Data Transformation for the Checkmarx One IntegrationConfiguring the Checkmarx One Vulnerability Integration
Once the data that is to be imported is identified, it is retrieved from the Checkmarx One application, processed through a set of data sources, and transformed in the instance.
Checkmarx One Application Vulnerable Item Integration
Note
The integration may not succeed if there are customizations in any fields on your ServiceNow platform.
The data from the API is first loaded into the Checkmarx One AppVul Item Import table, and the Checkmarx One AppVul Item Transform is used to transform the imported information.
To access this transform map:
Navigate to System Import Sets
Click Transform Maps
Search for Checkmarx One AppVul Item Transform
Note
The CheckmarxOne Application List Integration and CheckmarxOne Scan Summary Integration transform data similarly.
The following tables list the transform map fields by integration:
Table 1. CheckmarxOne App List transforms map fields:
Source Field(from CxOne) | Target Field(from SNOW) | Description |
|---|---|---|
app_id | Source Application ID | Project Id |
app_name | Application name | Project name |
project tags | Source APM AppId | Project tags |
groups | Source-assigned teams | Assigned group name of projects |
createdAt | Description | Project creation date in CxOne |
application Id & primary branch | Source additional info | Application ID and Primary Branch information |
Table 2. CheckmarxOne Scan Summary transforms map fields:
Source Field(from CxOne) | Target Field(from SNOW) | Description |
|---|---|---|
scan_id | Source scan ID | Scan type + Scan Id |
app_name | Discovered Applications | Project name |
loc | Static Scan Size | Lines of Code (only applicable for SAST scan) |
last_scan_date | Last scan date | Last scan date in CxOne |
scanId + last_scan_date | Scan summary name | Scan type + scan ID + last scan date |
total_no_flaws | Detected Flaw Count | Total no of vulnerabilities in the scan |
branch | Tags | Branch name |
Scan Origin, Scan Source, and Scan Type | Scan submitted by | Scan Origin, Scan Source, and Scan Type |
Table 3. CheckmarxOne AppVul Item transforms map fields:
Source Field(from CxOne) | Target Field(from SNOW) | Description |
|---|---|---|
similarityId+resultHash | Source AVIT ID | AVIT ID for SAST |
similarityId + package_unique_id | Source AVIT ID | AVIT ID for SCA |
similarityId | Source AVIT ID | AVIT ID for IaC |
app_name | Discovered Applications | Project name |
scanId + last_scan_date | Scan Summary | Scan type + scan ID + last scan date |
updatedAt | Last found | Last Scan date from CxOne |
scan_type | Scan type | SAST/IaC: 'Static’ SCA: ‘SCA’ |
category_name | Category name | SAST/IaC: query name SCA: CWE ID |
first_found_date | First found | First found date in CxOne tenant |
recommendedVersion | Recommendation | recommended version (only applicable for SCA scan) |
packageIdentifier | Package | Package ID (only applicable for SCA scan) |
nodeId + path | Source notes | Node ID and filename (only applicable for SAST scan) |
category_id + " -" + cweId | Vulnerability | SAST: ‘Checkmarx One’ + ‘CWE-‘ + CWE ID SCA: ‘Checkmarx One’ + ‘-‘ + CVE ID IaC: ‘Checkmarx One’ + ‘-‘ + Query Id |
sourcefile | Source link | CxOne vulnerability URL |
location | Location | File name (only applicable for SAST scan) |
description | Vulnerability summary | Source vulnerability summary |
description | Description | Vulnerability description |
line | Line number | Line on which the flaw was found (only applicable for SAST scan) |
state | Source finding status | Vulnerability state from Checkmarx One |
Application Id, Branch Name | Source additional info | Application ID and Branch name |
source_severity | Source severity | Severity information of vulnerability |
Branch | Project Branch | Branch name of the project |
similarityId | Source Request | Similarity Id of findings(only applicable for SAST scan) |
path/reference/node | References | Path details for the SAST scan, References for the SCA scan, and node information for the IAC scan. |
Result Status | Source Remediation Status | Result status of findings. |
Exploitable Path | Source Notes | Exploitable path if present in the SCA scan will be mapped to the Source Notes column of the AVIT table |
The following transform scripts are run during the transformation process.
