- Checkmarx Documentation
- IAST Documentation
- User Guide
- System Management Settings
- Query Lists
Query Lists
A list contains a combination of methods that defines how the IAST agent collects information. Queries contain the code that uses this information in order to detect vulnerabilities.
The Query Editor screen displays lists in the Lists tab. The Lists tab is divided into two expandable segments for Lists provided by Checkmarx and Custom Lists. In both segments the lists are separated according to list types. The available list types are listed below.
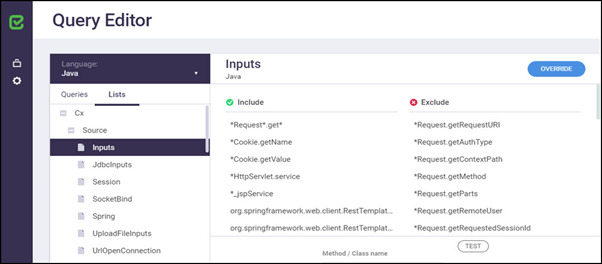
Click Settings and select Query Editor. Click the List tab. The query list is displayed as illustrated and explained below.
Type | Description |
|---|---|
Sources | Provides methods that potentially start a vulnerable flow, for example user input for SQL Injection or DB access to Stored XSS. |
Propagators | Provides methods that can potentially change the data and are important to track in order to detect vulnerabilities, for example sanitizers. |
Sinks | Provides methods that perform actions, for example DB access, OS execution, etc. |
Single Methods | Provides methods that expose application threats, for example cryptographic algorithms. |
By expanding a list type, all lists allocated to the selected type are displayed. Selecting a list displays the structure of the list in the List Structure panel to the right.
Each list contains an Included and an Excluded column, which specify the methods to be included or excluded from instrumentation while executing the application. These columns may contain the explicit method name (and class) or alphanumeric characters and asterisks.
Overriding a list simply means to use an existing Cx list and customize it according to your specific requirements. A customized list takes preference over the Checkmarx list, unless the customized list is deleted and the original Checkmarx list regains preference. You can also create a new list from scratch and define the specific list structure that you require.
Note
Adding new items to any of the lists or creating a new list requires an application restart.
To override an existing list:
Click the Lists tab, expand the Checkmarx Lists segment according to the relevant type and select the desired list. The selected list structure is displayed in the List Structure panel.
Click <OVERRIDE>. An overwritten version of the list is displayed in the List Structure panel as well as the Customer List segment according to the selected type.
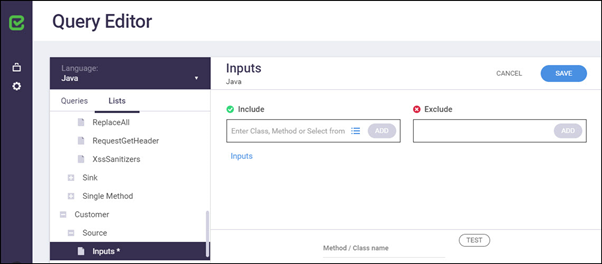
Upon override, a link to the original Checkmarx list is included, which cannot be deleted. You can add a specific method into the Include field, or you can select from a predefined list by clicking Include.
Click <ADD> to complete adding the method.
Add any methods that should be excluded into the Exclude field and click <ADD> to complete excluding the method.
Click <TEST> to validate the method. The method is applied when running the application next time.
Click <SAVE> to save the customized list.
Once a custom list is no longer required, you can choose to delete it from IAST.
To delete a custom list:
Click the List tab, expand the Cx Customer segment according to the relevant type and click … .
Click <DELETE>. The selected custom query is deleted from the system.