Container Scans
Warning
This article explains the functionality of scanning containers in the SCA standalone solution. Checkmarx One users who are using the new Container Securtiy scanner should refer to the documentation here.
In addition to scanning the packages in your source code itself, Checkmarx SCA also scans the Dockerfiles in your project to identify the container images used in your project. Checkmarx SCA extracts all layers of each public base image located in the Dockerfile, and identifies the packages used by each layer.
For scans run via the Checkmarx SCA web portal or Checkmarx plugins only public base images in the Dockerfile are scanned. For scans run via SCA Resolver, in addition to scanning the Dockerfile itself, you can also scan the image that is created from the Dockerfile, using the Syft open source tool. This enables greater visibility into all packages used in the image for all languages supported by SCA as well as many non-supported languages (e.g., Dart, Haskell, Swift etc.). In addition, you can use SCA Resolver to submit specific images from public or private registries for analysis by SCA using the Syft tool.
Supported Registries
Container scans run via SCA Resolver support scanning of images from any registry for which you can run the docker pull command, e.g., DockerHub, Amazon Elastic Container Registry (ECR), Google Container Registry (GCR), Quay, JFrog Container Registry (JCR) etc.
Supported Registries and Ecosystems
Supported Registries
Container scans support scanning of images from any registry for which you can run the docker pull command, e.g., DockerHub, Amazon Elastic Container Registry (ECR), Google Container Registry (GCR), JFrog Container Registry (JCR) etc.
Supported Ecosystems
Debian (dpkg)
Alpine (apk)
C (conan)
C++ (conan)
Dotnet (deps.json)
Go (go.mod, Go binaries)
Java (jar, ear, war, par, sar, native-image)
JavaScript (npm, yarn)
PHP (composer)
Python (wheel, egg, poetry, requirements.txt)
Red Hat (rpm)
Ruby (gem)dpkg
Viewing Container Scan Results
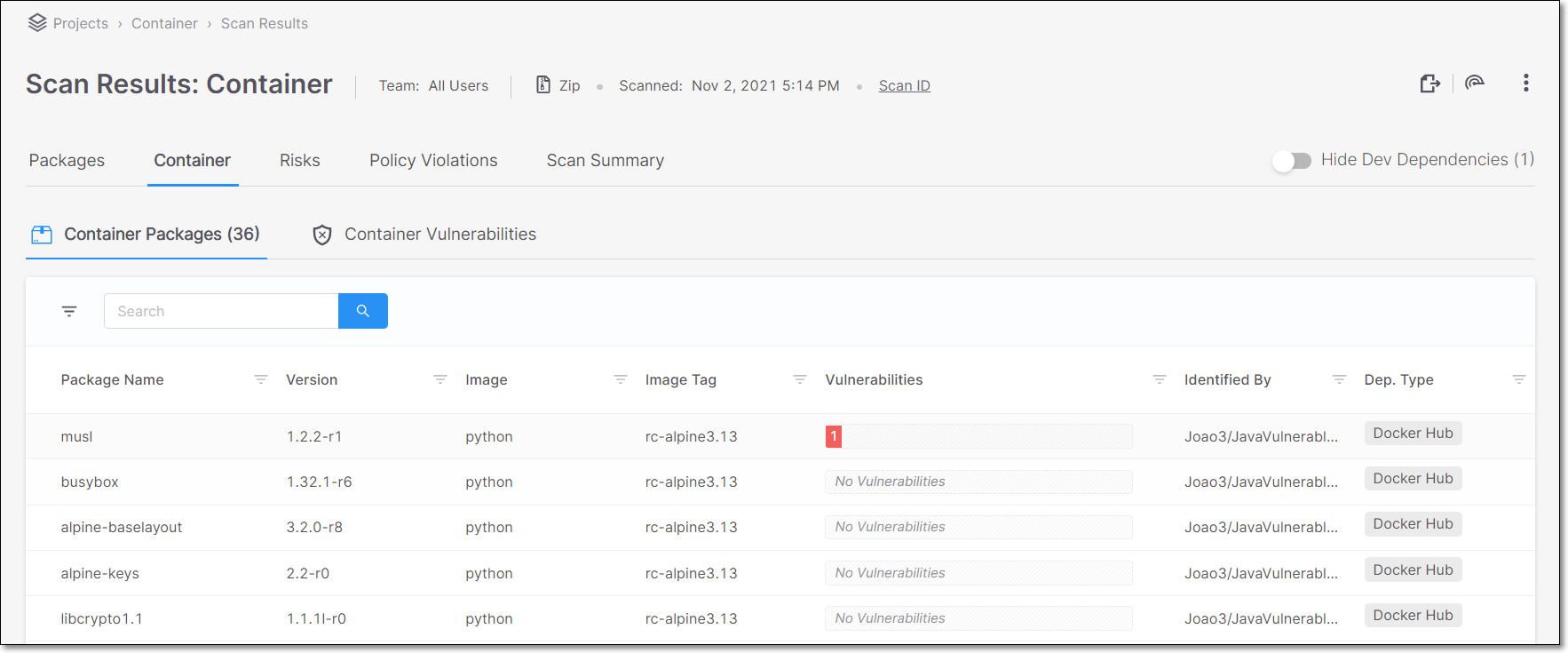
The Scan Results > Container tab shows the container packages identified in your project and the vulnerabilities associated with them. For a description of the info shown in the Container tab, see Container Tab.
