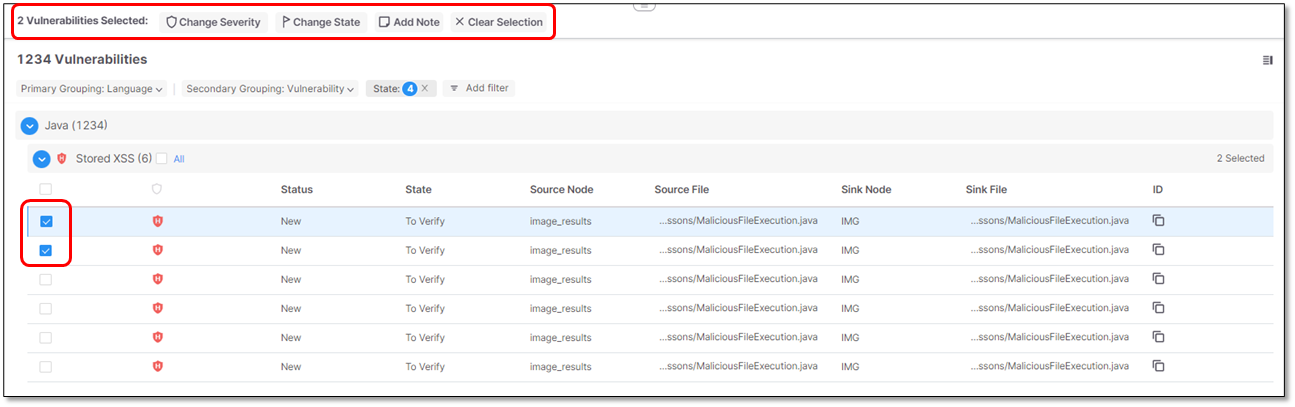
Choose what to modify as outlined below. Explanations for the various options can be found in the table above.
Option
Description
 Change Severity
Change SeverityClick to change the severity to one of the following:
Critical
High
Medium
Low
Info
 Change State
Change StateClick to change the state to one of the following:
To Verify
Not Exploitable
Proposed Not Exploitable
Confirmed
Urgent
 Add Note
Add NoteClick to add a note (free text).
 Clear Selection
Clear SelectionClear all the
 selected vulnerabilities. When clearing the selection, the options to modify severities are hidden again.
selected vulnerabilities. When clearing the selection, the options to modify severities are hidden again.
To view all the sensitive data in the code:
Under Parameters, click
 . All sensitive data parameters in the code appear.
. All sensitive data parameters in the code appear.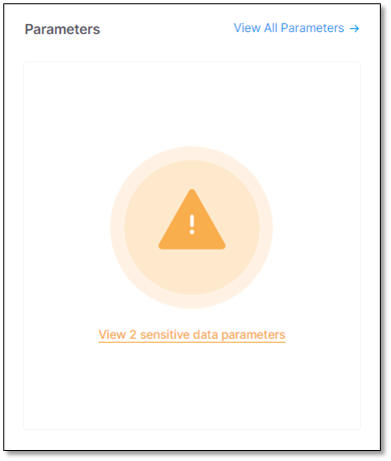
Interface
Description
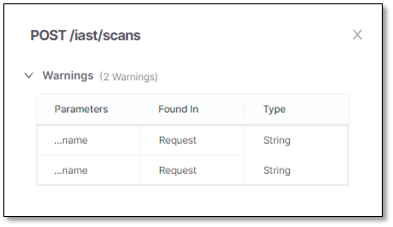
List of all sensitive parameters in the API with warnings. This section is identical to the list of sensitive data parameters.
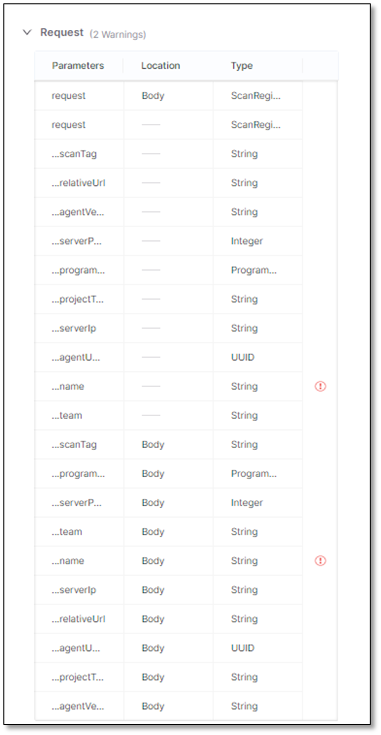
List of all parameters in the request to the API. The sensitive parameters are labeled
 .
.
List of all parameters in the response by the API. The sensitive parameters are labeled
 .
.