- Checkmarx Documentation
- Checkmarx One
- Upcoming Features
- SCA Remediation Tasks
SCA Remediation Tasks
We are adding a new tab, Remediation Tasks, to the SCA results viewer.
Remediation Tasks Tab
The Remediation Tasks tab shows detailed information about specific remediation tasks that Checkmarx recommends implementing for your Project. These tasks involve replacing vulnerable packages in your project with non-vulnerable versions of those packages.
 |
Notice
Remediation tasks are currently supported only for JavaSript npm packages and for Nuget packages with .csproj manifest files, otherwise this tab isn't shown.
The Remediation Tasks tab contains sub-tabs that show two types of pages:
All Remediation Tasks – shows a list of remediation tasks that are recommended for this Project, with general info about each task.
Task Details – shows detailed info about a specific task. The task details tab is opened by clicking on the How to fix button in a task row in the All Remediation Tasks sub-tab.
You can navigate between the various tabs that you have opened.
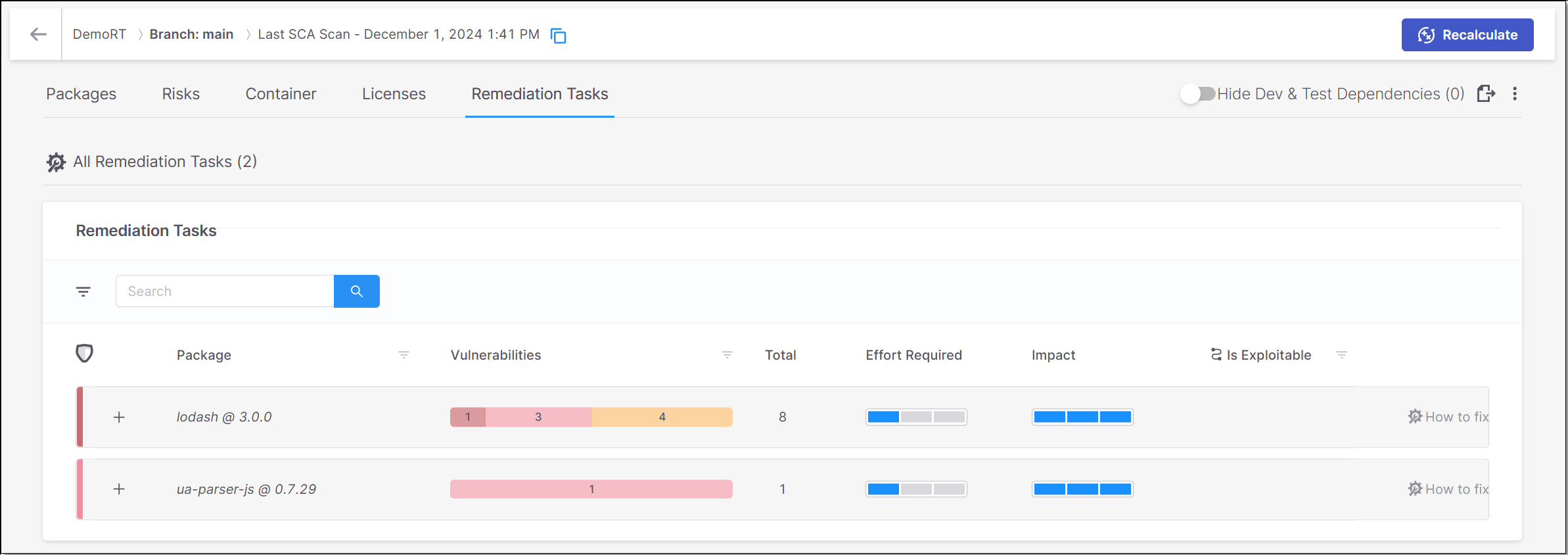
All Remediation Tasks
The All Remediation Tasks sub-tab shows a list of remediation tasks that are recommended for this Project.
Notice
Each task relates to a specific direct package in your project.
