Checkmarx Dependency Checker Plugin for Jetbrains IntlliJ IDEA
Overview
Dependency Checker is a native Intellij plugin powered by Checkmarx that enables users to initiate Checkmarx SCA scans directly from their IntelliJ IDE, and shows detailed results as soon as the scan is completed. The scanner checks against Checkmarx's proprietary database to identify the open-source dependencies used in your code and the security risks associated with those packages.
The identified packages are shown in a tree structure with an indication of the risk level for each package. You can drill down to show the specific vulnerabilities associated with a package. Checkmarx also offers recommended remediation steps, which can be implemented directly in the IDE.
Warning
This plugin was developed by JetBrains. As such, requests for assistance using the plugin should be addressed to JetBrains support.
Note
Checkmarx SCA is Checkmarx’s proprietary Software Composition Analysis (SCA) solution for detecting risks associated with your open source dependencies. Checkmarx SCA is a cloud native SaaS solution which enables you to easily identify, prioritize, and remediate the risks posed by your open source packages. These risks may include security vulnerabilities, suspected malware risks, license requirements and outdated open source packages. Checkmarx SCA addresses all of these issues, providing highly accurate, relevant, and actionable insights. See Checkmarx SCA
Main Features
Free tool, no Checkmarx account required
Run scans directly from your IDE
View actionable results in your IDE, indicating which of your open-source packages are at risk
Easily remediate vulnerabilities in the IDE
Provides links to learn more about each vulnerability on Checkmarx’s Advisories website
Limitations
This plugin currently supports only Maven and Gradle dependencies.
Prerequisites
You need to install all relevant package managers on your local environment, see Installing Supported Package Managers for Resolver.
Notice
This is a free tool for all IntelliJ users, and does not require the user to submit credentials for a Checkmarx SCA account. For SCA users, the scan results from this plugin are not synced with their SCA account.
Installing the SCA Extension
For users with IntelliJ IDEA v. 2022.1 and later, with a license for Ultimate or All Products Pack, Dependency Checker comes bundled with the IntelliJ IDEA installation.
For earlier versions, download the plugin installation file here.
Running a Scan
To scan a project in IntelliJ:
Right-click on the project in the navigation pane, and select Analyze > Show Vulnerable Dependencies.
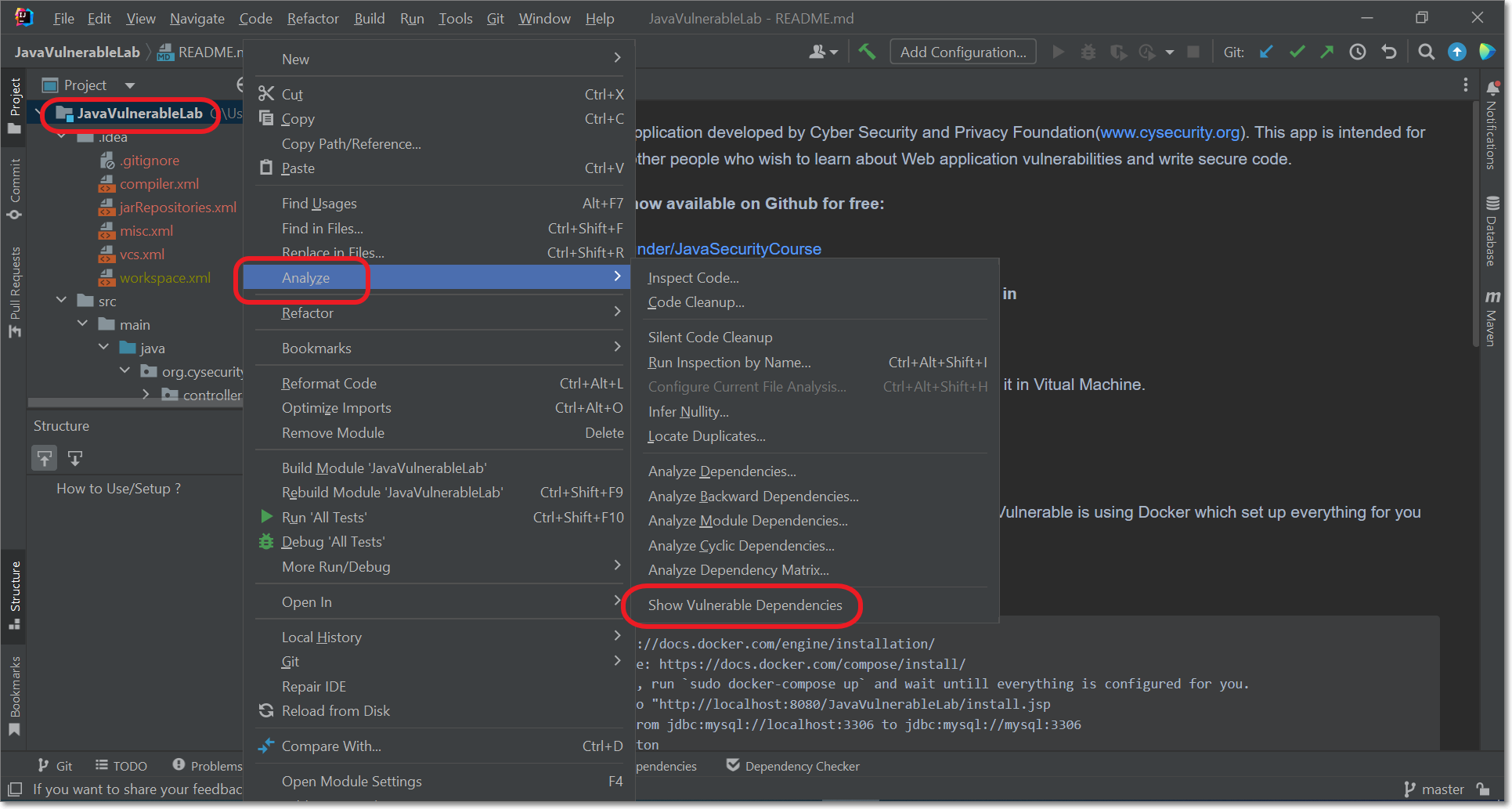
As soon as the scan is complete, the results are shown in the IDE.
Viewing SCA Results
The SCA results are shown in the Dependency Checker tab at the bottom of the screen.
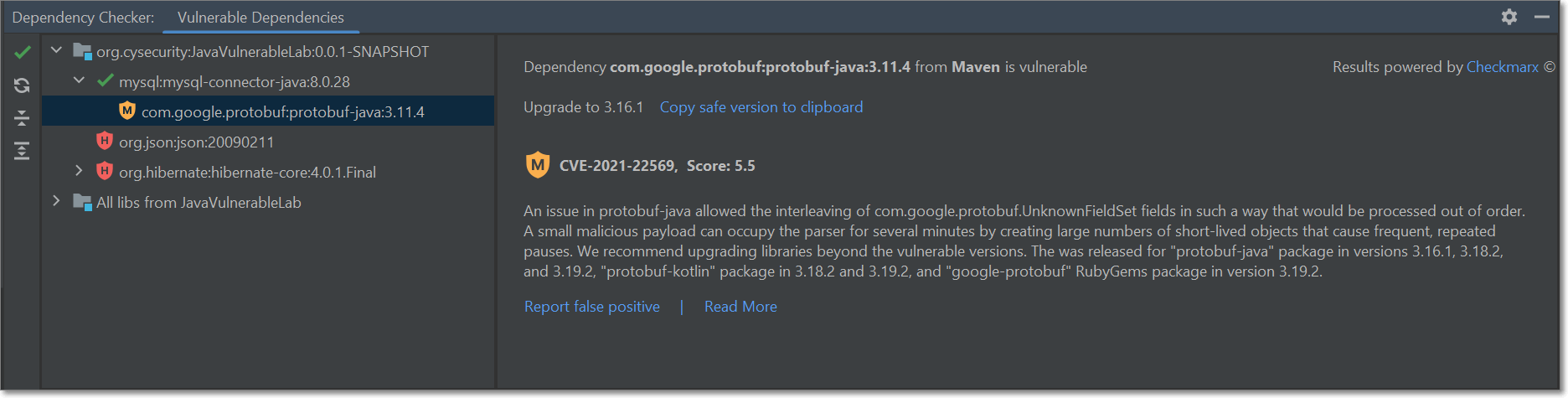 |
In addition, the vulnerable packages are highlighted in the editor window for the manifest file.
