Software Supply Chain Security Results Viewer
The Software Supply Chain Security results viewer shows detailed SCS results for the latest scan of a specific project.
This screen can be accessed in either of the following ways:
Go to the Workspace
 > Software Supply Chain Security tab and click on the row of the relevant project, or
> Software Supply Chain Security tab and click on the row of the relevant project, or Go to the Workspace
 > Projects tab, hover over the Results link for the relevant project and select the SCS results viewer.
> Projects tab, hover over the Results link for the relevant project and select the SCS results viewer.
The results are shown separately for each scanner. If the project was scanned by more than one scanner, then you can select which scanner results to show using the drop-down list in the header bar.
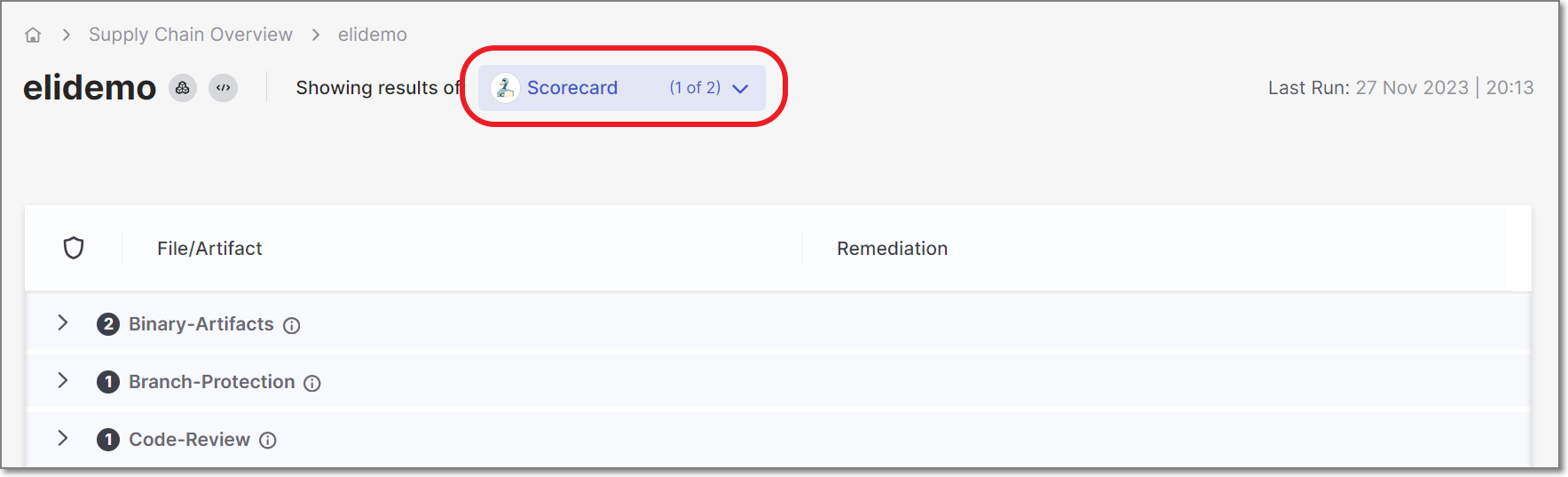
The main screen shows risks identified by the selected scanner, grouped by category. Click on a category to expand the display and show the affected file/artifact and the suggest remediation action.
You can apply filters and/or enter free text search strings.