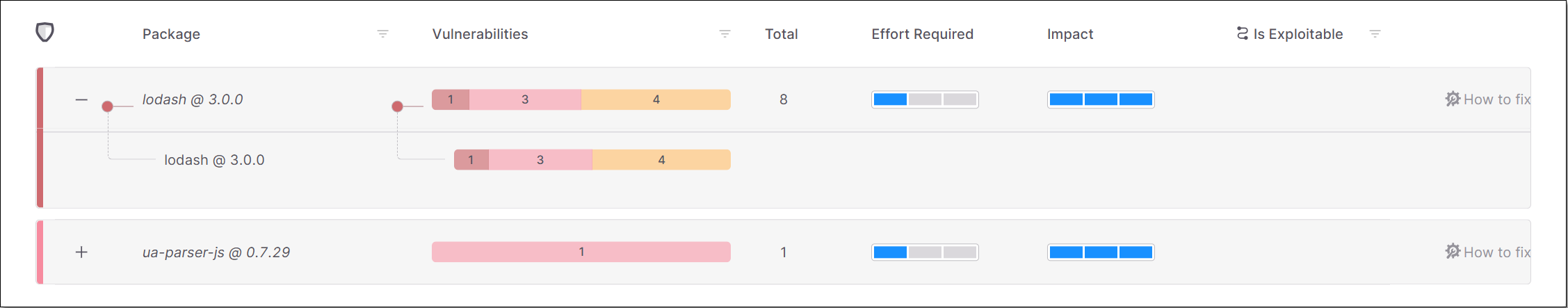
The data shown for each task relates to the vulnerabilities identified in the direct package as well as in the transitive dependencies associated with it. You can click on the “+” button for a task to expand the view of that task to show the transitive dependencies called by the package. The number of vulnerabilities of each severity level is shown for each transitive package.
 |
The following table describes the info shown for each task:
Parameter | Description |
|---|---|
+/- Button | Expand the display to show the transitive packages or collapse the display to show only the direct package. |
Package | The name of the package and its version number. |
Vulnerabilities | The number of vulnerabilities of each severity level in the package. |
Total | The total number of vulnerabilities in the package. |
Effort Required | An assessment of the degree of effort required to implement the recommended remediation task, e.g., if it requires fixing broken API methods. |
Impact | An assessment of the impact that the remediation task will have on your Project, i.e., the extent to which the procedure will remove risks from your Project. |
Is Exploitable | Indicates whether the vulnerabilities in this package are exploitable in the context of your Project. TipThis data is only shown for scans which ran using the Exploitable Path feature. |
“How to fix” button | Click on this button to open a new sub-tab showing details about this remediation task. |
Remediation Task Details
The Remediation Task Details sub-tab shows detailed info about a specific remediation task.
Notice
Each task relates to a specific direct package in your project.
The info on this screen is shown in the following panes.
Overview - shows key metrics for the remediation task.
Summary - shows general info about the remediation task.
Remediation Impact - shows a comparison between the current vulnerabilities and the vulnerabilities that will remain after remediation.
Developer Walkthrough - shows a breakdown of the steps that need to be taken to remediate this package.
Overview
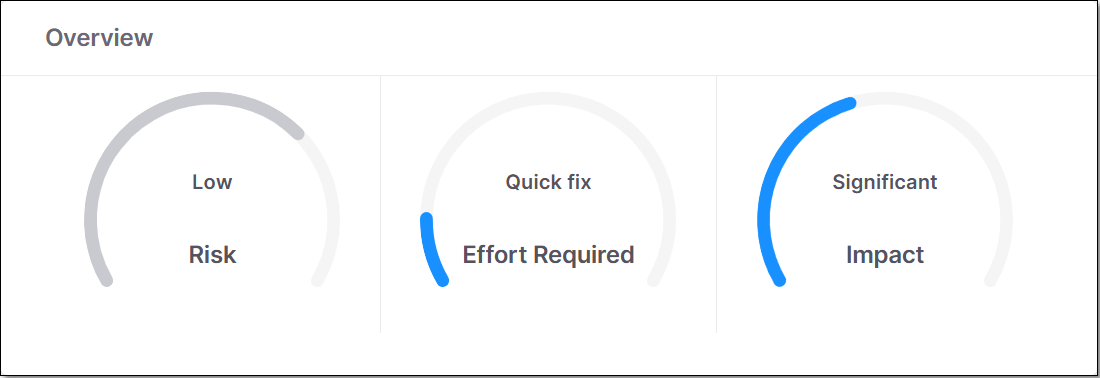 |
This pane shows gauge widgets indicating the overall risk level for the specified package, the effort required to implement the suggested remediation procedure and the impact of remediation.