Checkmarx One Transform Map Script Timing and Purpose
When the script is run | Purpose |
onComplete (when an import set has completed transformation) | Script that is used to process the data source and update the count of AVITs created, updated or unchanged, and the ones imported as part of this integration from Checkmarx One. This script is for internal use and should not be modified or deleted. |
Viewing Checkmarx One Vulnerability Integration Import
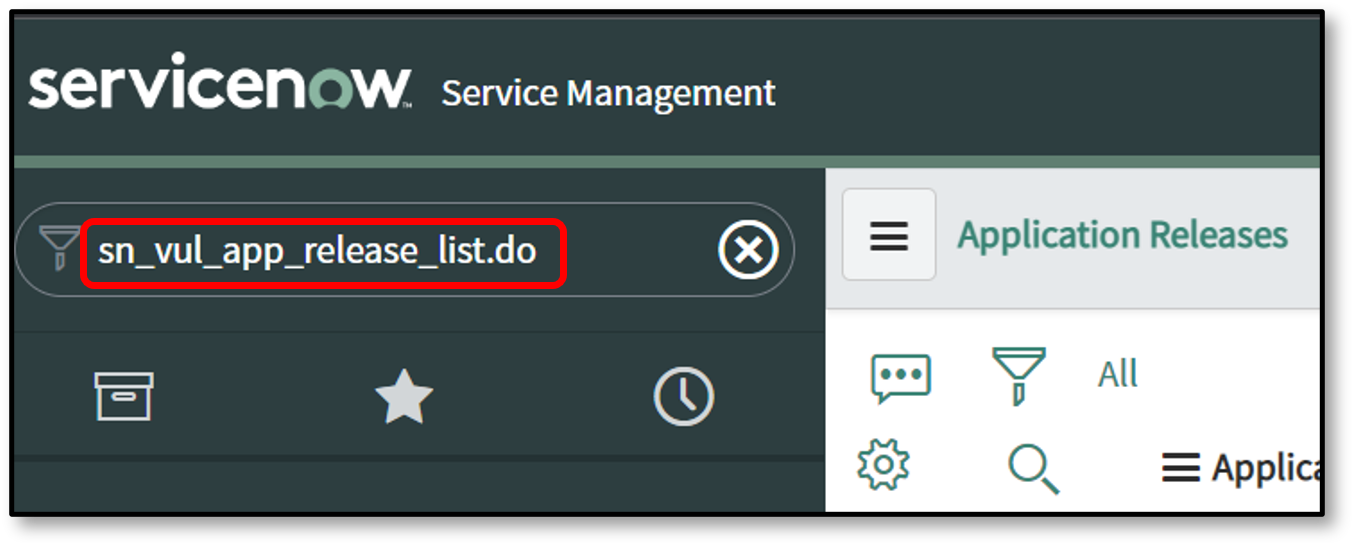
To view the Checkmarx One Application List Integration or Application Releases table in Filter Navigator enter sn_vul_app_release_list.do
 |
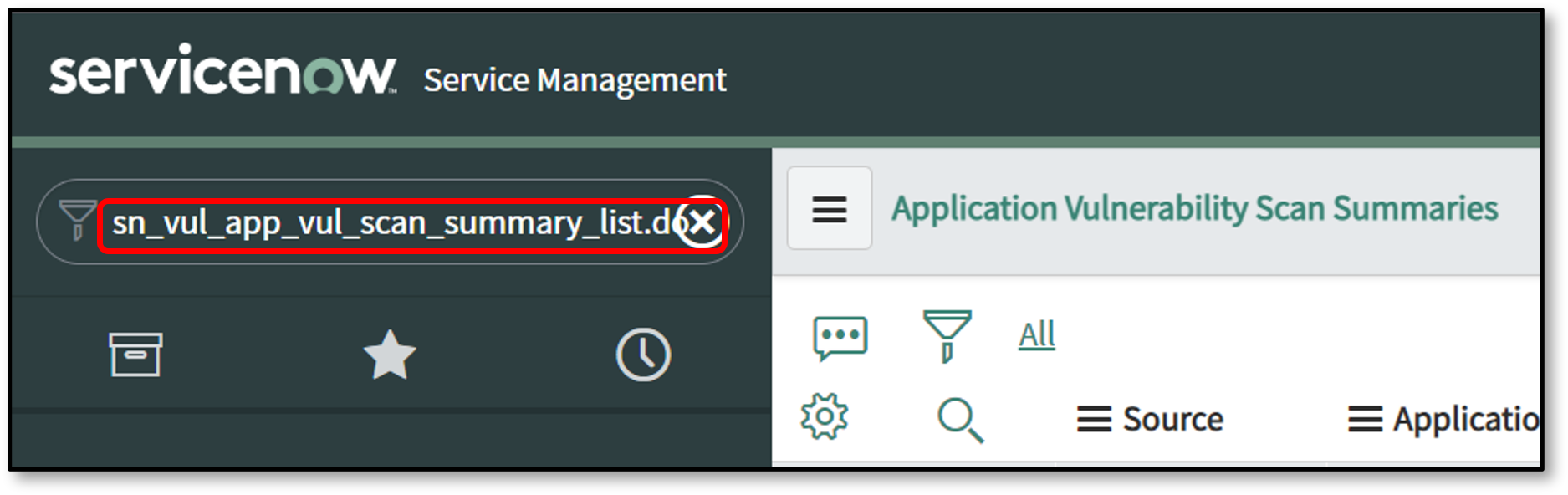
To view the Checkmarx One Scan Summary Integration or Application