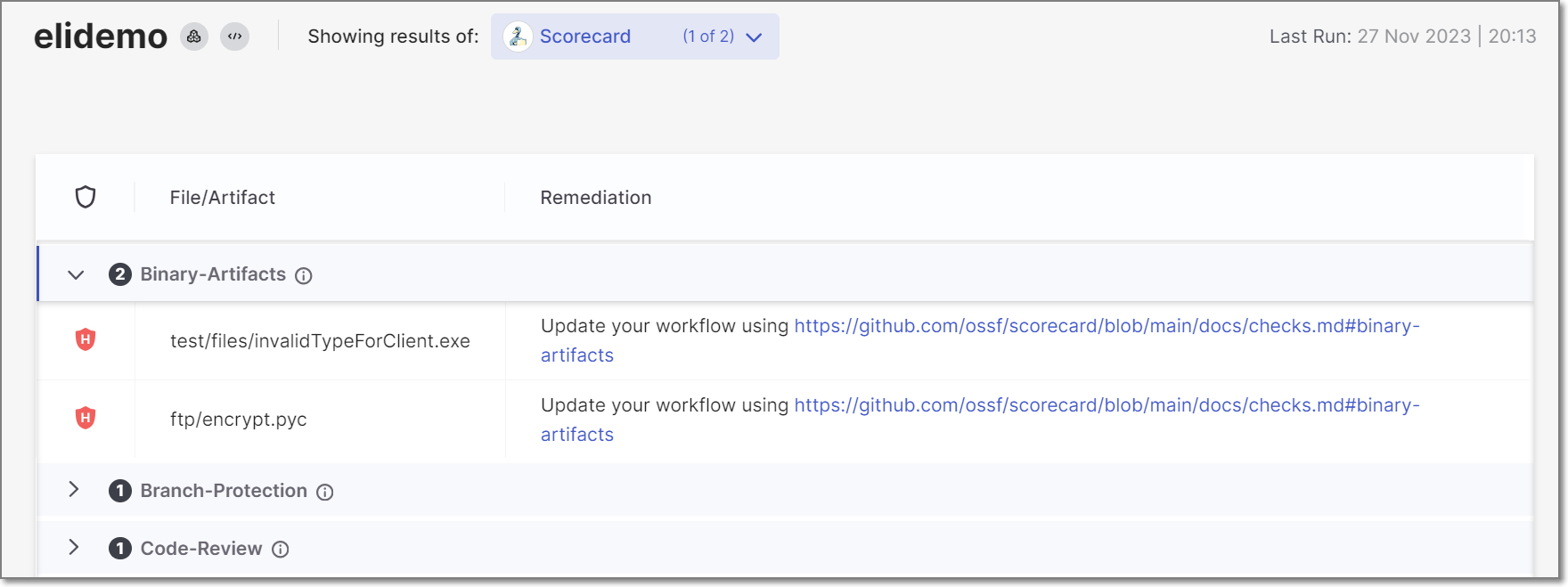
OSSF Scorecard
When the Scorecard scanner is selected, results are grouped by the OSSF check that identified the risk.
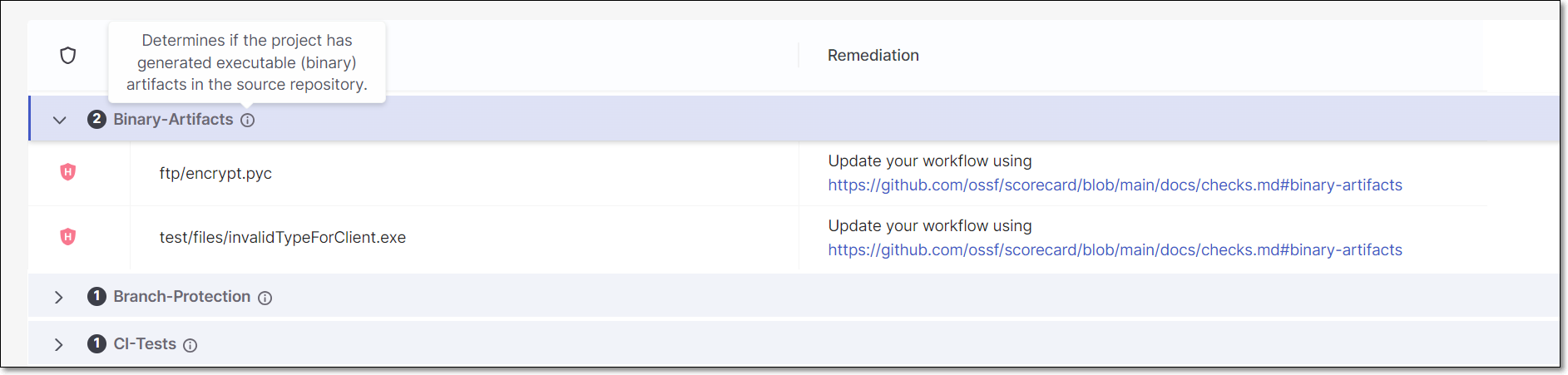
Hover over the info icon next to the name of a check type to see a description of that check.
Click on a check type to expand the section and show a list of risks of that type.
 |
The following table describes the information shown for each risk.
Item | Description |
|---|---|
Severity | The severity of the risk. |
File/Artifact | The path to the file or artifact in which the risk was detected. |
Remediation | Provides a link to the OSSF documentation which includes remediation recommendations for the relevant OSSF check. |
Secret Detection
When the Secret Detection scanner is selected, results are grouped by the type of secret detected. When you click on a type, a list of risks of that type is shown.
The following table describes the information shown for each risk.
Item | Description |
|---|---|
Severity | The severity of the risk. Note: The severity for all detected secrets is High. |
File/Artifact | The path to the file or artifact in which the secret was detected. |
Location | The line in which the secret was detected. |
Validity | Indicates whether or not the secret is currently valid. |
Remediation | Shows a few characters of the detected secret, with the remaining characters masked for security purposes. The recomended remediation for detected secrets is to first remove the secret from your file and then change the secret. |