 |
Running Container Scans Using Resolver
You can run a container scan on the Dockerfile in your project, on specific images in your repository, or on both.
Prerequisites
To run Resolver scans, it is required to have Syft version 0.83.1 installed on the machine where you are running Resolver. Download and install Syft from https://github.com/anchore/syft/releases/tag/v0.83.1.
If you would like to scan images that are not in your local Dockerfile, you need to have the name and tag for each of the images.
If you are using a private repo, you need to be authenticated for your registry.
Notice
Authentication can be done via Docker or Podman.
Alternatively, you can use the syft login command, as follows:
syft login <private_registry_domain> -u <your_username> -p <your_password>Before running the scan, it is recommended to verify that you are able to access the image on your local machine.
Running a Container Scan on your Dockerfile
Run an SCA Resolver scan, using the
--scan-containersflag in the scan command.
Notice
When running a container scan in Offline mode, you must use the --containers-result-path flag to specify the container results output location. Then, when running Upload, you need to use the same flag to refer to the file location.
Example of scanning the project's Dockerfile:
The following example shows a command to run a container scan on the Dockerfile in your project.
Running a Container Scan on a Specific Image
Add the
--scan-containersflag to the SCA Resolver scan command.If you want to scan only specific images (not an entire project), do the following:
Create a "dummy" folder in your project (for use in the
-sparameter) and give it a name that indicates that it is used for scanning images, e.g., scan_ecr_image.In the Resolver scan command, for the
-sparameter give the path to the "dummy" folder that you created, e.g.,/Users/DemoUser/scan_ecr_image.
Add the
--imagesflag followed by a comma separated list of images. Specify each image using the following syntax {image_name}:{image_tag}.
Example of scanning a specific image:
The following example shows a command to run a container scan on specific images.
Authentication for Scanning Private Repos
In order to access private repos you need to be authenticated in your container repo when you run the scan via Checkmarx SCA Resolver.
Notice
In addition, even when using public repos in DockerHub there is an advantage to authenticating your user in order to avoid the limits that apply to anonymous requests to public repos.
Build Arguments Configuration
Some projects may contain build arguments that are required for layer resolution.
Checkmarx SCA Resolver supports use of a .env_cxsca-container-build-args file, which can be added to repository code to provide custom build-arguments to Dockerfile FROM instructions. We recommend using this file when the docker is present and the build process requires arguments in order to enhance the docker layer resolution and improve results.
The format of this file is similar to an .env file, with each line containing a single argument with an = sign between the argument key and value.
Example:
An .env_cxsca-container-build-args file with the following argument for layer resolution:
LAYER=golang TAG=bullseye
can be used in Dockerfile as follows: FROM $LAYER:${TAG}
Hierarchy
Since many different Dockerfiles can be used inside a project, Checkmarx SCA Resolver applies a folder hierarchy. The following priority (high to low) is given to the files:
Same directory
.env_cxsca-container-build-argsSame directory
.envParent directory
.env_cxsca-container-build-argsParent directory
.envAncestor directory
.env_cxsca-container-build-argsAncestor directory
.envDefault argument value on resolution Dockerfile
This section provides additional info about how to scan images from an AWS ECR registry.
Authentication for AWS ECR
Before running scans via Resolver, make sure that your AWS IAM user is authenticated, and that the token is in the credentials file (AWS_SESSION _TOKEN) as explained here. And, if you are scanning images in a different region, then make sure that the region is correctly configured in the credentials file (REGION).
Obtaining the Image Name and Tag for an AWS ECR Image
The value submitted for the --images parameter for GCR uses the following syntax {repository_uri}:{image_tag}.