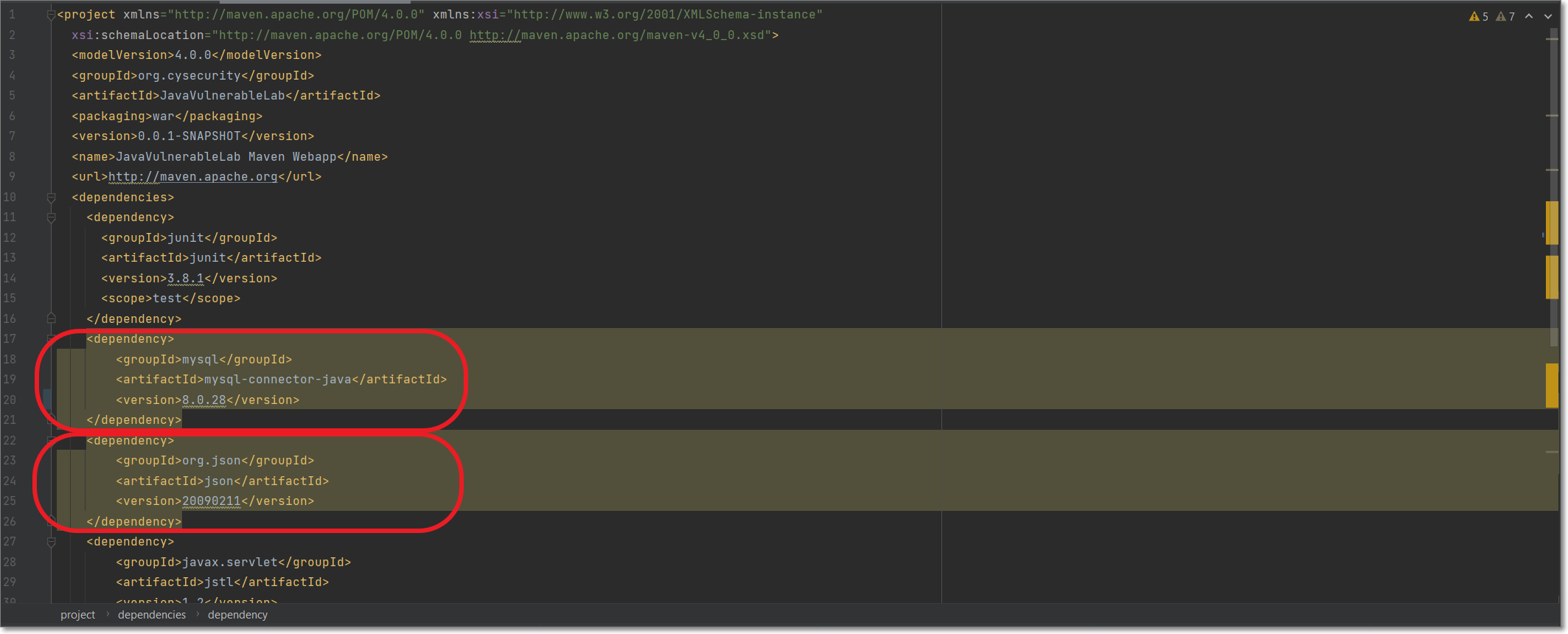 |
Viewing SCA Results in the Dependency Checker Tab
To view SCA scan results in the Dependency Checker:
Go to the Dependency Checker tab.
The Dependency Checker navigation pane shows results in a tree structure. The top section shows the hierarchical structure of direct dependencies and their associated transitive dependencies. Below that, the All libs tab, shows all vulnerable packages in a flat structure. For each package, an icon indicates whether or not it contains vulnerabilities and what the risk level is, see Dependency Checker Icons below.
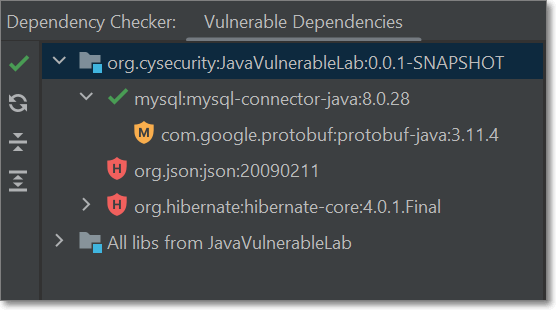
You can adjust the display using the toolbar options, see Dependency Checker Icons.
Click on a package to open a tab showing the vulnerabilities associated with that package.

Click on the Read More button to access an in-depth analysis of the vulnerability on the Checkmarx Advisory website.