Vulnerability Scan Summaries tables in Filter Navigator enter sn_vul_app_vul_scan_summary_list.do
 |
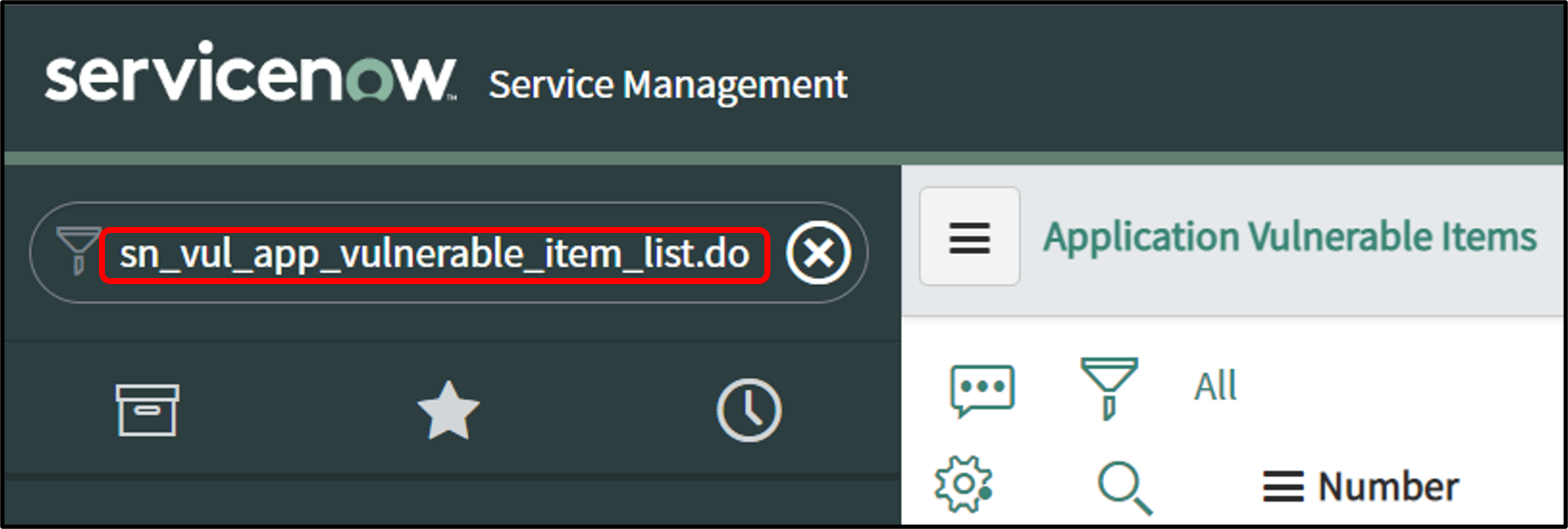
To view the Checkmarx One Application Vulnerable Item Integration or Application Vulnerable Item tables in Filter Navigator enter sn_vul_app_vulnerable_item_list.do
 |
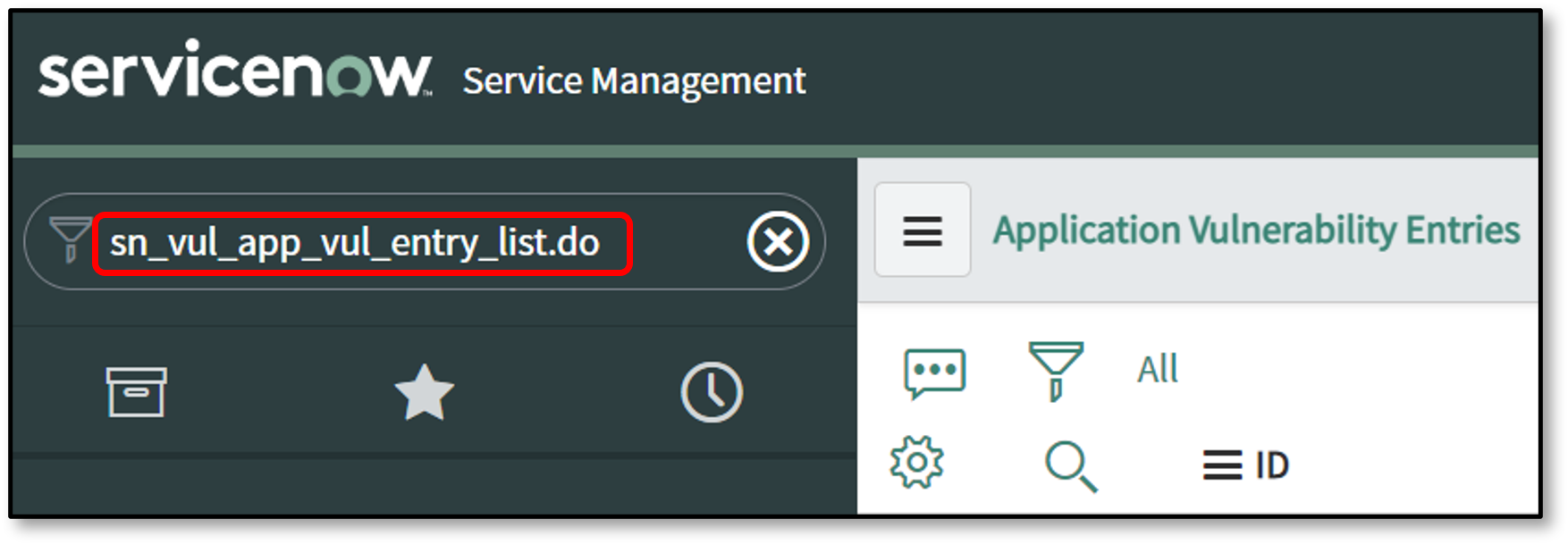
sn_vul_app_vul_entry_list.do
 |