Changed Functionality for Container Security Scanner
Caution
All changes described in this document relate only to Checkmarx One accounts. For SCA standalone users, container scan functionality will remain unchanged, see Container Scans.
For Checkmarx One users, the container scanning engine will function independently from SCA. This affects how scans are triggered as well as how the results are shown. The new Container Security scanner will be easier to use and will provide improved functionality. For complete documentation of the new Container Security functionality, see here.
Changed Functionality Summary Table
Item | Old Functionality | New Functionality |
|---|---|---|
Used to run container scans by selecting the SCA scanner. | Container Security is now shown as an independent scanner. 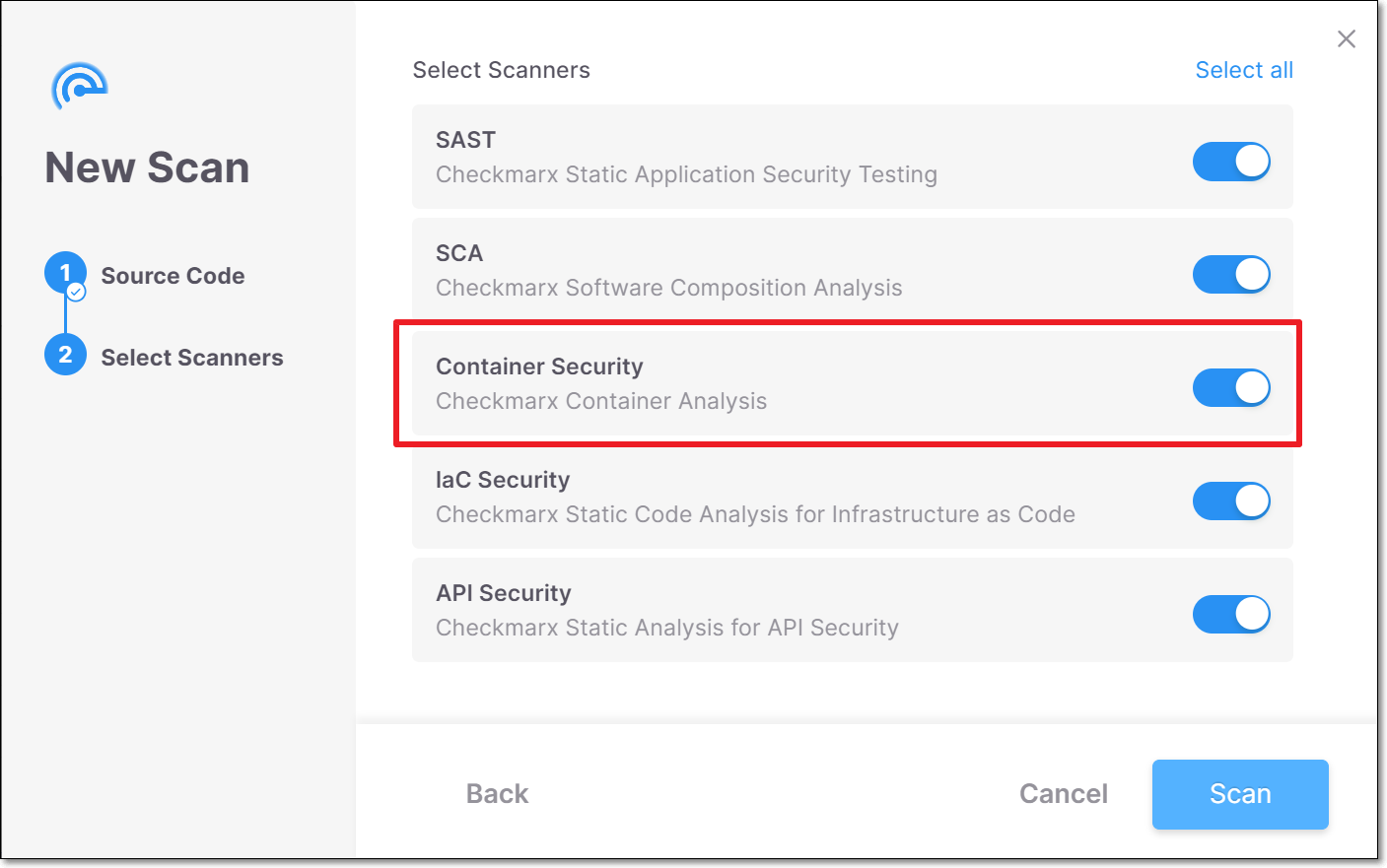 | |
Used to be shown in the Container tab inside the SCA results viewer. | Container Security is now shown as an independent results viewer. 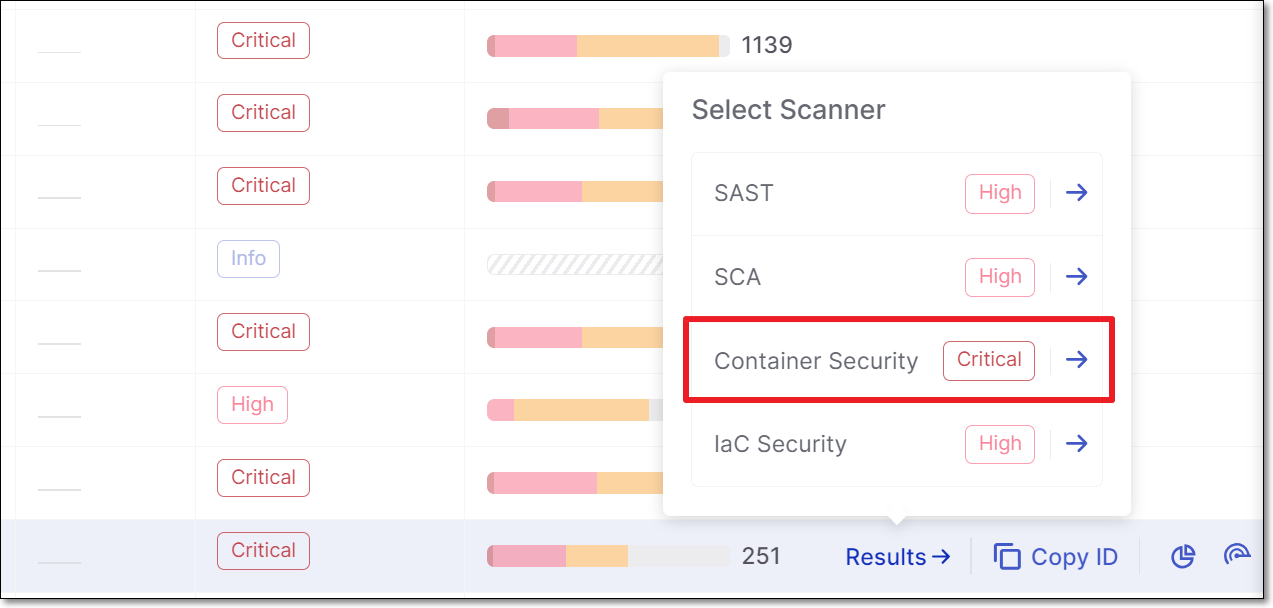 | |
Scanning project files via CLI | Used to run by adding the Sample command: ./cx scan create --project-name scan-containers -s ./containers-repo --branch main --scan-types sca --debug --sca-resolver './ScaResolver' --sca-resolver-params "--log-level Debug --scan-containers" | Now, in the Sample command: ./cx scan create --project-name scan-containers -s ./containers-repo --branch main --scan-types container-security --container-images manuelbcd/vulnapp:latest,debian:10 --debug |
Scanning specific images via CLI | Used to require installing SCA Resolver and Syft locally, and running the Sample command: ./cx scan create --project-name scan-containers -s ./containers-repo --branch main --scan-types sca --debug --sca-resolver './ScaResolver' --sca-resolver-params "--log-level Debug --scan-containers --images manuelbcd/vulnapp:latest,debian:10 --containers-result-path ./.cxsca-container-results.json" | Now, no need to install additional tools. Just run Sample command: ./cx scan create --project-name scan-containers -s ./containers-repo --branch main --scan-types container-security --container-images manuelbcd/vulnapp:latest,debian:10 --debug |