The following procedure describes how to obtain these values via the CLI.
To obtain the repository uri, run the CLI command
aws ecr describe-repositories --repository-name {your_repo_name}, and make a note of the value returned forrepositoryUri.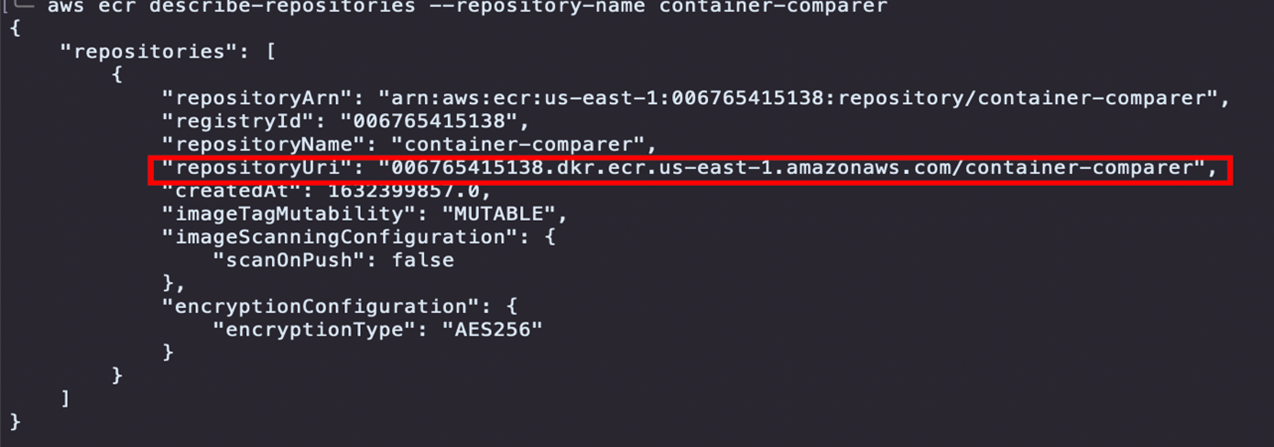
Example for repo named "container-comparer"
To obtain the image tags of the images in the repo, run the CLI command
aws ecr list-images --repository-name {your_repo_name}, and make a note of the value returned forImageTagfor the desired image.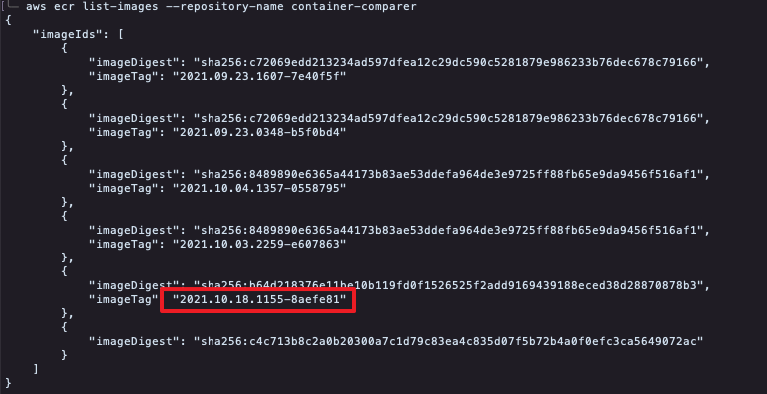
Example for repo named "container-comparer"
Run the SCA Resolver command with the
--scan-containersflag, and add the--imagesflag specifying the desired images using the syntax {repository_uri}:{image_tag}. For example:./ScaResolver -s /Users/DemoUser/scan_ecr_image -n DemoImageScan -a Checkmarx -u jack -p 'demo123!' --scan-containers --images 006765415138.dkr.ecr.us-east-1.amazonaws.com/container-comparer:2021.10.18.1155-8aefe81
Configuring Environment Variables for AWS ECR
Resolver is configured to scan your AWS ECR repo assuming that the default values/paths are in use. If the “credentials” file is in the default AWS path, and you are using the “default” profile, then no action is needed. If you have changed these settings, then you need to configure the following environment variables.
AWS_PROFILE (default value: “default”)
Note
You can configure multiple profiles, e.g., for different environments.
AWS_CONFIG_FILE (default path: “~/.aws/config”)
AWS_SHARED_CREDENTIALS_FILE (default path: “~/.aws/credentials”)
Example of Credentials File
File ““~/.aws/credentials”
[default] aws_access_key_id=ASI aws_secret_access_key=abcd region=us-west -1 aws_session_token=Absd [prod] aws_access_key_id=AKI aws_secret_access_key=xyz region=us-west -1
This section provides additional info about how to scan images from a GCR registry.