Summary
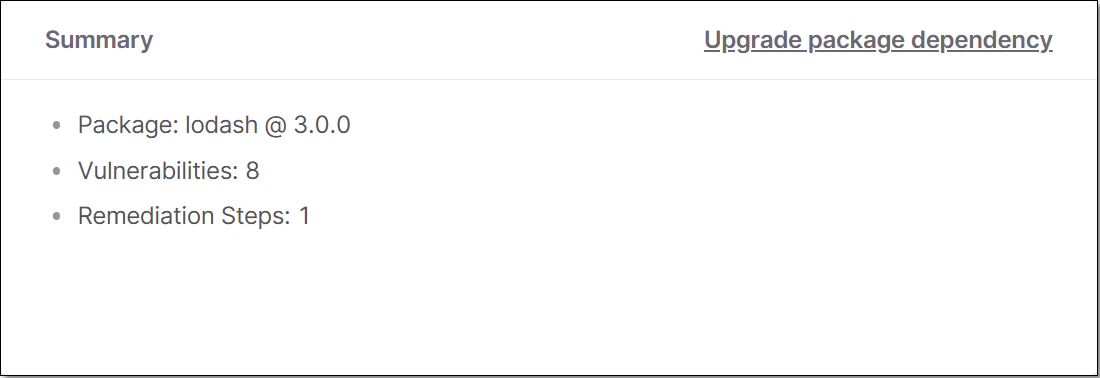 |
This pane shows a summary of the remediation task, including the package name, number of vulnerabilities and total number of remediation steps.
Remediation Impact
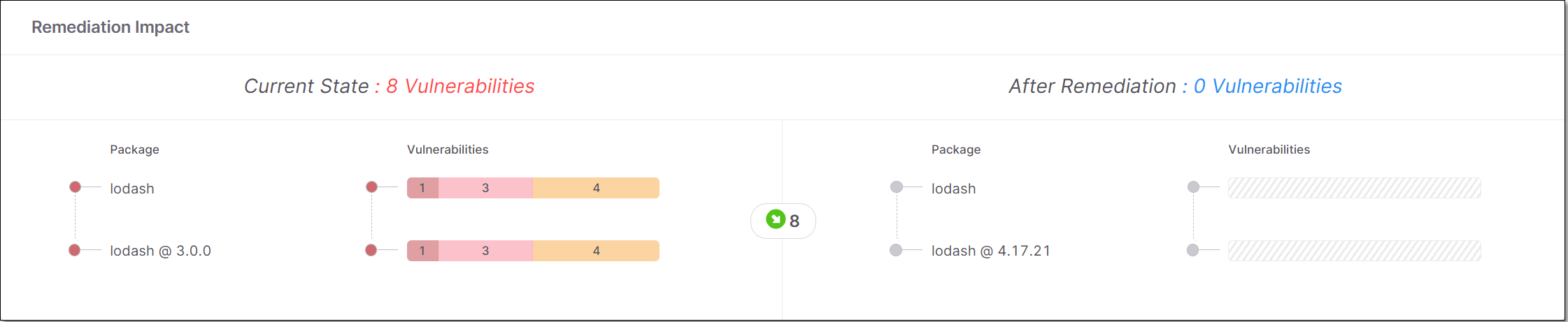 |
This pane shows a side-by-side comparison between the vulnerabilities currently in the direct and transitive dependencies and the vulnerabilities that will remain after remediation.
Note
Checkmarx SCA shows recommendations to upgrade each transitive dependency to the next suitable version, even if the current version doesn't have vulnerabilities. You should use your judgement to decide whether the benefit of upgrading is worth the effort of ensuring compatibility of the new version.
