Container Security - Unified Related Results
We have improved the handling of OS-level packages, making it easier to interpret the scan results. Previously, each binary package (e.g., libssl.so) was listed independently, even when it carried the exact same vulnerabilities as the source package it was built from (e.g., openssl-1.1.1k). This inflated vulnerability counts and caused confusion regarding remediation.
Now, if a binary has the same CVEs as its source, then they are shown as a single unified result and the CVEs are only counted once.· If a binary has different vulnerabilities than it's source, then it will still appear separately, so that nothing is missed.
Summary
One source, one count – binaries with identical CVEs as their source package are unified into one result.
Separate when different – binaries with unique vulnerabilities are still shown separately.
Backwards compatibility
If you triaged binary packages that are now unified with the source package, then that triage is no longer relevant, as the related vulnerabilities are now shown under the source package.
Comparison
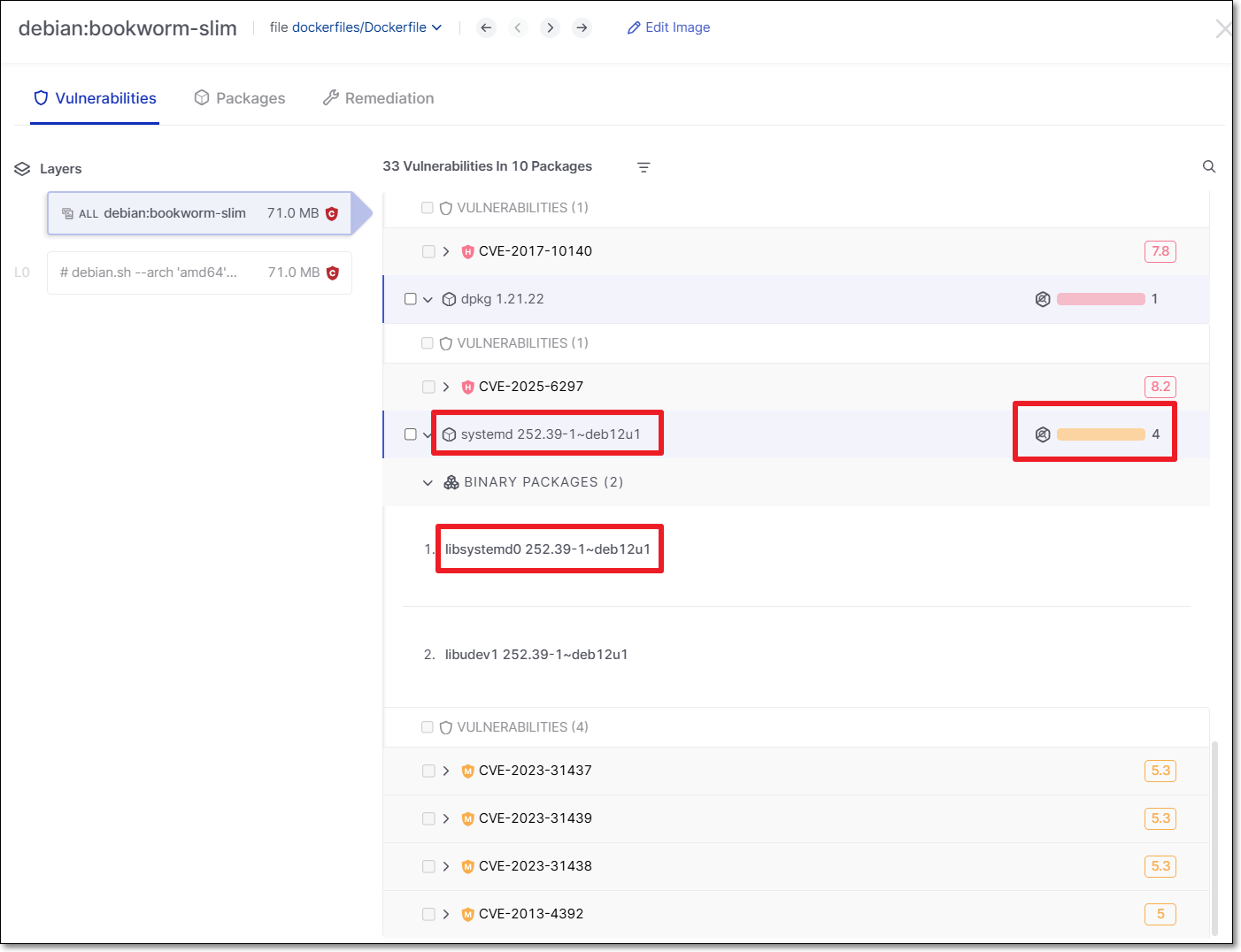
Old Behavior
Shows duplicate results for source and binary packages.