Authentication for GCR
Before running scans via Resolver, make sure that you are authenticated in GCR. You can test this by running the docker pull command for the desired image. Learn about possible authentication methods here.
The recommended authentication is using gcloud.
To authenticate using gcloud:
Log in to gcloud as the user that will run Docker commands and run the command
gcloud auth login.Configure Docker using the following command
gcloud auth configure-docker.Your credentials are saved in your user home directory.
Linux: $HOME/.docker/config.json
Windows: %USERPROFILE%/.docker/config.json
Obtaining the Image Name and Tag for a GCR Image
The value submitted for the --images parameter for GCR uses the following syntax gcr.io/{project_id}/{image_name}:{image_tag}.
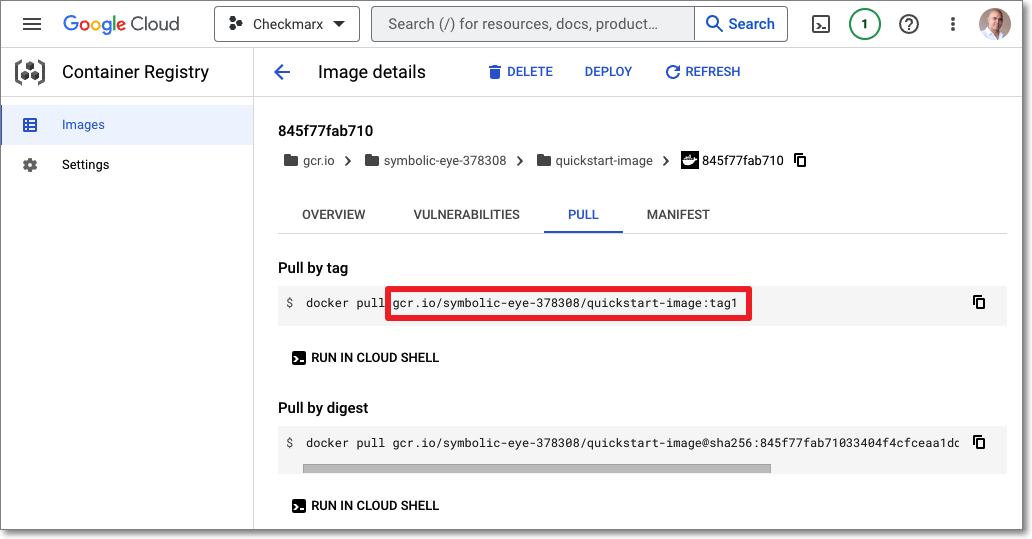
Obtain the value needed to identify this image. The following is on possible method for obtaining this info:
Open ECR in the Google Cloud portal and navigate to the image and tag of the desired image. Then, in the PULL tab, copy the value given in the Pull by tag snippet (without the "docker pull" command).
Run the SCA Resolver command with the
--scan-containersflag, and add the--imagesflag specifying the desired images using the syntax gcr.io/{project_id}/{image_name}:{image_tag}. For example:./ScaResolver -s /Users/DemoUser/scan_gcr_image -n DemoImageScan -a Checkmarx -u jack -p 'demo123!' --scan-containers --images gcr.io/symbolic-eye-1234/quickstart-image:tag1
This section provides additional info about how to scan images from a GAR registry.
Authentication for GAR
Before running scans via Resolver, make sure that you are authenticated in GAR. ou can test this by running the docker pull command for the desired image. Learn about possible authentication methods here.
The recommended authentication is using gcloud.
To authenticate using gcloud:
If it is the first time that you are pulling images, run the following command on your machine
gcloud auth configure-docker us-docker.pkg.devNotice
This command assumes that you are using the US region of GAR. If you are using a different region, then replace "us" with the name of your region.
Obtaining the Image Name and Tag for a GAR Image
The value submitted for the --images parameter for GAR uses the following syntax {gar_region}-docker.pkg.dev/{project_id}/{image_name}:{image_tag}.
Obtain the values needed to identify this image.
Run the SCA Resolver command with the
--scan-containersflag, and add the--imagesflag specifying the desired images using the syntax gcr.io/{project_id}/{image_name}:{image_tag}. For example:./ScaResolver -s /Users/DemoUser/scan_gar_image -n DemoImageScan -a Checkmarx -u jack -p 'demo123!' --scan-containers --images us-docker.pkg.dev/symbolic-eye-1234/quickstart-image:tag1