Running scans via API | Used to run POST /scans, specifying Sample request: http://{{base_url}}/api/scans
{
"type": "git",
"handler": {
"repoUrl": "https://github.com/cxsca/sca-goat",
"branch": "containers"
},
"project": {
"id": "71eacb3b-ae1d-4961-a96f-2b8593ff3dc7",
"tags": {}
},
"config": [
{
"type": "sca",
"value": {
"enabelContainers": true //default is true in SCA
}
}
],
"tags": {}
} | Now, run POST /scans, specifying as the scan type. Sample request: http://{{base_url}}/api/scans
{
"type": "git",
"handler": {
"repoUrl": "https://github.com/cxsca/sca-goat",
"branch": "containers"
},
"project": {
"id": "71eacb3b-ae1d-4961-a96f-2b8593ff3dc7",
"tags": {}
},
"config": [
{
"type": "containers",
"value": {}
},
{
"type": "sca",
"value": {
"enabelContainers": false
}
}
],
"tags": {}
} |
Retrieving scan results via API | Used to run GET /results, and the results type was shown as "sca-container". Sample container result: [
{
"type": "sca-container",
"id": "CVE-2016-10228",
"similarityId": "CVE-2016-10228",
"status": "NEW",
"state": "TO_VERIFY",
"severity": "MEDIUM",
"confidenceLevel": 0,
"created": "2024-06-09T07:22:58Z",
"firstFoundAt": "2024-04-16T09:04:13Z",
"foundAt": "2024-06-09T07:22:58Z",
"firstScanId": "4627cf29-3f45-4f71-aa0c-5658f8be3c99",
"description": "The iconv program in the GNU C Library (aka glibc or libc6) 2.31 and earlier, when invoked with multiple suffixes in the destination encoding (TRANSLATE or IGNORE) along with the -c option, enters an infinite loop when processing invalid multi-byte input sequences, leading to a denial of service.",
"data": {
"packageName": "libc6",
"packageVersion": "2.31-0ubuntu9.2",
"imageName": "library/maven",
"imageTag": "3-adoptopenjdk-11",
"imageFilePath": "docker/Dockerfile",
"imageOrigin": "Dockerfile"
},
"comments": {
"comments": ""
},
"vulnerabilityDetails": {
"cvssScore": 6,