Developer Walkthrough
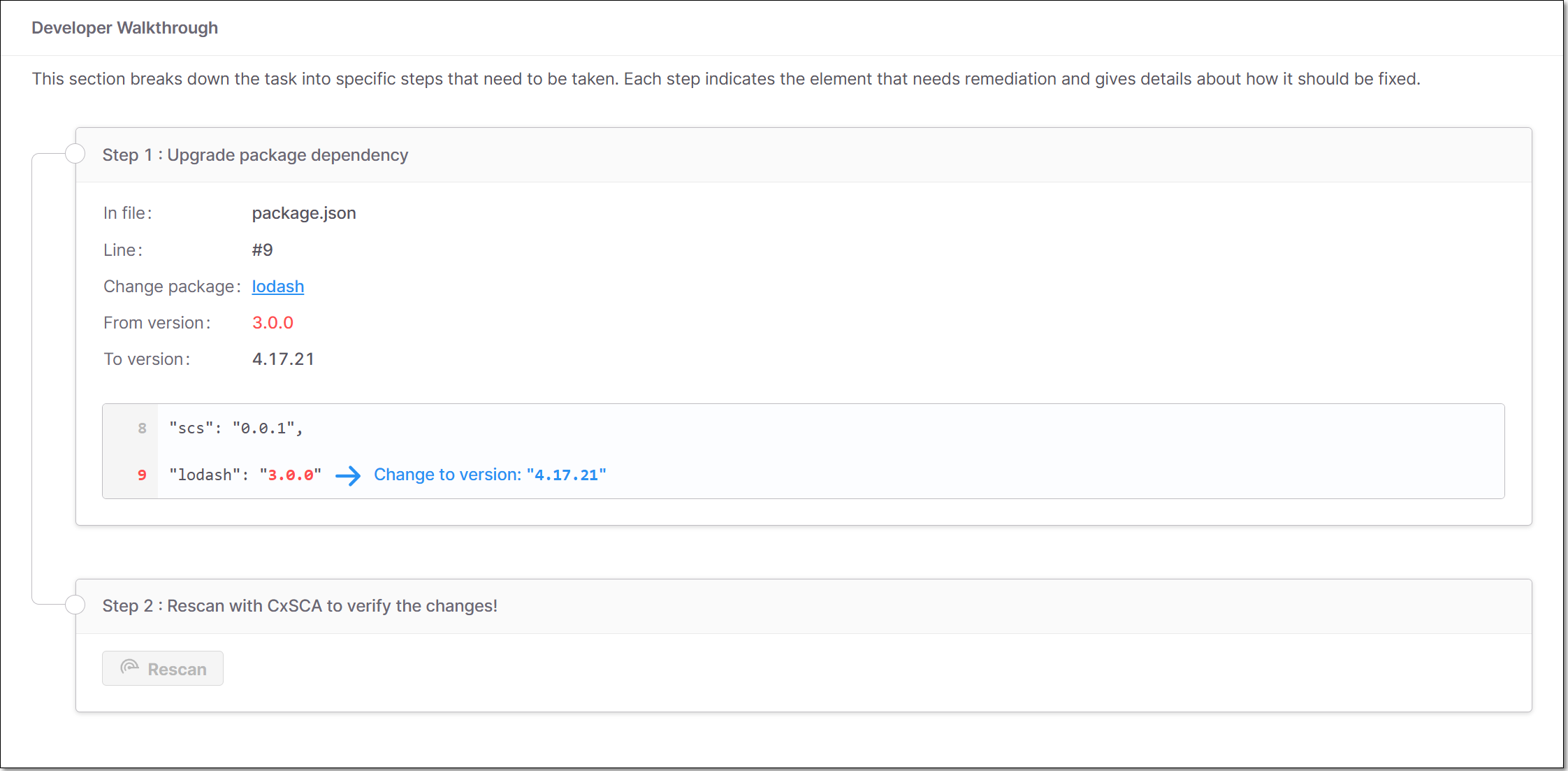 |
This section breaks down the task into specific steps that need to be taken. Each step indicates the element that needs remediation and gives details about how it should be fixed. There are three types of steps:
Upgrade package dependency - indicates the direct package that needs to be upgraded, where it appears in your code, and which version it should be upgraded to.
Add package dependency - indicates a specific version of a package that needs to be added to your manifest file (for transitive dependencies).
Notice
Recommended steps for remediating transitive vulnerabilities are given for each package independently. We recommend a secure version of the package that can be added to the manifest file in order to ensure that only that version will be used.
In some cases it may be possible to remediate transitive dependencies by upgrading the direct dependency to a version that references a newer, secure version. For Maven packages, the Maven repository shows the transitive package versions referenced by each package.
Fix broken API methods - shows each of the API methods that was broken and which upgrade caused the API to break. Fix broken API methods is shown as a sub-step under the “Upgrade package dependency” step that causes the broken method.
Note
Broken methods are only identified in scans for which the Exploitable Path feature is run.
Checkmarx SCA identifies broken API methods by comparing the number of parameters used in the public method for the new package with the number of parameters used for the original package. If the number of parameters is different, then we notify of the need to fix the API method.