For example: The source package systemd:252.39-1~deb12u1 and the binary libsystemd0 252.39-1~deb12u1 containing identical vulnerabilities, are displayed and counted separately.
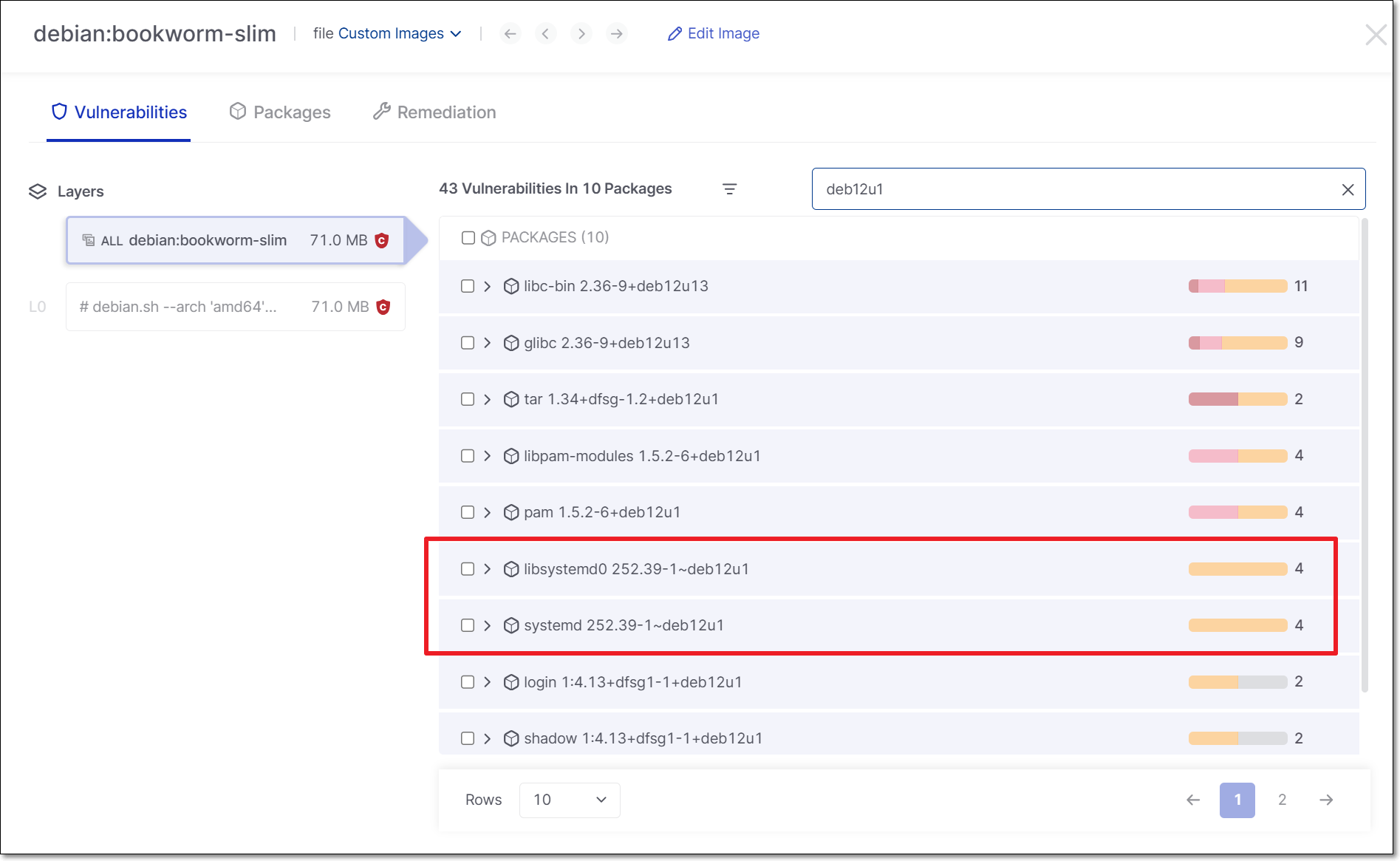
New Behavior
Clear visibility into each bin package with no duplication.
For example: The source package systemd:252.39-1~deb12u1 and the binary libsystemd0 252.39-1~deb12u1 are unified into a single result and the vulnerabilities are only counted once.