"cveName": "CVE-2016-10228",
"cweId": "CWE-20",
"cvss": {
"scope": "UNCHANGED",
"score": "5.9",
"severity": "Medium",
"attack_vector": "NETWORK",
"integrity_impact": "NONE",
"user_interaction": "NONE",
"attack_complexity": "HIGH",
"availability_impact": "HIGH",
"privileges_required": "NONE",
"exploit_code_maturity": "2.2",
"confidentiality_impact": "NONE"
}
}
},
]
| Now, run GET /results, and the results type is shown as "containers". TipAside from the "type" name, all other content of the result remains unchanged. Sample container result: [
{
"type": "containers",
"id": "CVE-2016-10228",
"similarityId": "CVE-2016-10228",
"status": "NEW",
"state": "TO_VERIFY",
"severity": "MEDIUM",
"confidenceLevel": 0,
"created": "2024-06-09T07:22:58Z",
"firstFoundAt": "2024-04-16T09:04:13Z",
"foundAt": "2024-06-09T07:22:58Z",
"firstScanId": "4627cf29-3f45-4f71-aa0c-5658f8be3c99",
"description": "The iconv program in the GNU C Library (aka glibc or libc6) 2.31 and earlier, when invoked with multiple suffixes in the destination encoding (TRANSLATE or IGNORE) along with the -c option, enters an infinite loop when processing invalid multi-byte input sequences, leading to a denial of service.",
"data": {
"packageName": "libc6",
"packageVersion": "2.31-0ubuntu9.2",
"imageName": "library/maven",
"imageTag": "3-adoptopenjdk-11",
"imageFilePath": "docker/Dockerfile",
"imageOrigin": "Dockerfile"
},
"comments": {
"comments": ""
},
"vulnerabilityDetails": {
"cvssScore": 6,
"cveName": "CVE-2016-10228",
"cweId": "CWE-20",
"cvss": {
"scope": "UNCHANGED",
"score": "5.9",
"severity": "Medium",
"attack_vector": "NETWORK",
"integrity_impact": "NONE",
"user_interaction": "NONE",
"attack_complexity": "HIGH",
"availability_impact": "HIGH",
"privileges_required": "NONE",
"exploit_code_maturity": "2.2",
"confidentiality_impact": "NONE"
}
}
},
] |
Retrieving scan summary via API | Used to run GET /scan-summary, and the summary counters were returned in the section | Now, run GET /scan-summary, and the summary counters are returned in the section |