Dependency Checker Icons
Icon | Description |
|---|---|
 | Project folder |
 | No known vulnerabilities |
 | Low risk vulnerabilities |
 | Medium risk vulnerabilities |
 | High risk vulnerabilities |
Toolbar Options | |
 | Show/hide packages that don’t contain any known vulnerabilities. |
 | Refresh the display. |
 | Collapse the display. |
 | Expand the display. |
Remediating Vulnerable Packages
To remediate a vulnerable package:
In the editor window of the manifest file, hover over a highlighted (vulnerable) dependency. A dialog opens showing the vulnerabilities associated with that package.
If Checkmarx has identified a version of the package that isn’t vulnerable, then a remediation actions will be suggested, indicating that you should change to the non-vulnerable package version. Click on this action to automatically change to the secure version.
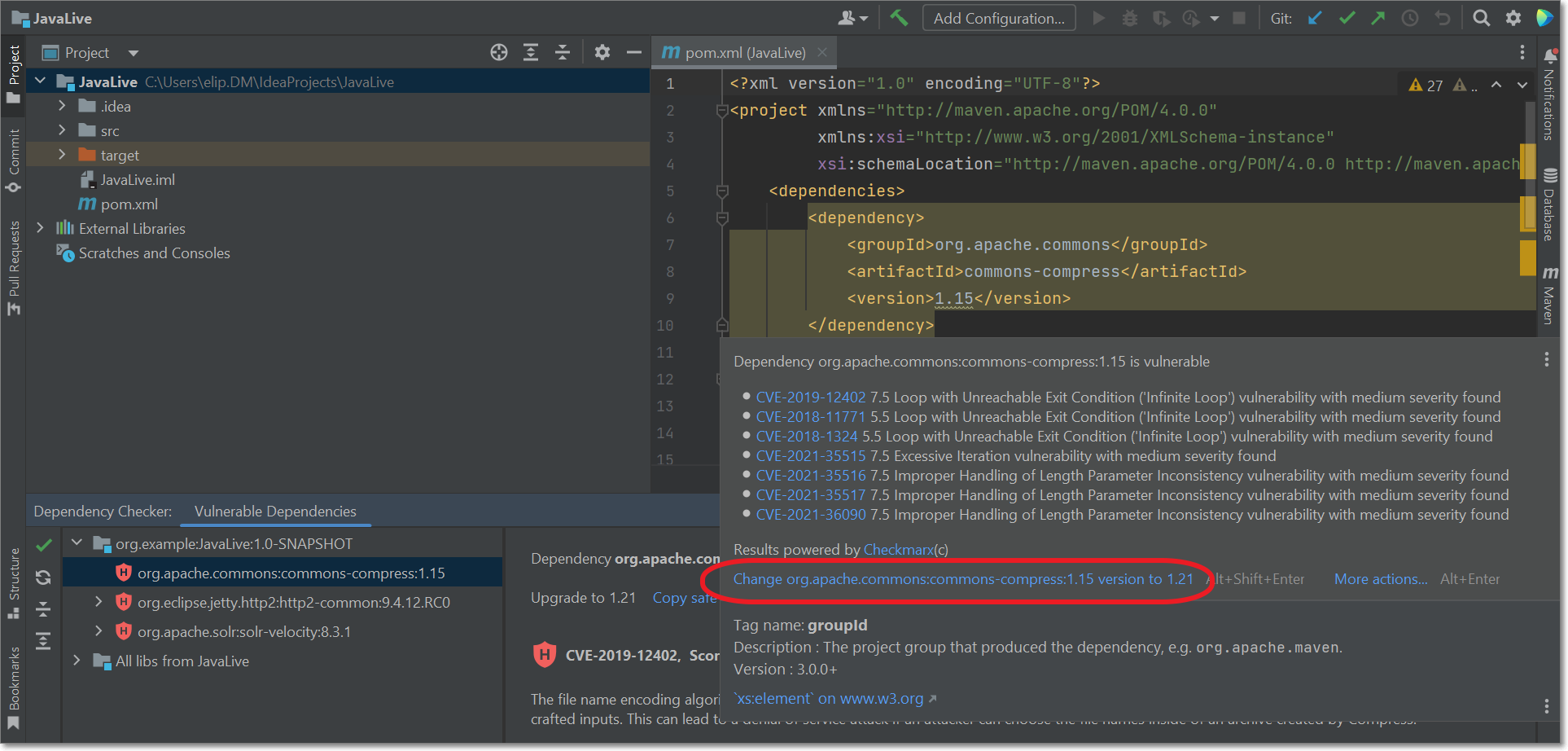
Click on the Load Maven Changes button that appears in the editor.

The change is implemented in the manifest file.